What Caused the Red Sea Submarine Cable Cuts?
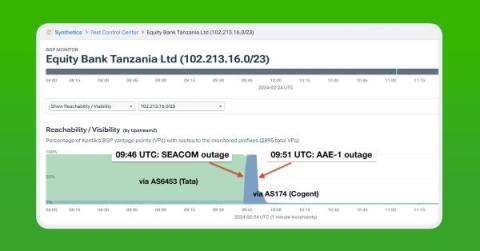
In the latest collision between geopolitics and the physical Internet, three major submarine cables in the Red Sea were cut last month likely as a result of attacks by Houthi militants in Yemen on passing merchant vessels. In this post, we review the situation and delve into some of the observable impacts of the subsea cable cuts.