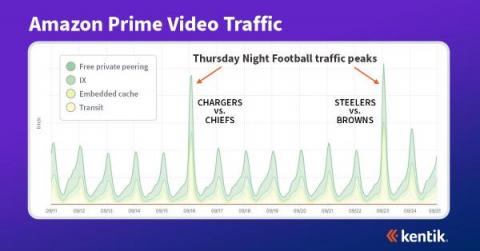
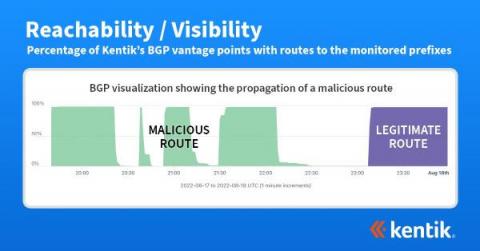
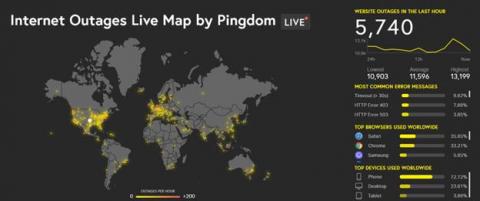
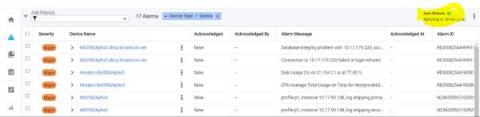
Why OpManager is the perfect tool to detect and troubleshoot Wi-Fi performance issues
Wi-Fi has untangled humanity, quite literally. Those jumbled Ethernet cables with their confusing ports are banished to backstage. Now, all we need is one connection to a Wi-Fi router and voila! Internet. Wi-Fi networks simplify your IT infrastructure. WLAN networks makes an office look less like a scene from The Matrix and more like a creative workspace, but it can bring an array of difficulties as well. Unlike the sturdy Ethernet cable, Wi-Fi connections fluctuate.