Operations | Monitoring | ITSM | DevOps | Cloud
October 2023
Cybersecurity Awareness Month: A Discussion About Cloud Security And AI
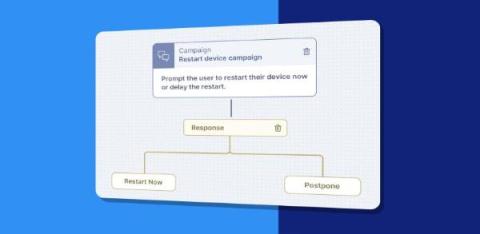
Manage and defend your IT estate like never before with Ivanti Neurons for ITSM
Modernizing ITSM with ITIL 4: Service value system
Demonstrating value is crucial to the success of any business. That's why it’s an important topic for IT service management (ITSM) service providers to consider when evaluating their service operations. How do IT service operations align with business outcomes and customer needs? How do operational metrics correlate to business value that stakeholders want to see?
Top 6 Benefits of AIOps You Must Know
AIOps — a term coined by Gartner back in 2017 has emerged as one of the hottest talking points in the realm of ITOps. Since its inception, its adoption by large enterprises has gone up from 5% to 30% in 2023. This impressive 6X growth is a clear indicator that AIOps is here to transform how businesses manage their IT operations. But what is it that makes AIOps special? What are the benefits of AIOps that businesses are looking to leverage.
Collective IQ included in the Gartner Market Guide for DEX Tools 2023
It is with great pride that we received the news that Almaden has been included in the Gartner Market Guide for DEX Tools 2023! If you are a Gartner subscriber the direct link to the research document is: Market Guide for DEX Tools.
What is Shadow IT - And How to Detect it?
Keysight Technologies: Automating Device Updates with Flow
Recently, Brandon Woods of Keysight Technologies shared two workflows that his team was able to implement with Nexthink Flow – allowing them to save time by solve problems more quickly and without human intervention.
Zero-Trust Security: Best Practices for Securing the Remote Workforce
Building an Equipment Checkout System With InvGate Insight
Simplify your back-to-school inventory management
New school year, same problem: outdated inventory management that doesn’t make the storekeeper’s job any easier. Keeping track of thousands of assets with Excel, library software (SIGB) or, worse still, by hand is a real ordeal… which could easily be avoided. Material tracking and loan management shouldn’t be cumbersome, time-consuming tasks that encroach on all your other projects. Not to mention that using old, manual methods predisposes you to wasted time and mistakes.
Security Webinar, Zero Trust For Users
Detect Shadow IT And Keep Unauthorized Assets Under Control
UEM vs. MDM: Everything You Need to Know!
Microsoft's release of Windows 10 modernized how IT teams approach device management. Windows 10 is not a strict evolution of Windows 7 and 8. It’s an evolution of Windows Phone 8 and 10, where an MDM API was available to manage all aspects of a device, such as DLP, restrictions, software distribution and so on.
What Is ITSM? IT Service Management Explained
Unable to accurately measure IT success? Watch out for these 7 KPIs
Innovators Preview - What's New in Ivanti Neurons 2023.4
Death, Taxes and Phishing - Cybersecurity Research Results (Pt. 1) | Ep.33 Security Insights Podcast
Understanding the ServiceNow CMDB - and how AIOps modernizes it
Navigating the complex world of ServiceNow’s Configuration Management Database (CMDB) can feel overwhelming. You might find yourself grappling with understanding the foundational aspects of the CMDB, or maybe you’re seeking effective ways to utilize and integrate it seamlessly into your IT processes. You want to extract the maximum value from your ServiceNow CMDB but need help figuring out how to start.
Importance of Network Monitoring
In today’s fast-paced digital world, the importance of network monitoring is growing by leaps and bounds. With real-time network monitoring, businesses can transform their user experiences and drive unstoppable growth. Whether you run a small business or a large corporation, incorporating network monitoring tools can help in the smooth functioning of your networks. Join us as we unveil the top benefits of network monitoring in the modern business landscape.
Secure UEM Solution Packages in 187 seconds
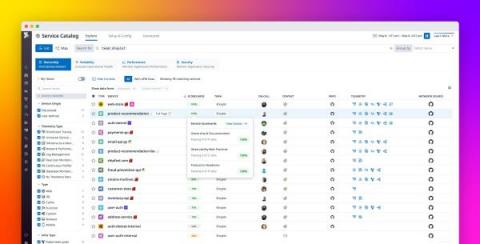
Prioritize and promote service observability best practices with Service Scorecards
The Datadog Service Catalog consolidates knowledge of your organization’s services and shows you information about their performance, reliability, and ownership in a central location. The Service Catalog now includes Service Scorecards, which inform service owners, SREs, and other stakeholders throughout your organization of any gaps in observability or deviations from reliability best practices.
