Operations | Monitoring | ITSM | DevOps | Cloud
October 2022
Confidential computing in public clouds: isolation and remote attestation explained
In the first part of this blog series, we discussed the run-time (in)security challenge, which can leave your code and data vulnerable to attacks by both the privileged system software of the public cloud infrastructure, as well as its administrators. We also introduced the concept of trusted execution environments and confidential computing, (CC), as a paradigm to address this challenge.
How To Protect Your Business In Case Of Accidents?
A more greenfield opportunity for threat actors
Preventing PII in Test environments
Securing Productivity in Supply Chains
Mobile device management – it’s been part of your operational technology portfolio for a long time. You’ve been using it for years – or maybe decades – to stage device configurations, push software updates and more. You might be using our Ivanti Avalanche MDM solution to manage your rugged mobile deployments. The device, OS and app management capabilities remain at the center of your mobility management program, and that isn’t going to change.
Show Notes: The Agent is In - Episode 18 - Policy Examples
Do you know how to use every function available in CFEngine? Join Cody, Craig, Herman to see how Nick uses org-mode, org-roam, and ob-cfengine3 to manage his personal collection of CFEngine Function Examples.
What is Ransomware?
Comparing Cybersecurity Trends Since the Pandemic
CFEngine: The agent is in 18 - Policy examples
Scary stories you won't believe until they happen to you!
For halloween this year, we wanted to share some scary scenarios along with security recommendations to help avoid them. All the names, companies and characters are made up, but the events and experiences are based on things which could happen, or have happened in the real world.
What Is MITRE D3FEND, and How Do You Use It?
MITRE is a world-renowned research organization that aims to help build a safer world. It is probably best known in the information security industry for being the organization behind the industry-standard CVE (Common Vulnerabilities and Exposures) list. Each entry on the list is supposed to include an explanation of how the vulnerability could be exploited. These attack vectors are tracked and defined in another well-known knowledge base called ATT&CK, which is also maintained by MITRE.
Seven steps to strengthen your security posture
Learn more about application security, why it matters and how to strengthen your security posture with these critical steps.
Open Policy Agent (OPA) Overview Session
Broadcom's Rally Software Receives FedRAMP Authorization For Value Stream Management Solution
What to Look for With Ivanti's Fourth Quarter Release
In 2004, a joint initiative of the US Department of Homeland Security and the National Cybersecurity Alliance declared October National Cybersecurity Awareness Month to help raise awareness of the best practices to remain safe while working online. Vigilance enables us to maintain privacy and productivity for our own sake and for the organizations we may work for.
Best Chrome extensions for web developers
Chrome revolutionized the way to extend browsers with new features. Back in the day, extensions were annoying toolbars (remember the Ask toolbar?) and related spam-like additions. Today, I couldn't live without extensions. Here's a list of our favorite extensions used while developing elmah.io. Let's jump right into the extensions. All extensions are sorted alphabetically so make sure to go through the entire list for the best extensions for Chrome (and mostly Edge too).
Introducing the New Snyk App for Bitbucket Cloud
Scanning Secrets in Environment Variables with Kubewarden
We are thrilled to announce you can now scan your environment variables for secrets with the new env-variable-secrets-scanner-policy in Kubewarden! This policy rejects a Pod or workload resources such as Deployments, ReplicaSets, DaemonSets , ReplicationControllers, Jobs, CronJobs etc. if a secret is found in the environment variable within a container, init container or ephemeral container. Secrets that are leaked in plain text or base64 encoded variables are detected.
Improve Response in the Threat Detection Response Equation - Webinar
Phishing Attacks and Marketing Minds: How Hackers Use Unexpected Skills to Break Their Targets
Microsoft's Coordinated Disclosure Discussion from BlackHat & DefCon '22: Security Insights
LIVE NOW: How Do Mature DevOps Teams Manage Software Security?
Privacy, Please! Why a Comprehensive Federal Framework is Essential to Protect Consumer Data Privacy
Laws vary by state. That’s expected. Fairbanks, Alaska, enacted a law prohibiting the provision of alcoholic beverages to moose, so don’t even think about it. In a part of Washington State, good luck trying to kill Bigfoot. (Not because Bigfoot doesn’t exist, but specifically because it’s illegal per a 1969 law.) But what happens when state-specific regulations are used to address a topic that transcends geographic boundaries like, say, the internet?
