Operations | Monitoring | ITSM | DevOps | Cloud
March 2023
Enreach for Service Providers partners with Netaxis Solutions to provide a converged environment for all UC systems and apps
Megaport LIVE: How to Optimize Hybrid Cloud Deployments
Smooth Sailing: Ensuring Reliable Connectivity with Azure ExpressRoute Monitoring
Are you ready to set sail on a journey to reliable connectivity with Microsoft Azure ExpressRoute monitoring? Just like navigating the seas, sailing in the cloud can be a bumpy ride if you don't have the right tools to keep your ship on course. But fear not, because we're here to help you chart a course to success with Azure ExpressRoute monitoring!
Announcing HAProxy Enterprise 2.7 & HAProxy ALOHA 15
HAProxy Enterprise 2.7 and HAProxy ALOHA 15 are now available. Users of our enterprise-class software load balancer and hardware/virtual load balancer appliance who upgrade to the latest versions will benefit from all the features announced in the community version, HAProxy 2.7, plus the ability to serve applications using HTTP/3 over QUIC. If you want to start the upgrade procedure straight away, go to the upgrade instructions for HAProxy Enterprise and HAProxy ALOHA.
The High Price of Internet Disruptions: New Study Reveals the Financial Impact on eCommerce Companies
Internet disruptions can be a real headache for any organization, but for eCommerce companies in particular, they’re proving to be a lot more than just an inconvenience. A new study by Forrester Consulting is bound to send shockwaves through the industry by quantifying the actual cost of Internet disruptions. Spoiler alert: it’s higher than you think.
Reinforcing Networks: Advancing Resiliency and Redundancy Techniques
Resiliency is a network’s ability to recover and maintain its performance despite failures or disruptions, and redundancy is the duplication of critical components or functions to ensure continuous operation in case of failure. But how do the two concepts interact? Is doubling up on capacity and devices always needed to keep the service levels up? The truth is, designing a network that can withstand the test of time, traffic, and potential disasters is a challenging feat.
Dealing with Unknown Threats
The cybersecurity threat landscape facing every organization is constantly changing. Cybercriminals are always looking for new vulnerabilities to exploit or changing existing attack methods to bypass protections. They also go to great lengths to hide their activities within regular network traffic and application activity. The attack surface that organizations present to attackers is also in a constant state of flux.
The Comprehensive Guide to SNMP
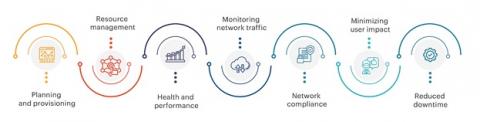
What is Network Operations?
While your approach to network operations (NetOps) is critical to business performance, the challenges of managing the needs of a modern network can keep Infrastructure & Operations (I&O) teams from helping their organization reach its full potential. Here’s what you need to know about NetOps to meet those challenges head on.
Identifying Layer 7 application traffic to optimize WAN links
Network administrators around the globe are very concerned about the types of traffic in their networks. They want their critical business applications over the WAN to perform at their best. Non-critical apps, like social media apps, downgrade the performance of WAN links. Therefore, administrators should have the necessary controls to prioritize business applications on WAN links.
7 Ways to Prevent Network Security Breaches in the Workplace
Network security breaches are every business’s nightmare. A security breach could be anything from password attacks with further unauthorized system access to data leakage. Whether it is a small start-up or a large enterprise with millions of dollars in turnover, a single network security breach can be detrimental to the reputation of any company, not to mention the financial losses incurred. According to the 2021 Thales Data Threat Report, 45% of US companies suffered a data breach in 2020.
The Watchful Eye: Microsoft Network Monitoring for Microsoft Teams, Office 365 & Azure
Do you ever feel like someone's watching you? Well, when it comes to your company's network, you should hope so! With so many people relying on Microsoft Teams, Office 365, and Azure to keep their businesses running smoothly, it's more important than ever to keep a watchful eye on your network. But who has the time to monitor everything 24/7?
Monitor Calico with Datadog
Calico is a versatile networking and security solution that features a plugable dataplane architecture. It supports various technologies, including Iptables, eBPF, Host Network Service (HNS for Windows), and Vector Packet Processing (VPP) for containers, virtual machines, and bare-metal workloads. Users can employ Calico’s network security policies to restrict traffic to and from specific clusters handling customer data and to quickly block malicious IP addresses during external attacks.
