Operations | Monitoring | ITSM | DevOps | Cloud
June 2021
Threat Stack and Squadcast Integration Streamlines Alerts with Greater Context
The New Developer Experience at Okta
DevSecOps is a practice. Make it visible
How the Elastic InfoSec team uses Elastic Security
At Elastic, we internally use, test, and provide feedback on all of our products. For example, the Information Security team is helping the Product team build a stronger solution for our customers. The InfoSec team is an extremely valuable resource who acts not only as an extension of Quality Assurance/Testing, but also as a data custodian.
Splunk Named Market Share Leader in ITOM and SIEM Reports
2020 was a challenging year for modern enterprises. In under a year, we experienced a decade's worth of transformation while a global pandemic raged on. And while the worst of COVID-19 will hopefully soon be behind us, the need to continuously transform our digital environment is unequivocally here to stay. We've already seen an example of this, thanks to a significant increase in data generated from across the business.
Interview With Transmosis CEO Chase Norlin
For the seventh instalment in our series of interviews asking leading technology specialists about their achievements in their field, we’ve welcomed the CEO of Transmosis, Chase Norlin to share his journey in the field of cybersecurity as well as his recommendations for those looking to start their career in cybersecurity.
Centralized Firmware Update of Power Infrastructure to Improve Cybersecurity
Today, it’s more important than ever to secure your critical infrastructure. You just have to look at some of the large cyberattacks that occurred this year to understand why. In 2020, 80.7% of organizations suffered at least one successful cyberattack, and 35.2% suffered six or more. You must follow best practices to avoid being one of these victims.
Detecting new crypto mining attack targeting Kubeflow and TensorFlow
Microsoft has discovered a new large-scale attack targeting Kubeflow instances to deploy malicious TensorFlow pods, using them to mine Monero cryptocurrency in Kubernetes cluster environments. Kubeflow is a popular open-source framework often used for running machine learning tasks in Kubernetes. TensorFlow, on the other hand, is an open-source machine learning platform used for implementing machine learning in a Kubernetes environment.
Securing pipelines through secret management
Secrets management plays a critical role in keeping your pipelines and applications secure. While secrets management tools help, you need to implement best practices and processes to successfully manage secrets in a DevOps environment. Standardizing, automating and integrating these processes also helps secure secrets by reducing the chance of human error.
We've Agreed to Acquire Vdoo, Unifying Developers and Security Teams from Source to Device
SOS! Why 2021 has to be the Summer of Security
Sunblock: Check. Life vest: Check. Zero trust security: Wait, what? Summer gives us all a little breathing room and a chance to relax. This summer, perhaps more than any other in our lifetimes, we’re all looking forward to loosening up. As we get a hint of normalcy, or at least what “normal” is going to look like now that we’re in the Everywhere Workplace, many people are letting their guards down. We want folks to relax. We really do.
The Role of Threat Hunting in Modern Security
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent need to scrutinize and control the use of these online resources to prevent data theft, exposure, and loss. This blog elaborates on how a robust URL filtering solution can help manage what cloud services your employees use and how they interact with these services.
Secure Software Development: How to Check Your Code
EventSentry on GitHub: PowerShell module, templates and more!
Since we’ve accumulated a lot of resources around EventSentry that are updated frequently, we’ve decided to launch a GitHub page where anyone can access and download scripts, configuration templates, screen backgrounds and our brand-new PowerShell module that is still under development.
Trigger agent runs and report collection from Mission Portal (Developer Demo)
Microlesson: Configure the Actions Button
A day in the life of cybersecurity. Splunk customer stories of SOC-cess
We have a saying at Splunk. It goes something like “if you’re ever having a bad day, go and talk to a customer”. What organizations around the world are doing with their data and Splunk brings a huge smile and an eyebrow raising, positive “can’t quite believe you’ve done that” very-impressed nod of the head. That’s never more true than with our security customers.
CFEngine: The Agent Is In 2 - Community User Demo with Jeff Carlson
Security Leaders Trust Splunk
How Much Damage a Ransomware Attack Can Cause
Understanding the DoD's Data Strategy: Part 2
Published in late 2020, the DoD Data Strategy emphasizes the importance of unlocking and operationalizing data-value from across its enterprise to support mission operations and maintain battlefield advantage. The strategy highlights seven goals and objectives that the DoD believes will align the DoD's Data Strategy with industry best practices.
