Operations | Monitoring | ITSM | DevOps | Cloud
September 2023
Defining Your Cloud Core Migration Strategy - Fail to Prepare, Prepare to Fail
The Evolution of Data Center Networking for AI Workloads
Traditional data center networking can’t meet the needs of today’s AI workload communication. We need a different networking paradigm to meet these new challenges. In this blog post, learn about the technical changes happening in data center networking from the silicon to the hardware to the cables in between.
The Power of SNMP Polling: Monitoring Your Network Like a Pro
Streamlining network efficiency: Unveiling the power of ManageEngine Network Configuration Manager
N-able Brings Partner Conference Empower 2024 to Frisco
How to Connect Your AWS and Microsoft Azure Environments: A Complete Guide
We explain why you should connect the leading two cloud providers, the options available, and which one is right for your business.
State of the Internet: Monitoring SaaS Application Performance
Quick Tip: Virtual Monitoring in WhatsUp Gold
The Power of Network Uptime Monitoring: Proactive vs. Reactive
New DX UIM Release: Start Monitoring New Linux Distributions on Day 1
From DX UIM 20.4 CU4 onward (that is, releases that have robot version 9.36 or above), robots automatically support Linux versions with newer GNU C Library (commonly known as “glibc”) versions. Prior to CU4, DX UIM robots needed certification and a release to provide support or compatibility with newer Linux operating systems that have a higher glibc version.
Enhancing Network Reliability: How to Measure, Test & Improve It
Augmenting behavior-based network detection with signature-based methods
Network detection tools utilize one of two prominent approaches for threat detection: AI-driven behavior-based methods capable of identifying early indicators of compromise, and signature-based ones, which flag known attacks and common CVEs. While these systems operate on distinct principles, their combination forms more robust defense mechanism, helps to consolidate tools, provides richer threat context and improves compliance.
How to enable signature-based detection in Flowmon Probe and Flowmon ADS
In this article, we explained the benefits of combining signature-based detection by Suricata IDS with behavior-based detection by Flowmon ADS. Now, let’s talk about how to enable this feature using Flowmon Probe and Flowmon ADS.
What Is an IP Address Management Service and Why Might You Need It?
Adding a CDN to a load balancer (for a much faster website)
Grafana 10.1: Introducing the geomap network layer
How to Configure a Linux Firewall: The Ultimate Guide
A firewall stands as a digital gatekeeper, meticulously sifting through network traffic and deciding what may pass. This protective shield, fundamental to cybersecurity, is integral in the Linux world. The Linux kernel itself is effectively a de facto packet switching firewall, crafted as it is around the principles of packet filtering at the most fundamental operating system level, thus exemplifying the pivotal role of firewalls in system security.
ICMP Required for Traceroute and Network Diagnostics
As previously detailed on the Exoprise blog, the ICMP (Internet Control Message Protocol) is crucial for troubleshooting, monitoring, and optimizing network performance in today’s Internet-connected world. Despite historical security concerns, disabling ICMP is unnecessary and hampers network troubleshooting efforts. Modern firewalls can effectively manage the security risks associated with ICMP.
Cloud Cost Optimization Best Practices
Businesses are rapidly transitioning to the cloud, making effective cloud cost management vital. This article discusses best practices that you can use to help reduce cloud costs.
Take Your Service Management Beyond IT
How AI is Changing Modern Networking
SolarWinds Continues Ongoing Business Evolution With New and Upgraded Service Management and Database Observability Solutions
What's Going on in There? What is Server Monitoring?
X-ray machines are one of the most sophisticated tools in the medical field. Capable of creating images of someone’s fractured arm, x-rays enable medical professionals to see what is going on in a patient’s most vital areas. In the IT world, server monitoring has a similar function.
LogicMonitor Excels in G2 Fall 2023 Network Monitoring Report
How to Troubleshoot Internet Connectivity Issues for IT Pros
Best Practices for TDM Masking with Docker
IT Pro Day Plays of the Week
Using Synthetic Testing for Better Network Observability with Kentik
Embedding DX Dashboards in APM and DX Operational Intelligence
As connected as the world is today, it can feel quite disconnected, especially in IT. Individual teams use various tools, each with specialized interfaces and dedicated dashboards, to present or interpret data each the specific functional team needs.
