Operations | Monitoring | ITSM | DevOps | Cloud
May 2022
Announcing HAProxy 2.6
HAProxy 2.6 is now available! As always, the community behind HAProxy made it possible to bring the enhancements in this release. Whether developing new functionality, fixing issues, writing documentation, QA testing, hosting CI environments, or submitting bug reports, members of our community continue to drive the project forward. If you’d like to join the effort, you can find us on GitHub, Slack, Discourse, and the HAProxy mailing list.
What is RMM? The Importance of Network Management
6 must-have features in network configuration management
Network configuration management is a function that comprises assortment, monitoring and storage of information about every component that forms a network. The true purpose of such a solution is to come alive in time of any eventuality; it could be the need to update, upgrade, recover or could even be disaster management. The solution will provide all pertinent information at the hands of the IT operations team, enabling them to decide the course of action going forward.
3 Cost Considerations For Your Multi-Cloud Environment
The 5 Levels of MSP Operational Maturity
How to Troubleshoot Routing Problems
N-able Unveils N-hanced Services to Help Partners Accelerate Time to Value
Introducing Megaport PartnerVantage
Network Fault Monitoring vs. Network Performance Monitoring
Every IT administrator knows that users typically complain of two things: the network doesn’t work or it’s slow. When your network isn't working, it’s usually because something is down and we can rely on Network Fault Monitoring tools to notify us. But where do we start when users complain of poor performance? And what tools are available to help us? In these situations, Network Performance Monitoring tools might be just what you need.
Charting a Course to Clearer Visibility | Discovering Observability: Session 1
How to Prepare for Peering Partner Business Review
What is ITIL? IT Infrastructure Library Guide
Blueline Madagascar Selects Ribbon's Optical Transport Solution to Deliver Increased Capacity across its Communications Network
NGINX Logging Configuration: How to View and Analyze Access and Error Logs
NGINX is one of the most widely used reverse proxy servers, web servers, and load balancers. It has capabilities like TLS offloading, can do health checks for backends, and offers support for HTTP2, gRPC, WebSocket, and most TCP-based protocols. When running a tool like NGINX, which generally sits in front of your applications, it’s important to understand how to debug issues. And because you need to see the logs, you have to understand the different NGINX logging mechanisms.
A Layman's Guide To HTTP/2
HTTP stands for Hypertext Transfer Protocol and is the backbone of the World Wide Web. HTTP/2 is the second major version of the HTTP protocol, which offers a performance improvement over its prototype. The new protocol has been in development for a long time, with the first draft published in 2012 and it was finalized in 2015. In recent times, HTTP is the obligation that boards almost all of the networks.
Round-Trip Time (RTT) - An Overview
A notable tool that renders the fortune of a web is Round Trip Time, which is also known as Round Delay Time. The time taken for a network request for a data packet and the flourishing of that data is the round trip time. The duration of RTT is calculated in milliseconds. RTT can be diagnosed and prompted by pinging a specific address. The time takes for an internet request to hit a destination and to lapse back to the primary resource.
From Baud to Awed: The History of the Modem
5 Executive Blindspots Around Hybrid IT Observability
Network topology software for your enterprise networks
Top Things To Consider When Connecting IoT Devices To The Cloud
Winning Over the Skeptics: How SD-WAN Is Transforming Government Networks
Using Brotli Compression in NGINX
Use the Proxy Protocol to Preserve a Client's IP Address
In this blog post, you’ll learn how the Proxy Protocol preserves a client’s IP address when that client’s connection passes through a proxy. You will also find resources for how to integrate the protocol into your own proxy or web server software. What is the Proxy Protocol? It is a network protocol for preserving a client’s IP address when the client’s TCP connection passes through a proxy.
Application connectivity in a hybrid cloud
A successful hybrid cloud architecture is one that addresses how to build, deploy, manage and connect a hybrid mix of applications across a hybrid infrastructure environment. These applications will span multiple infrastructure footprints—across cloud providers and customer datacenters and multiple Kubernetes clusters, as well as systems that run on vendor management systems (VMSs), bare metal and edge environments.
