Operations | Monitoring | ITSM | DevOps | Cloud
July 2022
How Chatbot Automation Benefits Security Teams
When you hear the term “chatbot,” your mind may at first turn to things like robotic customer support services on retail websites – a relatively mundane use case for chatbots, and one that is probably hard to get excited about if you’re a security engineer. But, the fact is that chatbots can do much more than provide customer support.
Processes, forks and executions - part 2
This is the second blog post in a short series about processes on UNIX-like systems. It is a followup to the previous post which focused on basic definitions, creation of processes and relations between them. This time we analyze the semantics of two closely related system calls that play major roles in process creation and program execution.
Welcome to Puppet Comply
CFEngine: The Agent Is In 15 - Extending Autorun
How Organizations Can Mitigate Human Operator Error & Increase Security
Why Hyperscale Data Centres Are Becoming More Important for Your Business
5 Secure Remote Access Solutions for Businesses
As many workers have shifted to working in offsite locations, the need for secure remote access for remote support and device management has never been greater. IT teams need It can be difficult to securely access and control all your organization’s endpoints, but secure remote access solutions simplify and streamline that process.
CFEngine Build in Mission Portal Web UI (Developer demo)
SOC 2: Data Security For Cloud-Based Observability
As more companies adopt SaaS services over on-premise delivery models, there is a natural concern around data security and platform availability. Words on a vendor’s website can provide insights to prospective customers on the process and policies that companies have in place to alleviate these concerns. However, the old adage of “actions speak louder than words” does apply. Trust in a website’s words only goes so far.
Zero Trust Security: Key Concepts and 7 Critical Best Practices
Zero trust is a security model to help secure IT systems and environments. The core principle of this model is to never trust and always verify. It means never trusting devices by default, even those connected to a managed network or previously verified devices. Modern enterprise environments include networks consisting of numerous interconnected segments, services, and infrastructure, with connections to and from remote cloud environments, mobile devices, and Internet of Things (IoT) devices.
How To Build Cybersecurity Culture At Your Company
Cybersecurity is a key priority for small, medium, and large companies. If you are a keen internet user or a lover of news and trending topics, I am sure you already know the current threats surrounding the cybersecurity realm. Cybersecurity threats are now a nightmare that faces all levels of organizations. Malware attacks, DDoS threats, phishing, brute force, SQL injections, etc. are running riot in the internet streets.
Thinking Smarter About M&A-Are you secure?
With the continued focus in our space on the movement from MSP to MSSP, it’s crucial to remember that products alone don’t necessarily make you an MSSP. For smaller customers, although you might be able to provide a range of security solutions (like EDR and backup) and compliment these with an RMM to provide insight and control over end user devices, this is not enough to call yourself an MSSP.
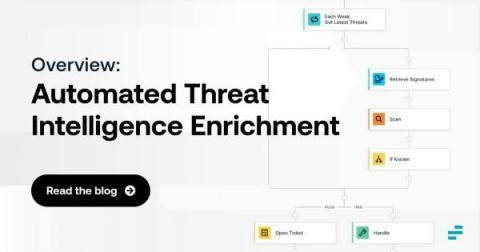
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.
What Is a Secure SDLC?
The Software Development Lifecycle (SDLC) framework defines the entire process required to plan, design, build, release, maintain and update software applications, including the final stages of replacing and decommissioning an application when needed. A Secure SDLC (SSDC) builds on this process, integrating security at all stages of the lifecycle. When migrating to DevSecOps (collaboration between Development, Security, and Operations teams), teams typically implement an SSDLC.
Processes, forks and executions - part 1
While working on the integration of CFEngine Build into Mission Portal we came to the point where we needed to start executing separate tools from our recently added daemon - cf-reactor. Although it may seem like nothing special, knowing a bit about the process creation and program execution specifics (and having to fight some really hard to solve bugs in the past) we spent a lot of time and effort on this step.
