Operations | Monitoring | ITSM | DevOps | Cloud
May 2023
HAProxy Fusion 1.1 Enables Application Delivery at Scale
HAProxy Fusion Control Plane gives you power to simplify, scale, and secure your HAProxy Enterprise infrastructure using a centralized orchestration solution, making it easier to extend HAProxy Enterprise’s security and performance across on-premises and cloud-hosted applications. With the release of version 1.1, HAProxy Fusion is more secure, more flexible, and even easier to use.
Announcing HAProxy 2.8
HAProxy 2.8 is now available, and HAProxy Enterprise 2.8 will be released later this year. Register for the live webinar HAProxy 2.8 Feature Roundup to learn more about this release and participate in a live Q&A with our experts.
What is Palo Alto Panorama?
How to Diagnose Internet Problems in Your Network
In today's digital age, a reliable and high-speed Internet connection is vital for the smooth operation of businesses. From communication and collaboration to accessing cloud-based services and online transactions, a stable internet connection is crucial for ensuring productivity and efficiency. However, despite the advancements in technology, network issues can still arise, leading to frustrating downtime and hampering business operations.
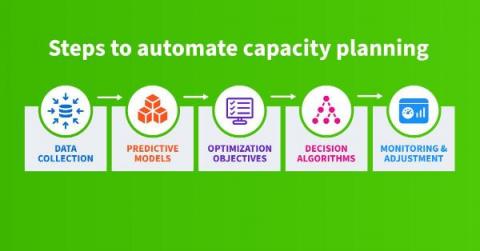
Automating Capacity Planning for IP Networks: A Journey into the Future
By automating capacity planning for IP networks, we can achieve cost reduction, enhanced accuracy, and better scalability. This process requires us to collect data, build predictive models, define optimization objectives, design decision algorithms, and carry out consistent monitoring and adjustment. However, the initial investment is large and the result will still require human oversight.
Top strategies for Network Performance monitoring
Networks today span the world and provide many connections between geographically disparate data centers, and public and private clouds. This creates a variety of network management problems. If your network is not working properly, it can be very difficult or even impossible to get the most productive or correct operation of your applications. A sophisticated network requires constant monitoring using the right tools and creating a network performance monitoring strategy.
Top network switches to use
When you set up on-premise digital infrastructure, it is crucial to enable your devices to communicate with each other. The devices on your network should be able to send and receive data packets to handle requests and send responses back to callers. One of the components that allow data transmission to the proper destination is the network switch. The network switch plays an important role in distributing data packets to devices.
What Is BGP and Why Is It Important?
When you send an email or load a website, you probably never think about how the data gets from your computer to the server that needs to process it. But something does have to decide how the data will move across the vast expanse of the Internet – and, in particular, which of the virtually infinite number of potential routes your data will take as it moves from your device to a server and back again.
Always Empowering: We are SolarWinds
Mastering Kubernetes Networking with Cilium
In a recent meetup I hosted alongside Kunal Kushwaha, we discussed Cilium, an eBPF-powered open-source cloud-native networking solution that offers security, observability, scalability, and superior performance. Throughout this blog I will explore how the increased usage of Kubernetes has led to the need for advanced networking, security, and observability solutions. This will allow us to take a closer look at how Cilium can benefit Kubernetes users.
Monitor your firewall logs with Datadog
Firewall systems are critical for protecting your network and devices from unauthorized traffic. There are several types of firewalls that you can deploy for your environment via hardware, software, or the cloud—and they all typically fall under one of two categories: network-based or host-based. Network-based firewalls monitor and filter traffic to and from your network, whereas host-based firewalls manage traffic to and from a specific host, such as a laptop.
Understanding MTTR Networking: How to Improve Incident Response Time
As organizations continue to shift their operations to cloud networks, maintaining the performance and security of these systems becomes increasingly important. Read on to learn about incident management and the tools and strategies organizations can use to reduce MTTR and incident response times in their networks.
What is End-to-End Network Monitoring?
