Operations | Monitoring | ITSM | DevOps | Cloud
October 2023
Meeting the SEC's New Cybersecurity Rules: How Flowmon Empowers Public Companies To Comply
The much-anticipated cybersecurity rules by the U.S. Securities and Exchange Commission (SEC) for public companies have arrived, signaling a significant step forward from the proposed rules released in March 2022. These final rules, effective July 26, 2023, introduce new obligations that public companies must adhere to, promising a more secure and transparent corporate landscape. However, these regulations bring significant compliance challenges and litigation risks.
Using Cribl Search to Aid in Threat Hunting by Enriching Data in Motion
Cribl Search is reshaping the data search paradigm, empowering users to uncover and analyze data directly from its source. Cribl Search can easily reach out and query data already collected in Amazon S3 (or S3 compatible), Amazon Security Lake, Azure Blob, Google Cloud Storage, and more. By searching data where it lives, you can dramatically speed up your search process by avoiding the need to move data before analyzing it.
Cybersecurity Awareness Month: A Discussion About Cloud Security And AI
Manage and defend your IT estate like never before with Ivanti Neurons for ITSM
Implementing Backstage 3: Integrating with Existing Tools Using Plugins
This third part of the “Implementing Backstage” series explains how to integrate Backstage with existing tools and plugins. If you’re at an earlier stage of your Backstage implementation, the two previous installments in this series focus on getting started and using the core features. If you’re looking for a more general introduction to Backstage, you can read the first article in the “Evaluating Backstage” series.
Why Should You Use IT Support Services in Northern Virginia
5 Reasons Why You Should Migrate to the Cloud in 2023
SIEM Logging for Enterprise Security Operations and Threat Hunting
Today's enterprise networks are diverse and complex. Rather than the simple network perimeter of old, bad actors can attack through multiple entry points, including cloud-based applications. Not to mention, these networks generate massive amounts of transactional data. Because enterprise networks have become larger, they're more difficult to secure and manage. As a result, IT operations teams and security analysts seek better ways to deal with the massive influx of information to improve security and observability.
Migrating from Travis to Github Actions
For CFEngine we manage several public and private repositories of code in GitHub for our Open Source and Enterprise products. In order to ensure quality we run many checks on the code both with nightly builds as well as on each pull request. We use a Jenkins server for nightlies which also includes more extensive deployment tests on all of the platforms we support. Previously we had used Travis for many of these checks but that system started to show its age and limitations.
Discovering Zero Days: Why configuration management wins
“Zero Days” may be one of the most recognizable cybersecurity terms, other than hacker of course, for good reason. Zero Day Vulnerabilities are notoriously challenging for defending security teams to identify. Because of delays between active exploit and discovery, they are one of the worst examples of “Known Unknowns” in cybersecurity (Other than user’s behavior of course..). It’s important to understand that Zero Days are not really brand-new vulnerabilities.
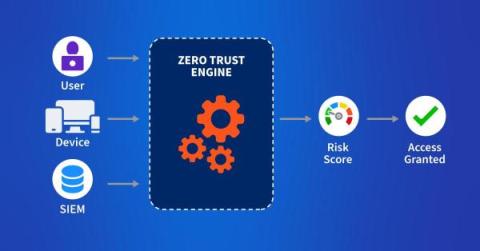
Zero-Trust Security: Best Practices for Securing the Remote Workforce
Security Observability - Vulnerability Dashboard and Risk Scorecard
Streamlining SAP Kernel upgrades with Avantra
Picture the SAP Kernel as the heartbeat of the system, vitalizing the core programs upon which the fundamental functionality of SAP applications rely on. It's the life force pulsing through the application server, executable programs, database, and operating system, rather than merely encompassing them within itself. SAP Kernel upgrades refer to updating the system's current executables with upgraded versions. These upgrades are essential to patch security vulnerabilities and fix bugs. Besides bug fixing, SAP Kernel upgrades improve hardware compatibility, boost speed, and enhance stability.
Security Webinar, Zero Trust For Users
Fighting DDoS at the Source
Secure UEM Solution Packages in 187 seconds
Death, Taxes and Phishing - Cybersecurity Research Results (Pt. 1) | Ep.33 Security Insights Podcast
How to Harden Zero-Trust Cloud Network Policy with Kentik
Zero trust in the cloud is no longer a luxury in the modern digital age but an absolute necessity. Learn how Kentik secures cloud workloads with actionable views of inbound, outbound, and denied traffic.