Optimizing Security and Digital Experiences: Why User Experience Monitoring is Key
For just about any organization, there’s a balance that has to be struck between absolute security and absolute convenience. Seemingly, every new innovation that increases convenience also introduces new risks. On the other hand, every safeguard instituted can also create complexity, delays, or in some other way diminish the user experience. Either way, businesses are exposed, whether to the catastrophic consequences of breaches, or of an erosion of user productivity and customer retention.
Driving Innovation Aligned with the AWS Security Competency Re-launch
Logz.io recently obtained the Amazon Web Services (AWS) Security Competency for our Cloud SIEM. We are thrilled to support the re-launch of the AWS Security Competency, as clearly the only way to combat today’s cybersecurity challenges is to modernize your analytics platform to respond to today’s evolving threat landscape.
Protect your cloud with Spot Security
How to use GitHub Actions securely
GitHub is one of the most popular source control platforms available. It relies on Git concepts, and millions of developers use it. GitHub Actions embrace all aspects of what source control needs, such as branching, pull requests, feature flags, and versioning. It also integrates nicely into third-party continuous integration and continuous development (CI/CD) pipelines or deployment tools like Azure DevOps, Jenkins, GitLab, and Octopus Deploy.
Masking PII: Minimize Your Risk and Stay Out of Trouble
Consumers expect their personal information to be safe in your hands as they use your apps, services, and stores. Even in-person retailers collect customer data for loyalty programs, shopping history, and more. In addition, regulators and auditors — and while we’re at it, let’s add investors, board members, and partners to the list of people who expect all customer data to be secure at all times.
Masking Data with Cribl Stream
N-able EDR and SentinelOne deliver for Ballast Services
How to develop a successful threat-hunting program
According to the 2021 Cost of Data Breach report, the average attack “dwell time”—the period between an attacker’s breach of an organization’s network and the point at which the organization finds out about it—is 287 days. During this time, the attacker can stealthily look to gather valuable information to steal or compromise data, incurring huge costs for affected companies.
Best Practice Series: Securing the Monitoring System
More than half of organizations prioritize security over user experience
API Security - Threats & Best Practices
An API is an interface that allows other software programs to access and execute software programs. Software programs exchange data and communicate via this code. Communicating between products and services without requiring users to understand how they work. Social networks, games, database systems, and devices use web APIs to connect with applications.
Personally Identifiable Information (PII) - A Beginner's Guide
PII stand for Personally Identifiable Information, so protecting Personally Identifiable Information (PII) is a top priority for companies small and large, as well as government agencies. Companies are amassing increasing amounts of data on their employees, customers, and partners, making PII security more important than ever. It's critical to understand what PII is and how to protect it. Personal information can be divided into two categories.
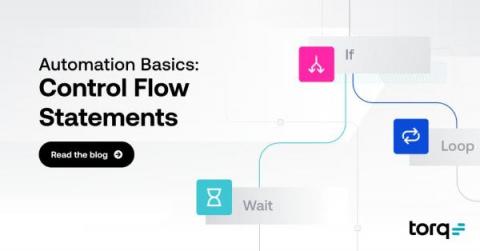
What Are Control Flow Statements?
Control flows are the backbone of automation. Identifying what to do with a set of data – and how – is a key component of high-value automation, but it can also be confusing to wrap your head around at first. What is a conditional? And what does it have to do with a loop? How do you deal with a set of information versus a single data point?
Voice Network Fraud: How to Fight Back with Automated Threat Prevention
Torq Automation Template - Generate report on non-compliant devices
Torq Automation Template - Just-In-Time Access
Torq Automation Template - Add/Remove URLs from a Blocklist
Torq Automation Template - Suspend Inactive Contractor Accounts
Torq Automation Template - IP Penalty Box with Timeout
Keeping repair manuals and parts lists private and current
Automating compliance in software delivery
Software development teams face a large and growing number of obstacles: shifting design requirements, organizational blockers, tight deadlines, complicated tech stacks and software supply chains. One emerging challenge that developers and IT leaders face is the need to stay compliant with regulations and control frameworks that stipulate comprehensive data security, incident response, and monitoring and reporting requirements.