24 Best End-to-End Network Monitoring Tools for 360-Degree Network Visibility
Ribbon Launches Ribbon Connect for Zoom
What to Consider for Monitoring Network Latency
In a perfect world, data would move over the Internet in real time. There would be no delays whatsoever between when one computer sends data out over the network and when it reaches the recipient. In the real world, however, there is always some level of delay when exchanging data over the network. That delay is measured in terms of network latency. Ideally, network latency is so low that no one notices it.
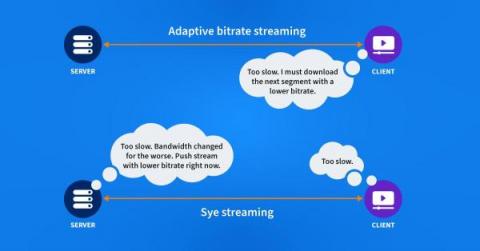
The Subtle Details of Livestreaming Prime Video with Embedded CDNs
Live sports have moved to the internet and are now streaming instead of being broadcast. Traditional streaming protocols have a built-in delay that challenges the experience of a live game. Amazon Prime has found a solution by combining a new protocol with a very distributed CDN.
Traceroute InSession: Catchpoint's effort towards a more reliable network diagnostic tool.
Since its inception in 1988, the traceroute has undergone several variations. You might be wondering, ‘Why so many?’ The answer is simple: achieving traceroute functionality has been a balance between security and utility. Whenever malicious actors exploited firewall and router vulnerabilities, their vendors responded with fixes and solutions which impacted the traceroute algorithms.
A Guide to Different Types of Network Monitoring Tools: Unveiling the Superheroes
Using Cisco Meraki Solution for SD WAN? ScienceLogic Was Built for That.
Since its acquisition by Cisco in 2012, Meraki has taken off as one of the most valuable tools for simplifying networking in the cloud era. Organizations using Meraki to install and configure software-defined networking (SDN) and software-defined wide area networking (SD-WAN) devices across their IT estates can attest to the fact.
The Power of Peer-To-Peer Networks and the Rise and Fall of Limewire
How to Achieve End-to-End Visibility Within Network Infrastructure
In March 2021, Commander of the United States Cyber Command General Paul Nakasone testified before the U.S. Senate, summarizing a key organizational challenge, "It's not that we can't connect the dots; we can't see all of the dots."
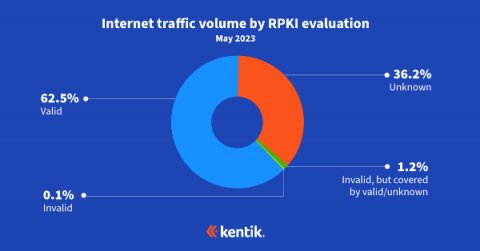
Exploring the Latest RPKI ROV Adoption Numbers
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly update their RPKI ROV analysis from last year while discussing its impact on internet routing security.
How To Diagnose Wireless Network Issues Like a Pro - Check These 4 Things First
Covering your bases: three ways to achieve network visibility
N-able Collaborates with JCDC to Help Create a More Secure Global MSP Ecosystem
5 Steps to Get Telemetry Data in DX NetOps
This practitioner blog will show you how to consume telemetry data from your network devices in five easy steps. Telemetry is a monitoring technology used to do high-speed data collection from network devices. According to EMA research on network performance management, “71% of enterprises are interested in collecting streaming network telemetry with their network management tools.” This next-generation approach to monitoring has been expected to replace SNMP for years.
How can companies improve Network and API performance?
In this bi-weekly micro webinar series, Catchpoint and ITOps Times have partnered to explore six critical topics that are essential for ensuring Internet Resilience for your business. Explore each of the topics in the series: In this fourth segment, we’ll discuss techniques for enhancing Network and API performance by implementing Internet Performance Monitoring. Now, let’s get into the episode!
Making Peering Easy: Announcing the Integration of PeeringDB and Kentik
Peering evaluations are now so much easier. PeeringDB, the database of networks and the go-to location for interconnection data, is now integrated into Kentik and available to all Kentik customers at no additional cost.