Endpoint Detection & Response (EDR) Guide
Cyberthreats and cyberattacks continue to grow more advanced and complex, making them much harder to stop. In fact, a recent study showed that cybercriminals can penetrate an organization’s network and access network resources in 93 out of 100 cases. The odds of keeping cybercriminals away don’t look hopeful for organizations across all industries.
The Latest Ransomware Stats Are In and It's Not Good News.
Out of 10 key metrics tracked quarterly to establish the state of ransomware activity, only one metric stayed static from Q1 to Q3 2022. The other nine all worsened. That’s an alarming trend, especially given that many business leaders hoped to see ransomware activity taper off after a historic surge during the peak of the pandemic. Ivanti, together with Cyber Security Works and Cyware, collaborated on the just-released report.
What Is Phishing?
Phishing is the fraudulent practice of manipulating people via emails, texts, websites or phone calls into disclosing sensitive information, like credit card numbers or login credentials, that can then be used to access and attack systems. Cybercriminals do this by tricking users into taking specific actions that cause them to inadvertently download malware.
Untangling Account Management With User Permissions
Companies, like most things, rarely grow in a straight line. Plants will take root where they can, and send shoots where they can to get the most sunlight, even if there are obstacles in the way. But vines and branches aren’t known for their efficient pathing, which can make a tangled mess of the whole plant. So get a good sun hat and some pruning shears ready; you’ll need them today! The difference between organic and structured growth is one of purpose and planning.
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Torq is extremely proud to have Jason Chan on our advisory board. Jason has more than 20 years of experience working in cybersecurity. He’s one of the world’s leading experts in adopting security automation, cloud security, and enhancing security in modern software development practices. Jason’s most recent career experience was leading the information security organization at Netflix for more than a decade.
Bridge Your Data Silos to Get the Full Value from Your Observability and Security Data
In my work as a technical evangelist at Cribl, I regularly talk to companies seeing annual data growth of 45%, which is unsustainable given current data practices. How do you cost effectively manage this flood of data while generating business value from critical data assets?
How Calico CNI solves IP address exhaustion on Microsoft AKS
Companies are increasingly adopting managed Kubernetes services, such as Microsoft Azure Kubernetes Service (AKS), to build container-based applications. Leveraging a managed Kubernetes service is a quick and easy way to deploy an enterprise-grade Kubernetes cluster, offload mundane operations such as provisioning new nodes, upgrading the OS/Kubernetes, and scaling resources according to business needs.
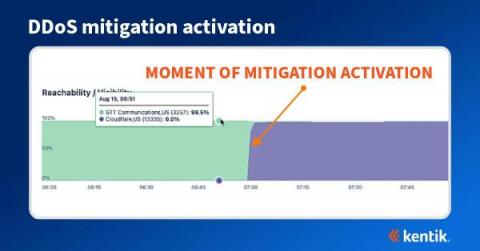
How BGP propagation affects DDoS mitigation
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.
How BGP propagation affects DDoS mitigation
4 Website Security Threats (2022) + Solutions
For server administrators tasked with ensuring the reliable operation of their web applications, the thought of a lurking cyberattack can be one to lose sleep over. An attack on your system and the services you provide could render your web applications unresponsive. What’s worse, important information that depends on privacy and the careful storing of data is put at risk.
Security Controls - REST API - PowerShell Tutorial
The State of Security Data Management in 2022
Today, Cribl is releasing The State of Security Data Management 2022 in collaboration with CITE Research. The report examines the challenges that enterprises are facing as they work to balance evolving business priorities with cyber threats. The report was conducted in September 2022 and surveyed 1,000 senior-level IT and security decision-makers. The survey found that, although most organizations are confident in their data management strategy, few believe it’s actually sustainable.
Three ways to encourage the importance of security posture
“I’m not a big enough business… I’m too small… no one will want to hack me.” “I don’t have anything of any importance that anyone would want… I’m not terribly concerned.” “It hasn’t happened to us yet, so it isn’t something I’m worried about.” “What you’re proposing seems like overkill to me. And besides, we don’t have the extra funds in our budget anyway.