Everything You Should Know About Spam Filters
We are all aware of the spam folder in our email dashboard. This article deals with how spam filters automatically identify and divert spam mail from our inbox to the spam folder. Spam filters are used to screen inbound emails (the emails entering a particular network) and outbound emails (the emails leaving the network). The Internet Service Providers utilize both methods for protecting the receiver and the sender. There are many types of spam filtering solutions available.
CFEngine 3.18 LTS released - Extensibility
Today, we are pleased to announce the release of CFEngine 3.18.0! The focus of this new version has been extensibility. It also marks an important event, the beginning of the 3.18 LTS series, which will be supported for 3 years. Several new features have been added since the release of CFEngine 3.15 LTS, in the form of non-LTS releases. In this blog post we’ll primarily focus on what is new in 3.18, but we will also highlight some things released in 3.16 and 3.17.
Practical CPU time performance tuning for security software: Part 1
Software performance issues come in all shapes and sizes. Therefore, performance tuning includes many aspects and subareas, and has to adopt a broad range of methodologies and techniques. Despite all this, time is one of the most critical measurements of software performance. In this multi-part series, I’ll focus on a few of the time-related aspects of software performance — particularly for security software.
Secure By Design | The CISO Perspective
The Visibility Gap: How to Avoid Blind Spots in IT Monitoring
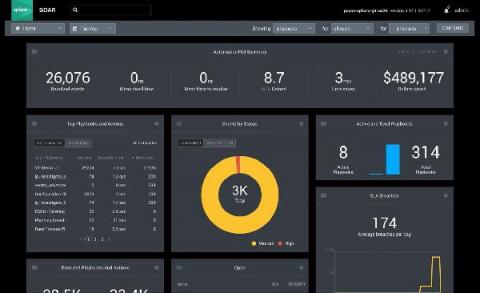
SOARing to the Clouds with Splunk SOAR
For years, security practitioners have kicked and screamed about their reality. There are too many alerts to fully investigate and manually resolve every day. There is a massive talent shortage of qualified security professionals across the globe. Then couple that with analyst burnout and siloed security point-products. All of these factors are preventing security operation centers (SOCs) from operating at their full potential, with increased efficiency, performance and speed.
Top vulnerability assessment and management best practices
By implementing these vulnerability assessment and vulnerability management best practices you will reduce the attack surface of your infrastructure. We’re human, and many things we build aren’t perfect. That’s why we take our cars for a periodic inspection, or why we have organizations certifying that products are safe to use. Software is no different.
Vulnerability Management with Sysdig
Onboarding Data in Splunk Security Analytics for AWS
Detecting and Investigating Threats in Splunk Security Analytics for AWS
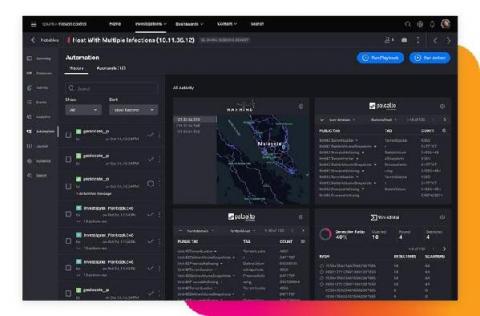
SOCtails Episode 4 - Respond Fast to Security Incidents with Automated Playbooks
How Biden's Executive Order on Improving Cybersecurity Will Impact Your Systems
President Joe Biden recently signed an executive order which made adhering to cybersecurity standards a legal requirement for federal departments and agencies. The move was not a surprise. It comes after a string of high-profile cyber-attacks and data breaches in 2020 and 2021. The frequency and scale of these events exposed a clear culture of lax cybersecurity practices throughout both the public and private sectors.
What's new in Sysdig - June 2021
Welcome to another monthly update on what’s new from Sysdig! Happy Pride month! We hope you are celebrating safely, in whatever manner you choose. It’s been over 50 years since the Stonewall riots, but we continue to fight for equality and justice. Love is love, and we’re sending you all of ours! Thank you to Marsha P. Johnson, Brenda Howard, and countless others for fighting for the freedom that many of us today enjoy.