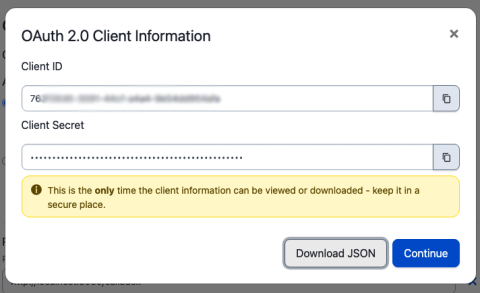
Build Sophisticated Apps for Your PagerDuty Environment Using OAuth 2.0 and API Scopes
Many PagerDuty customers create their own apps to help them manage their PagerDuty environments. Teams might have any number of workflows that might benefit from a custom application. A PagerDuty admin might want to be able to load CSV files with new users and their contact information into PagerDuty when new teams join the platform, or load new services before they are released to production.
Proactively secure your business with new Cisco Secure Application enhancements to protect cloud environments
Map, prioritize and act on security issues found in cloud environments with the newly expanded security offering from Cisco AppDynamics. Welcome to the October edition of the What’s New in Security series — and — happy security awareness month!
The DevOps Security and Compliance Guide
The fast-paced nature of modern software development means developers are capable of deploying changes to production multiple times a day. But, while DevOps allows development teams to deliver new features faster, increased deployment frequency can make it more difficult to stay on top of security threats. It only takes one malicious or incompetent change to dramatically increase the risk exposure of an application.
CFEngine: The agent is in 30 - Profiling CFEngine policy
Network Security Best Practices
A guide to maintaining a secure network.
Security Considerations in IoT PCB Design
How To Stop Norton Spam Emails
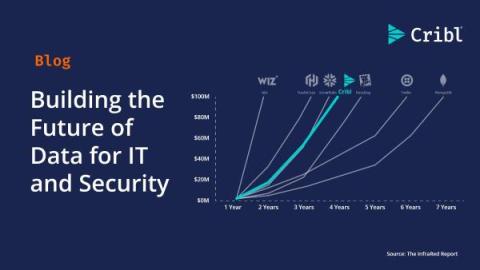
Building the Future of Data for IT and Security
Today, Cribl surpassed $100 million in annual recurring revenue (ARR), becoming one of the fastest companies to ever reach this milestone in under four years––an incredible achievement on our journey to building a generational company. Reaching $100 million in ARR so quickly shows that our unique approach and steadfast focus on IT and Security continues to be validated by the market.
The Dangers Lurking in Open Source Software
Our 1st blog in our series on securely consuming OSS. Today, I'll give an overview of some of the most common types of attacks from consuming OSS. Open-source software (OSS) fuels innovation. Over 96% of commercial applications rely on at least one OSS component (Synopsys, 2023). At Cloudsmith, we champion OSS and understand its indispensable role in today's software landscape. However, the escalating threat of supply chain attacks targeting OSS demands a robust defence.
ServiceNow Privacy Management Overview
Staying on the Right Side of HIPAA: Compliance Tips for 2023
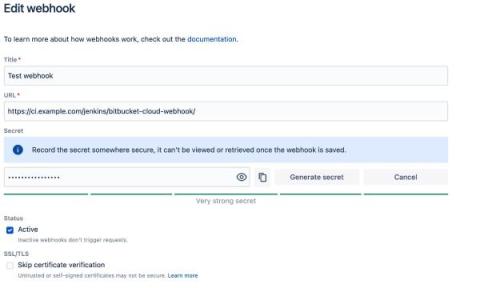
Introducing enhanced webhook security
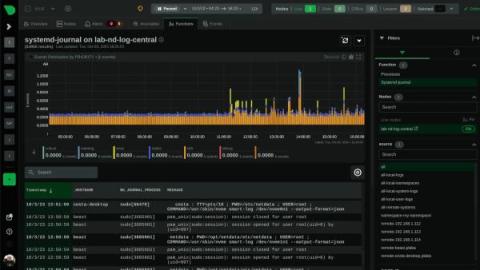
Improve Your Security With systemd-journal and Netdata
systemd journals play a crucial role in the Linux system ecosystem, and understanding the importance of the logs contained within is essential for both system administrators and developers.
