Operations | Monitoring | ITSM | DevOps | Cloud
January 2024
What is SAML and How Does It Work?
Ivanti Neurons for MDM: Protecting Samsung Devices from Phishing #shorts
Secure your stack with Ubuntu
Major Hospital System Cuts Azure Sentinel Costs by Over 50% with Observo.ai
Are Multi-Cloud Environments Getting Denser in 2024?
Announcing the Mattermost Trustcenter
The Risks of Using Piracy Websites Like Moviesflix
Maintaining Security with DevOps Compliance
Securing the Future: The Critical Role of Endpoint Telemetry in Cybersecurity
Meeting the SEC's New Cybersecurity Rules: How Flowmon Empowers Companies to Comply
CFEngine: The agent is in 33 - Celebrating 30 years w/ Mark Burgess
7 Best VPN Services for 2024
How to build DevOps automations with Kosli Actions
Understanding RBVM & Application Security Orchestration & Correlation
Best Tools for Preventing and Detecting Cyber Attacks
Best Service Delivery Management Software for 2024
Puppet Extends Compliance Enforcement to Support Open-Source Puppet Users in Meeting CIS Benchmarks
Revealing Suspicious VPN Activity with Anomaly Detection
Innovators Preview: Security Enhancements and Upcoming Events
Innovators Preview: Exploring New Features and Enhancements in UEM
Cybersecurity 101: Everything You Need to Know
What is a Compliance Audit? Definition & Importance
How to view firmware vulnerabilities in Site24x7's NCM tool
How to Deal with a Truck Accident - Aftermath of Truck Wreck
N-able Advances Security Suite with N-able Managed Detection and Response
The Impact of Technology on Modern-Day Legal Practice
GDPR Compliance in 2024
Elevating App Security with Amazon VPC Strategies
Continuous Compliance Content Hub
The Continuous Compliance content hub is a set of guides for DevOps teams who need to move fast while remaining in compliance for audit and security purposes. We know that the old change management processes for software releases that happened once every 6 months don’t scale for DevOps teams who want to deploy every day. This is where Continuous Compliance comes in.
DevOps Change Management Resources
Enhancing Corporate IT Security with Advanced Endpoint Solutions
Does Anonymous Web Hosting Really Make You Anonymous?
6 Tips for Promoting Safety on the Job
Understanding ISO27001 Security - and why DevOps teams choose Kosli
Modern software delivery teams find themselves under constant pressure to maintain security and compliance without slowing down the speed of development. This usually means that they have to find a way of using automation to ensure robust governance processes that can adapt to evolving cyber threats and new regulatory requirements.
A Guide to Continuous Security Monitoring Tools for DevOps
DevOps has accelerated the delivery of software, but it has also made it more difficult to stay on top of compliance issues and security threats. When applications, environments and infrastructure are constantly changing it becomes increasingly difficult to maintain a handle on compliance and security. For fast-moving teams, real time security monitoring has become essential for quickly identifying risky changes so they can be remediated before they result in security failure.
Cove Data Protection: The Guided Tour
Hacking in 2024: What to Watch Out For!
SAML vs. SSO: What's the Difference?
The landscape of modern authentication and authorization in IT systems has evolved significantly over the years. Initially, systems relied on basic password-based mechanisms, which gradually gave way to more sophisticated methods as security demands escalated. The advent of digital certificates and biometric verification marked a significant leap, offering enhanced security.
What Is NIS2?
To better protect its residents, organizations, and institutions, the European Union (EU) has strengthened its stance on cybersecurity with the introduction of NIS2 —the newly upgraded Network and Information Security Directive. This legislative framework is a response to the evolving cyber threats that show no sign of abating. In this article, we demystify NIS2 and share how it’s being used to establish a strong, unified cybersecurity framework across the EU.
Protect Against Netscaler Vulnerability CitrixBleed
How We Leveraged the Honeycomb Network Agent for Kubernetes to Remediate Our IMDS Security Finding
Picture this: It’s 2 p.m. and you’re sipping on coffee, happily chugging away at your daily routine work. The security team shoots you a message saying the latest pentest or security scan found an issue that needs quick remediation. On the surface, that’s not a problem and can be considered somewhat routine, given the pace of new CVEs coming out. But what if you look at your tooling and find it lacking when you start remediating the issue?
