Operations | Monitoring | ITSM | DevOps | Cloud
January 2021
How to implement CFEngine custom promise types in bash
This blog post will focus on the bash programming part of implementing a promise type. To understand what custom promise types are, and how to use them, you should read the introduction first.
Applying Strong Cyber Hygiene Security to IoT Endpoints
The Internet of Things, better known as IoT. You’ve heard of it, right? But do you know what it is? Simply, it is the interconnection of things (or endpoints) on the Internet to send and receive data. Today, experts calculate that there are 31 billion things connected to the insecure Internet, and growing exponentially. Did you know there are different types of IoT applications?
How We Use InfluxDB for Security Monitoring
At InfluxData, we believe it makes sense to use a time series database for security monitoring. In summary, it’s because security investigations are inevitably time-oriented — you want to monitor and alert on who accessed what, from where, at which time — and time series databases like InfluxDB are very efficient at querying the data necessary to do this.
How to detect sudo's CVE-2021-3156 using Falco
A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo. sudo is a powerful utility built in almost all Unix-like based OSes. This includes Linux distributions, like Ubuntu 20 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2). This popular tool allows users to run commands with other user privileges.
Coralogix - On-Demand Webinar: Outsmart the Hackers
Detecting the Sudo Baron Samedit Vulnerability and Attack
On January 26th, 2021, Qualys reported that many versions of SUDO (1.8.2 to 1.8.31p2 and 1.9.0 to 1.9.5p1) are vulnerable (CVE-2021-3156) to a buffer overflow attack dubbed Baron Samedit that can result in privilege escalations. Qualys was able to use this vulnerability to gain root on at least Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2), some of the most modern and widely used Linux operating systems.
InfluxData secures SOC 2 Type II certification for InfluxDB Cloud
SAN FRANCISCO — January 28, 2021 — InfluxData, creator of the time series database InfluxDB, today announced it has achieved Service Organization Control (SOC) 2 Type II compliance for InfluxDB Cloud, the fully managed and serverless time series platform. The certification demonstrates InfluxData’s ability to implement critical security policies and prove compliance over an extended period.
InfluxData is SOC 2 Certified
At InfluxData, we focus on our customers’ productivity — time to awesome, as we call it. Usually this is about product capabilities — InfluxDB’s features, speed, scalability, etc. But for some, your project will grow in size to the point where you need to purchase InfluxDB. And in some cases, you’ll need your compliance and/or security teams to sign off on the purchase.
7 Ways GroundWork Delivers Bulletproof Infrastructure Monitoring
Lately, security has become top of mind across infrastructure monitoring customers. This is no surprise considering the widespread reports about supply-chain vulnerabilities and embedded compromises rampant in popular network monitoring software. In light of this, we want to underscore how seriously we have always taken our security processes, and how we cultivate a culture based on a foundation of sound security protocols.
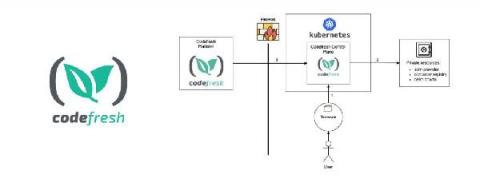
What Is Zero Trust & How Do We Implement It to Run Secure CI/CD Workflows in Kubernetes?
Zero trust is a security concept that is centered around the idea that organizations should never trust anyone or anything that does not originate from their domains. Organizations seeking zero trust automatically assume that any external services it commissions have security breaches and may leak sensitive information.
Datadog achieves FedRAMP Moderate Impact authorization
As government agencies accelerate migrating their operations to the cloud, they need to adhere to strict compliance and security standards. The Federal Risk and Authorization Management Program (FedRAMP) provides the standard that these agencies—and their private-sector partners—must meet to work and manage federal data safely in the cloud.
How to export and import Timelines and templates from Elastic Security
When performing critical security investigations and threat hunts using Elastic Security, the Timeline feature is always by your side as a workspace for investigations and threat hunting. Drilling down into an event is as simple as dragging and dropping to create the query you need to investigate an alert or event.
