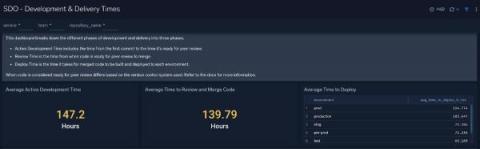
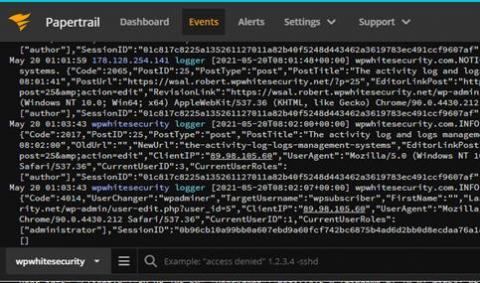
Latest Release of Our Network Monitoring Software Delivers AI-Driven Log Analytics
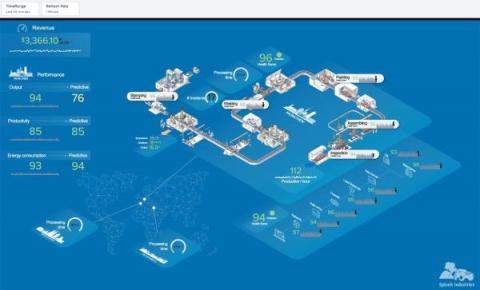
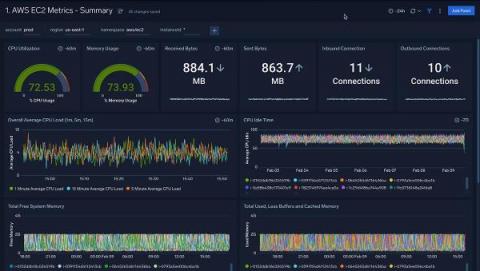
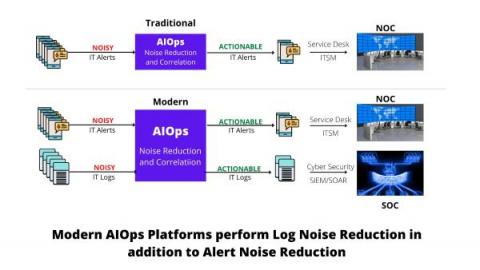
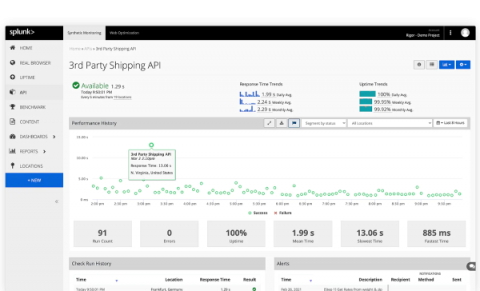
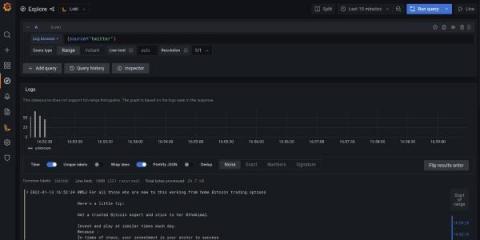
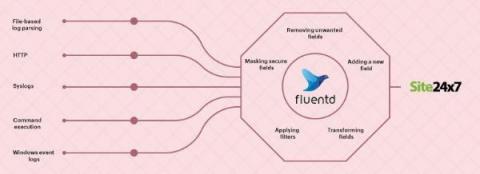
If you manage a network, every network device generates a large volume of logs. These logs are extremely important and narrate a story about both events and the sequencing of those events within your network. This capability is critical for any network monitoring software, helping you easily understand network activities, user actions, security breaches, and much more.