Detect Cryptocurrency Mining with Flowmon NDR
Top 5 Takeaways from RSAC 2022
It’s been just over a month since cybersecurity conferences returned in a big way with the comeback of RSA Conference after last year’s hiatus. A lot happened between 2020 and 2022 in the world, our lives, and cybersecurity, including the birth of a little no-code security automation start-up named Torq. RSAC 2022 was a great place to catch up on these changes and look forward to emerging trends and security needs.
Generating Secure Passwords for your Linux Server
Having a strong password is necessary to protect our information from being accessible by others. A strong password should be difficult to be identified, guess or decrypt by the attackers. Mostly, while entering passwords, we will be prompted to enter the upper case and lowercase letters along with numbers and special characters. But thinking of a new password every time is very difficult and most people end up repeating the same password for every website and application they use.
Empowering Security Engineers With the Cribl Pack for CrowdStrike
CrowdStrike is a class-leading endpoint monitoring solution. It collects a wealth of activity data from each managed endpoint that can be fairly voluminous. This includes network connectivity, DNS request, process activity, health checks, and the list goes on. In fact, there are over 400 event types reported by CrowdStrike! These events are a gold mine for threat hunters and blue teams looking for unusual or malicious activity. It can be extremely costly to place all this data in a SIEM.
How to help ensure cyber safety this summer
You’ve been waiting and planning all year. The sunscreen is packed, the neighbors have a spare key to water the plants while you are away, you made sure to set your out-of-office notifications, and emergency contact information has been updated. It is time for vacation season!
Powering government security and innovation in the cloud
It’s no secret that government agencies are facing increasing restrictions and compliance regulations as they strive to ensure effective data governance and protection. “Agencies have a lot of regulated information that needs to be governed, and they need to make sure it’s not compromised,” says Corey DuBois, senior advisory presales solution consultant at ServiceNow. “There are a lot of checks and balances they need to have in place.”
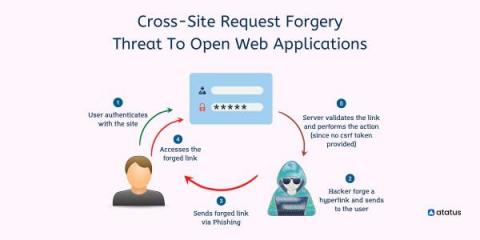
Cross-Site Request Forgery - Threat To Open Web Applications
Cross-site request forgery (CSRF) is an attack that tricks a user's browser into sending a malicious HTTP request to another website. This malicious HTTP request looks like it was sent by the user, but it actually comes from the attacker. A cross-site request forgery (CSRF) attempts to execute a change rather than trying to download personal data. Once an attack is executed there is no way for the attacker to directly monitor the result so attackers often execute multiple forgeries.
What IT Pros Can Learn from the Marriott Data Breach
Despite the best efforts of individuals to protect their own data, they cannot always account for the cybersecurity shortcomings of larger organizations such as their employers, financial institutions, and healthcare providers entrusted with their personal information. Hotels should also be added to this list of vulnerable entities, as was made painfully apparent in the most recent Marriott data breach.
Container Registry Scans with NeuVector
How Modern Log Intelligence Meets New Cybersecurity Regulations by CERT-In
Blueprint for Secure OSS Supply Chains
The CrowdStrike Pack
Automated Security Alert Remediation: A Closer Look
In cloud-native organizations and software as a service (SaaS) businesses, cloud security automation is becoming a must-have feature. You can't stay ahead of threats across several levels of your cloud environment using manual procedures alone, and you can't rely exclusively on cloud providers' security technology, which doesn't operate across different clouds and lacks advanced automation features. Managing these infrastructures and apps in multi-cloud settings becomes increasingly difficult and compounds the operational issues that you face today. Automation is the way to go if you want to stay ahead of the game and meet the expectations of your customers.
What is DataPower used for?
