Operations | Monitoring | ITSM | DevOps | Cloud
January 2024
Exploring Form Submission and Custom Keyboards #short
Revolutionizing the Digital Employee Experience: Almaden and Selbetti Join Forces in MSP Partnership
Continuous Monitoring Best Practices
5 Ways to Tackle Digital Transformation With ITSM
Elevating DEX: Nexthink's AppLearn Acquisition Marks a New Era
Ivanti Neurons for MDM: Protecting Samsung Devices from Phishing #shorts
Best ITSM Tools in 2024 and How to Pick One for Your Particular Case
Understanding Content Filtering with TMTT #shorts
Question Time: GenAI Trailer | ServiceNow
Question Time: GenAI for Customer Experiences | ServiceNow
Question Time: GenAI for Developing on the Now Platform | ServiceNow
Question Time: GenAI for IT | ServiceNow
Question Time: GenAI and the Future of Work | ServiceNow
MSPs and AIOps: How to get the best of both worlds
Innovator Preview: Ivanti Neurons for Patch Intune
Dell Warranty Check: How to do it - And How to Automate it
Continuous Monitoring: A Definitive Guide
How IT Managers and MSPs can drive transformation with Remote Monitoring and Management (RMM)
Innovator Preview: Ivanti Neurons for RBVM, ASOC, Patch Management, & Patch Intune
Understanding RBVM & Application Security Orchestration & Correlation
Best Service Delivery Management Software for 2024
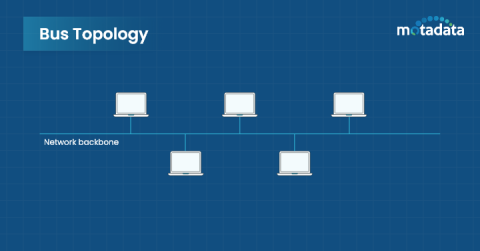
Understanding Network Topology: Types, Best Practices
Innovators Preview: Security Enhancements and Upcoming Events
Innovators Preview: Exploring New Features and Enhancements in UEM
How to successfully implement an inventory management software?
Understanding Software Licensing Models
What's New with Ivanti Neurons/DEX 2024.1
How to Conduct an IT Audit in 2024
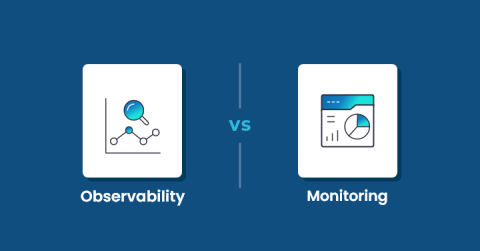
Observability vs. Monitoring: Decoding Key Distinctions
How to Check Lenovo Warranty (And How to Automate it!)
How AI-generated summaries speed IT ticket resolution #shorts
Warranty Management: How to Automate Hardware Warranty Checks
Emerging AI use cases in ITSM Knowledge management, chatbots and self-service
11 Best Incident Management Software in 2024
Hybrid Cloud Monitoring: The Ultimate Guide to Benefits
In the fast-moving tech world, your business faces two main challenges: maintaining control of in-house servers and harnessing the flexibility of cloud computing. It is where “Hybrid cloud monitoring” emerges as a torch bearer, guiding your organization through the complexities of a dual environment. A hybrid cloud monitoring solution functions like the control centre for your business’s digital operations.
Forms in the Velocity Platform: A Guide by Ivanti Wavelink
Modernize your ITSM with the New PagerDuty Application for ServiceNow
We live in an always-on world, where things move fast and break often. Building stronger resilience is critical for operational efficiency and delivering great customer experiences. CIOs have heavily invested in ITSM solutions, but a centralized, queued approach is no longer meeting the needs of modern organizations when it comes to critical, customer-impacting issues.
What are the Latest Asset Management Trends in 2024?
In today's digital age, technology is advancing at an unprecedented pace and the internet has made it possible for everyone to stay connected. This has not only created new opportunities for asset management but has also brought new challenges. In order to maintain compliance and make informed decisions based on accurate data, it is crucial to stay up-to-date with the latest trends in asset management. In this blog, we will explore the latest asset management trends that are shaping the industry.
Enhance Employee Engagement with Parametric Campaigns
In today's digital workplace, IT-employee engagement is crucial for communicating timely information, fixing issues collaboratively, and understanding employees’ experience with technology. At Nexthink, we have met this evolving need with our investments in engagement campaigns. And now, we are pleased to introduce the newest innovation to connect IT and employees: parametric campaigns.
4 GRC Automation Ideas to Protect Your Organization
Creating Conditional Emails Using Forms: A Step-by-Step Guide
4 Practical Tips for ITSM Professionals in 2024
In this time of the year when everyone reflects on their past and sets new goals, we thought it would be valuable to share some tips for ITSM professionals for the upcoming year. We talked to our CTO Ivan Samoylov, and he shared his ideas on what to focus on in 2024.
AIOps in Telecom Industry: Challenges, Benefits, and Use Cases
The telecom industry is rapidly evolving, with network operations becoming increasingly complex. To navigate this complexity, telecom operators are turning to Artificial Intelligence for IT Operations (AIOps) solutions. AIOps combines artificial intelligence, machine learning, and big data analytics to optimize network performance, enhance customer experience, and drive business outcomes.
Emerging use cases in AI for IT
The Future of Compliance: 10 Trends to Look Out For in 2024
What is ITAM? The ABC of IT Asset Management
Applying the 7 Guiding Principles of ITIL 4 to the Service Desk
How AI closes productivity gaps on short-staffed IT teams
Cloud Network Monitoring: Ensuring Visibility in a Distributed World
As businesses transition to the cloud, the need for strategic implementation of Cloud Network Monitoring has become essential. This is because IT managers and CIOs across organizations are looking for robust real-time monitoring, performance optimization, and security vigilance for their distributed network. If you’re also thinking of cloud networking monitoring and want to know more about it in detail, continue reading this article further.