7 Steps to Strengthen Your Security Posture
Learn more about your security posture and why it matters. Assess and strengthen your IT security posture with these critical steps.
The Increasing Popularity of Ransomware Amongst Cybercriminals
Cybercriminals are becoming increasingly savvy and ransomware attacks have soared over the last decade. A recent PwC UK Cyber Threat Intelligence report revealed a spike in cybersecurity incidents which have significantly affected many organisations that are already dealing with challenges caused by the pandemic.
Red Canary says 43% Lack Readiness to Notify Customers of a Security Breach
Introducing the World's First Modern Cloud-Based SecOps Platform: Splunk Security Cloud
To say that the past year presented its fair share of cybersecurity challenges to the InfoSec community would be a drastic understatement. The rapid migration to remote work at scale left 80% of CIOs unprepared, and SecOps teams struggled to confront the evolving threat landscape with disparate toolkits and skill sets. Not to mention that as more organizations shifted to hybrid and multi-cloud environments at scale, cloud complexity (and cloud-based threats) skyrocketed.
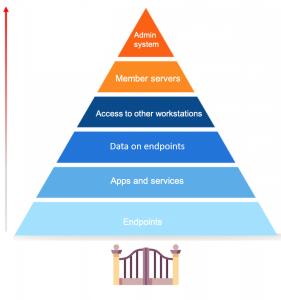
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are end-user devices like desktops, laptops, and mobile devices. They serve as points of access to an enterprise network and create points of entry that function as gateways for malicious actors. Since end-user workstations make up a huge portion of endpoints, we’ll be focusing on their security.
Rails Security Threats: Authentication
Authentication is at the heart of most web development, yet it is difficult to get right. In this article, Diogo Souza discusses common security problems with authentication systems and how you can resolve them. Even if you never build an authentication system from scratch (you shouldn't), understanding these security concerns will help you make sure whatever authentication system you use is doing its job.
Why UC Davis chose Elastic to enhance its Security Operations Center
The University of California at Davis is an agriculturally focused university of more than 30,000 students. Founded in 1905, the university performs federally funded research for the U.S. Department of Defense, U.S. Department of Agriculture, and other agencies. It’s also home to an electric power substation, police and fire departments, and even an airport. All of this combined is a digital security challenge for Jeff Rowe, the university’s cybersecurity architect.
Supply Chain Security & Robotic Heads: Open Source Matters
Welcome to the second edition of Open Source Matters: our regular publication about the latest happenings in open source! Let’s dive into the news.
Observe & Troubleshoot Your Kubernetes Environments with Dynamic Service Graph
Kubernetes workloads are highly dynamic, ephemeral, and are deployed on a distributed and agile infrastructure. Application developers, DevOps teams, and site reliability engineers (SREs) often require better visibility of their different microservices, what their dependencies are, how they are interconnected, and which other clients and applications access them. This makes Kubernetes observability challenges unique.
Threat Hunting with Cloud SIEM
The CFEngine UI gets a fresh look
In the past 2 and half months, we have refreshed the visual design of the CFEngine Mission Portal. You might already notice some differences in the navigation, iconography, and color set. This is a post to guide you through the major changes we made and also provide you an inside perspective into the design direction we are taking going forward.
Achieving the 8 guiding principles of the DOD's Data Strategy with Elastic
A modified version of this blog post appeared in the June 2021 issue of Signal magazine. Decisions that need to be made in an instant require answers in real time, but existing big data systems are unable to return queries quickly enough for real-time analytics. And with growing data being queried by more connected users than ever before, it’s getting increasingly challenging to maintain fast reaction times.
Secure Factory: Time to Step Up for the Manufacturing Industry
The ongoing news of massive cyberattacks on manufacturing and energy companies has been a wake-up call. Operational Technology (OT) Security had not been on the radar of many CISOs and plant managers until they got hit. After reacting in a defensive mode last year it is time to step up with a proactive security strategy including OT. Secure Factory by Splunk helps manufacturing companies better understand and address their unique security challenges.
