Operations | Monitoring | ITSM | DevOps | Cloud
April 2021
Importance of Data Security For Mobile Healthcare Apps
Telemedicine or mobile healthcare apps are unquestionably important in our daily lives, as the world is increasingly shifting to an all-digital landscape. And when you think of the current pandemic scenario when social distancing and wearing masks are the new normal, nothing seems to be safer than using mobile health apps. But are we really safe while using these apps? Well, that brings us to the concern of being safe on the internet while using mobile healthcare apps.
Incident Response Alert Routing
You have identified a data breach, now what? Your Incident Response Playbook is up to date. You have drilled for this, you know who the key players on your team are and you have their home phone numbers, mobile phone numbers, and email addresses, so you get to work. It is seven o’clock in the evening so you are sure everyone is available and ready to respond, you begin typing “that” email and making phone calls, one at a time.
Announcing Calico Enterprise 3.5: New ways to automate, simplify and accelerate Kubernetes adoption and deployment
We are thrilled to announce the availability of Calico Enterprise 3.5, which delivers deep observability across the entire Kubernetes stack, from application to networking layers (L3–L7). This release also includes data plane support for Windows and eBPF, in addition to the standard Linux data plane. These new capabilities are designed to automate, simplify and accelerate Kubernetes adoption and deployment. Here are highlights from the release…
The essentials of central log collection with WEF and WEC
Last week we covered the essentials of event logging: Ensuring that all your systems are writing logs about the important events or activities occurring on them. This week we will cover the essentials of centrally collecting these Event Logs on a Window Event Collector (WEC) server, which then forwards all logs to Elastic Security.
Sysdig Raises $188M at a Valuation of $1.19B to Secure Modern Cloud Applications
Security Starts With People, Unfortunately.
Mobile Devices are Ubiquitous, and so are Cyberattacks
We all like to enjoy untethered freedom, as is shown by the incredible growth of mobile devices we use every day for business and personal activities. We use mobile devices for buying products and services, and banking and investing. We download apps that allow us to connect with our favorite businesses and socially interact with friends and relatives.
Using Maths to Fight Financial Crime
Financial crime has become a red-hot topic over the last 12 months, as fraudsters have sought to exploit the monitoring gaps between people, process and technology across an ever-widening attack surface – driven by the growth in usage of remote (digital) channels. Even before its recent growth, the cost of fraud and financial crime was significant.
Exploiting and detecting CVE-2021-25735: Kubernetes validating admission webhook bypass
The CVE-2021-25735 medium-level vulnerability has been found in Kubernetes kube-apiserver that could bypass a Validating Admission Webhook and allow unauthorised node updates. The kube-apiserver affected are: You are only affected by this vulnerability if both of the following conditions are valid: By exploiting the vulnerability, adversaries could bypass the Validating Admission Webhook checks and allow update actions on Kubernetes nodes.
Our $188M funding round fuels our mission to help customers confidently run modern cloud applications
Today, I am excited to share that we secured $188M in a new funding round, at a valuation of $1.19B (read more here). At the outset, I want to thank our employees, partners, investors and most importantly, our customers for this important milestone. The funding follows a year of unmatched innovation that led to accelerated revenue growth, installed base growth, and rapid community adoption of our open source projects.
SIEM Deployment Remains Strategic in 2021
Some great new research coming out of the survey data published by 451 Research on Enterprise spending for Information Security. There have been more advanced ways of trying to implement security controls and avoid security issues by integrating security into the development or continuous integration and release pipelines. Despite that, there is still strong interest in using log and event data to manage the security posture of an organization in a SIEM solution.
Integrate security into development with Snyk, now a seamless part of Bitbucket Cloud
Vaccinating Against the Ransomware Pandemic
Just as our physical world has suffered from a devastating health pandemic, over the last 3 years the digital world has been suffering a ransomware pandemic that grew 7 times in 2020 compared to the same time in 2019. While we have vaccines for our health crisis what are our options to help protect us against this digital threat?
Splunk and Zscaler Utilize Data and Zero Trust to Eradicate Threats
The past year has challenged us in unimaginable ways. We kept our distance for the greater good, while companies faced the daunting task of transforming their workforce from in-person to remote — practically overnight. This presented a unique challenge for cybersecurity teams. How would they ensure employees retained access to critical data in a secure way? Working in the cloud has made remote work easier for many organizations, but has also presented new risks.
