Operations | Monitoring | ITSM | DevOps | Cloud
February 2023
Reducing Security Incidents: Implementing Docker Image Security Scanner
Are you utilizing Docker to deploy your applications? If so, you're not alone. The use of Docker has skyrocketed in popularity in recent years. While it offers numerous benefits, it also introduces new security risks that need to be addressed. But, why is reducing security incidents so important? Simple - the cost of a security breach can be devastating. From lost customer trust to financial losses, the consequences of a security incident can be severe. That's why it's crucial to take steps to prevent them from occurring in the first place. Enter Docker image security scanners.
Confidential K8s Control Plane - Securing Kubernetes API with Intel SGX
Introduction to CFEngine Build - Lars Erik Wik & Ole Herman S. Elgesem (CfgMgmtCamp 2023)
For slides and more information, see our blog post:
https://cfengine.com/blog/2023/cfgmgmtcamp/
What's new in Calico Enterprise 3.16: Egress gateway on AKS, Service Graph optimizations, and more!
We are excited to announce the early preview of Calico Enterprise 3.16. This latest release extends the active security platform’s support for egress access controls, improves the usability of network-based threat defense features, and scales visualization of Kubernetes workloads to 100s of namespaces. Let’s go through some of the highlights of this release.
Enabling TLS on a Cribl Leader Node: Step-by-Step Guide
Securing your internal systems with TLS can be a daunting task, even for experienced administrators. However, with the right tools and guidance, the process can be made more manageable. In this blog, we’ll show you how to enable TLS for your internal systems on your Cribl Leader Node. We’ll walk you through the steps, and provide a video tutorial embedded below to help you follow along.
5 Advanced DevSecOps Techniques to Try in 2023
If you're here, you know the basic DevSecOps practices like incorporating proper encryption techniques and embracing the principle of least privilege. You may be entering the realm of advanced DevSecOps maturity, where you function as a highly efficient, collaborative team, with developers embracing secure coding and automated security testing best practices.
How to choose and track your security KPIs
What do best-in-class cybersecurity organizations do differently? | CISO Panel
3 Android Settings You Need to Turn Off
In a World of Managing Risk, Do You Have Shiny Tech Syndrome?
There is always something new on the horizon when it comes to technology. Isn’t it human nature to want to wait for the next 'new' model car, the next 'bigger' TV or the next 'faster' smart phone? The newest release might be more appealing – especially to higher-ups, who want the latest and greatest trending technology. But there are hidden risks associated with waiting to implement a new tool or solution.
Top 7 SSL Monitoring Tools
Reliable SSL monitoring is crucial to every website and online service. Without it, you can lose customers, profits, and even your position in search engine rankings. But which SSL certificate monitoring is the best?
The Power of Combining a Modular Security Data Lake with an XDR
Fixing Security's Data Problem: Strategies and Solutions with Cribl and CDW
CFEngine: The agent is in 22 - Hackathon: Termux services on Android
Understanding Log4Shell: An Ultimate Guide to Protecting your System
Coding is a big part of building an application. But, most of the time, you don’t write the entire code. Yes, you don't! Some people, usually big companies, provide pre-written codes for certain standard functions - like loggers, APIs, etc. This is because these functions work the same way in most applications; they require only simple fine-tuning to be adapted for your program as well. In such a case, writing it all from scratch would be a waste. And that is why developers use libraries.
Linux security: your questions, answered
At Canonical, we often get questions about open-source security and of course, Linux security is a common topic. Based on a recent webinar hosted by our security team and an accompanying blog post, we put together the most common questions we receive. This is by no means an exhaustive list, but it should give you a general idea about Ubuntu’s approach to security vulnerability management, livepatch, IoT, and its compliance and hardening tools.
Monitor User Behavior to Detect Insider Threats
The risk from insider threats has grown massively, with perpetrators frequently getting around organizations' increasingly complex perimeter protections. It is one of the most common ways customer data or industrial and trade secrets leak. This very complex topic includes many types of threats and techniques. Let's discuss how you could detect insider threat activity at a network level.
How to Create and Manage Secrets in Kubernetes
Kubernetes Secrets are a built-in resource type that's used to store sensitive data. This blog teaches you how to work with Secrets in Kubernetes. Kubernetes can do many things, but we usually refer to it as a “container orchestrator.” Orchestrating containers means starting and restarting them when needed, ensuring their configuration matches the declared state, and autoscaling them. But Kubernetes can do much more than that.