Understanding the DoD's Data Strategy: Part 1
As my colleague, Tim Frank, wrote about recently in his blog post, "The Department of Defense Data Strategy: An Important Start," in late 2020 the Department of Defense (DoD) released its new Data Strategy — providing focus and direction for the Department’s efforts to become data-centric at all levels of its enterprise.
Introducing New Cloud Security Monitoring & Analytics Apps
Automate remediation of threats detected by Datadog Security Monitoring
When it comes to security threats, a few minutes additional response time can make the difference between a minor nuisance and a major problem. Datadog Security Monitoring enables you to easily triage and alert on threats as they occur. In this post, we’ll look at how you can use Datadog’s webhooks integration to automate responses to common threats Datadog might detect across your environments.
Joe Biden's Security Order: What it Means for DevOps
Cryptomining Attacks on Kubeflow: What You Need to Know
Microsoft recently reported two widespread cryptomining attacks targeting Kubeflow, a popular cloud-native platform for machine learning (ML) workloads on Kubernetes. Attackers targeted Kubeflow installations using either the Kubeflow central dashboard interface or Kubeflow Pipelines interface for scheduling crypto-mining workloads.
Splunk SOAR Playbooks: GCP Unusual Service Account Usage
As organizations increase their cloud footprints, it becomes more and more important to implement access control monitoring for as many resources as possible. In previous playbooks, we have shown examples of AWS and Azure account monitoring, but the series would not be complete without also supporting Google Cloud Platform (GCP).
Interview with Cybersecurity Specialist Jen Ayers
For our latest specialist interview in our series speaking to technology leaders from around the world, we’ve welcomed the COO of DNSFilter, Jen Ayers to share her insights from the world of cybersecurity including the latest trends she is seeing on the rise and what business leaders need to keep in mind for the rest of 2021.
The Colonial Pipeline ransomware attack: Lessons for cybersecurity teams
The recent ransomware attack on Colonial Pipeline is reportedly one of the most significant cyberattacks on the energy sector till date, and it has overwhelmed cybersecurity experts across the globe.
No One Likes Passwords and They are the Leading Cause of Data Breaches
Did you hear about the latest data breach caused by a stolen password? Technically, it was a user account security token used by the malicious cyber threat actors to gain initial access into the company’s chat workspace. Once on the IT chat channel, the threat actors impersonated an employee and then used a simple social engineering tactic to trick an IT support member into providing them with a long-lived login access token onto the corporate network.
What you need to know about Process Ghosting, a new executable image tampering attack
Security teams defending Windows environments often rely on anti-malware products as a first line of defense against malicious executables. Microsoft provides security vendors with the ability to register callbacks that will be invoked upon the creation of processes on the system. Driver developers can call APIs such as PsSetCreateProcessNotifyRoutineEx to receive such events.
Securing Modern Applications and APIs: Whose Job Is It, Anyway?
When an end user thinks of a modern application, they expect a user-friendly offering, one that works on any device, from any location, and that delivers constant innovation. To deliver on that expectation, under the hood there are a large number of distributed components (and micro-components) running heterogeneous workloads on hybrid environments.
Bad guys are watching for new openings in your cloud, are you?
You see the headlines, and perhaps, ‘thank goodness it wasn’t us’ flickers through your mind. An overly permissive web server exposes 100 million+ consumer credit applications, or an S3 bucket leaves hundreds of millions of user records open to the public. A nightmare scenario for any CISO and their cloud security team!
Splunk and Zscaler Utilize Data and Zero Trust to Eradicate Threats
SOARing w/ Splunk Phantom
Rollbar Integrations: Okta
Adversary emulation with Prelude Operator and Elastic Security
It’s no secret that organisations are up against skilled, relentless and determined adversaries. Security operations teams need to continuously test their detection capabilities by carrying out adversary emulation plans that are made up of varying tactics, techniques and procedures (TTPs) and track key metrics of their coverage in order to close any existing gaps. There are many tools available for running adversary emulation plans and performing purple team exercises.
Super Speed with Phantom Slash Commands
Are you the type of person who loves the command-line? Is tab-complete your friend? Do you move faster on a keyboard than with a mouse? Then Phantom Slash Commands are for you!