Code42 launches a new app in the Sumo Logic Open Source Partner Ecosystem
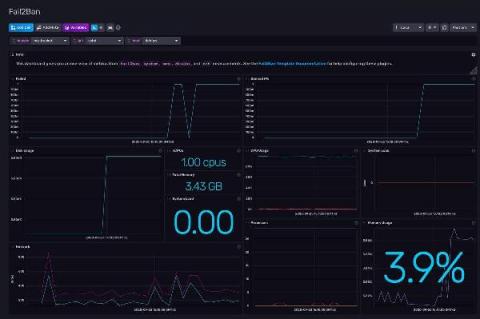
Fail2ban Monitoring with InfluxDB and Telegraf
If you have a server open to the internet on Port 22 (the default port for SSH servers), it’s common to find several “Failed password” in your auth.log (log file) every minute, due to bots constantly browsing the internet for servers that are easy to hack with common passwords. But if your auth.log is growing very fast and SSH daemon randomly refuses to create new connections, then someone probably marked your server as a target for coordinated SSH brute-force attack.
What's new in Sysdig - January 2021
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
Learn how to comply now before your next audit
Are you struggling to keep up with manual compliance across your infrastructure? In this 25-minute episode of the Pulling the Strings podcast, powered by Puppet, learn how Puppet Comply makes automating your configuration compliance easy -- with full view dashboards and the ability to assess, remediate and enforce all through the Puppet Enterprise solution. Listen in and discover:
How to set AWS S3 Bucket Read Permissions with Relay
Cloud environments are susceptible to security issues. A big contributor is misconfigured resources. Misconfigured S3 buckets are one example of a security risk that could expose your organization’s sensitive data to bad actors. Policies and regular enforcement of best practices are key to reducing this security risk. However, manually checking and enforcing security is time-consuming and can fall behind with all the demands a busy DevOps team faces every day.
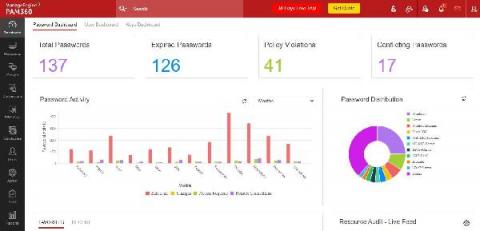
Why ManageEngine PAM360 is the ultimate privileged access management solution
At ManageEngine, we‘re building one of the most comprehensive and tightly integrated IT management software suites on the market. We have over 90 products and free tools to manage all your IT needs, including Active Directory management, help desk management, desktop and mobile device management, network and server management, application management, IT security, and analytics.
Secure Your Endpoints with Sophos & Logz.io
Intercept X is Sophos’ endpoint security solution, including anti-ransomware, zero-day exploit prevention, plus managed endpoint defense and response. It employs a layered approach reliant on multiple security techniques for endpoint detection and response (EDR). Those tactics include app lockdown, data loss prevention, web control and malware detection.
What the new WhatsApp Privacy Policy is all about and what it means for you
It was January 2007 when Steve Jobs officially announced the 1st Generation iPhone. At the time, there’s no doubt that he foresaw how the newly created concept of smartphone applications would become part of our everyday life. Fast forward a decade and we now have apps for literally everything, from trackable maps to online shopping, online banking to instant messaging.
Five worthy reads: Supply chain cyberwarfare
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we are exploring the concept of supply chain cybersecurity in a time when there is a rising number of third-party cyberattacks.
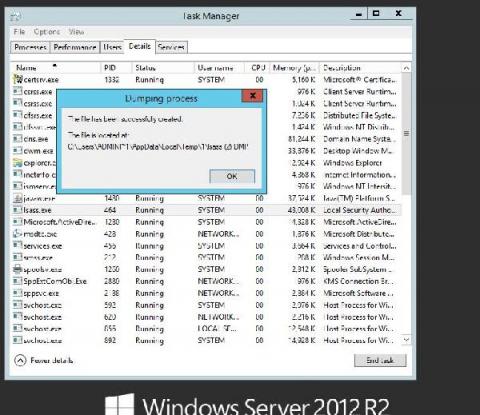
IT security under attack: Credential dumping attacks in Windows environments
Most of the time, threat actors in the cybersecurity landscape don’t employ advanced techniques and tools to intrude and establish a foothold within networks. Often, they disguise malicious operations by mimicking the activities of legitimate users, leaving behind little to no footprint. Blending malicious actions with day-to-day IT activities helps attackers maintain a low profile and remain undetected for a longer period.