AWS Configuration for the Cribl Pack for SentinelOne Cloud Funnel
In the blog titled “Streamline Endpoint Data with Cribl Pack for SentinelOne Cloud Funnel” we dove into the Cloud Funnel data, its relevance in the modern SOC, and how Cribl Stream transforms the data while addressing visibility gaps. We left the AWS-specific details to this blog for those not yet familiar with configuring AWS S3 buckets, SQS Queues, and Identity and Access Management (IAM).
How To Safeguard Your Business Against Data Leaks
3 Key Takeaways from CloudNativeSecurityCon 2023
CloudNativeSecurityCon North America, a two-day event organized by the Cloud Native Computing Foundation (CNCF), recently took place in Seattle, Washington, and gave the industry an opportunity to come together to discuss cloud native security projects and how to address today’s security challenges and opportunities. Supply chain security was a hot topic at the event, as it has been across the industry for the last few years.
Streamline Endpoint Data with the Cribl Pack for SentinelOne Cloud Funnel
Cribl empowers you to take control of your observability, telemetry, and security data. Wherever your data originates from, wherever your data needs to go, and whatever format your data needs to be in, Cribl gives you the freedom and flexibility to make choices instead of compromises. Addressing visibility gaps by ingesting more data sources as the threat surface continues to expand has been a challenge.
What is Managed Detection and Response (MDR)?
Cybersecurity is a top concern among businesses, especially as the number of cyberattacks, data breaches, and malware infections continue to grow each year. These attacks can happen at any moment during the day, too. It can be a headache trying to keep watch for cyberthreats 24/7 and know how to effectively respond when they are detected, especially for MSPs who have multiple different clients.
RapidSpike ROI Calculator
What Is a Business Continuity Plan, and Why Does Your Startup Need It?
What Is Cyber Security And Why Is It Important?
In an online age, cyber security is more crucial than ever. It is essential to do business, socialize, and store sensitive information. It is crucial to stay secure online. Whether it's ransomware, phishing emails, or data breaches, countless potential sources of attack can have huge implications and expensive consequences. To keep data secure from cyberattacks, businesses must invest in robust cybersecurity solutions tailored specifically to their needs.
N-able and SentinelOne Hit the Road for Security-Focused Partner Roadshow
Process monitoring: How you can detect malicious behavior in your containers
The default pod provisioning mechanism in Kubernetes has a substantial attack surface, making it susceptible to malevolent exploits and container breakouts. To achieve effective runtime security, your containerized workloads in Kubernetes require multi-layer process monitoring within the container.
Empowering SecOps Admins: Getting the Most Value from CrowdStrike FDR Data with Cribl Stream
Endpoint Detection and Response (EDR) Explained
Although endpoint detection and response has been around since 2013, EDR is still IT security’s most popular buzzword today. The reason why organizations around the globe choose to use endpoint detection and response as one of their top security solutions is simple: it works. Fighting against malicious endpoint threats and cyberattacks is by no means an easy task.
Top Reasons Why Testing Is Crucial In Every Field
Tech Tips To Go The Extra Mile With Cyber Security
Tackling the Security Budget in Times of Economic Uncertainty: IT and Security Leaders Prioritize Cybersecurity
In today’s economic climate, IT and security budget owners are always looking for ways to increase efficiency while controlling costs. With tighter budgets and increasing workloads, organizations have to find ways of stretching their limited resources while making sure investments are paying off.
Sneak peek: Groups in Mission Portal
Using CFEngine there are many ways to group and classify your hosts. In order to group their hosts, our users use a combination of JSON files, CFEngine policy language (with variables, classes, and class expressions), host specific data and host filters in Mission Portal. With these features you can choose which hosts to show in reports, and you can make decisions on what changes to make on which hosts.
Maximizing Uptime and Security: Best Practices for AWS and Azure IAAS
Cloud computing has become an essential tool for businesses looking to increase efficiency, reduce costs, and improve reliability. Among the most popular cloud providers, Amazon Web Services (AWS) and Microsoft Azure are two of the leading players in the industry. Both AWS and Azure offer Infrastructure as a Service (IaaS) solutions that allow businesses to host and manage virtual machines in the cloud.
