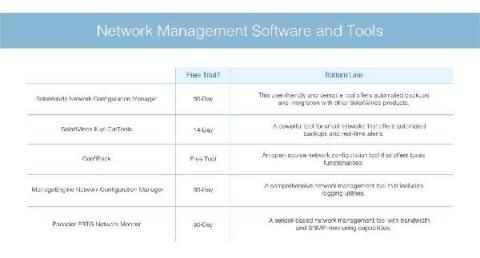
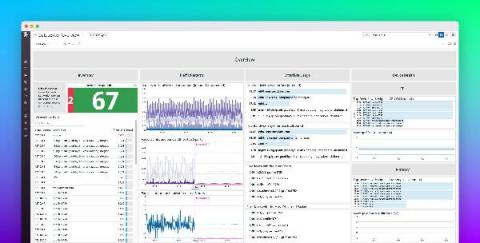
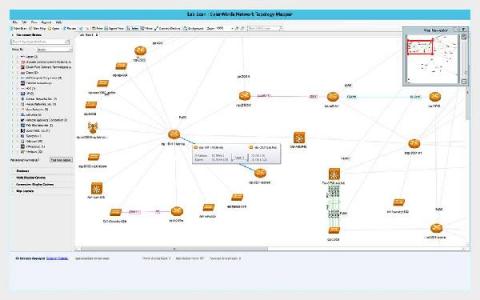
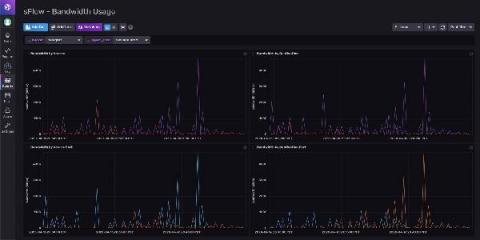
Connect S.P.A. ups its network performance management game with OpManager!
Connect S.P.A. is a European IT company offering services in networking, wireless, security, monitoring, data center, and servers. It has two data centers and nine servers. Before finding OpManager, the IT company was using a network monitoring tool, but it did not offer enough visibility into its network, which made it difficult to troubleshoot and fix recurrent network issues. This led to unpleasant network downtime experiences, especially since the tool Connect S.P.A.