Operations | Monitoring | ITSM | DevOps | Cloud
December 2022
Buying a Domain for Your Business: 6 Tech Tips to Help You
How Can Devops Speed Up The Software Development Process?
CFEngine: The agent is in 20 - The 2022 CFEngine holiday security calendar
Qovery now supports AWS STS: Protect your resources with temporary access keys
CFEngine 2022 retrospective
It’s that time of year again where we reflect & recap all things new with CFEngine from this year. You may recall from the 2021 retrospective that our focus for 2022 would be on collaboration, ease of use, and community engagement. I’m proud to summarize our progress below in these key areas for 2022’s Retrospective and give you a sneak peek at what’s to come in 2023.
6 Types of Access Control for a Residential Building and Which One You Should Choose
Getting Amazon GuardDuty alerts via SNS Endpoint
Surefire Remote Work Monitoring Hacks For New Businesses
Security holiday calendar - Part 2
Thank you for following along with our security themed holiday calendar. Today, we summarize the last half of the calendar, in case you missed some days.
4 Types of IT Security Issues Companies Are Facing in a Tech-Enriched Environment
Building Cyber Resilient Ecosystems
CFEngine 3.21 LTS released - Unification
Today, we are pleased to announce the release of CFEngine 3.21.0! The focus of this new version has been unification. Across our websites and UI, you should see that it’s a much more modern and unified experience, whether you’re reading this blog post on cfengine.com, browsing the new documentation site, looking for modules on the CFEngine Build website, or adding input to modules within Build in Mission Portal.
How detection engineering keeps ServiceNow safe
“Security defense is exciting, because you’re always trying to stay ahead of the bad guys,” says Tracy T., senior staff detection engineer at ServiceNow. Who are these bad guys? They could be malware or hackers who try to threaten the security of employee data or the company network—or anything in between. Detection engineering plays a major role in keeping a company safe, especially amid changing tool capabilities and detection methods.
How to build a service mesh with Istio and Calico
Microservices are loosely coupled software that provides flexibility and scalability to a cloud environment. However, securing this open architecture from vulnerabilities and malicious actors can be challenging without a service mesh. This blog post will demonstrate how you can create an Istio and Calico integration to establish a service mesh that will manipulate HTTP traffic in the application layer.
The Critical Role of Intrusion Prevention Systems in Network Security
An Intrusion Prevention System (IPS) is a network security and threat prevention tool. Its goal is to create a proactive approach to cybersecurity, making it possible to identify potential threats and respond quickly. IPS can inspect network traffic, detect malware and prevent exploits. IPS is used to identify malicious activity, log detected threats, report detected threats, and take precautions to prevent threats from harming users.
How Important Is The Infrastructure For Online Trading Services?
Enterprise and Edge Scale Security with NeuVector Container Security 5.1
I’m excited to announce the general availability of the SUSE NeuVector container security platform version 5.1. With the 5.1 release, customers will benefit from more efficient and powerful vulnerability scanning and admission controls across multiple clusters through centralized enterprise scanning, auto-scaling scanners and support for the new Kubernetes (1.25+) pod security admission (PSA) standard. The release also supports the Cilium network plug-in.
Jason Chan on How Torq Overcomes Cybersecurity's Biggest Challenges
Jason Chan is one of the world’s foremost cybersecurity authorities and we’re extremely proud to have him as a member of the Torq Advisory Board. He’s a pivotal figure in driving adoption of security automation best practices at many companies, including Netflix, where he led the information security organization.
5 security hardening CFEngine policy examples
Throughout the security holiday calendar, we’ve looked at modules for enforcing security requirements. Writing the policy to achieve these security hardening goals is easy. By learning how, you can write policy (or modules) for any requirements, including those specific to your organization. In this blog post, we’ll take a look at five beginner-level examples to get you started, focusing on the most common resources to manage with CFEngine; files and packages.
Should Your Business Use A VPN?
How you can do regulated DevOps with Kosli - Mike Long - CEO - Kosli
DevSecOps The Broken or Blurred Lines of Defense - John Willis - Kosli
How can tech bridge the gap on compliance audit risk and security - Panel Discussion
Kentik DDoS Protection in 20 Seconds
LIVE NOW: 2022 State of DevOps
Regulations vs DevSecOps Requiem - Diptesh Mishra - CTO - Shoal
How to Monitor kube-controller-manager
When it comes to creating new Pods from a ReplicationController or ReplicaSet, ServiceAccounts for namespaces, or even new EndPoints for a Service, kube-controller-manager is the one responsible for carrying out these tasks. Monitoring the Kubernetes controller manager is fundamental to ensure the proper operation of your Kubernetes cluster. If you are in your cloud-native journey, running your workloads on top of Kubernetes, don’t miss the kube-controller-manager observability.
