Operations | Monitoring | ITSM | DevOps | Cloud
August 2023
Discover the network maps
A Tale of Two BGP Leaks
Doug Madory investigates two large BGP leaks from August 28 and 29, 2023 and how RPKI ROV and other technologies can help mitigate widespread internet disruptions that can result for incidents like these.
The Impact of Network Topology
Beyond the Hype: The Power of AI and Large Language Models in Networking
Artificial intelligence is certainly a hot topic right now, but what does it mean for the networking industry? In this post, Phil Gervasi looks at the role of AI and LLM in networking and separates the hype from the reality.
How to Monitor VoIP PBX Systems for Call Quality
If you’ve ever used a business phone system, chances are that you’ve used a VoIP PBX or IP PBX system at least once. There are many advantages of using VoIP PBX for your business, but like most applications that work over a network, they’re prone to performance issues if network problems arise. In this article, we’re running you through how to monitor VoIP PBX systems to ensure optimal call quality with network monitoring.
NaaS and the API economy
Network Monitoring: A Comprehensive Overview
Imagine this: You’re a doctor. Your patient is a colossal network of computers, servers and cables, all intertwined and humming with activity. Your job? To keep an eye on this complex entity’s vital signs, ensure it runs smoothly and intervene when things start to look a little off. Welcome to the world of network monitoring and the role of network administrators.
Rogers Outage: How to Identify Network Outages & Internet Outages
The nationwide Rogers outage in Canada majorly disrupted the lives of many, affecting wireless, Internet, and even people’s ability to call 911. When major network outages or Internet outages occur, it’s important to be notified as soon as they happen. Understanding the causes and identifying network outages or Internet disruptions is not only essential for individual users but also for businesses striving to maintain uninterrupted operations.
DX NetOps in Action: Fujitsu Reduces TCO by 75% with Expanded "HumanCentric" Approach to NetOps
Fujitsu is a Japanese multinational information technology equipment and services company. Headquartered in Tokyo, Fujitsu has over 100 data centers worldwide. The company and its subsidiaries offer a diverse range of products and services in areas such as personal and enterprise computing (including x86), SPARC, and mainframe-compatible server products.
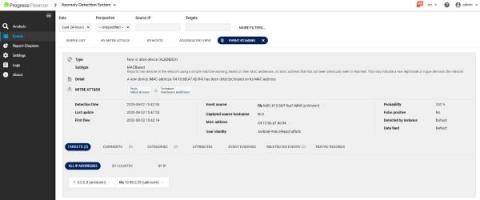
What is MITRE ATT&CK and How to Use the Framework?
The MITRE ATT@CK® framework is one of the most widely known and used. The Flowmon Anomaly Detection System (ADS) incorporates knowledge of the MITRE ATT&CK framework. Using ADS and its MITRE ATT&CK knowledge makes detecting advanced threats against networks and IT systems easier and simplifies explaining the danger and risks when outlining an attack to all stakeholders.
Black Hat USA: Adaptable Security From HAProxy
The curtain rose and fell on another spectacular Black Hat USA, the conference set against the backdrop of fabulous Las Vegas in the Mandalay Bay Convention Center. We knew upon hitting the Strip that all the glamor and neon lights were just the preshow for the main event: innovation and the latest in cybersecurity. We couldn’t wait to show attendees and fellow vendors what we had to offer.
Breaking the Cloud Illusion: The Hard Truth about Successful Migrations
How to Detect Microsoft Teams Outages: Is MS Teams Down?
Network Health and Performance Monitoring: SolarWinds MIB DB
Network Health and Performance Monitoring: Custom Pollers
Network Health and Performance Monitoring: SNMP Fundamentals
How seamless connectivity is driving the evolution of broadcast media
10 Best Firewalls for Small Business to Use in 2023
Escaping Cloud Jail
Cloud costs are spiraling out of control at companies of all sizes. Here’s how to not let your cloud infrastructure costs handcuff your business.