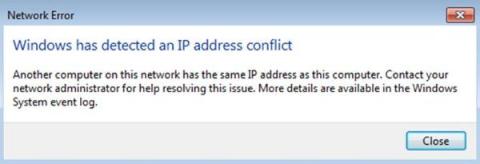
What's an IP Address Conflict, and How Do You Fix It?
What Is Workload Automation Observability?
As workload automation environments become more complex and job volumes increase, the need for true observability is becoming an increasingly essential and critical component for optimized automated business process delivery. Most organizations run several automation engines from different vendors in both distributed and mainframe environments, and in the cloud. Sometimes these automation engines operate in a silo, sometimes they have dependencies with each other.
What is Remote Network Monitoring: Network Optimization In The Remote Work Era
Can Network Monitoring Identify Security Threats? Here's What to Know
By continuously monitoring network activity and assets, network monitoring plays a key role in identifying cybersecurity threats. The network monitoring process gathers important data that can be used in analytics or in conjunction with cybersecurity applications to rapidly identify and respond to threats.
Troubleshooting SD-WAN Performance Problems
Software-Defined Wide Area Network (SD-WAN) technology is revolutionizing the way organizations manage their network traffic. With its ability to decouple the data plane from the control plane, SD-WAN provides organizations with a more flexible, scalable, and cost-effective solution for managing their network traffic. However, understanding and troubleshooting SD-WAN performance can be a challenge, especially when it comes to the underlying physical network, or underlay.
How to Decode the Hidden Information from Traceroute DNS
N-able Strengthens Diversity, Equality, and Belonging Commitment by Signing the CEO Action for Diversity and Inclusion Pledge
Securing the Enterprise from VoIP Network Attacks with Analytics
Voice over IP (VoIP) technologies and solutions have been widely adopted by consumers, businesses and service providers since the mid-2000s, but the rising popularity of remote work means businesses of all sizes are even more rapidly turning to VoIP for voice calls.
From logs to insights: Using Firewall Analyzer to monitor Squid proxy activity
Squid proxies are among the most popular open-source proxy servers preferred by companies across the globe to keep their networks safe and boost performance. Since Squid proxy’s release in 1996, companies have preferred it for its high-performance proxying, forwarding, and caching functions. Squid proxy logs contain information about the HTTP traffic passing through a server. This includes the source IP, destination IP, time of the request, and accessed URL.
Eliminating the Monitoring Blind Spots Introduced by ISP Networks
ISP networks are the connective tissue for most business traffic today. Are your network monitoring capabilities aligned with this new reality? This post examines why it’s so critical to establish visibility into ISP networks, and offers key tips for success.
Defined and Explained: IT Infrastructure Monitoring
Modern IT environments and networks are more complicated and distributed than ever before, spanning public clouds, private clouds, edge locations and on-premise data centers. What once worked well—manual or simple monitoring tools—can no longer ensure end-to-end visibility within complex networks. How can you monitor what you can’t see? Fortunately, you now have access to a new generation of monitoring tools designed for the hybrid network.
Mind Your MANRS: A Safer Internet Through Secure Global Routing
We access most of the applications we use today over the internet, which means securing global routing matters to all of us. Surprisingly, the most common method is through trust relationships. MANRS, or the Mutually Agreed Norms for Routing Security, is an initiative to secure internet routing through a community of network practitioners to facilitate open communication, accountability, and the sharing of information.
Perfecting the Customer & Employee Digital Experience featuring TMNAS
Unlocking the Power of Azure: Top 36 Solutions for Azure Monitoring Tools
The Experience Watchtower: Top 22 Digital Experience Monitoring Tools
Network Connection Monitoring 101: Your Path to Network Nirvana
SolarWinds Adds Transformative AI Features to IT Service Management Solutions
Overcoming performance bottlenecks by enhancing visibility
Are you a network admin who gets overwhelmed by the number of devices they have to manage? We can only imagine the plight you have to go through. Technological advancements have extended the scope of network monitoring. Way beyond the conventional norms of preventing downtime, network monitoring in today’s context is about maintaining the optimum performance of devices while delivering an enhanced end-user experience.