The 6 Fundamental Steps in a Network Monitoring Process
Network monitoring is vital for operating an IT environment at optimal performance. As a result, organizations can improve operational efficiencies with a well-managed network while proactively maintaining a secure network. While remote work has made the network monitoring process more challenging, new cloud-based tools have extended IT teams' reach into home and remote offices to ensure employees are secure and productive.
Top 5 Reasons for "Why AppNeta?"
AppNeta by Broadcom Software is a SaaS platform that enables large enterprises to gain visibility into their business-critical applications as experienced from remote offices and to understand how the networks that drive them operate. Because of our network focus we often get compared to traditional monitoring solutions, but with a quick overview it should be easy to explain to others in your organization how we differentiate.
How AppNeta Drives Business Value
While network and application performance grow increasingly business critical, IT’s ability to track and control service levels continues to be diminished. The shift to hybrid and remote work means users are now highly reliant upon public internet connections, which require additional security at the network edge. Plus, the majority of apps, internal or external, are now cloud hosted.
Infovista enables operators to test user experience of OTT voice, video and interactive 5G apps and services
VLAN monitoring in OpManager
A local area network, what we know more commonly as a LAN, is a network that comprises devices based out of the same geographic location, enabling communication between them. The virtual counterpart of a LAN is a virtual LAN, or VLAN. A VLAN augments a LAN, offering flexibility in making changes, higher scalability, and better security.
California's Quik Pick Express benefits from OpManager
California trucking company, Quik Pick Express, improves overall IT network performance using ManageEngine OpManager, efficiently solving downtime and troubleshooting issues and saving $10,000 annually.
CIT LAO, a prominent civil aviation agency, deploys OpManager to combat network faults
CIT LAO utilizes OpManager to optimize network performance and troubleshoot network issues before end users are impacted, saving time and effort.
New Report Finds Digital Product Management Adoption Is Accelerating to Meet Business Objectives
2022 Unified NetOps Explainer Video
Monitoring Azure and Your Entire Hybrid Infrastructure with DX UIM
While you often read about the move to “the cloud,” the reality is that most organizations aren’t moving to a single cloud, but multiple cloud environments from multiple providers. There can be a range of reasons for companies to use cloud services from more than one provider today.
Digitalization Is Key To Competing In This New Era Of Customer Experience
Customer experience (CX) is becoming an increasingly strategic part of any company’s brand as businesses become more customer-centric. And thanks to technologies that give customers more options than ever, right at their fingertips, consumers expect a flawless CX, anytime and anywhere, regardless of medium. In other words, customer retention and satisfaction is intertwined with CX.
Azure Monitoring with DX Unified Infrastructure Management
Broadband for Today, Scalability for Tomorrow!
OSL and BSO unveil strategic partnership to bolster connectivity for institutional exchange clients
Migrating to Teams Voice: Practical Steps
Financial Networking From the Edge
Top 7 Key Features Your Network Monitoring Software Should Have
Node to Node Monitoring w/ Catchpoint
How New Relic uses Kentik for network observability
New Relic is known for empowering the world’s leading engineering teams to deliver great software performance and reliability. And the network that delivers that service to New Relic’s users plays a critical role. Hiccups in the performance of the network between New Relic’s mission-critical service and their users can create a cascade of problems.
Enable Sticky Sessions in HAProxy
HyperText Transfer Protocol (HTTP), the protocol that defines the language browsers use to communicate with web servers, is stateless, meaning that after you make a web request and a server sends back a response, no memory of that interaction remains. To make anything more sophisticated than a static web page work, websites need other ways to remember previous interactions with users.
Securing SD-WAN in a Cloudy World
Colt Deploys Ribbon's Microsoft-Certified Session Border Controllers to Power its New Intelligent Communications Offering
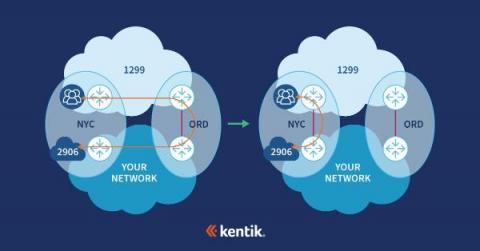
How to prepare for a peering-partner business review
Peering is more than just setting up sessions with any AS that will accept one. Peering can involve long-term relationships that require reviews and joint-planning to grow synergy. A critical milestone in any peering relationship is the business review – and when it comes to business reviews, it’s all about preparation. So where to start?
