Operations | Monitoring | ITSM | DevOps | Cloud
Messaging
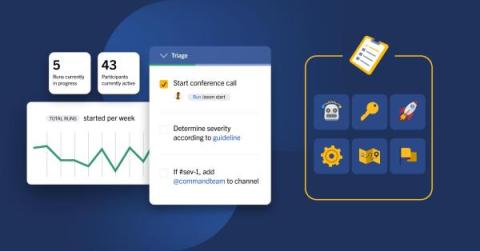
Mattermost Playbooks for Enterprise Workflows
Mattermost Playbooks are configurable checklists that power team workflows with automation and real-time messaging. At a high level, Playbooks help teams work through recurring workflows efficiently, making sure all important tasks are taken care of while keeping teams aligned.
Understanding the Differences Between RabbitMQ and Kafka
This blog was co-written by Howard Twine and Gregory Green. A few years ago, a colleague of ours wrote an informative post to help readers understand when to use RabbitMQ and when to use Apache Kafka. While the two solutions take very different approaches architecturally and can solve different problems, many people find themselves comparing them for situations where there is overlap.
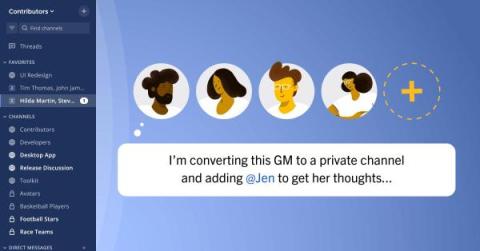
Mattermost v9.1: Group Message enhancements
Group Messages (GMs) allow for quick and/or infrequent interactions with three to seven users. In Mattermost v9.1, there are two new quality-of-life updates aimed at enhancing user experience.
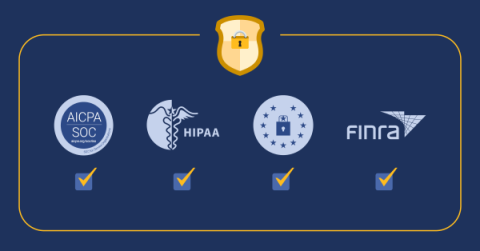
Security and compliance for enterprise collaboration
In today’s increasingly data-driven business landscape, security and compliance are more important for enterprise software than ever before. In an age where high-profile data breaches and regulatory violations seem to make headlines more frequently, enterprises must prioritize the protection of sensitive information while ensuring compliance with an exceedingly complicated labyrinth of legal and industry-specific requirements.
Mattermost v9.1 Changelog
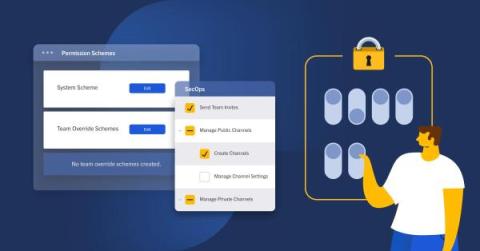
Advanced Access Controls with Mattermost Enterprise Edition
While some smaller companies may only need to use standard access controls to shore up systems, large organizations — particularly those with strict security, confidentiality, and compliance requirements — often require advanced functionality that gives them more authority over which users can access what systems and when.
Delivering Distributed Transaction Tracing Across Integration MESH
Distributed transaction tracing (DTT) is a way of following the progress of message requests as they permeate through distributed cloud environments. Tracing the transactions as they make their way through many different layers of the application stack, such as from Kafka to ActiveMQ to MQ or any similar platform, is achieved by tagging the message request with a unique identifier that allows it to be followed.
Everything you need to know about data sovereignty
In today’s digital age, the most effective organizations are using data to fuel innovation and accelerate business strategies. Data continues to be at the heart of business growth. Organizations increasingly rely on technology to manage and store their data. Questions about ownership, control, and security have emerged — leading to the rise of a concept known as data sovereignty. In this post we’ll explore.