LDAP authentication with Sensu Go: troubleshooting & tips (Part 2)
Sensu creator and Developer Advocate Todd Campbell recently wrote about using LDAP authentication for single-sign on (SSO) with Sensu Go. That post provided a great overview of Sensu authentication and included some useful LDAP troubleshooting tips. In this post, we'll focus on the Sensu LDAP implementation and explore how SSO/LDAP users are linked to RBAC "profiles" (i.e. Roles and ClusterRoles). We'll also demonstrate how Sensu supports multiple LDAP providers thanks to its groups_prefix feature.
3 Work-From-Anywhere IT Security Pressures
Five worthy reads: Confidential computing - The way forward in cloud security
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. In light of rising concerns over cloud cybersecurity, this week we explore the concept of confidential computing. The past year has seen strong adoption of cloud technologies due to accelerated digital transformation and a cloud-first approach in business.
Applying policy as code in the modern cloud-ready enterprise: Graeme Hay, Morgan Stanley
2021 Building an SDWAN Requirements Document and Vendor Selection
The Crossroad of Security & Observability in Kubernetes: A Fireside Chat
Ensuring adequate security, observability, & compliance for cloud native applications
Observations from the field: Best Practices for Securing your Kubernetes Clusters
3 ways to improve your enterprise IT security
You’ve undoubtedly heard the saying, “A chain is only as strong as its weakest link.” The same idea applies to your IT systems. They’re only as secure as their weakest vulnerability. No organization wants to fall victim to a cyberattack. These three ServiceNow webinars will help prepare you to boost your enterprise IT security and, ultimately, safeguard your business.
Upgrading DevSecOps with compliance automation - Bryan Langston, Mirantis
Building secure and observable Kubernetes platforms for scaled software delivery
Exploring intrusion detection techniques in cloud native environments - Garwood Pang, Tigera
Service Mesh, Observability and Beyond - Sheetal Joshi, AWS
Kubernetes Observability & Troubleshooting: Best Practices - Raj Singh, Box
The Importance of Modularity and Multiple Dataplanes - Chris Tomkins, Tigera
Calico/VPP : Unlocking performance & innovation for large scale Kubernetes clusters
Beyond the network: Next Generation Security and Observability with eBPF - Shaun Crampton, Tigera
Join Us to learn Service Mesh, Observability and Beyond
Completing the security testing automation cycle
DevOps, DevSecOps and CI/CD are synonymous with one word - automation. Automating their workflows gives developers the ability to deliver consistency, time savings, and useful insights into their software development life cycle (SDLC). But automation is only as efficient as your weakest link or most cumbersome bottleneck, which can sometimes be security testing. Security testing has traditionally been carried out either manually or quite late in the process.
Threats targeting Kubernetes and Defences
Securing Kubernetes workloads at Discover Financial Services
How to Avoid Domain Hijacking
After you register the domain for your website, you might take pride in owning your company’s online address. However, from a legal standpoint, you don’t own it. While you can register it, thieves can hijack it from you. Domain hijacking does not receive a lot of attention, but it is a real threat. Domain hijacking is also very frustrating, as it is relatively easy for thieves to hijack a domain, and once they get control, it can be very difficult and expensive to regain it.
How to rightsize the Kubernetes resource limits
Kubernetes resource limits are always a tricky setting to tweak, since you have to find the sweet spot between having the limits too tight or too loose. In this article, which is a continuation of the Kubernetes capacity planning series, you’ll learn how to set the right Kubernetes resource limits: from detecting the containers without any limit, to finding the right Kubernetes resource limits you should set in your cluster.
Enabling You to Get the Best from AWS: Introducing the New Calico AWS Expert Certification
Calico is the industry standard for Kubernetes networking and security. It offers a proven platform for your workloads across a huge range of environments, including cloud, hybrid, and on-premises. Given this incredibly wide support, why did we decide to create a course specifically about AWS?
Wall Street Journal Predicts Dire Cybersecurity Days Ahead, Endorses Zero Trust
Let’s be honest for a second. This is a corporate blog. Yes, we aim to provide our readers with actionable, educational information. And, yes, we strive for complete transparency. But, at the end of the day, we understand if you’re skeptical of some of what’s written here. We’re a business, not a news publication, and it’s impossible for us to be completely unbiased all the time.