Application Monitoring in WhatsUp Gold
Quick Tip: Application Monitoring in WhatsUp Gold
Quick Tip: Application Monitoring Overlay in WhatsUp Gold
Quick Tip: Device Roles in WhatsUp Gold
How to Give Your Business Website a Makeover - Essential Tips and Tricks
How to Log HTTP Headers With HAProxy for Debugging Purposes
HAProxy offers a powerful logging system that allows users to capture information about HTTP transactions. As part of that, logging headers provides insight into what's happening behind the scenes, such as when a web application firewall (WAF) blocks a request because of a problematic header. It can also be helpful when an application has trouble parsing a header, allowing you to review the logged headers to ensure that they conform to a specific format.
How to Use Kentik to Perform a Forensic Analysis After a Security Breach
In this post, Phil Gervasi uses the power of Kentik’s data-driven network observability platform to visualize network traffic moving globally among public cloud providers and then perform a forensic analysis after a major security incident.
SLM for New-Age Infrastructure Observability with DX UIM from Broadcom
Dashboards & Reports for New-Age Observability with DX UIM from Broadcom
Configuring Kubernetes and OpenShift Monitoring with DX UIM by Broadcom
Sneak Peek: New-Age Infra Observability Viewer with DX UIM from Broadcom
How to Use Nmap: Complete Guide with Examples
In the constantly changing cybersecurity landscape, staying one step ahead of malicious actors is crucial - and understanding the intricacies of your networks is an integral part of that. A tool that can help you do this has earned its reputation as a cybersecurity stalwart - Nmap. Nmap, short for Network Mapper, holds the keys to unlocking valuable insights in your network infrastructure.
Understanding the API economy
Scaling Monitoring Administration with Experience-Driven NetOps: AppNeta and DX NetOps
Today, pretty much every critical business service, every critical employee job function, every critical customer transaction, and so much more are all reliant upon network connectivity. It falls to network operations (NetOps) teams to ensure network connections continue to support these demands. Over time, the scale and the complexity of the networks the organization relies upon have continued to grow, making the job of NetOps teams increasingly challenging.
CISO's MOST WANTED: Outsmarting Cyber Criminals with Tips from a Former FBI Agent
Upgrading NPM and SAM to Hybrid Cloud Observability
Mastering Microsoft 365 Monitoring for Businesses
DX NetOps In Action: How Altice Accelerates Network Transformation with Broadcom
Altice Portugal is a wholly owned subsidiary of Altice Group, a multinational cable and telecommunications company. They have a presence across Europe, including in Belgium, France, Luxembourg, Portugal, and Switzerland, as well as in the Dominican Republic, the French West Indies, and Israel. With annual revenues of more than $2.8 billion (2,629 million Euros), Altice Portugal is Portugal’s largest telecom company. Altice offers fixed, mobile, and satellite network services to consumers.
Understanding Site24x7's NCM Automation, reports, and compliance
Dual Subsea Cable Cuts Disrupt African Internet
On Sunday, August 6, an undersea landslide in one of the world’s longest submarine canyons knocked out two of the most important submarine cables serving the African internet. The loss of these cables knocked out international internet bandwidth along the west coast of Africa. In this blog post, we review some history of the impact of undersea landslides on submarine cables and use some of Kentik’s unique data sets to explore the impacts of these cable breaks.
Private Connectivity to IBM Cloud - Portal Demo
How to Identify Network Problems & Diagnose Network Issues
Just because your network is "UP," doesn't mean it’s working well! Network issues like choppy VoIP, jerky video calls, and network and application slowness issues can affect your business in drastic ways - which is why it’s important to know how to identify network issues for network performance troubleshooting. There are many problems that can affect network performance, and some of them are very complex to identify and understand.
Using DX NetOps Dashboards To Harness the Power of AppNeta Data
In today’s dynamic, complex network environments, there’s a big difference between having monitoring data and having intelligence. To troubleshoot issues quickly, it’s vital to have timely, intuitive visibility into the metrics that matter. With the combination of AppNeta and DX NetOps, teams can gain the insights they need to efficiently and intelligently manage their environments.