See How Kubernetes Traffic Routes Through Data Center, Cloud, and Internet with Kentik Kube
Solving Faster in the Cloud Hybrid Infrastructure Observability with Kentik
Your Comprehensive Guide to HAProxy Protocol Support
Internet protocols are the lifeblood of internet communication, powering important connections between servers, clients, and networking devices. These rules and standards also determine how data traverses the web. Without these protocols, internet traffic as we know it would be severely fragmented or even grind to a screeching halt. And without evolving protocol development, the web couldn’t properly support the applications driving massive traffic volumes worldwide (or vice versa).
Network Observability Across the Enterprise
Container Network Observability
Data-driven Network Observability
Is your cloud provider executing network maintenance? Yes, yes they are.
What's New at Kentik in 2023
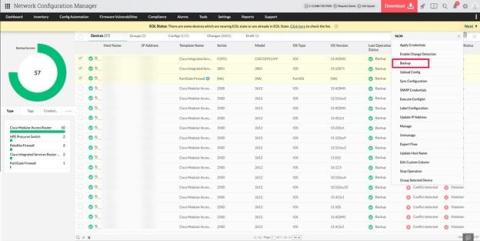
Brocade switch configuration management with Network Configuration Manager
Brocade network switches encompass a variety of switch models that cater to diverse networking needs. In today’s intricate networking landscape, manually handling these switches with varying configurations and commands within a large network infrastructure can be a daunting task. This complexity often leads to human errors such as misconfigurations. How can you optimize your network environment effectively when utilizing a variety of Brocade switches and eliminate the need for manual management?
Revolutionize your network performance with OpManager's versatile network management tool
As networks become more highly dynamic, managing an entire network efficiently is not an easy task. When it comes to network monitoring, all you need to figure out is the type of network devices and the specific metrics you need to monitor. But when it comes to network management, there’s more to be taken into account, from network security, bandwidth hogs, change management, and policy management to performance optimization.
Network Monitoring 101: How To Monitor Networks Effectively
Ivanti and Catchpoint Partner to Proactively Address Remote Connectivity Issues and Enhance Workforce Productivity
IT Trends Report 2023: Observability advances automation and empowers innovation, yet adoption still in early stages
Looking back at 15 Years of Catchpoint and Internet Performance History
Fifteen years ago, the Internet was a very different place. It operated on a very different scale, had different market leaders and it faced different technical challenges. What has not changed, however, is the need for the best – indeed ever higher - performance and resilience. We founded Catchpoint in September 2008 (amid terrible economic conditions) with the desire to make the Internet better. Not exactly the greatest year to launch a startup.
Mastering LAN Monitoring: How to Improve LAN Network Performance
Too Many Alarms? Take Advantage of Custom Situations
As IT infrastructures become increasingly complex to monitor and manage –with new compelling technologies such as virtual machines, software-defined networks and containers overlaid onto existing technology stacks– IT operations teams face the additional challenge of nearly unmanageable ticket volumes. Ticket prioritization, correlation, redundancies and sheer speed of ticket generation become problems in and of themselves.
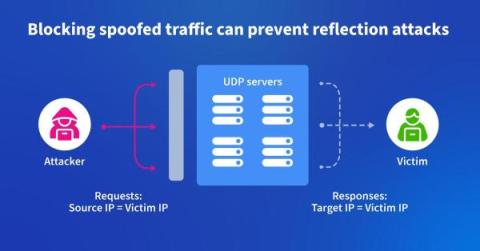
Using Kentik to Fight DDoS at the Source
In this blog post, we describe how one backbone service provider uses Kentik to identify and root out spoofed traffic used to launch DDoS attacks. It’s a “moral responsibility,” says their chief architect.
Connect Over Coffee | Cross-Cloud with Megaport Cloud Router (MCR)
How to Centralize and Automate Your Network Device Configuration Management
VPN Split Tunneling: A Guide for IT Pros
Monitoring TLS Network Traffic for Non-FIPS Compliant Cipher Suites
FIPS compliant cipher suites hold the U.S. government's seal of approval, guaranteeing their suitability for federal systems. On the other hand, non-FIPS compliant cipher suites may present security vulnerabilities due to outdated cryptographic algorithms and potential lack of perfect forward secrecy. As a result, it becomes paramount to monitor TLS network traffic for non-FIPS compliant cipher suites.