What is DataPower used for? It provides security, control, integration and optimized access to a full range of mobile, web, application programming interface (API), service-oriented architecture (SOA), B2B and cloud workloads.
Seven steps to help protect your ERP system against cyberattacks
Many companies’ enterprise resource planning systems, which house their most valuable data, are still too vulnerable. What would happen if your enterprise resource planning (ERP) system were attacked? For many companies, the consequences would be devastating.
Cloud Security: Key Emerging Trends You Need to Know in 2022 And Beyond
The early days of cloud computing saw people subject it to severe scrutiny. The main talking point revolved around its security and the ability of infrastructure providers to keep it secure. Regardless of the doubts, more businesses are migrating to the cloud. That's mainly because leading cloud service providers have consistently improved and upgraded their processes to secure their networks. However, even with years of improvement, the old fears remain.
Kafka Security - First Steps
Apache Kafka provides an unified, high-throughput, low-latency platform for handling real-time data feeds. Installing Apache Kafka, especially the right configuration of Kafka Security including authentication and encryption is kind of a challenge. This should give a brief summary about our experience and lessons learned when trying to install and configure Apache Kafka, the right way.
The state of configuration management
Since joining the CFEngine team in 2019 I’ve heard and read numerous times that the configuration management market is dying and becoming obsolete. While I and many others don’t personally adopt this line of thinking, I can understand why one would come to this conclusion being that we’re in an ever-changing industry and talking about solutions that have been around for decades.
Community Spotlight series: Calico Open Source user insights from Cloud Native Technologist, Jintao Zhang
In this issue of the Calico Community Spotlight series, I’ve asked Jintao Zhang from API7.ai to share his experience with Kubernetes and Calico Open Source. API7.ai is an open-source infrastructure software company that helps businesses manage and visualize business-critical traffic, such as APIs and microservices to accelerate business decisions through data.
LogRhythm Cloud: Too Little, Too Late
Over the last 12 months, we’ve seen growing momentum around several disruptive trends in the cloud SIEM market. One of the most pervasive and obvious developments for Logz.io is the frequency with which we encounter customers seeking to replace dated and legacy on-premises SIEMs with a solution such as our Cloud SIEM. The traditional provider that comes up most often is LogRhythm—for numerous different reasons.
IVANTI SECURITY INSIGHTS: Gartner Security & Risk Management Summit Takeaways
The case for EDR vs Antivirus: Three reasons to step up your game
Over the past couple of years, we’ve witnessed a rapid adoption of endpoint detection and response (EDR) in the MSP space. An increasing number of managed service providers are choosing to leave behind legacy antivirus (AV) solutions in favor of EDR security. The differences between the core functions of AV and EDR are easy to understand and many see EDR as an obvious choice. However, some still believe that AV is enough because the customers they support have a low risk profile.
How Long Does It Take to Notice a Ransomware Attack?
Ransomware was, once again, the top cyberattack type of 2021. It has been at the top of the threats list for three years in a row. Experts estimated that a ransomware attack occurred every 11 seconds last year. The average cost of ransomware recovery was estimated to be $1.85 million. These statistics explain why some have proclaimed ransomware to be a modern threat to public safety. In this blog, we’ll demystify ransomware and answer some key questions pertaining to it.
To Help You Secure Your Email, Private Portal Is Now Available-For Free
We live in a world where 83% of security professionals believe that employees have accidentally exposed customer or business-sensitive data at their organization via email (Business Wire). This sheds light on a great vulnerability faced by MSPs and internal IT businesses worldwide: once you share critical information with your end users, that data is no longer in your hands, hence your security does not extend to it anymore. If only there was a way to prevent that! Luckily, there is.
CFEngine 3.20 released - Modularity
Today, we are pleased to announce the release of CFEngine 3.20.0! Over the past few years we’ve focused on ease of use, new user experience, and out of the box value, giving you the ability to do much more through only the Mission Portal Web UI. This has resulted in several important steps forward; policy analyzer, compliance reports, host specific data (CMDB), and CFEngine Build with custom promise types and other modules.