Operations | Monitoring | ITSM | DevOps | Cloud
January 2022
Using cfbs with a traditionally managed policy set
With the recent release of build.cfengine.com and cfbs I have been thinking about the process of converting a traditionally manged policy set. I consider a traditionally manged policy set one where you have a repo with the root of masterfiles being the root of the repository, or even having no repository at all and managing masterfiles by editing directly in the distribution point (e.g. /var/cfengine/masterfiles).
The PwnKit vulnerability: Overview, detection, and remediation
On January 25, 2022, Qualys announced the discovery of a local privilege escalation vulnerability that it identified as PwnKit. The PwnKit vulnerability affects PolicyKit’s pkexec, a SUID-root program installed by default on many Linux distributions. The same day of the announcement, a proof of concept (PoC) exploit was built and published by the security research community.
How Broadcom Software Helps The Enterprise Secure and Protect the Network Edge
Elevate AWS threat detection with Stratus Red Team
A core challenge for threat detection engineering is reproducing common attacker behavior. Several open source and commercial projects exist for traditional endpoint and on-premise security, but there is a clear need for a cloud-native tool built with cloud providers and infrastructure in mind. To meet this growing demand, we’re happy to announce Stratus Red Team, an open source project created to emulate common attack techniques directly in your cloud environment.
How Big Data Analytics Strengthens Cybersecurity
The attacks cybercriminals are using grow more complex and sophisticated by the day. However, with the help of big data analytics, you aren’t left defenseless. You can use big data analytics to fortify your cyber defenses and reduce your vulnerabilities. 1. Analytics can help you uncover suspicious patterns. Big data analytics protects your business data and strengthens your cybersecurity by providing valuable cybersecurity intelligence to your data analytics experts.
CFEngine: The Agent Is In 9 - Intro To Using cf-secret
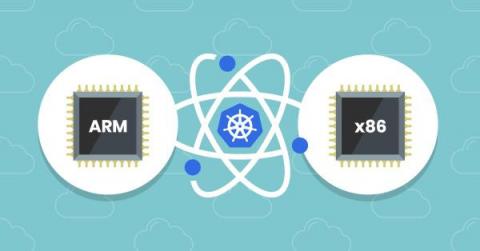
Is ARM architecture the future of cloud computing?
Central processing units (CPUs) can be compared to the human brain in that their unique architecture allows them to solve mathematical equations in different ways. x86 is the dominant architecture used in cloud computing at the time of this writing; however, it is worth noting that this architecture is not efficient for every scenario, and its proprietary nature is causing an industry shift toward ARM.
3 Ways LogStream Can Improve Your Data Agility
Four months into this new gig at Cribl, I wish I could bottle up that “lightbulb” moment I get when walking people through how Cribl LogStream can help them gain better control of their observability data. So I hope the scenario walkthroughs below will capture some of that magic and shed some light on how LogStream can improve your organization’s data agility – helping you do more with your data, quickly, and with less engineering resources.
Defining Your IT Security Perimeter
It wasn’t too long ago that a security system would be nothing more than a few walls, some cameras, and an inattentive security guard. That’s no longer the case In today’s digital landscape. Now organizations must invest in securing their assets from a growing number of cyberthreats. To start, they must first draw up the boundaries of their IT security perimeter.
Who is Most Vulnerable to Ransomware Attacks? New Report Reveals Latest Trends.
No one will be surprised to hear that ransomware is, once again, on the rise. The last two years have seen a stratospheric increase in both the frequency and sophistication of attacks. In a just-released report from Ivanti, Cyber Security Works and Cyware, 2021 closed out with alarming statistics including a 29% increase in CVEs associated with ransomware, and a 26% increase in ransomware families compared to the previous year.
Is Shadow IT Impacting Your Security? How An Organization Restored 90% Compliance in One Day
Just how effective can an employee engagement campaign be? Consider this: A single Nexthink Engage campaign prompted 90% of employees to update their browser in one day. Despite not having access to the enterprise version of the Google Chrome browser, thousands of employees in this U.S. biopharmaceutical company downloaded the personal version of Google Chrome. 5200 employees to be exact.
The Major Benefits of a SOAR
SOAR — or security orchestration, automation and response — is a collection of processes, software and tools that allows teams to streamline security operations. SOAR platforms are a hot topic in the realm of cybersecurity these days, and with good reason.
