Operations | Monitoring | ITSM | DevOps | Cloud
August 2021
Secure your clients and prevent churn with a canary
Many people are familiar with the stories of coal miners using canaries to detect carbon monoxide and other toxic gases as a warning system for when they should evacuate. Even though cybersecurity is far removed from coal mining, it has an equivalent “canary in the coal mine” that takes the form of indicators of compromise, or IoC for short. So why should an MSP be concerned with looking for IoCs?
Calico integration with WireGuard using kOps
It has been a while since I have been excited to write about encrypted tunnels. It might be the sheer pain of troubleshooting old technologies, or countless hours of falling down the rabbit hole of a project’s source code, that always motivated me to pursue a better alternative (without much luck). However, I believe luck is finally on my side.
PagerDuty Integration Spotlight: Teleport
Automating Identity Lifecycle Management
The identification of every user making a request to a given system is vital to ensuring that action is only taken by, and information only returned to, those who need it. This happens in two steps: first, the requester is identified (authenticated), and then that identity is used to determine which parts of the application they are allowed to access.
CFEngine: The Agent Is In 4 - CFEngine Build System (CFBS)
What Is DNS Blocking, and What Should You Know about DNS Security?
In the workplace, certain web pages can be a distraction for employee productivity—or worse, a disruption. If you’re a managed services provider (MSP), your customers may be interested in finding a way to control the types of websites their employees can access during the workday. One viable option for them to utilize is a DNS block to restrict access to certain web addresses on a given server. This article will help you understand what DNS block is, who uses it, and how it works.
Securing VMware Tanzu Mission Control with Access Policies
If you haven’t had a chance to check out VMware Tanzu Mission Control, you’re missing out on one of the greatest tools available to manage Kubernetes. However, it’s not just for managing one cluster; rather, it delivers “fleet-wide” management with a focus on policy. Policy management is powerful because it enables us to, for example, limit access to certain users or prohibit pulls from specific container registries.
Build an Automation-First Security Culture
When you think about how to automate processes within the IT industry, your mind probably goes first to tools. After all, the past decade has witnessed an explosion of tools from across the industry that promise to make it easy to automate virtually every aspect of IT operations — from low-code development solutions that automate coding, to release automation tools for applications, to automated monitoring and security platforms.
SpringOne Interview with Styra
eBPF: When (and when not) to use it
Extended Berkeley Packet Filter (eBPF) is a relatively new feature for Linux kernels that has many DevOps, SREs, and engineers excited. But is it a one-stop shop solution for all of your Linux kernel needs? Let’s take a look at what eBPF does well, and how it stacks up against standard Linux iptables.
21 basic computer security tips
The Internet is a tool that, without a doubt, offers a great amount of positive aspects in the daily life of our society, like instant communication, easy access to information… among many other benefits. But also it has negative aspects, and one of the big ones is cyberattacks. That is why we give you today 21 computer security tips for beginners!
Maintaining Internet Privacy for Your Business
Team Spotlight
The #LifeatTorq Team Spotlight is a Q&A series dedicated to the talented and generally kick-ass team that form the foundation of our growing company. Today we are spotlighting Kostya Ostrovsky , a Software Architect at Torq based in our Tel Aviv office. Kostya is one of the first employees at Torq.
Node.js Security and Observability using Lightrun & Snyk
As developers, we spend a lot of time in our IDEs writing new code, refactoring code, adding tests, fixing bugs and more. And in recent years, IDEs have become powerful tools, helping us developers with anything from interacting with HTTP requests to generally boosting our productivity. So you have to ask — what if we could also prevent security issues in our code before we ship it?
A Year of Supply Chain Attacks: How to Protect Your SDLC
How to detect security threats in your systems' Linux processes
Almost all tasks within a Linux system, whether it’s an application, system daemon, or certain types of user activity, are executed by one or more processes . This means that monitoring processes is key to detecting potentially malicious activity in your systems, such as the creation of unexpected web shells or other utilities.
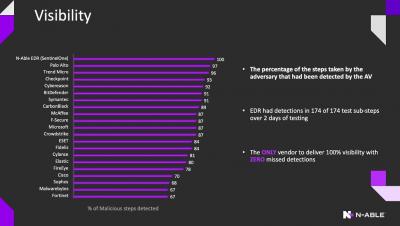
Cool things we do: N-Able EDR - MITRE Assessment Results
kOps adds support for Calico's eBPF data plane
Kubernetes operations (kOps) is one of the official Kubernetes (K8s) projects. The kOps project allows for rapid deployment of production-grade K8s clusters in multiple cloud platforms. By leveraging yaml manifests, kOps delivers a familiar experience to users who have worked with kubectl. Similar to K8s clusters in popular cloud platforms, kOps helps set up self-managed clusters to easily deliver high availability.
