Operations | Monitoring | ITSM | DevOps | Cloud
April 2022
SQL Injection: Types, Examples, Prevention
Catchpoint Achieves ISO/IEC 27001:2013 Certification
7 Cybersecurity Statistics Every SMB and MSP Needs to Know in 2022
Cybersecurity isn’t just at the top of the discussion queue within the IT channel. Businesses and governments worldwide have turned a sharp eye toward rising cyber threats. Many have learned the hard way that small businesses are frequent targets of cyberattacks. The idea of “targeting a victim” itself has come into question, and more realize that widespread, indiscriminate attacks are the status quo.
Spring4Shell and the future of zero-day threats
When zero-day vulnerabilities are discovered, Cisco Secure Application can help deliver the visibility and threat detection your applications need to thwart an attack.
CFEngine: The Agent Is In 12 - Spacemacs For CFEngine
How B2B Brands Can Protect Critical Business Information Through Cybersecurity
Is it DDOS or is it you?
Server load can tell you a lot about your day-to-day user traffic. A sudden spike in server traffic can indicate an attack, but that’s not always the case. As website and performance monitoring become more mainstream, and you add a wider variety of backend testing and web monitoring checks to your infrastructure – you have to ask the question – Is that spike in server traffic DDOS? Or is it me…
Automated Threat Hunting: A Closer Look
Proactively finding and eliminating advanced threats through threat hunting is a growing necessity for many organizations, yet few have enough resources or skilled employees to do it effectively. For those who do have an active threat hunting program, the process is often manual and time consuming. With cloud security automation, however, you can implement rules that automatically adjust your security policies based on the latest threat data.
What Are The Different Types of Authentication?
Getting started with CFEngine Pt. 2 - Modules from CFEngine Build
Getting started with CFEngine Pt. 3 - Reporting & Web UI
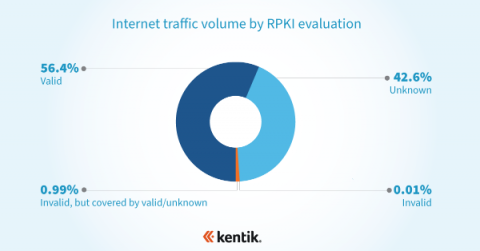
Measuring RPKI ROV adoption with NetFlow
Resource Public Key Infrastructure (RPKI) is a routing security framework that provides a mechanism for validating the correct originating autonomous system (AS) and prefix length of a BGP route. Route Origin Authorization (ROA) is a cryptographically signed object within the RPKI that asserts the correct originating AS and prefix length of a BGP route. For as long as the internet has existed, the challenge of securing its underlying protocols has persisted.
Why Is Normalizing Log Data in a Centralized Logging Setup Important: Operations & Security
The phone rings. Your email pings. Your marketing team just told you about a flood of messages on social media and through live chat that there’s a service outage. You thought your Monday morning would be calm and relaxed since people are just returning from the weekend. How do you start researching all of these incoming tickets? How do you know which ones to handle first? Is this just a hardware failure, or are you about to embark on a security incident investigation like Log4j?
Getting started with CFEngine Pt. 1 - Installation
The Anatomy of a Cybercrime: Dissecting a Phishing Attack
Our previous blog provided an outline of the current phishing trends and potential consequences of not being aware of them. This article, however, takes a deep dive into a particularly dangerous type of attack. There is a large amount of phishing that is targeting webmail users on non-free mail domains in an attempt to syphon out their credentials for later use.
How Network Monitoring Defuses Hacker Bombs
You know by now that hackers literally never sleep. Chances are your network has been hit before and absolutely will be hit again. Hackers invent new techniques every day and tweak existing ones, many of which are automated—which is why we can say that hackers literally never sleep. Hackers either attack your network directly or attack your infrastructure through your network. Either way, the network itself is your first line of defense.
Five Things a Secure Access Service Edge Plan Should Include
Getting started with CFEngine Pt. 2 - Modules from CFEngine Build
Two-factor authentication in Pandora FMS
I have been a regular user of Pandora FMS for years and the best I can say about them is that they always have something new to add to my learning. Today, for example, I rediscovered the Two-Factor authentication in Pandora FMS! *And I did it, in part, through this article already published on their blog Although I devote myself to programming (and it is what I like to do the most), I am more of a Web 2.0 person than a Web 3.0 person because I consider that the latter has been abused too much.
Why Use Storage as a Service
What Is Identity Lifecycle Management?
If you help to manage cloud environments, you’re probably familiar with the concept of identity lifecycle management. Identity lifecycle management helps you keep track of who is allowed to do what within your cloud. But merely understanding identity lifecycle management isn’t enough to administer modern cloud identities effectively. You also need a way to automate identity lifecycle management at massive scale.