Detecting Password Spraying Attacks: Threat Research Release May 2021
The Splunk Threat Research team recently developed a new analytic story to help security operations center (SOC) analysts detect adversaries executing password spraying attacks against Active Directory environments. In this blog, we’ll walk you through this analytic story, demonstrate how we can simulate these attacks using PurpleSharp, collect and analyze the Windows event logs, and highlight a few detections from the May 2021 releases.
Improve Your Cybersecurity with a Secure Software Development Supply Chain
The U.S. government is instituting stricter requirements on federal agencies and federal contractors to address cybersecurity threats. Adopting the right set of tools and practices will help organizations secure their software development supply chains and be prepared to meet these standards. However, the initial requirements also provide a valuable framework for any organization trying to reduce its security risk—not just government institutions and those doing business with them.
Digital Data Loggers vs. Chart Recorders. When To Upgrade
Automated Falco rule tuning
We recently released the automated Falco rule tuning feature in Sysdig Secure. Out-of-the-box security rules are a double-edged sword. On one side, they allow you to get started right away. On the other, it can take many working hours to learn the technology, configuration, and syntax to be able to customize the rules to fit your applications. Falco’s default security rules are no different.
CVE-2021-31440: Kubernetes container escape using eBPF
In a recent post by ZDI, researchers found an out-of-bounds access flaw (CVE-2021-31440) in the Linux kernel’s (5.11.15) implementation of the eBPF code verifier: an incorrect register bounds calculation occurs while checking unsigned 32-bit instructions in an eBPF program. The flaw can be leveraged to escalate privileges and execute arbitrary code in the context of the kernel.
Can They Really See That Data? Auditing Access Controls Across Environments
How South Dakota Bureau of Information and Telecommunications deploys Elastic to secure endpoints
The South Dakota Bureau of Information and Telecommunications (BIT) provides quality customer services and partnerships to ensure South Dakota’s IT organization is responsive, reliable, and well-aligned to support the state government’s business needs. The BIT believes that “People should be online, not waiting in line.” The bureau’s goals for the state's 885,000 residents include.
SolarWinds and the Secure Software Supply Chain
In early 2020, threat actors breached the build systems of Solarwinds and used this access to add malicious code into one of SolarWinds products. The product, called “Orion”, is very widely used and deployed by tens of thousands of companies, including many Fortune 500 companies.
Ensure Cloud Security With These Key Metrics
A cybersecurity journey: An airline's push to be digital-first
The airline industry faces years of uncertainty as the world recovers from the impact of COVID-19. Airlines will focus on operational efficiency and the means to adapt quickly to changing circumstances and new opportunities. Passengers may be required to carry a vaccine passport, most likely a digital solution, which could bring a host of data security complexity. For these reasons and more, Scandinavian Airlines System (SAS) aspires to be a digital-first airline.
ProblemChild: Generate alerts to detect living-off-the-land attacks
In an earlier blog post, we spoke about building your own ProblemChild framework from scratch in the Elastic Stack to detect living off the land (LOtL) activity. As promised, we have now also released a fully trained detection model, anomaly detection configurations, and detection rules that you can use to get ProblemChild up and running in your environment in a matter of minutes.
Total Economic Impact study: Elastic delivers 10X performance with up to 75% cost savings
Ten times faster at a fraction of the cost. If you want a headline as to why you should consider adopting Elastic for security and observability, that is it. We often work with our customers to help them establish the business value of Elastic within their organizations. We commissioned Forrester to conduct a Total Economic Impact (TEI) study of our security and observability solutions so our customers have an unbiased view that they can share with their internal stakeholders.
Tales of a Principal Threat Intelligence Analyst
At Splunk, we’re constantly on the hunt for new and emerging threats — tirelessly developing detection techniques to zero in on bad actors, while sharing key intelligence around cybercrime activity. But because threat intelligence can relate to so many different things — ranging from spear phishing campaigns to dark web dealings — it can be a challenge to cover and define all the specifics of what (or who) to look out for.
Protecting Windows protected processes
This quick blog is the first in a two-part series discussing a userland Windows exploit initially disclosed by James Forshaw and Alex Ionescu. The exploit enables attackers to perform highly privileged actions that typically require a kernel driver.