How to Check the Status of your Megaport Services
How to Check the Latency of your Megaport Services
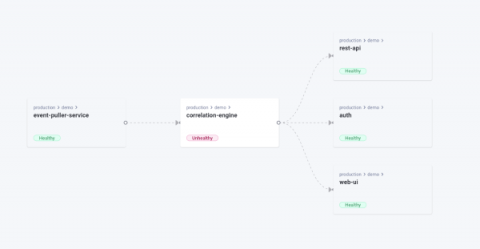
Unveiling Komodor's Network Mapping Capability
I am happy to share that thanks to the power of the open-source community, and our friends over at Otterize, we have now enhanced our Kubernetes offering for developers with another visual aid to streamline operations and troubleshooting – Dependencies Map. The Otterize network mapper is a zero-config tool that aims to be lightweight and doesn’t require you to adapt anything in your cluster.
A Deep Dive into Microsoft Cloud Monitoring for IT Pros
How to Perform a Forensic Analysis After a Security Breach
Veteran technology leader, Microsoft Data Platform expert returns to SolarWinds to focus on DataOps, SQL, cloud migration
The importance of a network backup tool
Configurations are regarded as the core of networks due to their importance. With businesses continually advancing and relying on networks for storing, processing, and transmitting critical data, the complexity of network management has increased, leading to difficulties and human errors that can cause significant network downtime.
Why should I consider Salesforce Express Connect?
Top 5 network management trends in 2023
New trends emerge in network management every year, and 2023 is no exception. This year the industry is set to witness a plethora of advancements and breakthroughs that will revolutionize network administration. From the adoption of sophisticated analytics and machine learning to the proliferation of cloud-based solutions and the surging significance of cybersecurity, here are the top network management trends to watch out for in 2023.
What is Network Troubleshooting? - The Ultimate Survival Guide
Are you tired of feeling like a lost sailor on a stormy sea of computer problems? Well, fear not, dear reader, for we are about to embark on a journey to demystify the world of network troubleshooting! Intermittent network problems interrupt your flow of work, frustrate users, and can wreak havoc on your business. Troubleshooting network problems as fast as possible is the key to making sure that doesn’t happen.
How Qonto used Grafana Loki to build its network observability platform
Christophe is a self-taught engineer from France who specializes in site reliability engineering. He spends most of his time building systems with open-source technologies. In his free time, Christophe enjoys traveling and discovering new cultures, but he would also settle for a good book by the pool with a lemon sorbet.
Agentless Network Monitoring: An Introductory Guide
From communication and collaboration to data storage and sharing, networks are critical to almost every business operation today. Thus, monitoring the reliability and security of your network infrastructure is more critical than ever. Network monitoring entails observing and analyzing network traffic to identify issues, optimize performance, and ensure security.
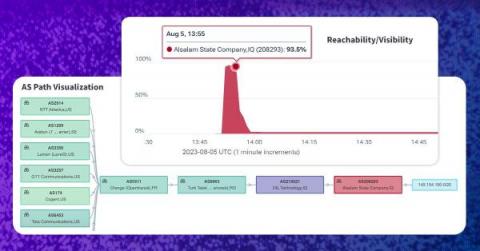
Iraq Blocks Telegram, Leaks Blackhole BGP Routes
This past weekend, the government of Iraq blocked the popular messaging app Telegram, citing the need to protect Iraqi’s personal data. However, when an Iraqi government network leaked out a BGP hijack used for the block, it became yet another BGP incident that was both intentional, but also accidental. Thankfully disruption was minimized by Telegram’s use of RPKI.
The Guide to MSP Network Monitoring for Multi-Client Visibility
G2's Most Recommended WAF & DDoS Protection
In case you missed it, HAProxy Technologies recently put out a press release about our stunning leadership position in G2’s Summer 2023 Grid® Reports for load balancing. We’re incredibly proud of these results, which are a direct result of the hard work and dedication of HAProxy’s community developers and our enterprise product and support teams. Looking at the Momentum Grid® Report for Load Balancing, the gap between HAProxy and the rest is impossible to ignore.
Enhancing Security Workflows with Real-Time Notifications via Microsoft Teams and Slack
The integration with popular collaboration platforms like Microsoft Teams and Slack marks a pivotal advancement in security workflows. We are introducing new capability to post events from Flowmon ADS into Teams channel or Slack to instantly notify security teams. Integrations scripts are based on simple webhooks and available out of the box on our support portal both for Teams and Slack.