Advanced Traffic & Security Analysis in WhatsUp Gold with Progress Flowmon
5 New Aethon TUG Robot Vulnerabilities Expose Healthcare Facilities to IoMT Hackers
Healthcare providers must be extremely vigilant in their cybersecurity defense posture. After all, vulnerabilities in the Internet of Medical Things (IoMT) cost hospitals nearly $21 billion in 2021. New security discoveries by Ivanti partner Cynerio recently made that statistic personal for many providers. While working with an existing healthcare customer, Cynerio found five zero-day vulnerabilities in Aethon TUG autonomous robots – an IoMT device found in many healthcare facilities.
ZScaler Event Optimization with Cribl Stream
ZScaler delivers a suite of well-regarded products for helping IT securely move from network infrastructure to the cloud, using principles of zero trust. According to their website, they have 5,600+ customers and process 200B+ daily transactions.
Tools for Threat Hunting and IT Service Risk Monitoring
Cybersecurity can often seem intimidating for IT teams. After all, things like “threat hunting,” “red teaming,” and “blue teaming” are not used in IT operations. On the other hand, just because these words are terms of art doesn’t mean that they’re activities you don’t do already. You’re probably already using log data as part of your IT operations incident response.
Using Global Namespaces and Zero-Trust Policies with VMware Tanzu Service Mesh
VMware Tanzu Service Mesh delivers a federated Istio service that brings significant value for enterprise customers beyond the core open source project, improving application security, resiliency, and multi-cloud operations.
2022 MITRE ATT&CK Evaluation Results Are In-What You Need to Know
It’s that time of the year again! The MITRE Engenuity ATT&CK evaluation results are in and generating quite the buzz in the industry. And for good reason. The MITRE Engenuity ATT&CK evaluation focuses on a tool’s ability to prevent and detect cyber attacker behaviors. Now in its fourth round of testing, it has become the de-facto standard for how security solutions perform against different advanced cyberattack scenarios.
Using Google Workspace Data for Security Observability
Keeping your systems secure is a never-ending challenge. Not only is it necessary to monitor and secure your own tech stack, but each new service a company uses creates another potential avenue for bad actors to try to exploit for their own ends.
Are disconnected RDP sessions ticking time bombs in your network?
I think we’ve all been there before – you log on to a server remotely via RDP, and do the needful – but don’t immediately log off. But then you get distracted by a phone call, an email, a chat, or a good old-fashioned physical interaction with another human being. So when it comes time clock out for the night, you shut down your computer or log off. Or maybe you’ve been working on a laptop and your VPN got interrupted.
Seamlessly Secure Your Cloud Workloads
You’ve secured your cloud identities. You’ve hardened your cloud security posture. You’ve configured strong cloud access controls. But there’s still one more thing you need in order to secure your cloud environment: a cloud workload protection platform, or CWPP. Cloud workload protection platforms secure the workloads that run on your cloud — which are distinct from the infrastructure, user identities and configurations that form the foundation of your cloud environment.
SAST vs DAST: what they are and when to use them
As digital transformation accelerates and more organizations use software solutions to facilitate work operations, security threats have become more commonplace. Cybercriminals tirelessly develop ways to exploit software application vulnerabilities to target organizational networks. A notable example is the 2017 Equifax data breach, which exposed the personal details of 145 million Americans.
Kubernetes Master Class: Securing the Supply Chain and Infrastructure for Kubernetes Deployments
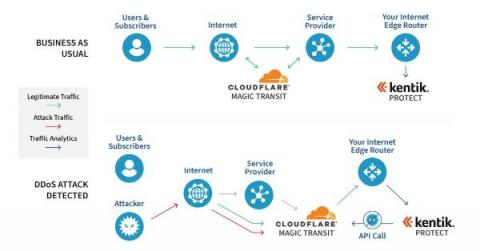
Working with Cloudflare to mitigate DDoS attacks
The rolling thunder of cybersecurity warnings has built to a crescendo this year. According to HelpNetSecurity, cybercriminals launched over 9.75 million DDoS attacks in 2022. The Cloudflare Attack Trends 2022 Q1 Report published yesterday shows an alarming increase in application-layer DDoS attacks. And our own Doug Madory has been sharing analysis on the impact of cyberattacks, too.