CI/CD Pipeline Security 101
In our previous post, we discussed the recent security incident at Codecov and the following investigation at Mattermost. As a follow-up to that we wanted to share some of the basic design principles as well as a handful of more technical tips and tricks around CI/CD pipeline security that helped Mattermost come out of the incident unscathed.
8 Utmost eCommerce Security Threats and Solutions of 2021
Last year, during the Magecart attacks saga, I was constantly flooded by calls from e-entrepreneurs – all sounding worried and anxious. The attacks were brazen, and the digital trust was taking a beating. After the initial shock waned, the entire conversation shifted gears. I still remember having long discussions with my clients about eCommerce security threats and their solutions. It now focused solely on building a reliable security system.
Security threats affecting your workforce productivity? Here's how Forrester says you can address them
According to Forrester, the number of permanent, full-time remote workers is expected to increase by 300 percent or more compared to pre-pandemic numbers. Amid the chaos surrounding the pandemic, getting your entire workforce back to the office seems trivial, especially when many employees’ work can be done remotely. It’s no wonder that, according to Gartner, almost half of employees will continue to work remotely post COVID-19.
Comparison: Snyk, Aqua Security, Sysdig
Security testing tools help us to monitor our cloud-native resources for potential vulnerabilities throughout our development lifecycle. By flagging security vulnerabilities early, our teams can react on time to reduce potential damage to our end-users and our business. This post will compare three different Security scanning tools that focus on cloud-native infrastructure and application security, namely.
Microlesson: Rule Tuning in CSE
Microlesson: Threat Investigation with CSE
MobileIron, Acquired by Ivanti, Named "Best Solution Partner" by Deutsche Telekom
Industry recognition is always something to strive for, but when the recognition comes from a trusted partner then it means even more. At Ivanti, we’re proud to be recognized by longstanding partner, Deutsche Telekom, as a “Best Solution Partner” of the year. This was the first year that the award was handed down and represents the deep commitment to partnership and execution.
Beware of QR Code Security Risks Lurking in User Mobile Devices
QR codes, those touch-free codes that look like square puzzles or mazes, seem to be everywhere these days. Gaining in popularity over the past few years, their proliferation has exploded with the onset of COVID-19 precautions. These wonder-codes make it easy for our mobile devices to quickly scan a menu, pay a bill, and find information about a product or service. QR codes blend the physical world with the virtual.
Streamlining Vulnerability Management with Splunk Phantom
Vulnerabilities are weaknesses in the security infrastructure that bad actors can exploit to gain unauthorized access to a private network. It is nearly impossible for security analysts to patch 100% of the vulnerabilities identified on any given day, but a vulnerability management plan can ensure that the highest risk vulnerabilities (those that are most likely to cause a data breach), will be addressed immediately.
How to Plan a Threat Hunt: Using Log Analytics to Manage Data in Depth
Detect unauthorized third parties in your AWS account
Detecting when an unauthorized third party is accessing your AWS account is critical to ensuring your account remains secure. For example, an attacker may have gained access to your environment and created a backdoor to maintain persistence within your environment. Another common (and more frequent) type of unauthorized access can happen when a developer sets up a third-party tool and grants it access to your account to monitor your infrastructure for operations or optimize your bill.
Adopting a cloud first strategy for modernizing security operations
AIOps in 2021 and Beyond: 5 Trends You Should Be Aware Of
Node.js's Underrated Combo: Passport and CASL
It’s easy to get lost with dozens of plugins and frameworks when starting a new project that requires basic authentication and authorization capabilities. It doesn’t have to be that way. In this article, we’re going to explore two valuable Node.js packages — Passport and CASL — that can help you boost the security of your application by providing both authentication and authorization functionality.
MITRE Engenuity ATT&CK Round 3: Carbanak + FIN7 vs. the free and open capabilities in Elastic Security
Whether this is the third time you are looking at the MITRE Engenuity ATT&CK® evaluation results or your first, you may be asking yourself: what was unique about this year’s evaluation? Well, let’s first start with: who is MITRE Engenuity? They are a tech foundation that collaborates with the private sector on many initiatives — most notably cybersecurity — and in recent years have become synonymous with cyber threat evaluations.
Monitoring Pulse Connect Secure With Splunk (CISA Emergency Directive 21-03)
To immediately see how to find potential vulnerabilities or exploits in your Pulse Connect Secure appliance, skip down to the "Identifying, Monitoring and Hunting with Splunk" section. Otherwise, read on for a quick breakdown of what happened, how to detect it, and MITRE ATT&CK mappings.