EO, EO, It's Off to Work We Go! (Protecting Against the Threat of Ransomware with Splunk)
On June 2nd, 2021, the White House released a memo from Anne Neuberger, Deputy Assistant to the President and Deputy National Security Advisor for Cyber and Emerging Technology. The subject? “What We Urge You To Do To Protect Against The Threat of Ransomware.” It outlines several recommendations on how to protect your organization from ransomware. The memo was a follow-up to President Biden’s May 12th Executive Order on Improving the Nation’s Cybersecurity Order (EO14028).
Testing the latest CFEngine features locally with nightly builds and vagrant (Developer Demo)
Hunting APTs with threat intelligence and EQL
Resolve network security issues efficiently with the Firewall Analyzer-ServiceDesk Plus integration
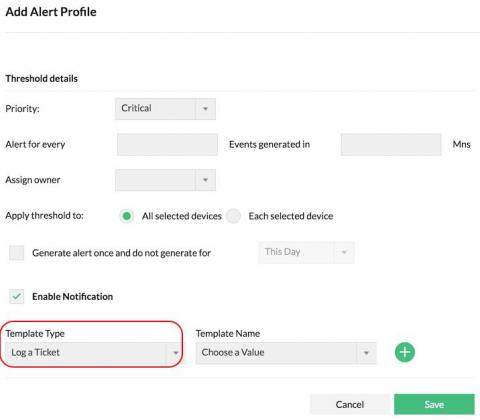
ManageEngine Firewall Analyzer reviews firewall logs to capture network security threats. It generates alerts upon detecting security threats and attacks, and notifies you, the security administrator, in real time. You can configure alerts to be sent via email, SMS, and more. With these real-time notifications, you can troubleshoot to take instant remedial action. You can also make changes to your firewall policies and configurations to prevent recurring security incidents.
Tackling remote workforce security challenges post-pandemic
In the wake of the COVID-19 pandemic, many organizations are adopting or experimenting with new models of long-term remote work. For some, that means keeping their teams fully distributed. For others, it means giving employees more flexibility to work from home or even simply putting plans in place for the future. But this shift to remote work brings new challenges that both large enterprises and smaller organizations must face.
What you need to consider when changing to a different operating system
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.
Ensuring compliance with DISA STIGs, NIST 800-53, CMMC, and RMF
This blog is the second in a four-part series on infrastructure automation for government agencies that are modernizing digital systems while grappling with budget and staffing constraints and the challenges of COVID-19.
Protecting digital privacy and using technology for good
Introducing Sumo Logic Cloud SIEM powered by AWS
How to Proactively Plan Threat Hunting Queries
As your security capabilities improve with centralized log management, you can create proactive threat hunting queries. Setting baselines, determining abnormal behavior, and choosing an attack framework helps you mitigate risk and respond to incidents. To reduce key metrics like the mean time to investigate (MTTI) and mean time to respond (MTTR), security operations teams need to understand and create proactive queries based on their environments.
Kubernetes Security Using Kube-Bench - Saiyam Pathak
Going Beyond Exclude Patterns: Safe Repositories With Priority Resolution
Long Weekend and you Locked Yourself Out of Your Computer
The latest Verizon DBIR report is out and we all should realize, normal is not the new workplace. Picture this: You’re logging into the work account after a long weekend of gratitude, remembrance and maybe even getting to hug someone safely. Okay, we’re exaggerating a little but variations of this scene are playing out all over the country this week. You’re frustrated and you haven’t even gotten started on the work that piled up over the weekend.
Google Authenticator and Pandora FMS, defend yourself from cyberattacks
For a long time, the Internet has been an easily accessible place for most people around the world, full of information, fun, and in general, it is an almost indispensable tool for most companies, if not all, and very useful in many other areas, such as education, administration, etc. But, since evil is a latent quality in the human being, this useful tool has also become a double-edged sword.
Understanding Splunk Phantom's Join Logic
If you’re an active Splunk Phantom user, it’s safe to assume you know what a playbook is. If not, here’s a quick summary: Phantom playbooks allow analysts to automate everyday security tasks, without the need for human interaction. Manual security tasks that used to take 30 minutes can now be executed automatically in seconds using a playbook. The result? Increased productivity and efficiency, time saved, and headaches avoided.