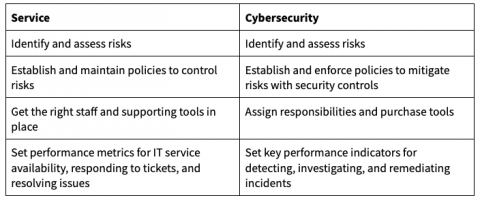
Use Service Design in Operations Management to Enhance Security
As an IT operations manager, you spend a lot of your time mitigating service outages and service level risks. You worked diligently to get the right people, products, processes, and partners in place to meet your goals. You managed to ensure continued uptime. You’ve reduced the number of tickets and the cost per ticket. And for your efforts, you’re rewarded with managing your company’s cybersecurity program. The problem? You’re not a security specialist.
Building a Culture of Security: Practical Tips to Spot a Phish
Technologies exist to limit and spot the number of phishing emails that come into your business. Still, humans are the last line of defense against social engineering attacks like this at the end of the day. At some point, you're going to "be beat" as an employer or MSP. Instead of locking everything down and slowing business communications, staff from the c-suite on down need to be equipped to identify phishing emails, so the worst happens in a training environment and not the real thing.
Automatically Add IP Addresses to a Penalty Box in Cloudflare with Torq
Good security may come from strong defenses, but strong security comes from a good offense. This is especially true for network security, where minutes can make the difference between a breach and a near miss. For example, if an unknown IP address triggers an alert for suspicious or abusive behavior, the faster you can isolate and block that address, the less likely it is that the person or entity at the other end can do damage.
DevOps vs. DevSecOps: What Are the Differences?
I've never really been sure how DevSecOps differs from plain-old DevOps, but over the past year I think there's finally something enough there to have a notion. To be concise, DevOps-think makes software delivery better by moving operations concerns closer to development with the help of a lot of automation and process change.
Going Beyond Dynamic Data Masking
Be Proactive Amid Growing Cyber Security Concerns
Over the past few weeks, we’ve all been paying very close attention to the events unfolding in eastern Europe. As an individual, it’s heartbreaking to see a war break out and the impact it’s having across the region. We know that cyberattacks are now a part of war. We also know cyberattacks can be targeted, but also have the potential for unintended consequences and increased impact as they can spread outside of the initial target.
How Privacy Organizations and NGOs Help Build a Better Society
6 Things You Should Know Before Incorporating Data Into Your Business Plan
Cilium network policy security tutorial on Civo
Achieve End-to-End Network Visibility for SASE
Using OpenID Connect identity tokens to authenticate jobs with cloud providers
Introducing OpenID Connect identity tokens in CircleCI jobs! This token enables your CircleCI jobs to authenticate with cloud providers that support OpenID Connect like AWS, Google Cloud Platform, and Vault. In this blog post, we’ll introduce you to OpenID Connect, explain its usefulness in a CI/CD system, and show how it can be used to authenticate with AWS, letting your CircleCI job securely interact with your AWS account, without any static credentials.
Data-Aware Security: How to Take a 360 View of Cloud Security
Don’t let your organization fall victim to data exposure; a well-defined strategy will cover all aspects of the cloud shared responsibility model and keep your data secure. Not long ago, security concerns were the number one reason IT executives hesitated to move workloads to the cloud. Much has changed since then. Security is now considered one of the great strengths of both cloud infrastructure and software-as-a-service (SaaS) platforms. But that doesn’t mean total security is assured.
Heroku Vs. AWS: Data Security Comparison
What is the Most Vulnerable Data My Company Holds?
Data security is on every priority list in 2022. With the frequency of breaches never higher, many businesses assess their situation and ask cybersecurity questions. With cybersecurity policy, everything boils down to risk. Ultimately, every decision-maker wants to know, “how likely are we to be attacked?” Many believe cybercriminals only target certain kinds of data. Sensitive information, high-value financial data, and medical records are all widely accepted to carry a high risk.
Using Log Management as a Security Analytics Platform
With the rising tide of data breach awareness, your senior leadership is asking you to mitigate cybersecurity risk with security analytics. You’ve built up the use cases and started researching different platforms. Then, you realized: you’re not sure you have the budget. The typical security analytics platforms come with upfront technology costs as well as the “hidden fees” associated with training your team members. You know you need to use analytics to help mitigate risk.
A practical guide to container networking
An important part of any Kubernetes cluster is the underlying containers. Containers are the workloads that your business relies on, what your customers engage with, and what shapes your networking infrastructure. Long story short, containers are arguably the soul of any containerized environment. One of the most popular open-source container orchestration systems, Kubernetes, has a modular architecture.
You want to know whether a dangerous stranger has your passwords?