Custom promise outcomes in Mission Portal
CFEngine 3.17.0 introduced custom promise types, which enable CFEngine users to extend core functionality and policy language in a simple way. As an example of the power and simplicity of this new feature, I will show a promise type that helps to observe a website’s status. The module which implements this promise type was written in a couple of hours.
Enterprise Security Controls for Kubernetes
Splunk SOAR Playbooks: Finding and Disabling Inactive Users on AWS
Every organization that uses AWS has a set of user accounts that grant access to resources and data. The Identity and Access Management (IAM) service is the part of AWS that keeps track of all the users, groups, roles and policies that provide that access. Because it controls permissions for all other services, IAM is probably the single most important service in AWS to focus on from a security perspective.
Why Use Active Directory Security to Improve Your Server Security?
How do you secure your network servers, laptops, desktops, and workstations? A good starting point is to have a checklist of how to enable security features on these devices. You also need to enable a server monitoring service to track specific events and generate event logs. Yet, your security tasks are never done. You can get a false sense of security if you merely go through your checklist of security items and stop.
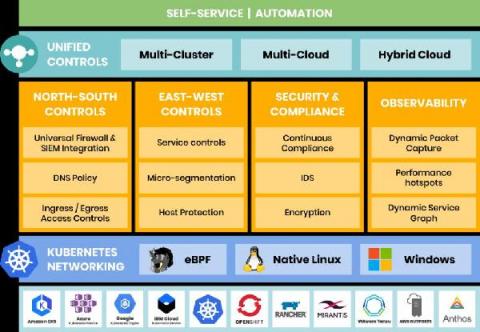
Calico Enterprise: An Overview
As we enter a new year, it’s an appropriate time to reflect on our achievements at Tigera and how much Calico Enterprise has evolved over the past year as the industry’s leading Security and Observability solution for Kubernetes Networking and Microservices.
7 Ways UEM Enhances Your Security
Introduction Many things blur the line between endpoint management and security. Examples? Managing an endpoint. Configuring it. Performing application and software management. And patching the endpoint. The fact is, managing and securing a device is so interrelated that it makes sense for these two functions to come together in a single platform that can accomplish these, and other tasks needed in your IT organization. Here are the seven ways Unified Endpoint Management (UEM) can support security.
SEGA Europe and Sumo Logic: Integrating security across clouds
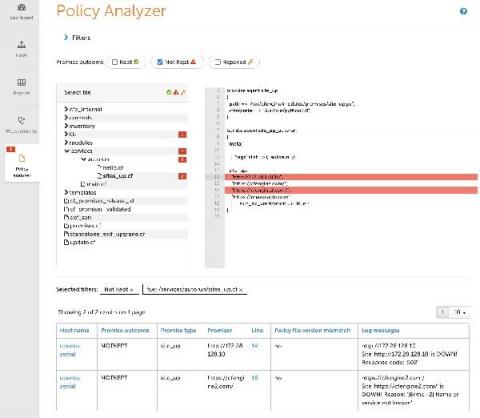
How to serve policy from a local git server
Several months ago I started the practice of using CFEngine Enterprise and its Mission Portal UI on a daily basis to manage the connected devices in my home. To start, I brought up an old desktop machine, cfengine-hub, to use as my hub and downloaded Enterprise, which is free for use up to 25 hosts. The next step in using best practices is to deploy policy from a version control repository.
Network Security: The Journey from Chewiness to Zero Trust Networking
Network security has changed a lot over the years, it had to. From wide open infrastructures to tightly controlled environments, the standard practices of network security have grown more and more sophisticated. This post will take us back in time to look at the journey that a typical network has been on over the past 15+ years. From a wide open, “chewy” network, all the way to zero trust networking. Let’s get started.