Catchpoint Expands Its Leadership in Internet Performance Monitoring
Catching the Pulse: The Top 30 Infrastructure Monitoring Tools
30 Powerful SNMP Network Monitoring Tools: Unleashing the Potential of Network Management
The impact of NWDAF on telco service providers: Embracing vendor agnostic data analytics
Network Data Analytics Function (NWDAF) is a key component in 5G networks, designed to collect, analyze, and deliver valuable insights to service providers. NWDAF provides an unbiased, vendor-vendor agnostic view of the network, expanding telco visibility beyond traditional use cases. As network complexities grow, service providers require unbiased and accurate data to make informed decisions, driving the demand for vendor agnostic data analytics.
How Visibility Makes Empathy Easier, From the IT Desk to the End-User
Network Operator Confidential: Diving Into Our Latest Webinars on DDoS Trends, RPKI Adoption, and Market Intel for Service Providers
Didn’t have time to watch our two recent webinars on the top trends network operators need to know about to be successful in 2023? We’ve got you covered. Let’s look at the biggest takeaways and break down some key concepts.
What is Decentralized Network Monitoring
All you need to know about Software Defined Cloud Interconnects
What Can Network Automation Do for You?
You probably have been hearing a lot about automation and artificial intelligence (AI) these days, with a vision of some kind of AI-driven world that will take all of our jobs away. The reality is that there’s always too much work to do. AI and automation are more likely to help people get their jobs done more efficiently rather than take them away. Basic automation can have large returns for the network – and improve the quality of work.
What is Cloud Network Monitoring & How it Ensures Sky-High Network Performance
Enhance network monitoring with the latest AI-powered features in OpManager
Network monitoring is a challenging job because networks continue to evolve to meet ever-changing client requirements. Businesses today heavily depend on their networks, and even a short outage can lead to penalties and lost profits. This is why your monitoring tool must also transform itself to not only scale as you grow but offer new features that address new challenges posed by the increasing usage demands placed on your network.
How to Reduce the Volume of NGINX Logs
A gentle introduction to XDP
XDP, or eXpress Data Path, is a Linux networking feature that enables you to create high-performance packet-processing programs that run in the kernel. Introduced in Linux 4.8 and built on extended Berkeley Packet Filter (eBPF), XDP provides a mechanism to process network packets earlier and faster than is possible through the kernel’s native network stack. In this post, we’ll discuss.
How container networking works at Platform.sh
At Platform.sh, we run containers. Lots and lots of containers. On hundreds of virtual machines rented from various IaaS providers. These containers run your software. They also team up with other containers that run other software that your software depends upon (such as databases or caches). This is naturally an extremely complex system, and today we'll take a look at how we wire (most of) it up.
40 Best Cloud Network Monitoring Tools of 2023 for All Platforms and Giants like AWS, Google, Azure, IBM, and Oracle
Kentik OTT and CDN Analytics
Full Overview: Reducing Web Server Logs (ex.NGINX)
IT Operations in 2023: AI/ML & Automation Will Continue to Be the North Star
The use of statistics, advanced algorithms and AI/Ml is becoming omnipresent. The benefits are visible in every walk of life, from web searches, to movie and retail recommendations, to auto-completing our emails. Of course, not many anticipated the dramatic entrance of generative AI in the form of ChatGPT for writing college essays and poetry on arcane topics.
Top 30 Network Connection Monitoring Tools for Seamless Connectivity
Understanding Global Internet Connectivity Trends
The Ins-and-Outs of Hardware Monitoring
Avid PC gamers know that if you want optimal performance, you have to push your computer to its limits. And if your gaming “rig” is not properly equipped with a large interior fan, your PC can overheat, resulting in more than a few performance issues. It is the same for enterprise-level devices or pieces of hardware: overheating creates problems. One such enterprise-level piece of hardware (and arguably the most crucial piece of equipment) is a server.