Datadog Cloud Security Platform
An introduction to the Avantra SUSE hardening Add in
Included with Avantra Enterprise edition, Avantra Add ins are pre-packaged best practice scenarios that accelerate your business time to value using our expertise. One such Add in is SUSE hardening and is based on the hardening guide from the makers of SUSE Enterprise Linux. This Add in is a collection of eight custom checks that are designed to be extensible by you to match your organizational requirements.
Mind Your Dependencies: Defending against malicious npm packages
Evolve to a Risk-Based Vulnerability Remediation Strategy with a Cloud-Native Patch Management Solution - Now Available from Ivanti
Ransomware attacks are increasing in frequency and severity every year. The impact to companies is devastating. These attacks typically lead to lost business for companies as they often cause increased customer turnover, system downtime, diminished reputation and other adverse side effects.
Recommendations for Detecting a Cyber Security Breach
Long gone are the days where a cyber security breach inferred you just had to change your log in password, or maybe run a virus scan. Modern cyber breaches are a constantly growing and changing combination of threats and security concerns that can put organizations in a lurch, and if not solved quickly can cause significant damage not only to reputation, but to customer trust.
VMware Tanzu Application Service Delivers Operational Excellence During Log4Shell
On two occasions in December 2021, VMware Tanzu Application Service released remediations within 48 hours of critical CVEs being announced. These remediations were both in response to the Log4j saga, enabling VMware customers to defend against attack vectors quickly after the Day 0 event. This quick response is a reflection of the dedication of the VMware engineering teams working on Tanzu Application Service today.
What is the Essential Eight Maturity Model - and where does your data fit into the picture?
Running regular security scans with scheduled pipelines
Security is a vital part of application development, yet it may be neglected until an attacker takes advantage of a vulnerability in the system. The consequences of a security breach can damage an application’s integrity as well as a company’s reputation and revenue. Software architects and engineers need to pay special attention to securing the systems they work on.
TOP 10 IT Trends
Harnessing AIOps to Improve System Security
You’ve probably seen the term AIOps appear as the subject of an article or talk recently, and there’s a reason. AIOps is merging DevOps principles with Artificial Intelligence, Big Data, and Machine Learning. It provides visibility into performance and system data on a massive scale, automating IT operations through multi-layered platforms while delivering real-time analytics.
Chatbots - Intro to Torq Webinar
LogStream for InfoSec: VPC Flow Logs - Reduce or Enrich? Why Not Both?
In the last few years, many organizations I worked with have significantly increased their cloud footprint. I’ve also seen a large percentage of newly launched companies go with cloud services almost exclusively, limiting their on-premises infrastructure to what cannot be done in the cloud — things like WiFi access points in offices or point of sale (POS) hardware for physical stores.
9 Types of Phishing and Ransomware Attacks-And How to Identify Them
Cyberattacks have become more pervasive globally, evolving quickly in sophistication and scale, and are now more lucrative than ever for cybercriminals. Not only has The Everywhere Workplace extended the cyber risk and threat landscape—especially for data privacy and its protection—but a lot of Agile software developers, many of whom lack any DevSecOps process, are publishing untested or poorly tested software that can be exploited as zero-days by criminal gangs.
Are there good hackers?
Hello and welcome back to our “Mystery Jet Ski.” Much better than those programs about supernatural stuff and alien suppositions. Today we will continue with our exhaustive investigation on the hacker world, and we will delve a little more into the concept of “ethical hacker.” Is it true that there are good hackers? Who are the so-called “White hats”? Who will win this year’s Super Bowl?
Monitoring Endpoint Logs for Stronger Security
The massive shift to remote work makes managing endpoint security more critical and challenging. Yes, people were already using their own devices for work. However, the rise in phishing attacks during the COVID pandemic shows that all endpoint devices are at a higher risk than before. Plus, more companies are moving toward zero-trust security models. For a successful implementation, you need to secure your endpoints.
Continuously Securing Software Supply Chain
Have You Forgotten About Application-Level Security?
Security is one of the most changeable landscapes in technology at the moment. With innovations, come new threats, and it seems like every week brings news of a major organization succumbing to a cyber attack. We’re seeing innovations like AI-driven threat detection and zero-trust networking continuing to be a huge area of investment. However, security should never be treated as a single plane.
Announcing lockc: Improving Container Security
The lockc project provides mandatory access controls (MAC) for container workloads. Its goal is to improve the current state of container/host isolation. The lockc team believes that container engines and runtimes do not provide enough isolation from the host, which I describe later in the “Why do we need it?” Section. In this blog post, I’ll provide an introduction to lockc, discuss why you need it and show you how to try it out for yourself.