Diving Deep into Submarine Cables: The Undersea Lifelines of Internet Connectivity
Under the waves at the bottom of the Earth’s oceans are almost 1.5 million kilometers of submarine fiber optic cables. Going unnoticed by most everyone in the world, these cables underpin the entire global internet and our modern information age. In this post, Phil Gervasi explains the technology, politics, environmental impact, and economics of submarine telecommunications cables.
The 2023 Network IT Management Report Part 4: Solutions for End-Users
How to get the client IP in ASP.NET Core even behind a proxy
Part of implementing an error monitoring platform like elmah.io is dealing with the IP addresses of the clients generating errors. In this post, I'll show you parts of how we have implemented this in ASP.NET Core, to make sure that different hosting scenarios still produce the correct IP address. Let's jump right in. ASP.NET Core supports getting the client IP directly on the HttpContext object available throughout various places.
What Is Network Discovery?
There’s a reason why the network monitoring market reached about $2 billion in 2019 and is expected to reach $5 billion by 2026. In today’s tech-focused world, organizations require network monitoring to secure and manage their IT infrastructures. One of the crucial systems that every network monitoring and management operation needs to succeed is known as network discovery.
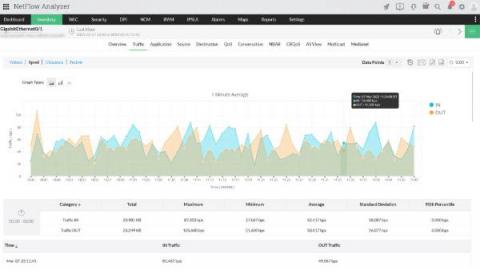
NetFlow: Application metrics | Online help Site24x7
How to Monitor Network and Zoom Performance & Fix "Your Internet Connection is Unstable" on Zoom
Laggy video, packet loss, and jitter make it difficult to have a clear and coherent conversation over Zoom - which is why it’s important to identify these Zoom issues before your next call. In this article, we’re teaching you how to monitor network performance and Zoom performance to help you have the clearest Zoom experience, and fix “Your Internet Connection is Unstable.”
Digital Transformation Drives a New Cloud Era
To understand the cloud computing landscape today and what true digital transformation looks like, we should first understand how we got here.
Lessons from hybrid working: Are businesses and networks coping?
Navigating the Cloud: A Fun Guide to AWS Direct Connect Monitoring
Welcome to the cloud! As businesses and organizations continue to adopt cloud computing, the need for reliable and secure connectivity has become increasingly important. That's where AWS Direct Connect monitoring comes in, allowing you to establish a private, high-speed connection between your on-premises data center and your AWS cloud resources. But, as with any network connection, there are bound to be performance issues and configuration challenges along the way.
How to Build a Cybersecurity Culture in Your Business
In IT, the latest tools are a must to keep companies safe. But here’s why culture is just as important – and how you can foster a safer workforce.
How Are SASE and SD-WAN Related?
Mythbusting IPv6 with Jan Zorz
IPv6 was developed in the late 1990s as a successor to IPv4 in response to widespread concerns about the growth of the Internet and its potential impact on the existing IPv4 address protocol, in particular potential address exhaustion. It was assumed that after some time as a dual-stack solution, we would phase out IPv4 entirely. Almost twenty-five years later, however, we are approaching full-scale depletion of IPv4 addresses, in part because the adoption of IPv6 is still lagging.
Top 10 Tips for Microsoft Teams in 2023
Ingesting and managing your Nginx Logs in Elastic
Tame The Congestion Jungle: A Guide to Network Congestion Monitoring
KCD France Roundup: HAProxy Evolving Alongside Kubernetes and Cloud-native Community
HAProxy Technologies attended Kubernetes Community Days France 2023, where 800 participants gathered to discuss cloud-native and DevOps technologies. It’s always a delight to interact with the heart of the industry and hear how professionals and hobbyists are implementing HAProxy as an ingress controller, load balancer, API gateway, and security solution. If we summarized KCD France 2023 in one word, it would be “community.”
Ensure Network Uptime with DNS Monitoring
Have you ever wondered how the internet manages to translate the domain names you type into the browser into IP addresses that connect you to your desired websites? The answer lies in the Domain Name System (DNS), a complex network of servers and protocols that makes online communication possible. But with this complexity comes the need for DNS monitoring, which plays a crucial role in ensuring website availability, preventing security breaches, and optimizing network performance.
How to Avoid The Network Traffic Jam: What is Network Congestion and How to Fix It
Modernized Communications Needed For A Smooth Evolution To Smart!