Spending Intelligence 2023.3 Teaser
How to Use ITAM Software as Your Equipment Check-Out System? [Video Tutorial]
ServiceNow Privacy Management Overview
Micro Product Demo: Ivanti Neurons for Spend Intelligence in 135 seconds
Anti-theft markings: everything you need to know
Many companies use anti-theft labels to prevent theft and protect assets. These tags are attached to objects to alert security personnel or staff to an attempted theft. What other advantages do anti-theft tags offer? And how do they work?
Planning for the unexpected with business continuity management
As a major retailer with more than 1,700 outlets, Canadian Tire needs robust business processes that continue to operate seamlessly when adverse events strike. Although the company had disaster recovery plans in IT and an established business impact analysis discipline in its business units, these processes ran on Microsoft Excel, Word, and emails—and weren’t connected.
Platform Engineering - Paving the Way to Accelerate Eeleases
On-Trend in Operations This Peak Season
Here we are, back again to another calendar fourth quarter and maybe the same for your business. But whether your fiscal calendar lines up or not, it is that most wonderful time of year we all know as peak season. Each year's a little different, especially lately. But rather than re-hash what we have all lived through leading up to this season, it feels right to have a look at what operations — maybe yours included, are doing to make peak season 2023 a success.
Ivanti Neurons for HR
How To Optimize Your Consulting Workflow
How Hackers Use Unexpected Skills
Patch Management vs. Vulnerability Management: What's The Difference?
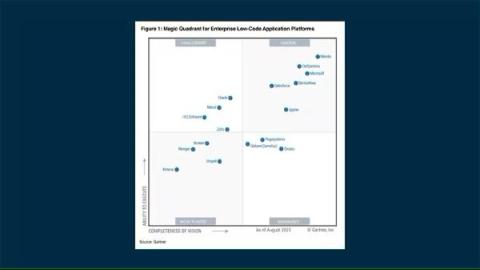
ServiceNow is a Magic Quadrant Leader for Low-Code for the fourth year
I’m delighted to announce that, for the fourth consecutive year, ServiceNow has been recognized as a Leader in the 2023 Gartner® Magic Quadrant™ for Enterprise Low-Code Application Platforms. We believe this recognition reflects our continued commitment to helping our customers eliminate the skills gap for app creation with low-code tooling.
The art and science of bridging the goals of IT teams and customer success teams
How to Get Equipment Back from a Terminated Employee: No Lasso Needed
Returning devices is more challenging in terms of effort while allowing employees to keep them puts data at risk. Is there an optimal solution? Let’s dive deeper and find out.
ServiceNow Integration
Demo ITSM 10-Minute Intro
The red team: ServiceNow's first line of defense
If you ask any ServiceNow employee about their role, they'll likely tell you their job and team are the best they’ve ever had. One small but mighty team proclaims this proudly: the red team, a group of professional hackers. As vigilant guardians of the company, the six-person team is tasked with testing the security of our systems and identifying cyber risks, data vulnerabilities, and security threats.
5 principles of great experiences
Product experience is a key driver of business success for ServiceNow and our customers. That’s why my product experience team and I spend a lot of time focusing on design principles that help ensure we exceed our customers' expectations. You don’t have to be a designer to use these principles and create great experiences. These are fundamentals that anyone can put into practice.
Vendor Risk Management 101-The Imminent Threat of IoT Litter Boxes | Ep.32 Security Insights Podcast
Elevate Your Teamwork in 2023: Dive into Collaborative Work Management! Infraon
Mastering SaaS License Management: A Comprehensive Guide | Infraon
Project and Portfolio Management with ITSM
How do you manage a fleet of measuring instruments?
Measuring instruments are indispensable tools in many fields. However, they require regular management and maintenance to ensure their reliability. Find out now how to look after your measuring instruments efficiently.
AI will empower app developers-not replace them
Despite the rise of AI, the need for app developers isn’t going away. In fact, a 2023 ServiceNow-sponsored study by Pearson suggests approximately 95,000 new application developer roles will be added globally over the next five years. According to ServiceNow’s special report on the impact of AI on tech skills, based on the research, only about 20% of app developer tasks will be either automated or augmented by 2027.