We already live in a post-apocalyptic future that has nothing to envy to great franchises like Mad Max or Blade Runner. Proof of this are pollution, pandemics and the fact that your most intimate secrets can be violated because your most impenetrable slogans are in a database of leaked passwords. Do you feel that pinch? It’s fear and cruel reality knocking at your door at the same time. But, well, let’s stand by. Just as Mel Gibson or Harrison Ford would do in their sci-fi plots.
18 Best Cybersecurity Movies Worth the Watch
Synchronize data between PostgreSQL and files
Databases are great for data processing and storage. However, in many cases it is better or easier to work with data in files on a file system, some tools even cannot access the data in any other way. When a database (DB) is created in a database management system (DBMS) using a file system as its data storage, it of course uses files on the given file system to store the data.
Spring4Shell Zero-Day Vulnerability: Overview and Alert Upon Detection for CVE-2022-22965
On March 29, 2022, a critical vulnerability targeting the Spring Java framework was disclosed by VMware. This severe vulnerability is identified as a separate vulnerability inside Spring Core, tracked as CVE-2022-22965 and canonically named “Spring4Shell” or “SpringShell”, leveraging class injection leading to a full remote code execution (RCE).
Bringing the SaaS ecosystem together to improve cybersecurity
In today’s digital environment, no company is immune to cyberattacks. In fact, more than one-third of organizations worldwide have experienced a ransomware attack or breach that blocked access to systems or data, according to IDC.1 From the Capital One incident to the SolarWinds attack, businesses and organizations of all facets and sizes are at the forefront of such threats.
Are You GDPR-Aware?
Since 2018, General Data Protection Regulation (GDPR) has been on everyone’s lips – and for good reason. It’s the gold standard for consumer protection. While privacy laws present challenges to enterprises big and small, we can’t escape the reality that consumer data is constantly mined and sold.
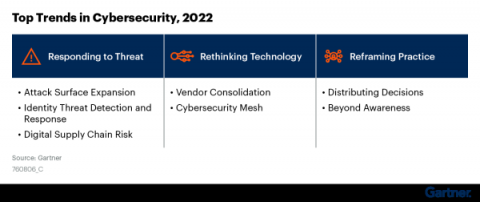
Top Trends in Cybersecurity 2022: A Gartner Report
Gartner recently released a report highlighting the top trends in cybersecurity for 2022. They discuss how businesses must reframe their security practices, rethink their technology, and adopt new responses to modern threats. This is in line with DevSecOps trends that we see in the market and hear about from our customers. Companies that are working in this way are taking a more holistic approach to cybersecurity by adopting tools that speed up and, when possible, automate security.
Modern Security Operations Center Framework
With agile development, the software development life cycle has evolved, with a focus on customer satisfaction to enhance product features based on user feedback. This helps shorten the time to market, since teams can release a minimally viable product, then continuously improve its features. The agile technique encourages team cooperation through sprints, daily standups, retrospectives, testing, quality assurance and deployment.
What makes Qovery secure?
Security intelligence analytics: Planning Increases ROI
It’s been a week. A long week. After the most recent Board of Directors meeting, your senior leadership tasked you with finding a security analytics solution. Over the last month, you’ve worked with leadership to develop some basic use cases to determine which solution meets your security and budget needs. You started your research, but everything on the market seems really overwhelming.
Spring4Shell: Responding to Zero-Day Threats with the Right Data
On March 30th, 2022, rumors began to swirl around a GitHub commit from a researcher containing proof of concept (POC) exploit code. The exploit targeted a zero-day in the Spring Core module of the Spring Framework, and was quickly confirmed against specific versions of Spring Core with JDK 9 and above. Anything running Tomcat is most at risk given the POC was based on Tomcat apps. This threat posture will evolve over time as new vectors and payloads are discovered and distributed.
Apple Zero-Day: How to Spot Devices to Update in Your Company in Seconds
5 Challenges to Security Operations Strategies
Do you love SecOps in theory, but just can't seem to make it work in practice? Or, maybe you've already implemented a security operations strategy to some degree within your organization, but struggle to make IT operations and security jive as seamlessly as you would like? Either way, there's a good chance that your troubles stem from one or more of the common barriers to SecOps strategies. This article explains why businesses often fail at implementing SecOps successfully and how they can work around the roadblocks.
April/2022 - CVE-2022-22965: Spring4Shell Remote Code Execution Mitigation
Recently, a Remote Code Execution vulnerability was discovered in the Java Spring Core library. This vulnerability allows attackers to execute arbitrary code on affected systems. You can find more information on that vulnerability in the announcement on the Spring Blog. While HAProxy Enterprise, HAProxy ALOHA, and other products within the HAProxy Technologies portfolio are not impacted by this (they do not use the Spring Core library at all), you can use our products to mitigate the attack.