Adopt open source securely from bare metal to cloud
Torq Poaches Splunk's Josh Morris as New SVP of Worldwide Sales and Taps Chief Marketing Officer Don Jeter From Pax8
Torq further accelerates growth and global expansion with world-class hires as broader tech sector struggles with revenue declines and layoffs New York, NY, February 13, 2023—Torq, the security automation leader, today announced the addition of new Senior Vice-President of Worldwide Sales Josh Morris and Chief Marketing Officer Don Jeter to its executive team.
What is Secure Access Service Edge (SASE)?
Check Point’s 2022 Workforce Security Report states that more than half of the workforce works remotely in 57% of organizations. The increase in the number of employees that work from home brings up new security implications that on-premise IT environments didn’t have to worry about. As organizations continue to undergo digital transformation, the existing network and network security architectures no longer meet the needs of the current digital era.
Future Cybersecurity Attacks Predicted to Cost 10x More Than Natural Disasters
Enterprises are entering 2023 following an increase in large-scale cybersecurity attacks over the last several years — Colonial Pipeline, Solarwinds, and even Twitter have all been victims — but events like these are not just increasing in number and sophistication. The amount of money involved is enough to make your head spin.
RapidSpike Synthetic User Journeys
The Importance of CVE & CVSS Scores
As we move into the new year, organizations can expect the number of cyberattacks to increase significantly. In order to battle these upcoming threats, effective patching and patch management processes will be essential. Before patching vulnerabilities, there are two main vulnerability assessments that IT teams should focus on: CVE & CVSS scores. Below, we’ll examine the importance of CVE & CVSS scores along with some of their uses and benefits in the cybersecurity space.
Open source security: best practices for early detection & risk mitigation
The ultimate guide to scanning Kubernetes workloads using Trivy-Operator
Testing is a vital aspect of security. Unfortunately, there are vulnerabilities that bypass the testing stage and introduce flaws in the production environment. Kubernetes vulnerabilities make more impact when exploited on running applications and production environments. These vulnerabilities can allow hackers to exploit the host machine if the container has escalated privileges.
How to Ensure SCCM Client Compliance on All Endpoints with Nexthink
SCCM is one of the most business-critical applications—a must have on all the devices. Administrators use SCCM for endpoint protection, software distribution, and patch management. Any machine where the SCCM client is not functioning will be unable to receive necessary policies or application updates, which can create a significant vulnerability for your organization because this leads to compliance and security issues.
What is Network Detection and Response and How Does it Work?
For the sake of security, performance and uptime, IT pros must find problems on the network immediately and fix them fast. Hmm. Sound like network detection and response (NDR)? It is.
Manage your Cloud Security Posture with Spot Security
Observing and Securing the Supercloud
The supercloud concept promises fewer accidental architectures and more cohesive cloud deployments with better manageability. Delivering on this vision requires a mix of vendor-agnostic tooling for performance monitoring and securing data.
Is open-source as secure as proprietary software?
We’re surrounded by news of data breaches and companies being compromised, and the existential threat of ransomware hangs over just about every organisation that uses computers. One of the consequences is that we are hassled by an ever-increasing number of software updates, from phones and computers to vacuum cleaners and cars; download this, restart that, install the updates.
Mitigate cyberthreats automatically with AIOps
The majority (83%) of employees across industries want their jobs to remain hybrid, Accenture reports. Yet nearly 50% of CIOs feel their cybersecurity initiatives aren’t keeping pace with their digital transformation efforts, according to research by ServiceNow and ThoughtLab. Neither are their cybersecurity budgets. Combining artificial intelligence (AI) and machine learning (ML) for IT operations (AIOps) can help.
SAST vs. DAST
Neglecting security is a rookie mistake. However, DevOps teams struggle to make it a priority in the quest to be continuously faster. Protecting your app from the ground up is challenging, so you need the right tools to improve your debugging process in development and production. To enhance security testing, developers can use SAST tools, which analyze program source code to identify security vulnerabilities, and DAST tools, which come up in later development phases in a running application.
Cisco introduces full-stack observability enhancement: Business Risk Observability
NOW AVAILABLE through Cisco Secure Application, on the Cisco AppDynamics SaaS platform, new security capabilities combine attack mapping and a business risk score for business transactions to help organizations prioritize responses based on likely impact on the business and users.