What's new in Calico Enterprise 3.15: FIPS 140-2 compliance, new dashboards, egress gateway pod failover, and more!
Tigera provides the industry’s only active Cloud-Native Application Security Platform (CNAPP) for containers and Kubernetes. Available as a fully managed SaaS (Calico Cloud) or a self-managed service (Calico Enterprise), the platform prevents, detects, troubleshoots, and automatically mitigates exposure risks of security issues in build, deploy, and runtime stages across multi-cluster, multi-cloud, and hybrid deployments.
A guide to cyber threat hunting with Promtail, Grafana Loki, Sigma, and Grafana Cloud
Fact: The Security Operations team at Grafana Labs loves logs. They are a key pillar of observability for many reasons, such as how they are stuffed full of details to help us diagnose the “why?” when things go wrong. This is especially true when the information pertains not to a series of unfortunate events, but instead to an adversary trying to cause us harm.
All I want for Christmas is...no more phishing emails!
It’s the holiday season again, which means family gatherings, good food, and plenty of toasts. It also means a lot of online activity—buying gifts, getting promotional offers, booking deliveries—all of which mean a continuous flow of emails sent to your personal and business accounts. With so much going on, even experienced users can accidentally fall prey to one of the many “hooks” that cybercriminals are putting out there.
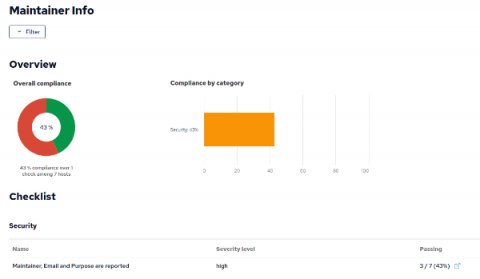
Track maintainers and purpose for hosts in your infrastructure
When something goes wrong or looks fishy for a particular host in your infrastructure how do you know who to ask about it? In an infrastructure managed by many and used by many it is also helpful to know what each hosts’ purpose is. In this article we show how to add maintainer and purpose information to individual hosts in your infrastructure via the CMDB feature of Mission Portal. We will also add a Build Module to add this information to the /etc/motd file for each associated host.
N-able Wins "Security Vendor of the Year" and "Backup and Archive Innovation of the Year" at 2022 SDC Awards
File integrity monitoring with CFEngine
File integrity monitoring is an important aspect in managing your infrastructure. Tripwire and AIDE are often cited as necessary tools by compliance frameworks1,2,3. Of course CFEngine can manage a file to make sure it contains desired content, but did you know that CFEngine also has the capability to simply monitor a file for change? In this blog post we take a look at CFEngines’ changes attribute for files promises.
Governance, Risk and Compliance for MSPs in 2023
Six Mistakes To Avoid When Mapping Your Enterprise Data Landscape
What's in store in 2023 for the tech industry?
Security holiday calendar - Part 1
As it was well received last year, we decided to do another security-focused holiday calendar this year. The concept was roughly the same, but instead of only adding security hardening modules, we’ve also added in some other security advice and blog posts to improve the variety. Now that we’re halfway through to 24 (or 25), let’s recap the first half of the calendar.
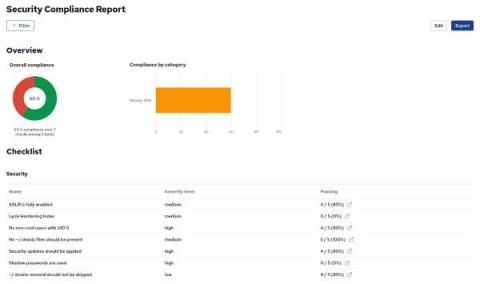
Building a Compliance Report based on inventory modules
In CFEngine Enterprise we collect information from each system in the infrastructure as inventory. Some inventory is available by default, and more can be added using modules or writing policy. You can use inventory information to create a Compliance Report with checks that determine if the information complies with your security requirements. In this blog post, we will use some modules from CFEngine Build which provide inventory data, and build a Compliance Report on top of those.
Top 5 benefits of network backup software
Grafana 9.3 feature: Grafana OAuth token improvements
As part of our efforts to improve the security of Grafana, we introduced a long-awaited feature in the latest Grafana 9.3 release that enhances Grafana’s OAuth 2.0 compatibility. The new Grafana OAuth token improvements, which are available in Grafana OSS, Grafana Cloud, and Grafana Enterprise, ensure that the user is not only logged into Grafana, but they’re also authorized by the OAuth identity provider.