Falco vs. AuditD from the HIDS perspective
In this blog, we will compare and contrast Falco vs. AuditD from a Host Intrusion Detection (HIDS) perspective. AuditD is a native feature to the Linux kernel that collects certain types of system activity to facilitate incident investigation. Falco is the CNCF open-source project for runtime threat detection for containers and Kubernetes. We will dig deeper into the technical details and cover the installation, detection, resource consumption, and integration between both products.
Troubleshooting microservices on K8S
Splunk SOAR Playbooks - AWS IAM Find and Disable Inactive Users
AWS Quickstart for Calico
NEW Feature: Configurable Assurance Alerts
At RapidSpike everyone gets involved with product and feature ideation, including our customers! We pride ourselves on being responsive to your needs, taking your feedback, and turning it into our next great feature — after all, you know what you need. We’re here to listen and our developers love tackling a new challenge and solving a tricky problem. This has trickled down into one of our latest features — Configurable Assurance Alerts.
The Benefits of User Journeys
Getting up and running with Calico On-Prem
Extending the Zero-Trust Security Framework to Your Home
Mixing your personal and work devices while connected to your home network and accessing the Internet is a risky proposition from a security and privacy standpoint. Why? I frequently monitor my firewall logs. What I observe on my WAN interface are blocked IP addresses sourced from adversarial nation states which makes the hair on the back of my neck stand up.
Sysdig Usage Report Finds Shifting Container Security Left is Not Enough
NEW Feature: Journey Pre-Actions
We have released a new upgrade to our script editor which is part of our ongoing commitment to build the best Synthetic User Journey monitoring tool on the market – Journey Pre-Actions. This upgrade is simple but will be useful for those websites that require certain prerequisites in order to allow tests such as these to be run. As with many of our features here at RapidSpike, this was born from a real-world requirement from a number of our customers.
Sysdig 2021 container security and usage report: Shifting left is not enough
The fourth annual Sysdig container security and usage report looks at how global Sysdig customers of all sizes and industries are using and securing container environments. By examining how and when organizations are implementing security in the development lifecycle, we have been able to uncover some interesting data points in this year’s report. For example, we can see that 74% of organizations are scanning container images in the build process.
Runtime Threat Detection on AWS
Security Analytics with Sumo Logic: Detect, Investigate, Respond
PostgreSQL security: The PgMiner botnet attacks explained
Assuring the security of PostgreSQL and all open source database systems is critical as many learned with the PgMiner botnet attacks in December 2020. Having an understanding of, and visibility into, how these attacks happen and following standard best practices is the best way to make sure that your data is not at risk. This blog details the latest security issue with PostgreSQL, how to fix/prevent these attacks and how to ensure security of your PostgreSQL database instances.
2020 Magecart Timeline
In this blog, we break down the timeline of the number one hacker threat to ecommerce sites today – Magecart. The 2020 Magecart timeline includes all the significant Magecart attacks in 2020. With 4,800 formjacking attacks each month alone, this timeline only represents a small proportion of attacks reported in the public domain in 2020.
Looking Inside TLS Certificates
In the last decade, it has become increasingly important to secure websites and applications using HTTPS instead of HTTP. A GroundWork Monitor installation is no exception, so in GroundWork 8, using HTTPS to access the system is the default setup, and you can add TLS certificates to it that you generate or purchase. See Adding Certificates to HTTPS for more information on doing so.
Runtime Threat Detection on AWS
Getting up and running with Calico on your Rancher Kubernetes Cluster
Sentry Receives SOC 2 Type 2 Certification
No matter your business, keeping customer data secure is critical toward keeping your customer’s trust. With the rise in data breaches (and subsequent security certifications), we don’t have to tell you why you should scrutinize every cloud service that you consider — including us. To that end, we believe in being explicit with our compliance. And that includes how we pursue independent certifications like ISO, HIPAA, and now, SOC 2 Type II.
Want to Strengthen Cybersecurity? MIT Says to Start With AIOps
A new MIT Technology Review report reveals how AI and machine learning can help companies protect themselves against growing cybersecurity threats.
Calico & Calico Enterprise: Now Available as AWS Quick Starts
As an AWS Advanced Technology Partner with AWS Containers Competency, Tigera is thrilled to announce that Calico and Calico Enterprise are both now available as AWS Quick Starts. If you’re unfamiliar with the concept, an AWS Quick Start is a ready-to-use accelerator that fast-tracks deployments of key cloud workloads for AWS customers.