What Is Phishing? Insider Risk & How to Prevent It
Monitoring Transaction Log Files for PCI compliance
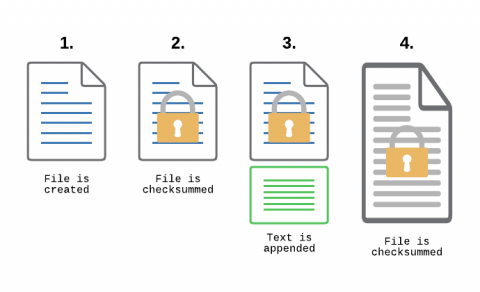
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
How To Properly Protect Your Intelectual Property On The Internet
Accessing CFEngine nightly packages
Did you know that nightly builds of CFEngine are available? cf-remote is the most convenient way to get nightly packages. If you’re not familiar with it, or if you need a refresher, check out our other blog posts about cf-remote.
Checkly Completes SOC 2 Type 1 Audit
A Service Organization Control (SOC) audit is one of the most extensive tests an organization can undergo to demonstrate the ongoing maintenance of high-level information security. Today, we’re thrilled to announce that Checkly is SOC 2 Type 1 compliant after completing a successful audit by an accredited auditing firm. This demonstrates that Checkly’s information security policies, procedures, and practices meet the SOC 2 guidelines for security and data privacy.
Application Control for Windows
Datadog alternatives for cloud security and application monitoring
How Do You Choose The Best Crypto Portfolio Tracking Software?
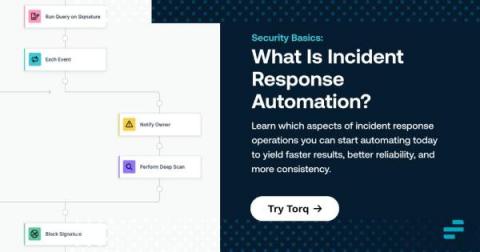
Security Basics: Incident Response and Automation
Incident response is one of the most challenging tasks that IT teams face. It's challenging not just because it typically involves many stakeholders and moving pieces, but also because teams usually face pressure to respond as quickly as possible. That's why investing in incident response automation is a wise choice. Although it may not be possible to automate every aspect of every incident response workflow, being able to automate at least the major elements of incident response will yield incident management processes that are faster, more reliable, and more consistent.Keep reading to learn about the components of incident response and which incident response activities to start automating.
Tips and Tricks for the Small SOC: Part II
It’s Cybersecurity Awareness Month, and in that spirit, we’re offering a number of tips and tricks small security operations center (SOC) teams can use. I started my career working as part of a small SOC team, and working with other security experts here at Logz.io, we’re happy to offer these to small SOC teams who can often use all the help they can get! In the last post, we talked about managing security talent and building processes.
New Vulnerability Scanning Features in Tanzu Application Platform 1.3
What is confidential computing? A high-level explanation for CISOs
Privacy enhancing technologies and confidential computing are two of my favorite topics to talk about! So much so that I am writing this blog post on a sunny Saturday afternoon. But wait, what’s that I hear you murmuring? “What is confidential computing? And how does it affect me?” Those are two very good questions.
To Thrive in the Everywhere Workplace, IT and Security Teams Need to Work Together
It’s Cybersecurity Awareness Month. For a CIO, this is like the holidays, and there’s lots to celebrate and lots to do. By reading this, you’re helping me check something off my list: I want everyone in the IT and security landscape to know how these two teams can work together for a more efficient, productive and secure enterprise. To those outside the departments, IT and security teams are often conflated.
Share secrets with standalone projects with project context restrictions
Introducing project context restrictions for GitLab organizations. This feature enables project-based restrictions on contexts for standalone projects that are not tied to a VCS. Standalone projects are available at this time only with a GitLab integration with CircleCI. In this blog post, we hope to explain the value of this feature and how it can be used to further secure your workflows.