Resilient Infrastructure for a Secure Future
Managing Secrets in the Browser in InfluxDB Cloud
Directly embedding passwords and API keys into the code you write is a bad practice. Of course, everyone knows this, but I’ll be the first to admit that it still happens now and then. In the world of source control and shared codebases, leaking a password can be a huge problem that costs your team time and money. Of course, today many companies leverage a secrets management system to lower the probability of something like this happening.
How VMware Tanzu SaaS Products Handle Data Privacy and Security
Companies today are adopting software as a service (SaaS) at a rapid pace. There are many factors contributing to this trend, including: Many large enterprises, particularly in banking and financial services, have been hesitant to adopt SaaS because it challenges existing risk management models already in place for software.
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly.
Adapting to New Federal Regulations on Cybersecurity and Log Management
The Biden administration signed an executive order recently to regulate security practices among federal agencies and establishments. The decision modernizes and improves government networks in pursuit of fool-proof federal cyber defense. This comes in the wake of a series of malicious cyberattacks that targeted both public and private entities in the past year. In the largest breach in US history, SolarWinds
7 Ways To Amp Up Website Security Without Ditching Great UX Design
Technology has paved the way for businesses to reach out to more customers and clients. One of the most effective ways to reach more people is through the Internet, by creating a great website. Nowadays, businesses with websites have a name and face in the online world. However, as technology advances, so do security risks. If hackers get into a website, they can steal sensitive data – say, customer information (i.e., payment methods, addresses, etc.).
Highlights from Black Hat USA 2021
Black Hat USA is one of the industry’s oldest and most well-established security events. Last year, the conference was held virtually for the first time in its history. This year’s conference brought together the best of both worlds, with a hybrid event that was held virtually and in person in Las Vegas. Historically, Black Hat has seen about 20,000 attendees at its in-person conference.
How to protect your secrets with Spectral and JFrog Pipelines
How to Effectively Prepare for a HIPAA Compliance Audit
The Department of Health and Human Services’ Office for Civil Rights (OCR) conducts periodic audits to verify that covered entities (CEs) and their business associates (BAs) are complying with HIPAA regulations. This article will discuss the steps organizations can take to ensure they pass a HIPAA compliance audit by having the proper data privacy and security measures in place for protected health information (PHI) and electronically protected health information (ePHI).
The CFEngine Build System - cfbs (Developer Demo)
5 Security Automation Examples for Non-Developers
If you’re a developer who lives and breathes code all day, you probably don’t mind having to write complex configuration files to set up an automation tool or configure a management policy. But the fact is that many of the stakeholders who stand to benefit from security automation are not developers.
The Compliance Bone Connected to the Security Bone: Sharing Accountability in IT, Risk, and Compliance
Throughout my career within the compliance and security space, I’ve seen the practice of proactively managing digital risk move from a nice-to-have to a must-have for enterprise organizations. And over the last 5 years, things have shifted drastically. Personally, it reminds me of the classic “Dry Bones” nursery rhyme song that my son loves so much which points out how all the different bones are connected to make one body.
Cloning git repos and creating systemd services with CFEngine
Using modules, you can add custom promise types to CFEngine, to manage new resources. In this blog post, I’d like to introduce some of the first official modules, namely git and systemd promise types. They were both written by Fabio Tranchitella, who normally works on our other product, Mender.io. He decided to learn some CFEngine and within a couple of weeks he’s contributed 3 modules, showing just how easy it is to implement new promise types. Thanks, Fabio!
August/2021 - HAProxy 2.0+ HTTP/2 Vulnerabilities Fixed
If you are using HAProxy 2.0 or newer, it is important that you update to the latest version. A vulnerability was found that makes it possible to abuse the HTTP/2 parser, allowing an attacker to prepend hostnames to a request, append top-level domains to an existing domain, and inject invalid characters through the :method pseudo-header.
Using Calico with Kubespray
In the Kubernetes ecosystem there are a variety of ways for you to provision your cluster, and which one you choose generally depends on how well it integrates with your existing knowledge or your organization’s established tools. Kubespray is a tool built using Ansible playbooks, inventories, and variable files—and also includes supplemental tooling such as Terraform examples for provisioning infrastructure.
How Sportsbet enhanced data security with automation
At Sportsbet, an Australian online betting company with more than 1.25 million customers, one thing we’re not willing to take a gamble on is customer security. That means having strict identity and access management protocols in place to protect customer data and get better visibility into whom our employees are and what they have access to.