DEX Show Live from London: The Future Workplace
Velocity Digital Forms - Explainer Video
The Future of Database Monitoring - AIOps
Cloud Package Creation with Ivanti Neurons for UEM
4 ways innovative companies can navigate digital transformation
From the tight global labor market to social and political volatility, macroeconomic headwinds continue to hamper business growth. Such a complex environment is anything but smooth. Your organization may be feeling pressure to deliver on initiatives to support talent, products and services, and business operations. Finding success in these areas requires digital transformation. Innovative companies are best positioned to prosper and thrive.
Alloy Navigator 2023.2 is Coming: What's in Store?
Unveiling the exciting new features in the upcoming release of Alloy Navigator, the all-in-one ITSM/ITAM solution.
Unlock the power of the Cloud with App Distribution in Ivanti Neurons for UEM
What is ITOM? IT Operations Management Definition, Benefits, And Best Practices
AI for Customer Support and Why You Need It
Providing exceptional customer support has become a key differentiator for businesses. Customers expect quick and personalized solutions to their queries and issues. To meet these expectations, organizations are turning to Artificial Intelligence (AI) for customer support solutions. AI technologies, such as Generative AI, have revolutionized the way companies interact with their customers, streamlining support processes, and delivering superior customer experiences. In this comprehensive guide, we will explore the significance of AI for customer support, its various use cases, how to implement it, the role of Generative AI, and the barriers to overcome for its successful adoption.
A KDC/One senior system administrator shares why ADManager Plus blows his mind!
Phishing 2.0: Anyone lose a dog?
Nexthink Flow: 90 Second Demo
Learn more about Nexthink Flow: https://nexthink.com/platform/flow
How Nexthink Helps You See and Diagnose Issues at Scale
Digital Employee Experience is vital to attract and keep the best employees. A solid DEX strategy also increases employee productivity and motivation, a selling point for business leadership across the board. Yet, IT teams have less and less ability to control the factors that make up the digital employee experience. Although IT still own the devices, most of the network and applications are managed by third-party vendors.
Employee onboarding for better engagement and retention from Day 1
Only 52% of workers felt satisfied with their latest employee onboarding experience, according to a Paychex survey. That means just under half of new hires are dissatisfied and feel unprepared to start their new jobs. Nearly 40% of survey respondents found onboarding clear, 32% said it was confusing, and 22% said it was disorganized. Four out of five (80%) new hires who feel undertrained due to poor onboarding plan to quit. Poor onboarding experiences aren’t new for HR teams.
IT vs Security - When Hackers Patch for Profit | Ep.31 Security Insights Podcasts
Micro Product Demo: Ivanti Neurons for Patch Management
Practical Demo: Protect all endpoints with secure UEM countermeasures
SQL Sentry Then and Now Part 2
3 ways to enhance digital experiences and productivity
Digital transformation is critical to enabling organizational change. In fact, 85% of CEOs recognize that digital capabilities are a strategic business differentiator and vital for accelerating revenue growth, according to IDC. IT leaders play a central role in business strategy. They’re asked to deliver digital capabilities to enhance organizational speed, agility, and innovation that leads to change and growth.
Taking the Work Out of Workflows with Nexthink Flow's Low Code Visual Designer
How automated are your automations? You (or your expert engineers) are probably spending hours on complicated PowerShell coding – writing, testing, reviewing, signing, and updating. What if there were a better way to coordinate your automations with workflows? Orchestrate multi-layer automated detection, communication, integration, and action.
Introducing Nexthink Flow
Today, we announce a revolutionary new product that will put an end to recurring, complex IT issues and deliver continuous engineering with full scale, start-to-finish automation for EUC teams.
3 Nexthink Flow Integrations to Help You Automate Anything, Anywhere
Nexthink’s ability to integrate with anything has long been one of the most popular aspects of our products. From your ITSM tool to Azure AD, Nexthink data can be connected across your environment – so you can act on Nexthink insights to build the best possible digital employee experience. Nexthink Flow continues our dedication to integrations by allowing for the sharing of data and actions in both directions for several key integrations.
5 of Our Favorite Use Cases for Nexthink Flow
Automation and orchestration present huge opportunities for business efficiency, time optimization, and cost savings. With Nexthink Flow, EUC teams now have the power to orchestrate full end-to-end automations that eliminate repetitive manual work and drive employee productivity. But with so many opportunities at your fingertips, it can be hard to know where to begin. Flow is a powerful orchestration engine, with incredible flexibility designed to fit diverse business needs.
