Open source log management tools in 2024
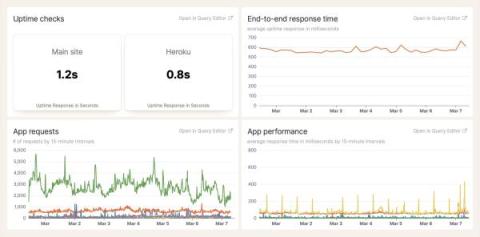
Log management tools provide visibility into the performance and behavior of systems, applications, networks, and infrastructure components. By collecting and analyzing logs, you can monitor for anomalies, track trends, and identify potential issues before they escalate. Choosing the right log management solution requires careful consideration of several factors to ensure that it meets your specific needs and goals. Here are the most popular open source log management tools to help you choose.