Troubleshooting Cloud Application Performance: A Guide to Effective Cloud Monitoring
The scalability, flexibility, and cost-effectiveness of cloud-based applications are well known, but they’re not immune to performance issues. We’ve got some of the best practices for ensuring effective application performance in the cloud.
Microsoft Teams Monitoring to Troubleshoot & Optimize Performance
Automate network topology mapping with OpManager's topology software
Network topology mapping is the process of mapping topological relationships between network components and establishing those relationships in the form of network diagrams. Network mapping helps visualize physical and logical connections between all elements and nodes, thus simplifying network management. A network topology mapper is a tool that helps perform network mapping effectively.
Driving A Successful SD-WAN Migration: Obkio's NPM Solution Empowers StableLogic in a Global SD-WAN Deployment
Troubleshooting Wi-Fi Issues for Hybrid Workers: Key Requirements for NetOps Teams
In recent years, employees have grown increasingly accustomed to the untethered connectivity of Wi-Fi. For many, the days of having a computer tethered to an ethernet cable can seem like a distant memory. That was true when employees were working in an office, and it is all the more the case as we’ve moved to a hybrid work world.
What are Traceroutes and How Do Traceroutes Work?
If you've ever wondered why your Internet connection seems slow or experiencing connection problems with a website, you might have heard of a tool called "traceroute." But what is a traceroute, and how does it work? In this article, we'll be giving a quick and simple introduction to what are traceroutes, and how traceroutes work to help identify and troubleshoot network problems.
The First 48 Hours of Ransomware Incident Response
What Is APM and How Can It Help Your Services/Applications?
APM is one of those buzzwords that is slowly becoming a necessity. Most people are still unsure what APM means and how it can help their services. But what is it? What does it stand for? And how can it help your services or digital products? This blog will answer your questions—and more.
Using Helm Dashboard and Intents-Based Access Control for Pain-Free Network Segmentation
Helm Dashboard is an open-source project which graphically shows installed Helm charts, revisions, and changes to their Kubernetes resources. The intents operator is an open-source Kubernetes operator which makes it possible to roll out network policies in a Kubernetes cluster, chart by chart, and gradually achieve zero trust or network segmentation.
N-able Announces New Partner-Focused Podcast Showcasing Stories of MSP Success
Best Practices for SaaS and Network Incident Management
Computer and network systems have (obviously) become vital to business operations. Occasionally, there are SaaS or network incidents and these systems do not operate as needed. Enterprises want to minimize the potential damage and get their systems back online ASAP. Integrated incident management and a strong End User Experience Management (EUEM) platform that provides synthetic and real-user monitoring is a foundation for meeting that objective.
3 Steps to Get DX NetOps Events in Slack and Google Chat
Network operations centers (NOCs) play a critical role in any organization’s operational and business continuity. To meet their vital charters, NOC teams must constantly strive to maintain uninterrupted network availability and to minimize the business impact of network issues. Within the NOC, effective collaboration is essential for quick troubleshooting and resolution of network issues.
5 Things to Look for in a SaaS Management Platform and Why
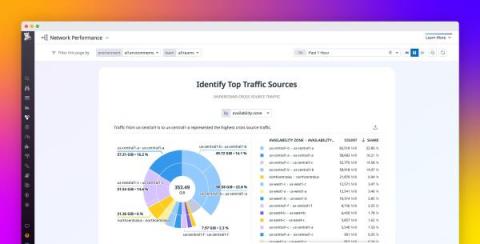
Quickstart network investigations with NPM's story-centric UX
Datadog Network Performance Monitoring (NPM) gives you visibility into all the communication that takes place between the network components in your environment, including hosts, processes, containers, clusters, zones, regions, and VPCs. As organizations scale, and as their networks grow in complexity, the massive volume of network data to be monitored can become overwhelming. Knowing precisely what network data to surface to resolve issues within these larger environments can be a challenge.
Exploring AKS networking options
At Kubecon 2023 in Amsterdam, Azure made several exciting announcements and introduced a range of updates and new options to Azure-CNI (Azure Container Networking Interface). These changes will help Azure Kubernetes Services (AKS) users to solve some of the pain points that they used to face in previous iterations of Azure-CNI such as IP exhaustion and big cluster deployments with custom IP address management (IPAM).