Operations | Monitoring | ITSM | DevOps | Cloud
October 2022
Preventing PII in Test environments
Documenting your APIs with developer API portals
Autoscaling Checkly Agents with KEDA in Kubernetes
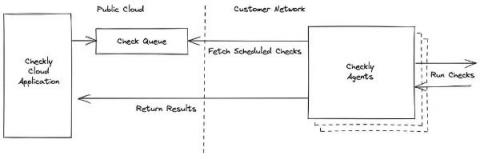
Checkly private locations enable you to run browser and API checks from within your own infrastructure. This requires one or more Checkly agents installed in your environment where they can reach your applications and our Checkly management API. You need to ensure you have enough agents installed in order to run the number of checks configured in the location. We have a guide to planning for redundancy and scaling in our documentation.
GitHub Sync goes GA
We now support Playwright Test!
Security Controls - REST API - PowerShell Tutorial
Checkly GitHub Sync Goes into GA
Welcome to the last day of our first Checkly Launch Week! We already talked about security, our new Playwright test runner and alert enhancements. Today, I’m delighted to announce that GitHub Sync is going into general availability (GA)! This post goes into the following topics.
Unleash the Full Power of Playwright With @playwright/test
Welcome to day three of our very first Launch Week! The last two days we shared how alerting became so much better and how we moved one level up by completing our SOC 2 Type 1 audit. Are you curious what’s next? I’ll tell you, but first let’s set the stage and look at Microsoft’s Playwright.
Checkly Completes SOC 2 Type 1 Audit
A Service Organization Control (SOC) audit is one of the most extensive tests an organization can undergo to demonstrate the ongoing maintenance of high-level information security. Today, we’re thrilled to announce that Checkly is SOC 2 Type 1 compliant after completing a successful audit by an accredited auditing firm. This demonstrates that Checkly’s information security policies, procedures, and practices meet the SOC 2 guidelines for security and data privacy.
New alert notifications, mobile improvements and our new community
Checkly Announces Business Milestones, SOC 2 Compliance, New Playwright Test Runner, GitHub Sync, Enhanced Alert Notifications, and More
Checkly Alerting Improvements and Our New Slack Community
Welcome to day one of our very first Launch Week! In the upcoming days, we’ll release new features every day. We’ll share new alerting capabilities, unlock the power of Playwright, and will talk about new ways to control and write your Browser checks. It’ll be a nice feature and improvements mix, trust me! To kick things off, let’s have a look at what’s new in the world of monitoring and alerting.
What's New in Checkly Launch Week
The Checkly development team is continually improving our platform and user experience, and we’re excited to unveil some new features that we’ve been working on during our first ever Checkly Launch Week. From October 11th through 14th, we’ll be announcing and discussing our latest innovations, new features, functionality, and capabilities for users every single day of the week.
Production Data Simulation: Record in One Environment, Replay in Another
Have you ever experienced the problem where your code is broken in production, but everything runs correctly in your dev environment? This can be really challenging because you have limited information once something is in production, and you can't easily make changes and try different code. Speedscale production data simulation lets you securely capture the production application traffic, normalize the data, and replay it directly in your dev environment. There are a lot of challenges with trying to replicate the production environment in non-prod.
Datadog on gRPC
We're SOC2 compliant!
Why IT Skills Are Vital When You're Running an eCommerce Business
An Introduction to gRPC
gRPC is an inter-process communication protocol used in high-performance applications in cloud computing, Internet of Things (IoT), mobile computing, and microservices environments. This article examines how gRPC works, how to use it, and how it compares to other popular API architectures. It also discusses a unique use case where gRPC excels.