Operations | Monitoring | ITSM | DevOps | Cloud
April 2022
How to Ensure Microsoft Teams PSTN Connectivity and Monitor its Service Quality
VXLAN vs VLAN: a Definitive Guide
Avoid IT's Worst Nightmare by Monitoring Proactively - Not Reactively!
How to Ensure Microsoft Teams Voice Quality for VIPs
CDN Provider Performance Monitoring: Best CDNs in the UK
This blog continues our best CDN series. Today we will be analyzing content delivery network performance and uptime in the United Kingdom over the last seven and 30 days. Tip: Are you new to CDNs? Visit our What is a CDN resource to learn more.
4 steps to bring network observability into your organization
The vast majority of corporate IT departments have a network monitoring solution. Typically that solution is built on standalone software platforms. If that’s you, this post is for you. You’re probably hearing a lot about “observability” these days. Generally, that’s the ability to answer any question and explore unknown or unexpected problems to deliver great digital experiences to your users.
Optimizing Microsoft Teams PSTN for the Hybrid Workforce
Network Monitoring Safety Checklist-5 Steps to Take
Network monitoring is a vital part of your security architecture and layered security portfolio. Step one in your network monitoring safety checklist is making sure you have network monitoring in the first place. The rest of our steps assume you have network monitoring and lay out five ways to optimize its value.
The Great Resignation - What's at Stake for IT?
Roughly 47.4 million people quit their jobs and left the workforce last year in search of better ones, leading to what we now call the Great Resignation. Then, as the economy re-opened and companies intensified hiring efforts, millions of people switched careers, searching for better working conditions and higher salaries. Experts say the trend will continue as the Gen Z population reshapes the labor market.
How To Configure Flowmon and WhatsUp Gold
In the previous “Flowmon and WhatsUp Gold: Discover application experience issues through single pane of glass” blog post we have demonstrated how IT Infrastructure Monitoring (WhatsUp Gold) and Network Performance Monitoring & Diagnostics (Flowmon) work seamlessly together to report on application performance, user experience and infrastructure status.
Peering, edge computing, and community with Grant Kirkwood | Network AF Episode 16
Introducing OID Monitor History
Measuring RPKI ROV adoption with NetFlow
Resource Public Key Infrastructure (RPKI) is a routing security framework that provides a mechanism for validating the correct originating autonomous system (AS) and prefix length of a BGP route. Route Origin Authorization (ROA) is a cryptographically signed object within the RPKI that asserts the correct originating AS and prefix length of a BGP route. For as long as the internet has existed, the challenge of securing its underlying protocols has persisted.
SolarWinds IT Management and Monitoring for Government
How Network Monitoring Defuses Hacker Bombs
You know by now that hackers literally never sleep. Chances are your network has been hit before and absolutely will be hit again. Hackers invent new techniques every day and tweak existing ones, many of which are automated—which is why we can say that hackers literally never sleep. Hackers either attack your network directly or attack your infrastructure through your network. Either way, the network itself is your first line of defense.
Multi-Cloud Trends In The Banking And Finance Sector
The evolution of network visibility
In the old days, it took a bunch of help desk tickets for an engineer to realize there was something wrong with the network. At that time, troubleshooting meant logging into network devices one-by-one to pore over logs. In the late 80s, SNMP was introduced giving engineers a way to manage network devices remotely. It quickly became a way to also collect and manage information about devices. That was a big step forward, and it marked the beginning of network visibility as we know it today.
Advanced Traffic & Security Analysis in WhatsUp Gold with Progress Flowmon
Ribbon Partners with Microsoft to Enable Service Providers to Automate and Accelerate Microsoft Operator Connect Deployments
MYCOM OSI supports Amazon Elastic Kubernetes Service (Amazon EKS) for its suite of Service Assurance applications
What is Microsoft's New Operator Connect Accelerator?
One of the great things about being in the telecom industry is the constant innovation that occurs. For example, Microsoft just announced an exciting new offering for telecom service providers, Operator Connect Accelerator, aimed at helping them get the most out of their Teams investments. Operator Connect is Microsoft’s managed service for connecting Teams and telephony services.
The Role and Risks of Using Internet Control Message Protocol (ICMP)
With so many organizations focused on locking down environments, protocols like ICMP get immediately blocked without first weighing out the benefits.
Filling in the Gaps: Manufacturing and MSPs
CDN Provider Performance Monitoring: Best CDNs in India
This blog continues our best CDN series. Today we will be analyzing CDN performance and uptime in India over the last seven and 30 days. Tip: Are you new to CDNs? Visit our What is a CDN resource to learn more.