As I’ve discussed in my previous blogs in this series, smart networks are becoming increasingly important in an ever-increasing range of industries. These smart networks can deliver significant benefits, but there are some risks, challenges and issues associated with moving to “smart”. In my final blog in the series I will discuss what is required from a modernized communications network to counter some of these risk, challenges and issues.
Weathering the IT Storm
Taking the Next Transformation Step With Telco Cloud
With communications evolving at a dizzying pace, service providers of all stripes are challenged to adopt the latest technologies and reshape their businesses for the new world. Telco Cloud, an area Ribbon is deeply focused on, is one of the key components in helping operators transform successfully.
How To: SLA Monitoring & Reporting
Are you tired of feeling like you're in the dark about the services you're paying for? Are you getting what you paid for? Many businesses are in the same boat when it comes to Service Level Agreement (SLA) monitoring and reporting. It’s great having an SLA (or Service-Level Agreement) for the provision of a service, but you need to go further to really understand if the standards specified in the SLA are actually being met. That’s where SLA monitoring and reporting comes in.
IT Operations in 2023: Mapping IT to Business Goals
Welcome to 2023! As we transition from 2022 — which in many ways was exciting for undesirable reasons such as the lingering pandemic, conflict in Ukraine, and uncertain economic conditions — I am eager to look ahead to anticipate themes that will affect IT or, more specifically, IT Operations. As vendors, customers, and practitioners, we’ve worked in IT through many eras of disruption.
The Need for Speed: How to Troubleshoot Network Slowness and Boost Your Connection
What Does It Mean To Build a Successful Networking Team?
What does it mean to build a successful networking team? Is it hiring a team of CCIEs? Is it making sure candidates know public cloud inside and out? Or maybe it’s making sure candidates have only the most sophisticated project experience on their resume. In this post, we’ll discuss what a successful networking team looks like and what characteristics we should look for in candidates. What does it mean to build a successful networking team?
Network Optimization Strategies: How to Optimize Network Performance
Optimizing your network is the key to help improve network performance. It helps provide optimal performance of your Internet, VPN, Firewall, VoIP and UC apps, and most importantly - your user experience. Keep reading to learn how to optimize network performance for continuous network optimization.
Why the Rail Communications Infrastructure Must Be Brought Into the 21st Century
Rail operators rely on their communications network to support an increasing and varied set of both legacy and modernized systems to improve safety, reduce carbon footprint, manage expanding freight and passenger loads, increase customer satisfaction, grow profitability, and comply with regulation.
Embark on an Epic Adventure: Mastering Viptela Network Monitoring Tools
The security challenge facing global IoT projects
That's My Slice!
How to Measure Latency: The Need for Speed (or Lack Thereof)
When monitoring network performance and health, latency measurements help you understand how quickly, or slowly, data is traveling across the network. This is why network latency monitoring is important to your overall network performance. In this article, we’re teaching you how to measure network latency using Obkio Network Monitoring.
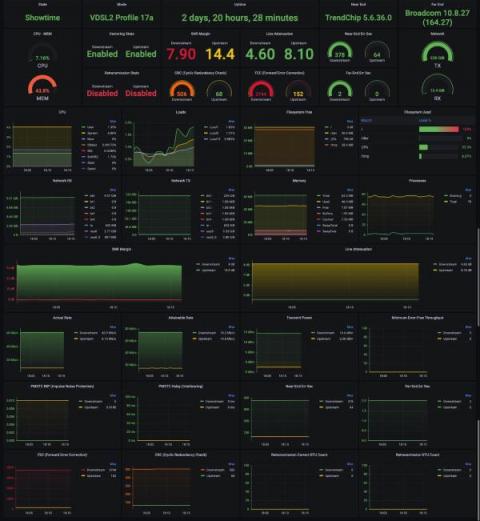
How to monitor an xDSL Modem using a Prometheus Exporter plugin and Grafana Agent on Grafana Cloud with Grafana OnCall
Furkan Türkal likes to design and implement new tech stacks with a deep focus on distributed and low-level systems. He is interested in contributing to open source projects, communities, and project management, and has a strong interest in the CNCF world! Recently, he has been doing research on Supply Chain Security. Hardware breaks, just like our hearts — and both can be due to complicated situations.
The Fast and the Frustrated: A Guide to Troubleshooting and How to Improve Latency
How I used Graylog to Fix my Internet Connection
In today’s digital age, the internet has become an integral part of our daily lives. From working remotely to streaming movies, we rely on the internet for almost everything. However, slow internet speeds can be frustrating and can significantly affect our productivity and entertainment. Despite advancements in technology, many people continue to face challenges with their internet speeds, hindering their ability to fully utilize the benefits of the internet.
