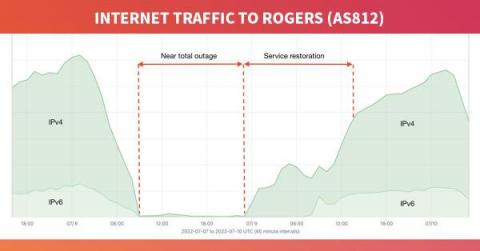
GigaOm, Again Names Broadcom Leader in Radar Report for Network Observability, 2022
Download your complimentary copy of the 2022 GigaOm Radar Report For Network Observability here. As the 2022 GigaOm Radar Report for Network Observability states, "Network observability is a category of platforms and tools that go beyond device-centric network monitoring to provide truly relevant, end-to-end visibility and intelligence for all the traffic in your network, whether on-premises, in the cloud, or anywhere else.".