Importance of Networking Performance Monitoring Tools and How Infraon can Help
Types of Network Performance Monitoring Tools
DX Unified Infrastructure Management 20 4 Service Level Management
Teams Operator Connect FAQs
How to Monitor Network Speed | Obkio
Flowmon 12 - Workflows and UX Improvements
We released Flowmon 12 at the end of February. The new and updated functionality in the latest version has been well received by existing users, and has prompted many new organizations to consider the product. The headline changes in Flowmon 12 are in the blog post Progress Flowmon 12 – Ultimate Enabler of Your Multi-cloud Strategy.
Understanding data analysis and online activity with David Belson
Network Alerts-Monitoring and Notifications
When it comes to IT, you can’t do anything with an asset you can’t see. When it comes to your networking, monitoring offers the eyeballs to know what is going on. But IT and network pros don’t spend all day staring at a dashboard waiting for something to happen. Like your local police department, they rely on notifications of trouble. Instead of 911 calls, IT depends on network alerts.
Why Redundancy Should Be An Important Part Of Your Multi-Cloud Strategy
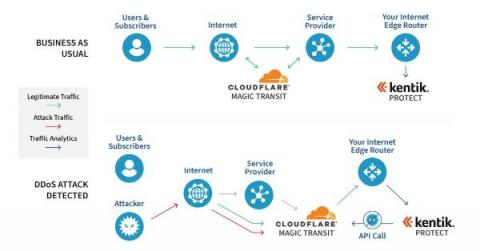
Working with Cloudflare to mitigate DDoS attacks
The rolling thunder of cybersecurity warnings has built to a crescendo this year. According to HelpNetSecurity, cybercriminals launched over 9.75 million DDoS attacks in 2022. The Cloudflare Attack Trends 2022 Q1 Report published yesterday shows an alarming increase in application-layer DDoS attacks. And our own Doug Madory has been sharing analysis on the impact of cyberattacks, too.
Rally Software for Enterprise Agile Management
What's New with Flowmon ADS 12 and outlook ahead?
Expert Series: Large MSP Was First to Upgrade to DX UIM 20.4
A NoSQL database provides a mechanism for data storage and retrieval, without using the tabular relations associated with relational databases. Originally referred to as "non-SQL" or "non-relational" databases, NoSQL databases are increasingly used in big data and real-time web application environments. NoSQL systems are also sometimes called “Not only SQL” to emphasize that they may support SQL-like query languages or sit alongside SQL databases in polyglot-persistent architectures.
NoSQL Database Monitoring with DX UIM
A NoSQL database provides a mechanism for data storage and retrieval, without using the tabular relations associated with relational databases. Originally referred to as "non-SQL" or "non-relational" databases, NoSQL databases are increasingly used in big data and real-time web application environments. NoSQL systems are also sometimes called “Not only SQL” to emphasize that they may support SQL-like query languages or sit alongside SQL databases in polyglot-persistent architectures.
Infovista launches Precision Drive Testing to automate 5G testing
What is remote network monitoring?
Remote network monitoring is a technical specialty that was born almost at the same time as networks themselves. Since then, many strategies have emerged when it comes to monitoring network elements. In this article we will talk about the current techniques based on SNMP polling and network statistic collection through Netflow, and we will also mention outdated systems such as RMON. Most techniques are purpose-oriented, so they are especially useful.
Network Nickels and Dimes: Government IT on a Budget
Bolster network monitoring with root cause analysis
If you own an enterprise, then you know the value of a healthy network and how seriously detrimental a network outage is to your business. But network issues are inevitable. The heavy dependence on networks to meet the ever-changing client and internal usage requirements takes a heavy toll on the network. This makes networks vulnerable to common problems such as unplanned, sudden downtime, high resource utilization, and hardware malfunctioning.
Welcome to the Auvik family, MetaGeek!
Modernizing Network Monitoring with InfluxDB and Telegraf
This article was originally published in The New Stack. As the technology landscape continues to change at a rapid pace, enterprise companies are in a rush to catch up and modernize their legacy IT and network infrastructure to capture the benefits of newly developed tools and best practices. By adopting modern DevOps techniques, they can reduce their operational costs, increase the reliability of their services and improve the overall speed and agility at which their IT teams are able to move.
Cilium network policy security tutorial on Civo
Achieve End-to-End Network Visibility for SASE
Network AF, Episode 13: Talking networking and PR with Ilissa Miller
In this episode of the Network AF podcast, Avi Freedman connects with Ilissa Miller, network whisperer and PR industry veteran. Ilissa and her team translate technology into business terms by helping clients understand the value and functionality of a company. Avi asks Ilissa how she got into the field, her biggest takeaways that helped launch her own business and what’s important in today’s networking world.
The Future of Monitoring: Turning Unknown Unknowns into Known Knowns
To ascertain risk, national security and intelligence professionals have long used concepts such as known knowns, known unknowns, and unknown unknowns. The idea of unknown unknowns was created in 1955 by American psychologists Joseph Luft (1916–2014) and Harrington Ingham (1916–1995). This concept continues to be used today in risk assessments and is applicable to technology. The unknown unknowns are the threats and potential problems that remain invisible until their impact manifests.