The Velocloud Network Monitoring Jigsaw Puzzle: Putting Your Network Pieces Together
Securing Your Network Against Attacks: Prevent, Detect, and Mitigate Cyberthreats
As networks become distributed and virtualized, the points at which they can be made vulnerable, or their threat surface, expands dramatically. Learn best practices for preventing, detecting, and mitigating the impact of cyberthreats. As networks become distributed and virtualized, the points at which they can be made vulnerable, or their threat surface, expands dramatically.
How to Detect and Identify Intermittent Network Problems
We talk a lot about intermittent network problems. There’s a reason for that. Many network problems are intermittent, which means that they are sporadic, and much more difficult to pinpoint and troubleshoot than constant network problems. Picture this: You're in the middle of an important video conference call with a potential client when suddenly your network connection drops, leaving you stranded and looking like a pixelated mess on the other end. Sound familiar?
PC Pro Gives WhatsUp Gold Five Stars, Adding to Accolades
Popular computer magazine PC Pro added WhatsUp Gold to its "A List" of products for advanced features and ease and affordability of licensing, awarding it five stars in its review. WhatsUp Gold, first launched in 1996, has been growing in features and refinements for the past 27 years. More recently, the IT infrastructure monitoring (ITIM) solution gained capabilities another way.
The importance of baseline configuration management in a network
In a network environment, configurations are often considered of incalculable value because a small change in a device’s configuration can make or break the entire network infrastructure in minutes. These configurations are divided into two parts: startup and running configurations. In a network device, the first configuration version, by default, is considered the baseline version (a stable and efficient configuration) for both running and startup configurations.
How Taking Inventory of Your Network's Assets Can Benefit Your IT Workers
The ABCs of IT Infrastructure Monitoring (ITIM)—the Letter I is for Inventory of Assets. "Doing inventory" is probably one phrase retail and hospitality workers loathe. For many workers in these jobs, physically counting items can sometimes be an overnight job. For others in similar positions, it can make for an arduous all-day task while tending to customers' needs. However, despite the time it takes, it is still essential. How else will managers know which items to order for their store?
Network Performance Monitoring Tools: Choose Your Fighter - Network Edition
IT Infrastructure Management Services
Network traffic analysis: A brief report on significant network performance monitoring avenue
Most corporate IT landscapes have a variety of traffic types involved, like cloud, web, and video. With network endpoints interconnected, the performance and risk of handling these traffic types can also increase. Although major solutions can detect threats with predefined signatures, detecting newer attacks requires focusing on communications such as those from API or SaaS applications.
Squadcast + Auvik Integration: Routing alert made easy
How to Perform a Network Assessment Like A Network Detective
Are you ready to put on your detective hat and become a master network sleuth? We rely on our network to be the backbone of our businesses. From your Internet, to your VPN, to running VoIP and Unified Communication applications (like Zoom), networks have large responsibilities. But how can you know if your network is performing as it should be? That’s when you perform a network assessment.
How to Use WhatsUp Gold Device Groups
Today's Enterprise WAN Isn't What It Used To Be
For most enterprise NetOps teams, a discussion about the WAN is a discussion about the cloud. Whether it’s as simple as ensuring solid connectivity with a SaaS provider or designing a robust, secure, hybrid, and multi-cloud architecture, the enterprise wide area network is all about connecting us to our resources, wherever they are.
The Evolution of Network Visibility
Getting Started with Instant Evaluation
What is Latency? The Hitchhiker's Guide to the Latency: Why it Matters, and How to Minimize It
Shooting for the Stars: Achieving Optimal Network Performance through Cisco SD-WAN Network Monitoring
DX UIM for Hybrid Cloud Environment Monitoring and Management
What's New With Megaport's Services
Here’s everything you need to know about Megaport’s latest service enhancements.
Why Grouping Devices Is So Critical for IT Infrastructure Management
135,000 is the average number of endpoint devices connected to an enterprise network. The estimate is in a joint report from Adaptiva and the Ponemon Institute, along with several other surprising statistics: A common challenge facing IT professionals is gaining insight into the devices connected to their network. With so many devices being used by employees, managers and IT workers, a solution to categorize and analyze these devices in one spot is essential.
Become a Hero: How to set up Fortigate SD-WAN Network Monitor and Save the Day!