How Parallel Loop Empowers Torq Users to Rapidly Automate Bulk Data Processing Up to 10x
Torq is proud to introduce Parallel Loop, a new capability that enables users to process bulk data from myriad security tools with unprecedented ease. It also provides the power of orchestration like no other automation tool in the security automation industry with true parallelism. That means multiple tasks can be run simultaneously, and optionally, on multiple elastically-scaled compute resources, shortening the time workflow automations take to complete by 10x or more.
Using SOC-as-a-Service to Bridge the Cybersecurity Talent Gap
As the cyberthreat landscape is getting more sophisticated, the need for skilled cybersecurity professionals is also rising. The recent 2022 (ISC)2 Cybersecurity Workforce Study revealed that, in the past year, the cybersecurity workforce gap (the difference between the number of security professionals required and the number of suitably qualified people in the marketplace) has grown more than twice as much as the number of actual cybersecurity workforce hired, with a 26.2% year-on-year increase.
New CircleCI features for secure secrets management
When security incidents happen, it’s crucial for software providers and users alike to take swift and effective action. In response to our recent security incident, we witnessed firsthand how an open and collaborative effort between our customers, technology partners, and engineering teams helped to contain the threat and mitigate risk of unauthorized access to customer systems.
IT Security Checklist to Protect Your Business
During the COVID-19 Pandemic, it was reported that cybercrime increased by 600%. As the world has become more reliant on technology, whether for personal life or for business, cyberattacks have risen with it. Unfortunately, there are a lot of cybersecurity misconceptions that prevent businesses from adequately preparing for and responding to these attacks. More time and resources need to be spent protecting this critical information.
High throughput Kubernetes cluster networking with the Calico/VPP dataplane and accelerated memif
This blog will cover what the Calico/VPP dataplane is and demonstrate the performance and flexibility advantages of using the VPP dataplane through a benchmarking setup. By the end of this blog post, you will have a clear understanding of how Calico/VPP dataplane, with the help of DPDK and accelerated memif interfaces, can provide high throughput and low-latency Kubernetes cluster networking for your environment.
Secure Remote Access Software: Everything You Need to Know
Restoring Microsoft 365 data with Cove Data Protection
Use Cases for Black Screen Mode: When Privacy Matters
The advent of the modern MDM has given organizations unprecedented agility when it comes to their remote support. Instead of deploying engineers to fix hardware devices on-site as they did before, they can now troubleshoot and fix them entirely remotely. While this kind of remote support provides exponential value to organizations and their employees and customers, it also presents another major challenge: privacy.
Cyber Resilience: The Key to Security in an Unpredictable World
Protect Data from Ransomware with Flowmon & Superna
Demo Den: Open DevOps, Security in Jira (Feb 2023)
Integrate CircleCI with HashiCorp Vault using OIDC
Well-designed secrets management is a delicate balancing act between security and usability. Secrets must be easily accessible to the right users when building and deploying, but they must also at the same time be well-secured and easy to rotate. This article will cover how to thread this needle by integrating CircleCI with HashiCorp Vault and retrieving secrets using short-lived OpenID Connect (OIDC) authentication tokens.
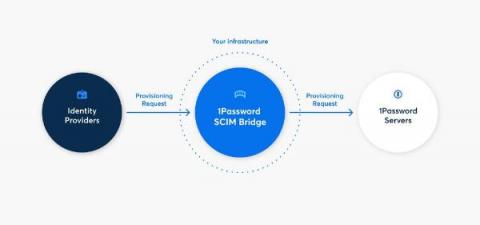
How 1Password Relies on Checkly for Secure System Health Monitoring for Thousands of Business Customers
1Password uses Checkly to provide transparent, advanced synthetic monitoring to 1Password SCIM bridge customers 1Password is a leader in human-centric security and privacy, with a solution that’s built from the ground up to enable anyone—no matter the level of technical proficiency—to navigate the digital world without fear or friction when logging in.
Be ransomware ready with cloud-first DPaaS
Did you know that your choice of a data protection solution can not only help you recover from cyber-attacks, but can also reduce your vulnerability to those attacks? By storing your primary backups safely off the local network, and choosing a remotely hosted SaaS data protection application, two critical attack vectors will be safely out of the reach of ransomware.