Cloud SIEM accelerates modernizing security operations across Asia Pacific
SOC 1 or SOC 2, which should you comply with and why?
Organizations today are more vulnerable than ever to cyberattacks and data breaches. Whether the attack is executed by an external actor or an insider, the unauthorized intrusion comes at a great cost. This cost may differ, depending on several factors. These include the cause of the breach, the actions taken to remediate the incident, whether there is a history of data infringements, what data was compromised, and how the organization aligned with the authorities and regulators.
Kubernetes Security and Observability
How to detect EC2 Serial Console enabled
Recently, Amazon AWS introduced the new feature EC2 Serial Console for instances using Nitro System. It provides a simple and secure way to perform troubleshooting by establishing a connection to the serial port of an instance. Even though this feature is useful in case of break glass situations, from a security perspective, it could be used by adversaries to gain access through an unguarded secondary entrance.
What's new in Sysdig - April 2021
Welcome to another monthly update on what’s new from Sysdig. Ramadan Kareem to all observing the holy month of Ramadan. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! This last month was a big month for security with our release of Cloud Security Posture Management (CSPM), and we had lots of fun designing and releasing our new Cloud Chaos game!
The Global Pandemic Has Led to Unprecedented QR Code Security Challenges
Over the past year, we have witnessed remarkable changes brought on by our response to a global pandemic. Along with accelerated digital transformation and the consumerization of technology, Covid-19 has birthed the everywhere workplace, where users work with any device, to connect to business-critical systems and applications. Work has become something you do rather than a place you go.
How attackers abuse Access Token Manipulation (ATT&CK T1134)
In our previous blog post on Windows access tokens for security practitioners, we covered: Having covered some of the key concepts in Windows security, we will now build on this knowledge and start to look at how attackers can abuse legitimate Windows functionality to move laterally and compromise Active Directory domains. This blog has deliberately attempted to abstract away the workings of specific Windows network authentication protocols (e.g., NTLM and Kerberos) where possible.
Elevate Your Cloud Security Posture with Splunk and Google Cloud
It’s more critical than ever to secure your company data and protect your workloads in the cloud. This blog post is a roundup of the latest technical resources and product capabilities by both Google Cloud and Splunk to enhance your threat prevention, detection, and response techniques, regardless of where you are in your business-transforming cloud journey.
Dashbird becomes SOC 2 compliant
We are pleased to announce that as of 13th April 2021, Dashbird has successfully completed its SOC 2 Type 2 audit. SOC 2 engagements are based on the AICPA’s Trust Service Criteria. SOC 2 audit reports focus on a Service Organization’s non-financial reporting controls as they relate to the Security of a system. The audit was conducted by Dansa D’Arata Soucia LLP.
Thoughts On the Codecov Breach
It was revealed just a few days ago that US Federal investigators are looking into an intrusion and insertion of malicious code into Codecov. As many readers here will already know, Codecov is a software auditing tool that analyses your source code to check for the amount of test coverage. The intrusion targeted the Codecov bash uploader, which is a script that provides a way to send coverage reports to Codecov.
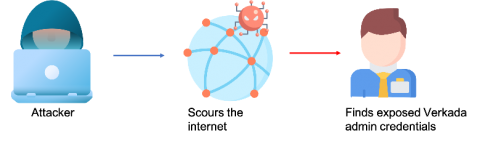
Operation panopticon: How a weak IAM strategy led to the security camera hack across organizations
On March 9, 2021, Verkada, a software company that specializes in making security cameras for monitoring physical access control, was subject to a security hack. Hackers gained access to the video feed of at least 15 thousand cameras deployed across various locations and exposed the inner workings of hospitals, clinics, and mental health institutions; banks; police departments; prisons; schools; and companies like Tesla and Cloudflare.
Mitigating CVE-2021-20291: DoS affecting CRI-O and Podman
The CVE-2021-20291 medium-level vulnerability has been found in containers/storage Go library, leading to Denial of Service (DoS) when vulnerable container engines pull an injected image from a registry. The container engines affected are: Any containerized infrastructure that relies on these vulnerable container engines are affected as well, including Kubernetes and OpenShift.
Introducing Splunk Attack Range v1.0
The Splunk Attack Range project has officially reached the v1.0 release. By achieving this milestone, we wanted to reflect on how we got here, what features we’ve built for v1.0 and what the future looks like for Splunk Attack Range. What is the Splunk Attack Range? 🧐
Collaboration and sharing - Our plans for 2021
As we’ve hinted at before, 2021 will be a big year for CFEngine. In the summer, we will release CFEngine 3.18 LTS. This is the first LTS release with Compliance Reports , Custom Promise types , and all of the other improvements we’ve made over the past year .