CIS benchmark compliance: Introducing the Ubuntu Security Guide
The CIS benchmark has hundreds of configuration recommendations, so hardening and auditing a Linux system manually can be very tedious. Every administrator of systems that need to comply with that benchmark would wish that this process is easily usable and automatable. Why is that? Manual configuration of such a large number of rules leads to mistakes – mistakes that cause not only functional problems, but may also cause security breaches.
Ubuntu introduces the Ubuntu Security Guide to ease DISA-STIG compliance
January 17th: London, UK – Canonical, the company behind Ubuntu, the world’s most popular operating system across private and public clouds, now offers the Ubuntu Security Guide tooling for compliance with the DISA Security Technical Implementation Guide (STIG) in Ubuntu 20.04 LTS. The new automated tooling builds on Canonical’s track record of designing Ubuntu for high security and regulated workloads, powering U.S. government agencies, prime contractors, and service providers.
Ransomware: Prevention and Response Software by Pulseway
The Danger of Ransomware: Patrick
Ransomware Prevention And Response Software
Ransomware Awareness - Protect Yourself with Pulseway
Lightrun For Application Security - Detecting, Investigating and Verifying Fixes for Security Incidents Using Lightrun
Cover major milestones in app security: finding the issue, evaluating a breach, proving it and validating the fix. We didn’t design Lightrun for this task, but it rises to the challenge. I’m not a security expert. I’d like to think of myself as a security conscious developer, but this is a vast subject with depth and breadth. What I understand is Lightrun and Debugging. In that capacity, I can show some creative ways you can use it as a security tool.
How to Build a Culture of Cybersecurity in Your Company
It's been a crazy couple of years, and things are still changing rapidly all around us. But you don't need me to tell you that; you're probably living it in your organization already. In the IT sector, we've gone through a global chip shortage, the postponement of major tech events, the delay of product launches, and perhaps most importantly, almost all companies shifted almost completely to remote work.
Netreo Full-Stack Monitoring and Observability Suite Achieves Veracode Verified Standard Recognition
Netreo, the award-winning provider of IT infrastructure monitoring and observability solutions and one of Inc. 5000’s fastest growing companies, today announced that the Netreo full-stack IT infrastructure monitoring and Retrace by Netreo full lifecycle APM solutions have both earned Veracode Verified Standard recognition for proven security practices in application development.
Cloud 66 Feature Highlight: Application Surge Protection
Why cloud native requires a holistic approach to security and observability
Like any great technology, the interest in and adoption of Kubernetes (an excellent way to orchestrate your workloads, by the way) took off as cloud native and containerization grew in popularity. With that came a lot of confusion. Everyone was using Kubernetes to move their workloads, but as they went through their journey to deployment, they weren’t thinking about security until they got to production.
Graylog Insights -- How 2021 Will Shape 2022
People may not reminisce over 2021, but as Winston Churchill once said, “Those that fail to learn from history are doomed to repeat it.” 2021 swooped in on the coattails of a major supply chain data breach, and a lot of the challenges we experienced during this past year seemed to follow suit. To celebrate the best and hopefully move away from the worst that 2021 had to offer, this look back at 2021 trends can inspire us all to learn, and most of all, show us how to move forward.
5 top hybrid cloud security challenges
Hybrid cloud environments can add complexity, reduce visibility, and require different logging and monitoring approaches for security teams. For a growing number of organizations, IT environments encompass a blend of public cloud services, private clouds, and on-premises infrastructure—with the latter becoming an ever-smaller portion of the mix. The past two years have seen a major uptick in the use of cloud services, and the trend shows no signs of slowing.
What SecOps Teams Can Expect in 2022
Traditionally, most organizations have had siloed departments wherein teams’ activities are highly separated and the objectives within organizational structures are divided. This operational methodology has brought about friction – especially within the IT department, where developers and ITOps lack collaboration.
Interview with Cyber Czar & Founding Partner of NIST, Jeffrey R. Wells
For the next interview in our series speaking to technology and IT leaders around the world, we’ve welcomed Co-chair of Cybersecurity, Data Protection & Privacy at Clark Hill, Jeffrey R. Wells to share his views on the state of cybersecurity today.
