Operations | Monitoring | ITSM | DevOps | Cloud
April 2021
Network Observability for Distributed Services
How to Monitor Zoom Network Performance | Obkio
How To - Monitor Split Tunnel Traffic with Catchpoint
When the world transitioned to a remote workspace, one of the things that most of us figured out quickly was that some applications just don’t work well with corporate VPN. Video and voice applications, like Microsoft Teams, are essential to business operations. I wouldn’t want to add another point of failure that I’d need to troubleshoot if I didn’t have to.
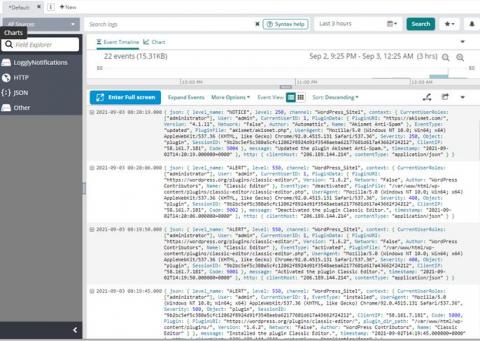
Using Coralogix to Gain Insights From Your FortiGate Logs
FortiGate, a next-generation firewall from IT Cyber Security leaders Fortinet, provides the ultimate threat protection for businesses of all sizes. FortiGate helps you understand what is happening on your network, and informs you about certain network activities, such as the detection of a virus, a visit to an invalid website, an intrusion, a failed login attempt, and myriad others. This post will show you how Coralogix can provide analytics and insights for your FortiGate logs.
A Modern Network Provides a Smooth Evolution to Smart
“Smart” is the buzzword for strategic industries operating in Energy, Utilities, and Transportation. We are also starting to see this “Smart” nomenclature used in local authorities, defense and public services.
Have Your Say in the new Idea Portal
What is 802.1X Authentication?
Pineland Telephone Cooperative Upgrades Communications Network with Ribbon IP Optical Solutions
N-able (Formerly SolarWinds MSP) Announces Integration of N-able N-central with Microsoft Intune
What We Learnt At Collision 2021
Autoscaling with the HAProxy Kubernetes Ingress Controller and KEDA
One of the greatest strengths of containers is the ability to spin more of them up quickly. As the volume of traffic to your application increases, you can create more application containers on the fly to handle it, in almost no time at all. Kubernetes ships with autoscaling baked in, giving you the power to scale out when the system detects an increase in traffic—automatically!
N-central Integration with Microsoft Intune
Five Ways Containerized eSBCs Optimize Teams, Zoom & Other Cloud Communications Deployments
Enterprises are using Unified Communications as a Service (UCaaS) solutions like Microsoft Teams and Zoom, and Contact Center as a Service Solutions (CCaaS) like Five9 and Genesys to improve communications, simplify operations, and accelerate IT agility. As the COVID-19 outbreak clearly demonstrated, UCaaS and CCaaS solutions are ideal for delivering enterprise communications services to remote workers, mobile users, and small/home offices.
Five Ways Containerized eSBCs Optimize Teams, Zoom & Other Cloud Communications Deployments
Enterprises are using Unified Communications as a Service (UCaaS) solutions like Microsoft Teams and Zoom, and Contact Center as a Service Solutions (CCaaS) like Five9 and Genesys to improve communications, simplify operations, and accelerate IT agility. As the COVID-19 outbreak clearly demonstrated, UCaaS and CCaaS solutions are ideal for delivering enterprise communications services to remote workers, mobile users, and small/home offices.
N-able (Formerly SolarWinds MSP) Appoints Mike Adler as Chief Technology and Product Officer
Ribbon's Partner Program Receives 5-Star Rating in the 2021 CRN® Partner Program Guide
HAProxy Reaches Over 2 Million Requests per Second on a Single Arm-based AWS Graviton2 Instance
How a customer turned digital transformation success with Elastic into a partnership opportunity
Our journey with Elastic began with a search for a single monitoring platform service for all kinds of applications and infrastructure across geographies and in the cloud. Like many other organizations who use Elastic, our story does not end there.
How to Find IP Addresses on a Network and Monitoring their Usage
NGINX Ingress Controller Template
We set out with a plan this year to nurture and grow our developer ecosystem. In 2020, we launched our Template Library to empower joint users of LogDNA and our partners to have an out-of-the-box logging experience from every layer of their stack. As the use of these templates has grown, users have told us that they save them time from manually creating Views, Boards, and Screens, and helps them gain insight from their logs much quicker.
We Want Your Ideas (Auvik Idea Portal)
How to Find and Fix IP Address Conflicts
DHCP server monitoring made easy with OpUtils
In today’s complex IT infrastructures, Dynamic Host Configuration Protocol (DHCP) servers play an indispensable role in automating IP allocation and configuration. A DHCP server’s capacity to allocate IPs to the requesting clients in real-time is one of the factors that ensures constant uptime of dynamic networks. However, even though a network’s availability depends on them, DHCP servers are often not closely monitored by IT teams.