Ten modern SIEM use cases
Security Information and Event Management (SIEM) protects organizational assets in today's evolving cybersecurity landscape. As threats become more sophisticated, the importance of well-structured SIEM use cases cannot be underestimated. Dive in as we explore the modern approaches to building, organizing, and prioritizing SIEM use cases. Read on to learn the right approach to building SIEM use casesGathering the Right Data for Meaningful Insights The top ten use cases you cannot afford to miss.
Optimizing SharePoint Security
In today’s digital-first business landscape, collaborative platforms like Microsoft SharePoint are not merely a convenience but a necessity. They facilitate seamless interaction, information sharing, and collective project management across geographically dispersed teams. However, the enhanced connectivity and accessibility come with a set of security challenges.
How Hackers Use Unexpected Skills
Patch Management vs. Vulnerability Management: What's The Difference?
Leveraging Tines and Cribl Search for Security Automation
At Cribl, we have the privilege of helping our customers achieve their strategic data goals by giving them visibility and control over all of their observability data. The reality today is that data is commonly stored across many places. Whether intentional (such as using Cribl Stream to create a security data lake) or unintentional (because of silos and tool sprawl), organizations desire the ability to access and analyze all of this information at any time.
What Are Network Security Devices?
Find out about different network security device types and their uses.
Why Every Business Needs a Technology-Driven Protection Plan
The red team: ServiceNow's first line of defense
If you ask any ServiceNow employee about their role, they'll likely tell you their job and team are the best they’ve ever had. One small but mighty team proclaims this proudly: the red team, a group of professional hackers. As vigilant guardians of the company, the six-person team is tasked with testing the security of our systems and identifying cyber risks, data vulnerabilities, and security threats.
Ensuring Data Security in the Digital Age: A Legal Perspective
How do you measure software security maturity?
Vendor Risk Management 101-The Imminent Threat of IoT Litter Boxes | Ep.32 Security Insights Podcast
SASE Monitoring: How to Monitor & Optimize A SASE Architecture
How to Transform the Way Your Company Manages Its IT Infrastructure
Security and compliance for enterprise collaboration
In today’s increasingly data-driven business landscape, security and compliance are more important for enterprise software than ever before. In an age where high-profile data breaches and regulatory violations seem to make headlines more frequently, enterprises must prioritize the protection of sensitive information while ensuring compliance with an exceedingly complicated labyrinth of legal and industry-specific requirements.
Learn how to secure your applications like the experts
Unpacking the Hype: Navigating the Complexities of Advanced Data Analytics in Cybersecurity
The cybersecurity industry is experiencing an explosion of innovative tools designed to tackle complex security challenges. However, the hype surrounding these tools has outpaced their actual capabilities, leading many teams to struggle with complexity and extracting value from their investment. In this conversation with Optiv‘s Randy Lariar, we explore the potential and dangers of bringing advanced data analytics and artificial intelligence tools to the cybersecurity space.
Implementing Backstage: Kubernetes Plugins
This second last part of the “Implementing Backstage” series explains how to use the Kubernetes plugin in Backstage using real-world scenarios. The previous installments covered getting started, using the core features, integrating with existing tools using plugins, and security and compliance. If you’re entirely new to Backstage and want to learn more, you can read the first entry in the “Evaluating Backstage” series.
Implementing Backstage: Kubernetes Deployment
This final part of the “Implementing Backstage” series focuses on how to deploy Backstage on Kubernetes. This tutorial is a direct continuation of Using the Kubernetes Plugin in Backstage, which you should complete before tackling this one. The other installments in this series covered getting started, using the core features, integrating with existing tools using plugins, and security and compliance.
3 Essential Mobile Apps for Optimizing Your Device
Is Technical Support Outsourcing Right for Your Business?
Phishing 2.0: Anyone lose a dog?
Semper vigilans: how Platform.sh stays ahead of emerging cybersecurity threats (so you don't have to)
October is Cybersecurity Awareness month. So, we’ve asked Diogo Sousa, Platform.sh Security team manager to share how his team contributes to helping customers protect their websites and applications from external threats, 24x7.