Understanding the Different IT Security Certifications
Microsoft Zero-Day Exchange Exploits Show Value of Network Behavior Visibility
There is no end to zero-day attacks. Lessen the pain by spotting them early. In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited. The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
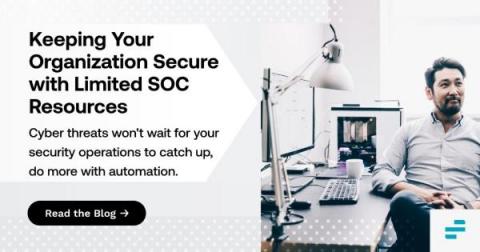
Keeping Your Organization Secure with Limited SOC Resources
Organizations face a growing threat from cybercriminals while struggling to find qualified security professionals who can protect their infrastructure and sensitive data. This blog will explore the concept of a Security Operations Center (SOC) and the role of SOC analysts in securing your organization. We will also discuss how your organization can leverage automation to improve SOC effectiveness and fill in the gaps when you cannot support a full staff of security professionals.
How to Put Software Development Security First
What are the keys to building software development security into the early stages of product development? And what are the costs of ignoring security? In this article, xMatters Product Manager Kit Brown-Watts provides his insights on the matter. Every investment decision comes with trade-offs, usually in the form of cost, quality, or speed. The CQS Matrix, as I like to call it, captures the dilemma most product people face.
How To Make A Complete And Thorough Protection For Your Business
Elastic Announces Innovations to Transform the Way Organizations Search, Observe and Protect their Data
Why IT Skills Are Vital When You're Running an eCommerce Business
Tips and Tricks for the Small SOC: Part I
Every security operations center (SOC) team is different, and for smaller teams, even small challenges can seem big. I started my career in cybersecurity as part of a smaller team, and eventually grew into a SOC role. During that time, I gained a good deal of knowledge about the dos and don’ts of what a small SOC team needs to do in order to be successful.
3 Common Misconceptions about Executive Order 14028: Improving the Nation's Cybersecurity
The United States is the #1 target for cybersecurity attacks in the world. 38% of targeted cybersecurity attacks so far in 2022 were aimed at the United States data and systems. That’s alarming. And we see it in the news almost every day. Solarwinds, Colonial Pipeline, The Pulse Secure VPN zero-day… There’s an increasing number of threats and attacks, to the tune of 15.1% year over year.
Automate Calico Cloud and EKS cluster integration using AWS Control Tower
Productive, scalable, and cost-effective, cloud infrastructure empowers innovation and faster deliverables. It’s a no-brainer why organizations are migrating to the cloud and containerizing their applications. As businesses scale their cloud infrastructure, they cannot be bottlenecked by security concerns. One way to release these bottlenecks and free up resources is by using automation.
10 steps to securing the cloud
When it comes to cloud adoption, the analogy I always use is that our networks used to be built like castles. We put all our servers and users inside, and we had big walls to protect everything. Today, we’ve shifted large parts of our businesses outside of these walls, and moved them to various cloud and SaaS providers. As a result, we no longer always have the knowledge or expertise to secure and protect them.
It's Cybersecurity Awareness Month! Here's What You Need to Know
Okay, I’ll admit it – I probably get more excited for Cybersecurity Awareness Month than most people. It’s a professional hazard. It has been 18 years since the first Cybersecurity Awareness Month, but this one feelsparticularly important.
Network Security - Making Sure VoIP Is Not A Security Risk
What Kind Of Tech Resources Are Used To Maintain Public Safety?
MSP's Guide to Customer Data Protection
Customer data protection is important to every business that wants to protect its financial security and its reputation -- but it’s even more important for managed service providers (MSPs). When talking to your clients, you’ll probably tell them that a huge reason why protecting customer data is mission critical is because their entire business depends on it.
How Puppet is making platform engineering more secure
As platform engineering continues to rise in popularity, there is a new side effect to watch out for: the people using the internal developer platforms aren't the people who built it. They’re not necessarily familiar with the codebase, they may not know what's powering it behind the scenes – and the platform might even have to contend with malicious users. So how is Puppet evolving to contend with this new challenge?
Tips for National Cybersecurity Awareness Month You May Be Overlooking
NIST Cybersecurity Framework: Core Functions, Implementation Tiers, and Profiles
Key Lessons for Building Secure and Resilient Ecosystems From the Forbes CIO Summit
Security Best Practices at MetricFire
At MetricFire, we treat your data as our data, and we secure our data. Security is prioritized at every level of our infrastructure so you can have peace of mind that your data is sent and stored safely. Keeping MetricFire secure is fundamental to the nature of our business. One of our key priorities is to secure our customers’ metrics and trust. We diligently ensure that we comply with industry security standards so that our customers can trust that their metrics are safeguarded.