Optional arguments with getopt_long(3)
I recently had a minor task involving changing an option - on one of our command line tools - from taking a required argument, to taking an optional argument. This should be easy they said; just change the respective option struct to take an optional argument, add a colon to the optstring, and get on with your life. Well, it proved to be easier said than done. My initial expectation was that a solution similar to the one below should just work. And it does work, just not in the way I expected.
Open Source Robotics Challenges - Planning for Security
Open Source Robotics Challenges is a series of blogs that will share guidelines and advice for open source companies to overcome market barriers. We will touch on topics regularly raised by companies in our open source community such as security awareness, prototyping strategies, safety architecture, adoption and more.
Connecting Your Data with Tanium and LogStream
Are You Spending Enough on Cybersecurity?
Cybercriminals do not discriminate against the organization, people or industry they target. These actors look to exploit vulnerabilities in resources to intercept valuable data from small and medium-sized businesses (SMBs). Cyberattacks are inevitable, and organizations must have the right controls and information security systems to mitigate the impact of an attack.
Humans Can be Hacked. So Stop Using Passwords, Already!
Humans are the weakest link in the cybersecurity chain. Where have you heard that before? Humans can be hacked! That too? Yes, I am also one of those weak links in the constant battle against malicious cyber criminals and it can be attributed to just being lazy. It’s human nature and we can easily be socially engineered into giving up our precious online user credentials to the bad guys.
5 Automated Anti-Phishing Protection Techniques
In an age when attackers create over a million phishing sites each month, and phishing serves as a beachhead for 95 percent of all attacks against enterprise networks, how can businesses respond? Part of the answer lies in educating users to recognize and report phishing, of course. But user education only goes so far – particularly because the same statistics cited above show that, on average, only 3 percent of users will report phishing emails.
The number one business bad habit MSPs need to stop doing immediately
The N-able Head Security Nerd, Lewis Pope, just published a blog outlining the top 25 cybersecurity bad practices demonstrated by MSPs today. To accompany his post, I wanted to add one more risky bad habit to his list. It’s something I commonly see being practiced by too many MSPs from a business perspective—allowing a customer’s budget to dictate what a cybersecurity offering should look like.
25 cybersecurity bad practices: more than just bad habits
The CISA (Cybersecurity & Infrastructure Security Agency) recently started an initiative to create a catalogue of exceptionally risky cybersecurity bad practices. While this will be a welcome and very useful tool once it is complete, only two practices are currently listed. Since cybersecurity and business decisions can be time-sensitive, we wanted to expand on the CISA’s list.
How to Schedule Patching for Security Event Manager
Interview with Cybersecurity Specialist Mark Kerzner
For the newest instalment in our series of interviews asking leading technology specialists about their achievements in their field, we’ve welcomed Mark Kerzner, software developer and thought leader in cybersecurity training who is also the VP at training solutions company, Elephant Scale. His company has taught tens of thousands of students at dozens of leading companies. Elephant Scale started by publishing a book called ‘Hadoop Illuminated‘.
How we keep N-central updated and secure
Following the security issues in the MSP market over the past 24 months, our customers, who are understandably concerned, have been asking what we do to keep the N-central® appliance (hosted or on-premises) updated and secure for them. I will do my best in this short article to outline how our engineering team keeps up with security. Please note this is valid as of the time of writing, but can change at any point.
Applied AI for fraud prevention and detection
Securing AWS IAM with Sysdig Secure
Last year’s IDC’s Cloud Security Survey found that nearly 80 percent of companies polled have suffered at least one cloud data breach in the past 18 months.
Kubernetes security issues: An examination of major attacks
In a never-ending game of cat and mouse, threat actors are exploiting, controlling and maintaining persistent access in compromised cloud infrastructure. While cloud practitioners are armed with best-in-class knowledge, support, and security practices, it is statistically impossible to have a common security posture for all cloud instances worldwide. Attackers know this, and use it to their advantage. By applying evolved tactics, techniques and procedures (TTPs), attackers are exploiting edge cases.
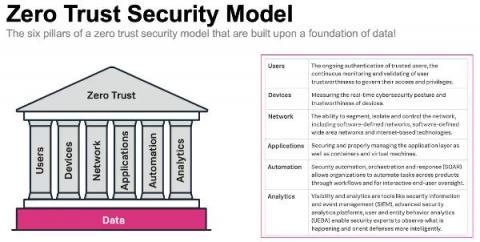
A Zero Trust Security Approach for Government: Increasing Security but also Improving IT Decision Making
Public sector organisations are in the middle of a massive digital transformation. Technology advances like cloud, mobile, microservices and more are transforming the public sector to help them deliver services as efficiently as commercial businesses, meet growing mission-critical demands, and keep up with market expectations and be more agile.