Digital-First SecOps: A CISO Perspective
The Transformative Effect of No-Code Security Automation
Find and mitigate Log4j vulnerabilities with Puppet Enterprise
Log4j, the popular open-source logging library, had a rough December and closed out the year with an impressive streak of four critical vulnerabilities so far. Many are calling this the worst cybersecurity event in history. Again, so far.
Momma Said Grok You Out: Use LogStream to Streamline Searches, Aid in Reformatting Data and Parsing
It is commonly believed that once data is collected and ingested into a system of analysis, the most difficult part of obtaining the data is complete. However, in many cases, this is just the first step for the infrastructure and security operations teams expected to derive insights.
The JNDI Strikes Back - Unauthenticated RCE in H2 Database Console
Five reasons why you should work with an SD-WAN partner
SD-WAN is one of the fastest-growing segments of the network infrastructure market. Designed correctly, it will deliver unique advantages, enabling true digital transformation while reducing costs and management time and increasing application performance, availability, visibility and user experience. While the benefits of SD-WAN are obvious, we know it can often be a challenge to select the appropriate approach to design, implementation, and ongoing management.
Detecting Log4J/Log4Shell exploits with LogStream
Extending Panorama's firewall address groups into your Kubernetes cluster using Calico NetworkSets
When deploying cloud-native applications to a hybrid and multi-cloud environment that is protected by traditional perimeter-based firewalls, such as Palo Alto Networks (PAN) Panorama, you need to work within the confines of your existing IT security architecture. For applications that communicate with external resources outside the Kubernetes cluster, a traditional firewall is typically going to be part of that communication.
Detecting and Preventing Log4J Attacks with Cribl LogStream
Shortly before the December holidays, a vulnerability in the ubiquitous Log4J library arrived like the Grinch, Scrooge, and Krampus rolled into one monstrous bundle of Christmas misery. Log4J maintainers went to work patching the exploit, and security teams scrambled to protect millions of exposed applications before they got owned. At Cribl, we put together multiple resources to help security teams detect and prevent the Log4J vulnerability using LogStream.
Dark Data: The Cloud's Unknown Security And Privacy Risk
Over the last few years, multicloud frameworks have drifted into the mainstream. Organizations now create, store and manage enormous volumes of data across different cloud platforms. Despite the magnitude of this trend, there’s a stark and often disturbing truth: Businesses often have little or no visibility into much of the data that resides in these clouds. The culprit? Dark data.
Exploring Ninja Data Protection
With image backup now generally available to our partners, Ninja Data Protection is ready for prime time. When we first launched Ninja Data Protection in 2020, our backup solution was a Windows-only, cloud-only file and folder backup solution. With several hundred partners adopting the solution and providing feedback, we were able to rapidly adapt our backup roadmap to customize the solution to our partners needs and wants.
Why is SAP security monitoring important?
SAP applications drive the most business-critical processes in companies around the globe. It will not surprise anyone that cybersecurity is of utmost importance to prevent SAP customers from vulnerabilities. A joint threat-intelligence report from SAP and Onapsis, released on 6 April 2021, warns that cyber attackers are actively exploiting known SAP security vulnerabilities to steal information and compromise mission-critical SAP landscapes.
Mitigating the Next Log4shell: Automating Your Vulnerability Management Program
As CVE-2021-44228, a.k.a "Log4Shell" or Apache Log4j Remote Code Execution vulnerability continues to send shockwaves across the world of software, many security vendors and practitioners are rushing to provide recommendations on dealing with the crisis. If you need immediate help mitigating the impact of Log4shell, we're here for that. But the goal of this post is to look forward. This isn't the first and won't be the last high-impact vulnerability to be uncovered. So it's worth preparing your organization for the next one, so that you can respond faster, mitigate and remediate sooner - and have fewer weekends like the last one.
IoT's Importance is Growing Rapidly, But Its Security Is Still Weak
The weakest link in most digital networks is the person sitting in front of the screen – the defining feature of the Internet of People (IoP). Because that’s where, through cunning and manipulative tactics, unsuspecting recipients can be tricked into opening toxic links. Little do they know, however, they’ve unwittingly opened the gates to digital catastrophe. Of course, I have nothing against people. In fact, some of my best friends are people!
Enhanced security for the Spot-Jenkins plugin
CFEngine: The Agent Is In 8 - Security Hardening Holiday Calendar
5 key strategies for protecting legal privilege during security incidents
When a cyber incident hits, there are certain questions that are asked right away almost every time...