N-able (Formerly SolarWinds MSP) Announces Partnership with DNSFilter to Help MSPs Protect Customers from Online Security Threats with Advanced DNS Technology
Why Should My Business Consider Direct Connectivity to Microsoft Azure?
Power Your Consul Service Mesh with HAProxy
Many of you use HashiCorp Consul for service discovery. It makes connecting one backend application or service to another easy: Your Consul servers store a catalog of addresses to all of your services; when an application within the network wants to discover where a service is listening, it asks Consul, which gives it the address.
THWACK Livecast Series - Session 1: Keeping Your ISP Honest and Troubleshooting SaaS Applications
Troubleshooting Firewall Issues in DigitalOcean
Monitoring Nginx web server with Bleemeo
This blog article will cover how to monitor your nginx web server with Bleemeo, what is monitored and graphed by default and how to go further by configuring custom dashboards to have a global overview of your infrastructure.
The SolarWinds 5 Essential IT Tools Pack Overview
It's a Mad, Mad, Mad, Mad Multipath World
Network Firewall Security: Monitoring Firewalls 101
Why Should My Business Consider AWS Direct Connect?
What is an ARP Table?
ThousandEyes Intelligence in AppDynamics Dash Studio Demo
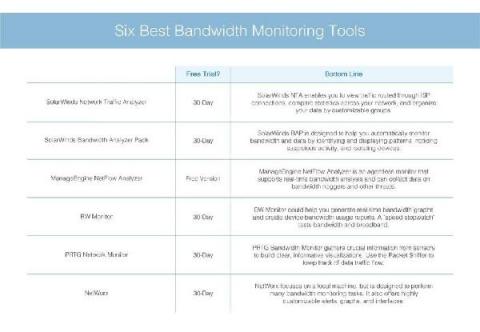
6 Best Bandwidth Monitoring Tools
Troubleshooting Firewall Issues in DigitalOcean
How to Monitor Router Traffic: 6 Router Monitoring Tips
Network Packet Loss Triage Explainer
HAProxy Forwards Over 2 Million HTTP Requests per Second on a Single Arm-based AWS Graviton2 Instance
For the first time, a software load balancer exceeds 2-million RPS on a single Arm instance. A few weeks ago, while I was working on an HAProxy issue related to thread locking contention, I found myself running some tests on a server with an 8-core, 16-thread Intel Xeon W2145 processor that we have in our lab. Although my intention wasn’t to benchmark the proxy, I observed HAProxy reach 1.03 million HTTP requests per second.
9 Best Network Discovery Tools
Enabling Profitable Business Services through OTN Switching
5 Best Network Uptime Monitoring Software
Network Design and Best Practices
SolarWinds Appoints Charles Damerell as Senior Director of UKI Sales
Network Monitoring and Its Best Practices
All networks, no matter how sophisticated, are vulnerable to attack from outsiders. They can also face compromise from poor program integration, outdated software, lagging connections, and insufficient bandwidth. These issues impede the efficiency of your workforce and can frustrate clients who depend on reaching you through reliable communication methods. A technologically advanced network needs constant attention to run at peak efficiency.
Network Performance Monitoring: The Tools and Strategies
In this post, we are going to look at different tools and strategies for Network Performance Monitoring. To follow along with this blog article, make sure to book a demo and sign up for MetricFire's free trial where a lot of our customers are doing network performance monitoring using Hosted Graphite and Prometheus service. These tools are part of MetricFire’s offering.
How Network Monitoring Takes Observability to the Next Level
With expectations around digital experience never higher, organizations should seriously consider implementing a network monitoring solution to support optimal business performance.
Network Integration: Moving from Reactive to Proactive with Mature Processes
Conquering the Next Normal: Monitoring Techniques to Keep Up With the Pace of Change in 2021
Web Server Monitoring Your Application on Nginx with Logz.io
A big topic of interest nowadays is web application monitoring. Application performance monitoring and log analytics are required by businesses of all sizes to ensure their web applications’ smooth operation. If your application serves as the backend for your business processes, it is critical for your organization. You need to know, in real-time, when and why it breaks. To answer these questions, we will use Logz.io products to monitor a simple web application served by Nginx.
The Unprecedented Transformation of IT Goals in 2020
Resolve Network and VPN Performance Problems Faster with Endpoint Monitoring
IT professionals are now adapting to remote environments and learning to manage a distributed, homebound workforce. In recent conversations with IT pros, many have cited that connectivity/VPN and home network issues are their top challenges but they lack the visibility to diagnose and troubleshoot these problems. Catchpoint for employee experience monitoring gives IT teams what they need: visibility from remote users’ devices to any business-critical application across any network.