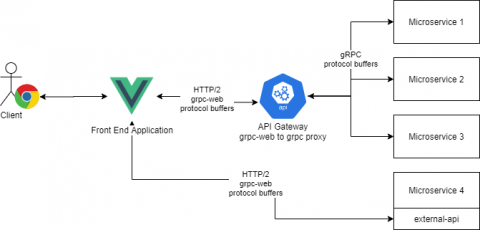
The full stack isn't just cloud-based, microservices apps, but includes on-premises and hybrid private cloud infrastructure and packaged applications. The challenges associated with aggregating, analyzing, reporting, and alerting intelligently on logs have become more complex than ever due to the acceleration of packaged and customized application deployment in support of business transformation, alongside the growing requirements needed to ensure security and compliance. This webinar will explore multiple methods to ensure compliance, identify threats, and optimize MTTR by monitoring, analyzing, and managing logs across all types of application and infrastructure architectures.