How to Measure VoIP Quality & MOS Score (Mean Opinion Score)
VoIP Quality is highly reliant on network performance, which means that many network problems like packet loss, latency, and jitter can cause high levels of VoIP degradation. To avoid embarrassing choppy voice calls, or lagginess during your next client meeting, we’re running you through how to measure VoIP Quality with MOS Score (Mean Opinion Score).
What Else But SNMP?
A practical guide to container networking
An important part of any Kubernetes cluster is the underlying containers. Containers are the workloads that your business relies on, what your customers engage with, and what shapes your networking infrastructure. Long story short, containers are arguably the soul of any containerized environment. One of the most popular open-source container orchestration systems, Kubernetes, has a modular architecture.
Network Monitoring Handbook: Your Complete Guide to Network Monitoring and Management
Why Build a Transport Network
What's New with Flowmon 12?
Do you know these IP Scanners?
Close your eyes. Imagine that, instead of being a good person reading this article at home, you are a newbie network administrator who must manage the IP addresses of thousands of devices networked on the extensive networks of a large company. At first you use your spreadsheet…, but it’s not enough!
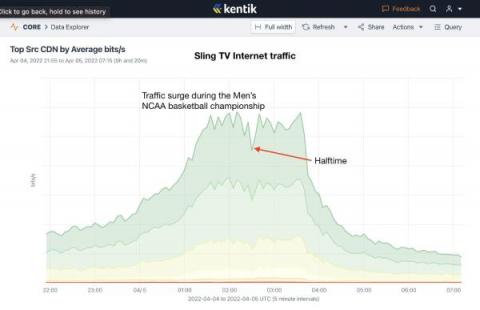
Anatomy of an OTT traffic surge: 2022 Men's NCAA Basketball Championship
Last night, Kansas topped the University of North Carolina in a thrilling come-from-behind victory to win their fourth championship in men’s college basketball. It was also notable in how viewers saw the game. Instead of being aired on CBS (network television), the game was carried on TBS requiring viewers to have either a cable TV package or use a streaming service to watch the game. Here’s what we saw.
Data Sovereignty: Everything You Need to Know
How to Import/Export Orion Custom HTML Widgets
How Network Vulnerabilities Can Impact Operational Resilience
Operational resilience remains the top priority for those in financial services. From the U.S. Federal Reserve's study into "Sound Practices to Strengthen Operational Resilience" and "Principles of Operational Resilience" from the Basel Committee to the Bank of England's upcoming rule changes for financial organizations in the UK, the intent is to create financial services institutions that are geared towards managing digital disruption. The goal is that financial service businesses can continue providing mission-critical services in the event of disruptions such as IT glitches, outages, and cyber-attacks.
Source-Side Queueing: You Down With UDP?
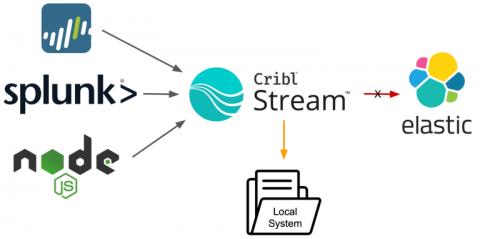
Source-side queueing is a fancy way of saying: You can configure Cribl products to make sure data isn’t lost in the event of downstream backpressure, again. Those familiar with Cribl Stream might be aware of destination queuing or persistent queuing, wherein Stream can write data to the local disk in the event of an issue reaching the destination. Maybe your SIEM is suffering from disk I/O latency. Maybe there is a DNS problem with your load balancer (Hint: It’s always DNS).
The Benefits Of A Data Centre Partnership With Console Connect
[Live Webinar] Achieving Multi-Datacenter High Availability with HAProxy ALOHA and GSLB
HAProxy ALOHA is a load balancer that’s ideal for companies in search of high performance and ease of use. It comes as either a hardware appliance or a virtual appliance and provides load balancing of TCP, UDP and HTTP traffic, DDoS protection, and active-active clustering. One of its newest features is the ability to distribute traffic across multiple datacenters or regions through global server load balancing(GSLB).
Calling all IT heroes
Monitoring your network traffic using Site24x7
April/2022 - CVE-2022-22965: Spring4Shell Remote Code Execution Mitigation
Recently, a Remote Code Execution vulnerability was discovered in the Java Spring Core library. This vulnerability allows attackers to execute arbitrary code on affected systems. You can find more information on that vulnerability in the announcement on the Spring Blog. While HAProxy Enterprise, HAProxy ALOHA, and other products within the HAProxy Technologies portfolio are not impacted by this (they do not use the Spring Core library at all), you can use our products to mitigate the attack.