Take Your Pick! The Best Server Monitoring Tools on the Market
IT professionals are always presented with myriad solutions when seeking additional software for their network infrastructure. When it comes to server monitoring solutions, there are multiple options available. After all, every organization has its own needs, individual infrastructure and software requirements. With that in mind, the following list is a guide to help IT professionals select what they believe may be the best possible server monitoring solution for their organization.
Box and Kentik: A Google Cloud Migration Success Story
Tools and partners can make or break the cloud migration process. Read how Box used Kentik to make their Google Cloud migration successful.
The Importance of ICMP in Today's Digital Landscape
In today’s interconnected world, where network performance is crucial for business operations, understanding the significance of ICMP (Internet Control Message Protocol) becomes paramount. Today’s post sheds some light on the critical role of ICMP and why it should not be disabled despite legacy security concerns. By implementing proper security measures, businesses can leverage the benefits of ICMP while mitigating potential risks.
Comparing Your Multicloud Connectivity Options
As multicloud adoption surges, so too do the choices for connecting to your clouds. We break down the key solutions and their benefits.
5 Best Network Vulnerability Scanners
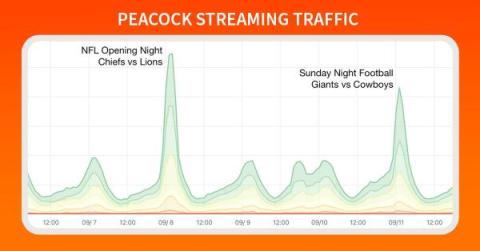
Anatomy of an OTT Traffic Surge: NFL Kickoff on Peacock
Football is officially back, and Doug Madory is here to show you exactly how well the NFL’s streaming traffic was delivered.
VPN vs. SD-WAN tunnels
How improved network performance is a key part of Web 3.0 delivery
What is Network Response Time & How to Monitor It
What Is Storage Area Network (SAN)? Benefits & Implementation
In the ever-evolving landscape of technology, data has become the lifeblood of businesses. The exponential growth of data has spurred the development of intricate data storage systems to accommodate these volumes efficiently. One such vital player in the realm of data storage is the Storage Area Network (SAN). SANs are paramount in managing and processing large data volumes, ensuring seamless accessibility, scalability, and high availability.
Top tips: Five ways you can reduce unplanned network downtime
Top tips is a weekly column where we highlight what’s trending in the tech world today and list out ways to explore these trends. This week we’re looking at five ways your business can minimize unplanned network downtime. Network downtime is the bane of the IT service provider. It disrupts not only internal operations, but can greatly inconvenience your customer who relies on the uninterrupted access to and the full functioning of your product or service.
Should You Reload or Restart HAProxy?
Managing your load balancer instances is important while using HAProxy. You might encounter errors, need to apply configurations, or periodically upgrade HAProxy to a newer version (to name a few examples). As a result, reloading or restarting HAProxy is often the secret ingredient to restoring intended functionality. Whether you’re relatively inexperienced with HAProxy or you’re a grizzled veteran, understanding which method is best in a given situation is crucial.
A Comprehensive Guide to Network Device Monitoring
What is a virtual private cloud in AWS?
Understanding Kubernetes Network Policies
Kubernetes has emerged as the gold standard in container orchestration. As with any intricate system, there are many nuances and challenges associated with Kubernetes. Understanding how networking works, especially regarding network policies, is crucial for your containerized applications' security, functionality, and efficiency. Let’s demystify the world of Kubernetes network policies.
Mastering Network Monitoring: Your Guide to Uninterrupted Excellence
In the age of digital dominance, where every click and connection propels businesses forward, the lifeline of success lies in the seamless operation of computer networks. Imagine this: your website’s pulse is in perfect sync, applications running smoothly, and customers navigating without a second’s delay. This is where the art of network monitoring steps in, weaving the invisible threads that ensure unparalleled performance and uninterrupted excellence.
Microsoft Dynamics Monitoring: CRM Performance Optimization
Megaport ONE Beta Is Available Now. Here's How You Can Use It
Our feature-rich network, compute, and orchestration platform is here. Find out how it can simplify and future-proof your network.
How to Monitor Multi-layer Huawei Switch with MetricFire
Monitoring your network infrastructure plays a pivotal role in identifying potential bottlenecks, optimizing performance, and ensuring seamless operations. By implementing a comprehensive monitoring solution like MetricFire, you gain access to a wide range of features and functionalities designed to simplify the process of monitoring and managing your Huawei switches.