The Evolution Of Cybersecurity Over The Decades
The Time Has Arrived: Upgrading to TLS Version 1.2 or Newer
The time has arrived to upgrade to TLS 1.2, if you have not already done so for any of your systems. At Circonus, we will be dropping support across our platform for all connections using TLS versions less than 1.2 on January 21, 2021. Virtually none of our customers will be impacted by this change, as this has been in the works for a very long time, and most customers will have made this transition already.
Improve Your Security Posture By Focusing on Velocity, Visibility, and Vectors
Five worthy reads: Make data security your New Year's resolution
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. More than ever, now is the time for organizations to prioritize data security. This week we look at some data security trends that are shaping the industry today. Illustration by Balaji KR A recent study conducted by RiskBased Security has labeled 2020 the worst year for data security with a shocking 36 billion records compromised, twice the number from 2019.
5 Hacks to Monitor in 2021
Of all the polls, round-ups, and end-of-year wrap-ups, none gives us as much trepidation as the 2021 projected line-up for MVP hacks. As provider lists grow longer, and monitored data grows broader, we decided to distill our list of culprits down to the most likely suspects you’ll need to monitor. Ready? Okay!
How the Nissan Source Code Leak Could Have Been Avoided
And you thought you were having a bad day…did you see what happened to the developers over at Nissan? The source code (Git repos) for Nissan’s mobile apps and internal tools was leaked to the Internet because the link was publicly accessible and the password easy to guess. 😬 Yikes.
Stackrox Acquisition: The Race to Secure Containers
Today, Red Hat announced its intent to acquire Stackrox. This is a very exciting development in the world of cloud-native security! First and foremost, congratulations to Stackrox, an early participant in the container security space. This acquisition is a great outcome for Stackrox given their nascent scale and on-premises offering.
5G and the Journey to the Edge
Recently, AT&T Cybersecuritypublished important findings in the tenth edition of their Insights report entitled, “ 5G and the Journey to the Edge.” Ivanti was thrilled to contribute to the report, which outlines the most pressing security concerns organizations face in a world embracing the revolutionary transformation to 5G and edge technology.
Automate your SIEM with Sumo Logic in 7 Clicks
Ship Your ModSecurity Logs to Logz.io Cloud SIEM
Now, you can ship ModSecurity logs to Logz.io to automatically surface high-priority attacks identified by ModSecurity. Logz.io will automatically parse those logs to project a greater bird’s-eye-view of your security situation within dedicated dashboards. ModSecurity is a prolific web application firewall (WAF) popularly used to help secure web servers. It supports Apache HTTP, IIS, and NGINX. It can deploy either as a proxy server or within a web server itself.
How to Connect Elastic Security to Jira - Version 7.10
Understanding Kube-Proxy
Automation Made Easy: What's New with Splunk Phantom
The Splunk Security Team is excited to share some of the new and enhanced capabilities of Splunk Phantom, Splunk’s security orchestration, automation and response (SOAR) technology. Phantom’s latest update (v4.10) makes automation implementation, operation and scaling easier than ever for your security team.
How Clorox leverages Cloud SIEM across security operations, threat hunting, and IT Ops
Hacked! Solve the Dreaded DevOps Problem With This
Hacks that make headlines are painful for everyone involved, but with some clever preparation and web monitoring at your side you can avoid the worst of this pain. Those who have been victimized face a steep uphill battle to reclaim trust and authority. Unwitting victims, like customers and end users, suffer downtime or leaks containing personally identifiable information. If your eye is not on security, your organization is inviting these kinds of attacks.
How to Contribute to Detection Rules in Elastic Security - Version 7.10
Stop Enforcing Security Standards. Start Implementing Policies.
In days gone by, highly regulated industries like pharmaceuticals and finance were the biggest targets for nefarious cyber actors, due to the financial resources at banks and drug companies’ disposal – their respective security standards were indicative of this. Verizon reports in 2020 that, whilst banks and pharma companies account for 25% of major data breaches, big tech, and supply chain are increasingly at risk.