Zero Trust - An Analyst's 10-Minute Perspective
Introducing Nexthink Flow: IT Orchestration for Efficient IT
What is Infrastructure Monitoring : Comprehensive Guide
Tired of being a firefighter in your IT department who is always battling issues after they erupt? Well, you’re not the only one. With IT infrastructure becoming more complex day by day, IT managers across the globe face the same challenge. But not anymore. Infrastructure monitoring tools are here to save the day by empowering IT managers to not only predict but also prevent IT infrastructure issues. But how?
The benefits of medical asset management
Here are 4 reasons why effective medical material management can improve your services while delivering improved patient care.
3 ways to maximize efficiency with hyperautomation
Efficiency is the bedrock of success for any organization. In the continuous pursuit of streamlined operations and increased productivity, ServiceNow Automation Engine serves as a valuable asset, enabling ServiceNow platform owners and automation leaders to quickly and cost-effectively connect or automate any system, document, or task with minimal code.
Best GRC Software Options For 2024
Protect Your Mobiles with MDM
Deter Phishing Attacks
Stefan Kempter on What is YaSM, Yet Another Service Management Model
S2E3: Implementing visual life cycles and workflows in ServiceDesk Plus - Masterclass 2023
S2E3: Utilizing visual life cycles and workflows to standardize ITSM practices - Masterclass 2023
How to Identify Your Organization's Attack Surface
Our glossary page on attack surfaces defined the terms associated with the concept. This post provides information that'll help your organization identify its attack surface. Much like your lawn after a good rain, your attack surface will grow rapidly if left unchecked. Along with increases in attack surface size comes an increase in cybersecurity risk. That risk can’t be eliminated as attack surfaces are always evolving, but it must be carefully managed.
What's New With InvGate: October Updates
Enhance Your Customer Service with PagerDuty for ServiceNow CSM
In today’s fast-paced, digital-first landscape, delivering exceptional customer experience is paramount to business success. For customer service teams, that means maintaining service level agreements (SLAs) and ensuring swift responses to customer issues that can make or break your company’s reputation. Fortunately, PagerDuty has improved the way companies handle customer service teams and has built applications into ServiceNow’s CSM platform.
Guide to ITIL Root Cause Analysis (RCA)
Step into the nerve center of IT service management (ITSM): root cause analysis (RCA). This isn’t just another process—it’s the key to unlocking effective and efficient IT service. As an IT professional, this is where your expertise comes to the forefront. Let’s dive into the mechanics.
Planning and measuring digital employee experience - DEX, short clip
When should you upgrade to a CMBD
Which Gen Is Most Tech-Savvy? A Workforce Dilemma
Part one of a four-part series covering Ivanti’s latest research. Get the full series: According to new cybersecurity research by Ivanti, the employees who are the most tech-savvy aren’t necessarily the ones we’d presume, demographically speaking. Why is that? And what are the issues it creates for an enterprise?
Red Flag Reluctance: The Risk to Cybersecurity
Part two of a four-part series covering Ivanti’s latest research. Get the full series: Keeping an organization safe means getting near-real-time information about security incidents or breaches. But new research shows some employees are less inclined than others to report red flags, which puts your business at risk. Will your employees get in touch quickly if they have a security concern?
International Inconsistencies: How Cybersecurity Preparedness Varies Across Countries
Part three of a four-part series covering Ivanti’s latest research. Get the full series: An organization’s culture and training programs have a significant influence on security preparedness, but our research shows both are inconsistent at the country-to-country level. As we’ve seen in the previous posts in this series, employee demographics and their willingness to report security risks are hidden threats to your cybersecurity posture.
Taking a Real Look at Hidden Risk
Part four of a four-part series covering Ivanti’s latest research. Get the full series: Big-picture excellence can hide pockets of risk. It’s time to explore security risk in detail — drilling down to look at vulnerabilities hidden in the data and by taking preventative action.
Demo ITSM & ITAM The Powerful Duo
The Ins And Outs of Software Compliance
Double Down on Your Backups
Proactively improve your DEX
Fighting the Good Fight for a Resilient Digital Future
This Cybersecurity Awareness Month, cybercriminals have far too much to celebrate. Attacks are rising in sophistication and brazenness, and no company or organization is immune. We could panic. Or we could lock arms, fight the good fight and put customers first. I vote for the latter.