Cybersecurity & Compliance: What the Board needs to know and needs to ask
Vigilance and awareness are critical for compliance and cybersecurity maturity. If board members are not familiar with the key indicators of success for maintaining a resilient business and meeting compliance requirements, they are not fulfilling all their responsibilities. Board members need to understand the principles of their duties to alleviate potential exposure to cyber risk and other outage causing events that could harm the organization’s revenue, and reputation.
Navigating AI in SOC
With notable advancements in Artificial Intelligence (AI) within cybersecurity, the prospect of a fully automated Security Operations Center (SOC) driven by AI is no longer a distant notion. This paradigm shift not only promises accelerated incident response times and a limited blast radius but also transforms the perception of cybersecurity from a deterrent to that of an innovation enabler.
Cyber Security - The Beacon of Trust
As John Lennon once said, another year over…and a new one just begun. As we head into 2024, it’s important to reflect on what we’ve seen and where we need to focus in the year ahead.
Privacy by default
While companies tout the importance of user privacy, few put their money where their mouth is – or in our case, actually live and breathe the concept the way we do as a company. From how we think about our Product to the way we implement our Marketing, Sentry’s take on privacy is rooted in three key fundamentals: Don’t make me choose, think like your customer, and build for tomorrow today.
Detect Ransomware with Flowmon
Unveiling Red Teaming Services
Why Spyware Detectors are Essential in Today's Cyber Environment
Understanding Computer Programs and Copyright Protection
4 GRC Automation Ideas to Protect Your Organization
Cisco Secure Application: Fulfilling the APM + ASM promise for OpenTelemetry
Cisco AppDynamics is making big strides in enabling both application performance and security monitoring for OpenTelemetry. Learn what we’ve done so far. When DevOps began taking hold around 2007, it was meant as a mechanism to remove silos between IT teams and accelerate software development.
Building a Secure OpenTelemetry Collector
The OpenTelemetry Collector is a core part of telemetry pipelines, which makes it one of the parts of your infrastructure that must be as secure as possible. The general advice from the OpenTelemetry teams is to build a custom Collector executable instead of using the supplied ones when you’re using it in a production scenario. However, that isn’t an easy task, and that prompted me to build something.
Why Is Cybersecurity Consulting Important?
5 Cutting-Edge Technologies Transforming Prisons Today
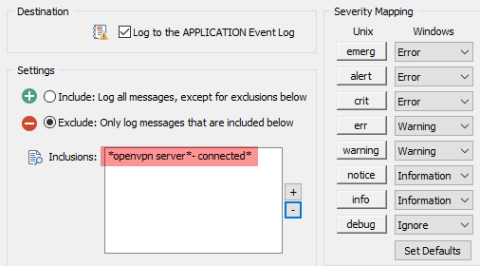
EventSentry Troubleshooting: Managing Database Size
How to Remove Trojan Viruses and Prevent Them in the Future
As subtle as they are dangerous, Trojan horses (or just “Trojans”) masquerade as benign software only to unleash havoc once inside your computer. Despite their stealthy nature, there are specific strategies you can employ to safeguard your digital assets from these threats. Below, we’ll discuss how to recognize the signs of a Trojan infection, steps for removing Trojan viruses from your devices, and how to reduce the risk of future infiltrations.
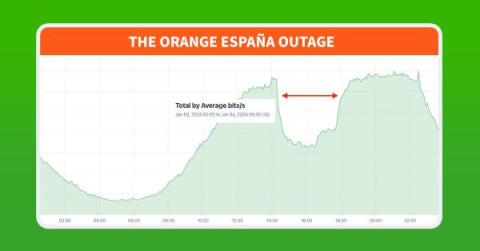
Digging into the Orange España Hack
Orange España, Spain’s second largest mobile operator, suffered a major outage on January 3, 2024. The outage was unprecedented due to the use of RPKI, a mechanism designed to protect internet routing security, as a tool for denial of service. In this post, we dig into the outage and the unique manipulation of RPKI.
Modernizing Financial Services with Automated, Proactive Threat Management
There’s a rising and intensifying pressure on financial services institutions that aligns with the demand for modernization, down to the core. It comes from laws like those of the Service Organization Control Type 2 (SOC 2) and the General Data Protection Regulation (GDRP), which enforce the need to build and hold down cybersecurity policies.
Navigating the Transition to Secure Texting
Recently, I stumbled upon an eye-opening NPR podcast that delved into the lingering use of pagers in healthcare—a seemingly outdated technology that continues to drive communication in hospitals. As I listened through the debate around its persistence, discussing challenges and unexpected benefits, it prompted reflections on facilitating a seamless shift to secure phone-app-based texting, acknowledging the considerable advantages it brings.