How to Ensure WFH Is as Secure as an Office Job
Detect anomalous activity in your environment with new term-based Detection Rules
When it comes to securing your production environment, it’s essential that your security teams are able to detect any suspicious activity before it becomes a more serious threat. While detecting clear-cut attacker techniques is essential, being able to spot unknowns is vital for full security coverage.
Sleuth + SOC 2 Type II: Our constant commitment to security
In Sleuth’s continuing efforts to help our customers to deliver faster and safer, we have always put security as a top-level business priority. Security and privacy of our customers’ data is always in the forefront of our design, development, and deployment concerns. We understand the level of trust our customers put in us when they connect key systems together with Sleuth.
Bits of Security, Security Panel
Bits of Security
What's the Difference Between DevOps and DevSecOps?
DevOps vs DevSecOps: Learn the similarities and differences of each agile methodology and the essential processes involved.
Automatically Assess and Remediate the SolarWinds Hack
Bits of Security, Snyk.io: Stranger Danger: Finding Security Vulnerabilities Before They Find You!
Bits of Security, PedidosYa: Fraud Detection using Datadog and Sherlock
Phishing and Ransomware: Connecting the Dots!
Phishing and ransomware. Ransomware and phishing. The two are inextricably connected and are now often chained together as the most potent exploit tools in a cybercriminal’s arsenal.
Endpoint Security Data Collection Strategy: Splunk UF, uberAgent, or Sysmon?
Many threats originate from the endpoint and detecting them requires insights into what happens on the endpoint. In this post we look at different endpoint activity data sources, comparing the benefits and capabilities of Splunk Universal Forwarder with vast limits uberAgent and homegrown solutions.
The Facebook data breach that affects over 533 million users explained
If you’re a Facebook user, brace yourself for this one. It’s recently come to light that 533 million Facebook users’ details were found on a very suspicious hacker forum. The details found include users’ phone numbers, Facebook IDs, full names, locations, birthdays, and email addresses – all typical information that is stored on a Facebook account.
Kubei walk-through: A Kubernetes Runtime Vulnerabilities Scanner - Milind Chawre
Unveil hidden malicious processes with Falco in cloud-native environments
Detecting malicious processes is already complicated in cloud-native environments, as without the proper tools they are black boxes. It becomes even more complicated if those malicious processes are hidden. A malware using open source tools to evade detection has been reported. The open source project used by the malware is libprocesshider, a tool created by Sysdig’s former chief architect Gianluca.
Why You Need to Closely Monitor Your Exchange Servers
Monitoring your on-prem and hybrid cloud infrastructure has always been important. With an ever-growing rise in cyber attacks, zero-day exploits, and insider threats, keeping track of your infrastructure has a renewed level of significance. Microsoft Exchange is one of the most prominent enterprise systems in use today, with both cloud and on-prem iterations.
Assessing the cybersecurity landscape
Continuous integration that you can trust: announcing SOC 2 certification
At CircleCI, we care about security - in 2018, we became the first CI/CD tool to meet the rigorous security and privacy standards required by government agencies to get FedRAMP authorized. Now, CircleCI is SOC 2 certified, adding another industry-recognized security accreditation.
IAM Policies: Good, Bad & Ugly
In my last post we looked at the structure of AWS IAM policies and looked at an example of a policy that was too broad. Let's look at a few more examples to explore how broad permissions can lead to security concerns. By far the most common form of broad permissions occurs when policies are scoped to a service but not to specific actions.
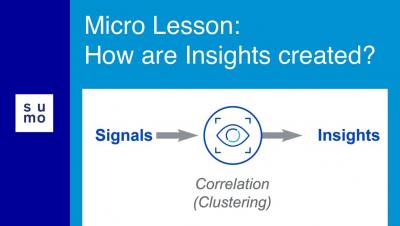
Microlesson: How are Insights Created?
Splunk SOAR Playbooks: Azure New User Census
AppDynamics with Cisco Secure Application Demo
Run confidently with secure DevOps
Taking Automation Beyond the SOC With Advanced Network Access Control
Security orchestration, automation and response (SOAR) tools are most commonly known for automating manual security operations processes in order to expedite security investigations or cyber response. For instance, Splunk’s SOAR technology, Splunk Phantom, is most commonly used to automate alert triage, phishing investigation and response, threat hunting and vulnerability management.