DNS Performance Testing - May 2022 North America
Whether you are looking to research, switch, or add additional DNS providers for redundancy, it's important to consider several factors and ask the right questions that will determine the provider that best suits your organization's needs.
Taking The Power Of Automation To The Edge
Supercharge Your SBC Call Detail Records
As Teams Phone becomes the norm in the Enterprise space, managing the quality of service delivery and user satisfaction, whether it’s cloud or connected to the PSTN, is mission critical. Teams PSTN calls are used for just about every type of meeting as well as for Contact Centers, Customer service, town halls and client pitches. Because of this ubiquitous usage, Enterprise IT needs analytics to understand how this service is performing for users and when problems are occurring.
Updates Paused: How are MSPs Navigating Today's Supply Chain Issues?
Automation and transformation in IT infrastructure with Jordan Lowe
Experience-Driven NetOps from Broadcom Software
Kubernetes Networking: How to monitor Kubernetes using synthetic testing
AWS NAT Gateway Pricing: How To Reduce Your Costs In 5 Steps
10 steps to modernize network monitoring
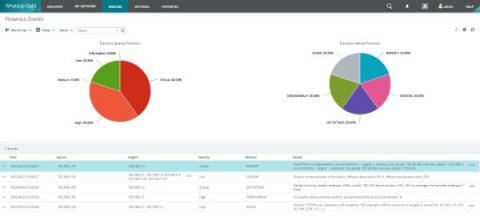
Flowmon and WhatsUp Gold: Automatic Threat Detection Through Single Pane of Glass
Network Detection & Response (NDR) is a key element that provides an additional level of security across the company wide network through detection of threats that bypass traditional security measures and materialize in the company’s digital environment. Progress Flowmon ADS (Anomaly Detection System) is a typical representative of an NDR system that combines various detection techniques to ensure that malicious activity is recognized and flagged as a security incident.
Minimize application complexity with AppDynamics and Cisco Intersight
See how AppDynamics and Cisco Intersight manage infrastructure resources to enable premium user experiences.
Using synthetics to get the big picture
Nobody actually cares about the network. Provocative words coming from a network visibility company, you might be thinking. However, consider what you’re doing right now. You’re reading a blog on a website, maybe clicking around other tabs, possibly streaming some music, and likely keeping an eye on your work chat. These are all applications, and that’s what we all truly care about, not the plumbing that delivers them.
The value of performance mesh testing for ISPs, CDNs, telcos and cloud service providers
Subnet Masking Cheat Sheet: A Beginner's Guide to Subnetting
CDN Provider Performance Monitoring: Best CDNs in Japan
This blog continues our best CDN series. Today we will be analyzing CDN performance and uptime in Japan over the last seven and 30 days. Tip: Are you new to CDNs? Visit our What is a CDN resource to learn more.
Compliance And The Cloud
Looming 2022 (and Beyond) Network Security Threats
Every year hackers grow in numbers, aggressiveness, organization, and sophistication. And every year there are new attack types and new areas of IT infrastructure that cybercriminals target. 2022 is no different. We are about a third of the way in already and IT pros and security specialists already have their hands full with new attacks and new issues.
How to Import/Export Orion Custom Query Widgets
The MSP Provider's Guide to Getting Hired
WiFi Observability to Boost Employee Digital Experience
We are all moving towards a digital workplace - or a hybrid work scenario. Whatever be the case, you can expect end-users to call and complain about a poor WiFi experience. That's because network monitoring needs to be done from their standpoint, not from the enterprise end. And without the correct WiFi observability data, it's challenging to narrow down the root cause of the problem affecting remote employees. And those problems - poor WiFi performance leading to poor digital experience - can be pervasive and persistent.