Hunting for threats in multi-cloud and hybrid cloud environments
Remote work and its lasting impact: What our global research uncovered
The COVID-19 pandemic has not only had a profound impact on everyone across the globe; it has also fundamentally changed the way organizations function. We are nearing one and a half years since remote work became the norm and organizations had to adapt to this new mode of working almost overnight. This rapid transition wouldn’t have been possible without the massive technology, workflow, and process upgrades undertaken by IT departments.
Secure your infrastructure in real time with Datadog Cloud Workload Security
From containerized workloads to microservice architectures, developers are rapidly adopting new technology to scale their products at unprecedented rates. To manage these complex deployments, many teams are increasingly moving their applications to third party–managed services and infrastructure, trading full-stack visibility for simplified operations.
Elastic Introduces the Industry's First Free and Open Limitless XDR
The Cost of Avoiding Security Automation
Security touches every aspect of an organization's infrastructure and influences most of its processes. That's a lot to cover, and it seems like there are never enough people to handle the work. Even with budgets increasing by an average of 10% annually over the last 5 years, the recent increase in remote work and cloud adoption is stretching security teams even thinner.
What is Splunk Security Analytics for AWS?
CFEngine: The Agent Is In 3 - What's New In 3.18 LTS?
What's New in Calico v3.20
We’re excited to announce Calico v3.20! Thank you to everyone who contributed to this release! For detailed release notes, please go here. Below are some highlights from the release.
Automate Secure Access Management With Rollbar + Okta
At Rollbar, we know security matters. Our customers represent the leading technology companies in the world today, and keeping their data secure is our top priority. Look no further than our investment in security and compliance. Rollbar is fully compliant with stringent industry standards like GDPR and HIPAA. We have also received ISO27001, SOC 2 Type 1, and Type 2 compliance certifications to ensure that even the most security-conscious companies can use our SaaS platform.
Fighting Ransomware: Using Ivanti's Platform to Build a Resilient Zero Trust Security Defense
Ransomware is a strain of malware that blocks users (or a company) from accessing their personal data or apps on infected iOS, iPadOS, and Android mobile devices, macOS laptops, Windows personal computers and servers, and Linux servers. Then the exploit demands cryptocurrency as payment to unblock the locked or encrypted data and apps. This form of cyber extortion has been increasing in frequency and ferocity over the past several years.
Our plan for world domination: take down the internet
We have been warning for a long time: Pandora FMS will control the world. We have given time to world governments to prepare, to North American villagers to prepare their bunker, for sects to draw their banners with “THE END IS NEAR”. And it is, it is indeed. Today, in our blog we reveal the secret plans of this company to overthrow the institutions and rule the world, then you will say that we did not warn you.
Limitless XDR defined: Ingest, retain, and analyze security data freely
Elastic Security's newest features define the potential of XDR for cybersecurity teams. Our single platform brings together SIEM and endpoint security, allowing users to ingest and retain large volumes of data from diverse sources, store and search data for longer, and augment threat hunting with detections and machine learning. Security vendors are using the term “XDR” with increasing frequency, applying varied definitions to suit their respective technologies.
Elastic 7.14.0 introduces the industry's first free and open Limitless XDR
We are pleased to announce the general availability (GA) of Elastic 7.14, including our Elastic Enterprise Search, Observability, and Security solutions, which are built into the Elastic Stack — Elasticsearch and Kibana. Elastic 7.14 empowers organizations with the first free and open Limitless XDR, which delivers unified SIEM and endpoint security capabilities in one platform.
Legacy vs. Modern Cloud SOAR-Powered SOC
Democratizing Automation for Security Teams
Everyone wants to automate security. Traditionally, though, doing so has been challenging because setting up security automation tools required a specialized set of skills that no one engineer at a company possesses. It’s time to change this state of affairs by democratizing security automation. Here’s why and how.
Building a Network Architecture to Support the Next Phase of Remote Work
Ivanti Acquisition of RiskSense Provides Greater Protection for the Everywhere Workplace
If you have been watching Ivanti this year, you have seen that we are delivering on our commitment to make the Everywhere Workplaces possible by providing our customers more robust solutions to discover, manage, secure and service their IT assets. We have been doing this organically, we rolled out our Ivanti Neurons hyper-automated platform last July, and we have also added to the platform’s capabilities and value with acquisitions.
Ransomware is on the rise. Here's how Ivanti x RiskSense will solve it.
Ransomware started making more headlines in 2016, but it was treated largely as a nuisance – not a tangible, resource-worthy threat. Fast forward to 2021 and ransomware has graduated to the big leagues, buoyed by a pandemic-fueled, hasty scramble toward decentralized workforces and digital everything. But this rising threat can’t be entirely blamed on the pandemic.