Web Access Control Redefined
One of the focuses of version 2.9 of Icinga Web 2 will be on access control. For years on now, Icinga Web 2 had a very simple role based access control (RBAC) implementation. This suited most of our users fine. However, there were still some requests to enhance this further. The next major update of Icinga Web 2 (Version 2.9) and Icinga DB Web will allow users to configure exactly this.
Secure Your IT Assets for an Optimal Return
How Does Ivanti Approach Zero Trust Security?
Are you curious about how Ivanti is tackling Zero Trust? Check out this video clip below and hear from Scott Erickson, Lead Technical Marketing Engineer at Ivanti, to learn more and then visit the Zero Trust Access page for even more resources.
Shifting Security Left: Tools and Best Practices
Software development pipelines typically cycle through key four processes—design, development, testing and software or update releases. Traditional pipelines perform quality and security tests only after completing the development phase. Since there is no such thing as a perfect code, there are always issues to fix. However, if significant architectural changes are needed, fixing them at the end of the process can be highly expensive.
Threat Hunting with Threat Intelligence
With more people working from home, the threat landscape continues to change. Things change daily, and cybersecurity staff needs to change with them to protect information. Threat hunting techniques for an evolving landscape need to tie risk together with log data. Within your environment, there are a few things that you can do to prepare for effective threat hunting. Although none of these is a silver bullet, they can get you better prepared to investigate an alert.
What's the Most Powerful Tool in Your Security Arsenal?
Trying to work out the best security tool is a little like trying to choose a golf club three shots ahead – you don’t know what will help you get to the green until you’re in the rough. Traditionally, when people think about security tools, firewalls, IAM and permissions, encryption, and certificates come to mind. These tools all have one thing in common – they’re static.
How Calico Cloud's runtime defense mitigates Kubernetes MITM vulnerability CVE-2020-8554
Since the release of CVE-2020-8554 on GitHub this past December, the vulnerability has received widespread attention from industry media and the cloud security community. This man-in-the-middle (MITM) vulnerability affects Kubernetes pods and underlying hosts, and all Kubernetes versions—including future releases—are vulnerable. Despite this, there is currently no patch for the issue.
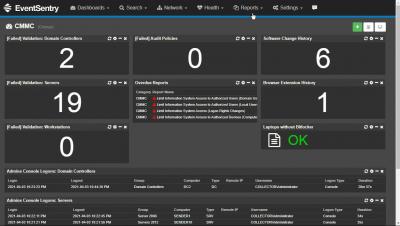
CMMC compliance with EventSentry
AWS IAM Privilege Escalation - Threat Research Release March 2021
The Splunk Threat Research Team recently developed an analytic story to help security operations center (SOC) analysts detect adversaries attempting to escalate their privileges and gain elevated access to Amazon Web Services (AWS) resources. In this blog, we’ll walk you through an AWS privilege escalation analytic story, demonstrate how we simulated these attacks using Atomic Red Team, collect and analyze the AWS cloudtrail logs, and highlight a few detections from the March 2021 releases.
Interview With Cyber Security Author Scott Steinburg
For our first specialist interview on the Logit.io blog, we’ve welcomed Scott Steinburg to share his thoughts on the current state of cybersecurity as well as the reasons behind writing his new book Cybersecurity: The Expert Guide. Scott is the creator of the popular Business Expert’s Guidebook series, host of video show Business Expert: Small Business Hints, Tips and Advice and CEO of high-tech consulting firm TechSavvy Global.
Strategies to Reduce Alert Fatigue in Your SOC Team
In a SOC (security operations center), alerts originating from hundreds of systems compete to get attention. What ensues is a security analyst’s battle to beat alert fatigue while effectively defending their organization from cybersecurity threats. Alert fatigue is a major challenge faced by security operations center (SOC) teams. The stakes are even higher since they take on the enormous responsibility of maintaining networks and data systems.
Why We're Embracing Password 3.0...And You Should Too
Password 1.0 was your cat’s name and your birth year and you used it across every endpoint for a decade. We see you, Sprinkles1979. Password 2.0 was SSO and MFA and WTF because literally everyone used Facebook for authentication. We all saw how well that went. It’s time for Password 3.0 We’ve always operated at the leading edge of innovation, and this is no exception. While the industry gets bogged down in sending texts to confirm authorization, we’re moving forward.