Modernizing Network Data Analytics With a Unified Data Repository
Analyzing multiple databases using multiple tools on multiple screens is error-prone, slow, and tedious at best. Yet, that’s exactly how many network operators perform analytics on the telemetry they collect from switches, routers, firewalls, and so on. A unified data repository unifies all of that data in a single database that can be organized, secured, queried, and analyzed better than when working with disparate tools.
N-able Announces Cove Data Protection with Disaster Recovery as a Service, Introducing Microsoft Azure Recovery Option
Network Automation: Top Use Cases and Benefits
Network automation enables teams to use software to plan, develop, operate, or optimize networks with little or no human intervention. Effectively, network automation leverages some logic to execute “task A” when “event B” happens. Network automation can be used in a range of ways, anything from AI-driven network analytics to traditional health checks. Do you want to know how network automation can help your business? Keep reading.
Top Five Firewall Monitoring Best Practices
In today's hyper-connected world, cyber threats are an ever-present challenge that organizations of all sizes must face. With cybercriminals becoming increasingly advanced, prioritizing monitoring and managing your firewalls to safeguard your digital assets has never been more critical. This article aims to comprehensively understand five essential firewall monitoring best practices to fortify your network and protect your valuable data.
Simplifying Network Security: How AI is Changing the Game
As companies come to rely on digital systems in everything they do, network security has become more important than ever. Unfortunately, with that digital transformation comes complex networks to support it, and thus complex network security.
Best 19 Performance Monitoring Tools: APM vs. NPM
Resilience and Redundancy in Networking
Predictability in network flows is the ability to consistently deliver traffic from one point to another, even in the face of disruptions. Yet, establishing predictability has its share of challenges. Learn all about resilience in networking and how it relates to redundancy.
Mythbusting IPv6 with Jan Zorz, and Why IPv6 Adoption is Slow
IPv6 was developed in the late 1990s as a successor to IPv4 in response to widespread concerns about the growth of the Internet and its potential impact on the existing IPv4 address protocol, in particular potential address exhaustion. It was assumed that after some time as a dual-stack solution, we would phase out IPv4 entirely. Almost twenty-five years later, however, we are approaching full-scale depletion of IPv4 addresses, in part because IPv6 adoption is still lagging.
VoIP Monitoring 101: Keeping Your Calls Crystal Clear
Flowmon Integrations into Enterprise Ecosystem
Flowmon is not a stand-alone system used in isolation. It is part of an ecosystem of monitoring and security tools used across the enterprise. Recently, we have introduced new integrations with Splunk and ServiceNow to simplify interoperability and enable IT and security teams to be more efficient. This is a good opportunity to remind of all the integration options and resources we have.
Best 37 VoIP Monitoring Tools of 2023
GigaOm Names Broadcom Highest Scoring Leader for Third Straight Year in 2023 Radar Report for Network Observability
Broadcom has been named the highest-scoring vendor for the third consecutive year in a row in the 2023 Radar Report for Network Observability.
Monitor More of Your Modern IT Infrastructure Webinar
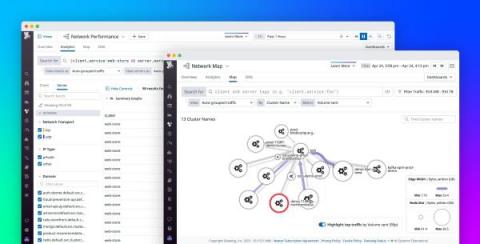
Streamline network investigations with an enhanced querying and map experience
Effective network troubleshooting requires collecting and correlating thousands of data points across your entire stack. The more data you ingest, however, the more data you have to search through in order to locate important signals. This can make it hard to find the information you need during time-sensitive investigations.