Implementing Backstage 4: Security and Compliance
This is the fourth part of the “Implementing Backstage” series and explores how to ensure your Backstage application is secure and how Backstage can contribute to more secure practices in general. The previous installments focused on how to get started, using the core features, and integrating with existing tools using plugins. If you’re unfamiliar with Backstage and need an introduction, check out part one of the “Evaluating Backstage” series.
Security Considerations for Your Internal Developer Platform
Can You Use the ELK Stack as a SIEM? A Fresh Take
What Is Continuous Security Monitoring Software?
Many DevOps teams work proactively to meet security and compliance standards. They consider security best practices when developing software with open source components, scanning code for vulnerabilities, deploying changes, and maintaining applications and infrastructure. Security is a key feature of many of the tools they’re using, and the policies and industry standards they’re following.
Advanced Access Controls with Mattermost Enterprise Edition
While some smaller companies may only need to use standard access controls to shore up systems, large organizations — particularly those with strict security, confidentiality, and compliance requirements — often require advanced functionality that gives them more authority over which users can access what systems and when.
Mitigating cybersecurity risks with Elasticsearch Platform
IT vs Security - When Hackers Patch for Profit | Ep.31 Security Insights Podcasts
Micro Product Demo: Ivanti Neurons for Patch Management
Practical Demo: Protect all endpoints with secure UEM countermeasures
Staying Ahead of Threats with Continuous Security Monitoring Tools for DevOps
According to the latest Crowdstrike report, in 2022 cloud-based exploitation increased by 95%, and there was an average eCrime breakout time of 84 minutes. Just as significantly, in 2021, the Biden administration passed an executive order to improve the nation’s cybersecurity standards. There are also upcoming laws like DORA in the European Union. So, increased cyber attacks and legislative pressures mean you need to (a) actively protect against threats and (b) prove that you are doing so.
Public Web Data: Main Reasons to Leverage Data in Your Business Operations
VMware Was Named an Overall Leader in Cloud Security Posture Management by KuppingerCole Analysts AG
KuppingerCole AG published its report assessing Cloud Security Posture Management (CSPM) solutions in the market for 2023. Their leadership compass helps cloud users find an appropriate solution to meet CSPM needs of an organization to monitor, assess, and manage risks associated with the use of cloud services. Fifteen vendors were assessed based on responses to a questionnaire, strategy briefing, and demo.
EventSentry in under 5 minutes
Why collaboration is vital for mature security practices and how to achieve it
Learn how collaboration fueled by business risk observability can help your teams protect what matters most. According to IDC, 750 million cloud native applications will be created globally by 2025, underscoring the seismic shift to cloud native application environments to harness the scalability and agility of the cloud.
N-able Empowers MSPs with Enterprise-Grade Security Solutions
Everything you need to know about data sovereignty
In today’s digital age, the most effective organizations are using data to fuel innovation and accelerate business strategies. Data continues to be at the heart of business growth. Organizations increasingly rely on technology to manage and store their data. Questions about ownership, control, and security have emerged — leading to the rise of a concept known as data sovereignty. In this post we’ll explore.
6 Ways Cloud-based Computerized Accounting Systems Can Help Small Businesses
Exploring the Summer of Zero-Days - SolarWinds TechPod 079
(Crowd)Strike While the Data Is Hot: Getting Started with CrowdStream, Powered by Cribl
In today’s landscape, what’s considered security data has expanded to encompass more diverse data types like network data, behavioral analytics, and application metrics. These sources are now essential for a comprehensive security strategy, and visibility into all that data makes proactive threat detection possible. That said, organizations often struggle to process data from various vendors and merge telemetry sets to gain a complete view of their environments.
6 Things to Keep in Mind When Choosing Software for Your Business
Deter Phishing Attacks
Calico monthly roundup: September 2023
Welcome to the Calico monthly roundup: September edition! From open source news to live events, we have exciting updates to share—let’s get into it!
Follow These Smart Steps And Secure Protocols For Business Applications
Future-Proof Your Observability Strategy With CrowdStrike and Cribl
Traditional logging tools are struggling to keep up with the explosive pace of data growth. Data collection isn’t the most straightforward process — so deploying and configuring all the tools necessary to manage this growth is more difficult than ever, and navigating evolving logging and monitoring requirements only adds another layer of complexity to the situation.
