Easily Automate Across Your AWS Environments with Splunk Phantom
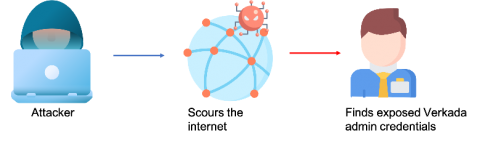
When running Splunk Phantom with AWS services, it can be tricky to make sure Splunk Phantom has the right access. When you’re managing multiple AWS accounts, the effort to configure Splunk Phantom’s access to every account can feel insurmountable. Fortunately, Amazon has the Security Token Service to solve this problem with temporary credentials, so we’ve integrated it with Splunk Phantom!