Best 36 Network Bandwidth Monitoring Tools of 2023 (Home, Free & Professionals)
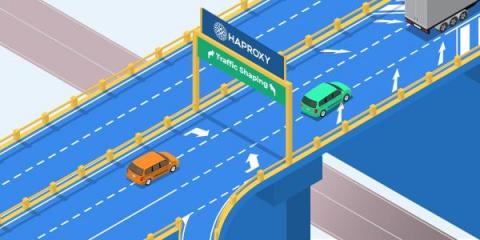
Introduction to Traffic Shaping Using HAProxy
High levels of web traffic can lead to network congestion, often causing network latency, and in some cases, outages. Traffic shaping is a technique that can help prevent network congestion by controlling how much traffic enters and leaves a network. We debuted traffic shaping in the release of HAProxy 2.7 and HAProxy Enterprise 2.7, allowing our users to control client upload and download speeds.
Three large language models walk into a Network Operations Center...
IT alerts are difficult to understand, even for experienced professionals. The language of IT alerts is akin to an enigmatic code requiring fluency in dozens of observability languages to extract technical meaning and business impact from a stream of seemingly disconnected events, alerts, and notifications.
30 Network Monitoring Tools With All The Information You Need of 2023
Megaport LIVE: How to Deploy Multicloud Applications With Megaport ONE - NAM April 26th, 2023
N-able Publishes Inaugural ESG Report
Debugging tips for common issues with cloud-based applications
Debugging in a cloud environment can be tricky, as it involves multiple layers of abstraction and virtualization. Unlike traditional on-premise environments, cloud environments are highly distributed and dynamic, making it challenging to identify and troubleshoot issues. One of the biggest challenges with debugging cloud applications is the need for more visibility into the underlying infrastructure and the complexity of the application architecture. Fortunately, pinpointing and resolving the cause of the issue is much more manageable with server-side monitoring, detailed error reporting and cloud debugging solutions.
Streamlining Troubleshooting for Work-from-Home Users: Tips for Effective Active Monitoring
It may feel like ancient history, but it was only a few years ago that, in response to the pandemic, organizations made a wholesale shift to support hybrid work models—and did so literally overnight, in many cases. While some time has passed, this is a shift to which many IT organizations are still struggling to fully adapt.
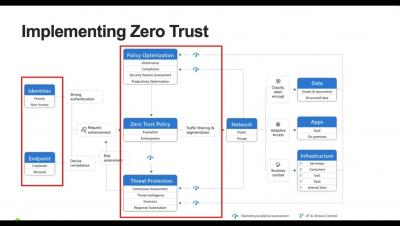
Applying Zero Trust to Data Centre Networks
Network Backup Solution Guide
Business Wire reports that over the next three years, more than three out of every four businesses believe that they are going to experience major data loss or a breach of data.
Kentique - The Fragrance of Observability
30 Best Network Performance Monitoring Software of 2023
The Insider's Guide to Network Connectivity Monitoring: Keeping Your Connections Strong
The 7 Step Guide on How To Budget for Layer 2 and Layer 3 Switches
Best 30 Enterprise Network Monitoring Software of 2023
Enhanced Security, Improved Performance Reporting with DX UIM 20.4 Cumulative Update 7
In today's fast-paced digital world, keeping up with the latest technology advancements is crucial for businesses to stay ahead of the competition. This is especially true in the world of IT infrastructure management, where technology is rapidly evolving and new solutions are being developed to meet the changing needs of businesses.
Q&A: How the DoD Can Modernize Its Networks and Optimize User Experience
The Department of Defense (DoD) is on a mission to modernize its IT environments, radically changing the nature of its network operations (NetOps) in the department. Network availability and performance keep getting more integral to the DoD’s charter, which means downtime isn’t just troublesome, it’s a life-or-death matter. In this post, we’ll outline how key DoD modernization imperatives are affecting NetOps.
SNMP Monitoring: What is SNMP & How to Use It
Are you tired of constantly running back and forth to check the status of your network devices? Do you wish you had a magic wand that could tell you everything you need to know about your network at a glance? Well, unfortunately, we can't give you a magic wand, but we can give you something pretty close: SNMP monitoring!