Using Device Telemetry to Answer Questions About Your Network Health
When coupled with a network observability platform, device telemetry provides network engineers and operators critical insight into cost, performance, reliability, and security. Learn how to create actionable results with device telemetry in our new article. For cloud network specialists, the landscape for their observability efforts includes a mix of physical and virtual networking devices.
5 Tips to Improve Network Security Monitoring
Optimizing network security monitoring requires pursuing continuous improvement. Even when people have monitoring tools or processes, it’s always advisable to identify weak spots and look for ways to reduce or eliminate them. Here are five options to consider.
N-able Propels Diversity, Equality, and Belonging Efforts with Participation in Chief
6 hacks for your enterprise's network bandwidth usage checking
Enterprises that want to improve the performance of their network often look into limiting access to bandwidth-hogs such as social media and video streaming applications. But for those that really need to gain efficient network, this won’t be enough. You need to keep track of bandwidth usage regularly. While there are many tools to help you check bandwidth usage on network, sometimes finding KPIs specific to your organization can be painstaking.
Save network costs with VictoriaMetrics remote write protocol
Prometheus remote write protocol is used by Prometheus for sending data to remote storage systems such as VictoriaMetrics. See these docs on how to setup Prometheus to send the data to VictoriaMetrics. This protocol is very simple - it writes the collected raw samples into WriteRequest protobuf message, then compresses the message with Snappy compression algorithm and sends it to the remote storage in an HTTTP POST request.
Get your Network in Fighting Shape with The Right Tools for Fortinet SD-WAN Monitoring
The Rise of the Cognitive NOC and the Role of IT Process Automation
Today’s Cognitive Network Operations Center (Cognitive NOC) is a significant advancement that employs artificial Intelligence (AI) and machine learning (ML) to dramatically modernize and improve network management and operations. Working together, the NOC and IT Process Automation (ITPA) propel superior efficiency and effectiveness of network operations, minimize downtime, lower operational costs, and overcome additional challenges in optimizing network performance.
Data Gravity in Cloud Networks: Distributed Gravity and Network Observability
So far in this series, I’ve outlined how a scaling enterprise’s accumulation of data (data gravity) struggles against three consistent forces: cost, performance, and reliability. This struggle changes an enterprise; this is “digital transformation,” affecting everything from how business domains are represented in IT to software architectures, development and deployment models, and even personnel structures.
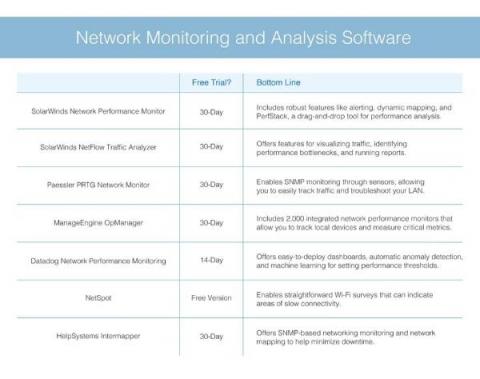
Network Monitoring and Analysis Software
Bypassing Network Detection with Graftcp
What is the difference with similar tools? Detect graftcp with Falco Conclusion A new network open source tool called graftcp (GitHub page) has been discovered in everyday attacks by the Sysdig Threat Research Team (TRT). Nowadays, threat actors try to improve their techniques by using new tools (as we mentioned in the PRoot article) to enhance the compatibility of their code to hit as many targets as possible and hide their traces properly.
IaaS, NaaS, PaaS, and SaaS: How Are They Different?
With a range of network and computing capabilities now offered via the cloud, it can be tricky to keep up. We explain the four core “as a service” offerings and their use cases.
Next Play 2023 - A New Stage of Leadership at Auvik
SD-WAN Monitoring Survival Guide: Be the Master of Your Network
How We're Using AI and ML to Improve Cloud Management
With artificial intelligence and machine learning in the news of late, what might they mean for cloud computing? Michael Vitale explains how we’re positioning these technologies to benefit our customers.
What Is the Network Operations Center (NOC): A Brief Overview
The true financial harm of downtime is significant. As of Aug 11, 2022, each minute costs an average of $9,000, according to the Ponemon Institute, raising the downtime cost per hour to over $500,000. It goes without saying that network outages hurt revenue, kill productivity, and harm the corporate brand, as well as the reputations of professionals who may be dragged into the mess.
HAProxy Fusion Has Landed
This is a big one. HAProxy Fusion Control Plane is here to give our customers the power to simplify, scale, and secure their HAProxy application delivery infrastructure using a centralized control plane. HAProxy Fusion enables your business to scale up, launch new products faster, and improve security and resilience.