The What, Why and How of Auto-Remediation in Cybersecurity
When you’re facing a cyberattack, waiting even just minutes to respond could be the difference between business as usual and a calamity. It may only take that long for threat actors to exfiltrate sensitive data or disrupt critical systems. That’s one reason why automating remediation is an essential ingredient in an effective cybersecurity strategy.
Cyber Attacks Are Getting Smarter... Are You Ready?
It feels like everything is getting a “smart” upgrade these days. From the cars we drive to how we operate our domestic appliances, almost every gadget has had a smart upgrade or now uses Artificial Intelligence (AI) to improve our lives – or so they claim…
How to Augment an Existing Data Lake with Exabeam and Cribl Stream
Organizations have different data lakes they use to search, whether it is Splunk, Qradar, or Sumo Logic just to name a few. Exabeam (UEBA Advanced Analytics) sits on top of those existing data lakes and pulls specific sources by running continuous queries every few minutes into Exabeam. The image below shows a Splunk query to pull windows event logs into Exabeam Advanced Analytics over the port (8089). The query is complex.
The Economics Behind Cloud-First Data Protection
Graylog 5.0 - A New Day for IT & SecOps
We are excited to announce the release of Graylog 5.0! Graylog 5.0 brings updates across our entire product line, including changes to infrastructure, Security, Operations, and our Open offerings. For more detailed information on what’s changed, visit our changelog pages for Graylog Open and Graylog Operations/Graylog Security.
Torq Users Hit 1,000,000+ Daily Security Automations
Security automation is an increasingly critical element in optimizing enterprise cybersecurity postures. Today, Torq announced its users are executing more than 1,000,000 daily security automations using our security automation platform – a major milestone that underlines the traction and importance of unifying today’s complex security stacks.
Don't be held to ransom: Security awareness with Platform.sh
Ransomware is an ever-evolving type of malicious software (a.k.a malware) in which an attacker encrypts the files on a victim’s device, rendering it inaccessible and unusable. Then - you guessed it - they demand a ransom from the target before they’ll fix it. Not something any organization ever wants to deal with, and not something any organization has to deal with if they have the right measures in place to minimize the risk. Let’s talk about how!
4 API Security Best Practices To Safeguard Sensitive Data
Thanks to the increasing usage of different software solutions, API usage has become an everyday practice. As such, API security is a more prevalent issue in app development than ever before. SaaS companies have an average of 350 integrations, whereas major SaaS companies like Slack, Zoom and Shopify have 2,000+ integrations. This is great for developers and end users, as Application Programming Interfaces (API) make life easier.
Baking Security into your DevOps Supply Chain with Argo CD & OPA - Dan Garfield (DevOps Experience)
Cyber, incident, downtime: Three words that chill the board, and how to tame them
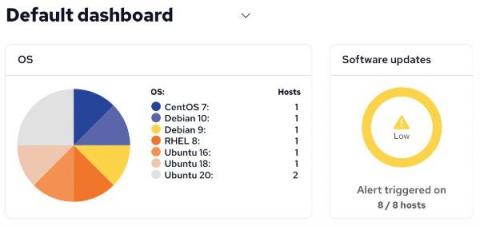
Updates, upgrades, and uptime
All software of any significant size has bugs, vulnerabilities, and other weaknesses. This includes the operating system (OS), libraries, command line tools, services and graphical applications. Across your infrastructure, you should have an overview of what operating systems and software you have installed. Additionally, automated ways of upgrading the OS, as well as packages are desirable.
Reasons to Use a Virtual Private Network
Five Hidden Security Risks You May Find with Traditional Backup Mechanisms
It’s always been important for managed services providers (MSPs) to exercise backup best practices but this has become even more important with the pandemic having reset employees’ expectations around remote work. Up to 74% of professionals believe that remote work is here to stay according to Growmotely, while 16% of companies globally are already completely remote and 40% offer hybrid working.
Your Checklist for an Application Blocklist
With the advent of remote and hybrid work, the line that separates work from personal life is increasingly hazier. This thinking applies especially to our digital lives. When work still revolved around fixed hours on-site, admins could easily determine which applications to block. For example, a worker should not be able to access the Netflix application at the office during business hours.
Top 6 Emerging Cybersecurity Challenges For 2023
Protecting sensitive data from malicious code and dangerous third parties is a critical task rather than something that should be taken for granted. With that in mind, it's an important - yet often overlooked - aspect of security that users stay informed about what's happening in this niche. After all, data security threats evolve at a staggering pace, and 2023's future cyber-attacks are bound to be as inventive as they've ever been.