Prepare your Website for Black Friday
In this video, we'll be discussing to find out more, visit: https://www.rapidspike.com/black-friday/
How to Protect Vital Cloud Systems from Cyber Attacks
In today's digital era, cloud computing has become the backbone of numerous businesses. Cloud systems have become the go-to choice for many organizational needs thanks to advantages like unparalleled scalability, accessibility, and cost-effectiveness. Still, the rapid surge in cloud adoption has attracted the attention of cybercriminals. According to a report from Netwrix, 68% of organizations experienced at least one cyber attack incident in the past year.
How to Identify Your Organization's Attack Surface
Our glossary page on attack surfaces defined the terms associated with the concept. This post provides information that'll help your organization identify its attack surface. Much like your lawn after a good rain, your attack surface will grow rapidly if left unchecked. Along with increases in attack surface size comes an increase in cybersecurity risk. That risk can’t be eliminated as attack surfaces are always evolving, but it must be carefully managed.
Important Situations Every Business Owner Should Be Aware Of
Implementing Backstage 2: Using the Core Features
This article is the second installment of the “Implementing Backstage” series and focuses on how to use Backstage’s core features. Backstage has an extensible plugin architecture in active development and large community support and offers simplified tool management, workflow optimization, and time-saving features. However, to reap these benefits, you need to know how to use Backstage’s core features, including its software catalog, templates, documentation, and search.
Configure a policy to detect and block attacks and exploits
10 Essential Office Security Upgrades for the Digital Age
EventSentry v5.1 - New Features
Zenbleed vulnerability fix for Ubuntu
Which Gen Is Most Tech-Savvy? A Workforce Dilemma
Part one of a four-part series covering Ivanti’s latest research. Get the full series: According to new cybersecurity research by Ivanti, the employees who are the most tech-savvy aren’t necessarily the ones we’d presume, demographically speaking. Why is that? And what are the issues it creates for an enterprise?
Red Flag Reluctance: The Risk to Cybersecurity
Part two of a four-part series covering Ivanti’s latest research. Get the full series: Keeping an organization safe means getting near-real-time information about security incidents or breaches. But new research shows some employees are less inclined than others to report red flags, which puts your business at risk. Will your employees get in touch quickly if they have a security concern?
International Inconsistencies: How Cybersecurity Preparedness Varies Across Countries
Part three of a four-part series covering Ivanti’s latest research. Get the full series: An organization’s culture and training programs have a significant influence on security preparedness, but our research shows both are inconsistent at the country-to-country level. As we’ve seen in the previous posts in this series, employee demographics and their willingness to report security risks are hidden threats to your cybersecurity posture.
Taking a Real Look at Hidden Risk
Part four of a four-part series covering Ivanti’s latest research. Get the full series: Big-picture excellence can hide pockets of risk. It’s time to explore security risk in detail — drilling down to look at vulnerabilities hidden in the data and by taking preventative action.
Your Tokens, Your Control
In today’s fast-paced development environment, managing your project access tokens efficiently is more crucial than ever. That’s why we're excited to unveil a series of upgrades to Rollbar’s Project Access Token user interface to streamline your workflow and enhance your project’s security.
7 Cybersecurity Statistics You Needs to Know in 2023
Cybersecurity isn’t just at the top of the discussion queue within the IT channel. Businesses and governments worldwide have turned a sharp eye toward rising cyber threats and cybersecurity statistics. Many have learned the hard way that small businesses are frequent targets of cyberattacks. The idea of “targeting a victim” itself has come into question, and more realize that widespread, indiscriminate attacks are the status quo.
Top DevOps Experts offer Key Insights at swampUP
Double Down on Your Backups
Best practices for creating custom detection rules with Datadog Cloud SIEM
In Part 1 of this series, we talked about some challenges with building sufficient coverage for detecting security threats. We also discussed how telemetry sources like logs are invaluable for detecting potential threats to your environment because they provide crucial details about who is accessing service resources, why they are accessing them, and whether any changes have been made.
SSO is now available
Fighting the Good Fight for a Resilient Digital Future
This Cybersecurity Awareness Month, cybercriminals have far too much to celebrate. Attacks are rising in sophistication and brazenness, and no company or organization is immune. We could panic. Or we could lock arms, fight the good fight and put customers first. I vote for the latter.