Operations | Monitoring | ITSM | DevOps | Cloud
May 2022
Puppet and Government: Achieving Zero Trust adoption and mission success at the same time
Government agencies have been working diligently to comply with the 2021 Executive Order on Improving the Nation’s Cybersecurity. The Executive Order (EO) addresses cybersecurity issues by imposing a new series of federal-wide Zero Trust mandates. Agencies were required to submit their plan development and cloud migration path reporting by July and August of 2021, with more deadlines on the horizon.
Automated Developer-First Security: Our Partnership with Snyk
Today’s developers move at increasingly rapid speed – making it more critical than ever to identify and resolve code vulnerabilities early in the software development lifecycle. By tackling security early – instead of waiting until testing and deployment – engineering teams can reduce unnecessary patching and maintenance cycles, reduce risks, and ensure timely delivery of new features.
Boosting your cluster networking with the Calico VPP data plane (beta)!
Calico v3.23 is out, and with it a lot of new features! This release marks a long-awaited milestone for me and my team, as it includes the Calico VPP data plane (beta). So now seems to be a good time to reflect on what this integration actually is, and why we built it.
Redgate Software Adopts Policy-Driven Approach to Data Protection with New Data Catalog Release
CFEngine: The Agent Is In 13 - Custom Promise Types
IVANTI INSIGHTS: Healthcare and Cyber Security with Daniel Brody and Chad Holmes
The pandemic has indeed caused a massive spike in cybercrime
Recent events of the pandemic have facilitated a rapid implementation of remote working tools, causing an increase in ransomware attacks – businesses suffer from financial and data losses. In order to prevent such attacks, companies must not only educate their employees about best cybersecurity practices but also embed professional security solutions within the internal business processes and systems.
Role-Based Access Control (RBAC) in eG Enterprise
eG Enterprise is a single pane of glass that provides monitoring and oversight of every layer and tier of your IT infrastructure. However, this does not mean every user in the organization has the same view of the IT infrastructure or needs to use the tool in the same way. In fact, controlling a user’s view of the monitored applications and infrastructure, as well as their privileges to perform tasks and access data via Role-Based Access Control, is a critical feature for our customers.
Introducing The NinjaOne 5.3.2 Release
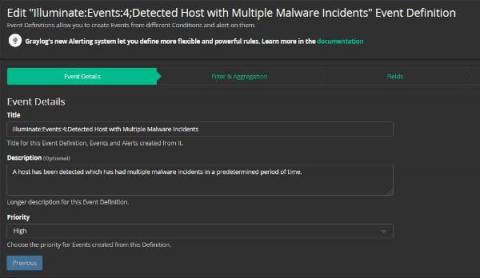
BIG things are Happening at Graylog!
Did you hear the news? Graylog is on a mission to help make your IT environment and data more efficient and secure by making it super easy to uncover the answers stored in your machine data. At Graylog, coming up with solutions to problems faced by IT and Security professionals is what drives us. Our teams are always working on ways to add meaningful functionality that increases productivity so you can focus your resources on the innovation and core competencies that you’re known for.
Cybersecurity Measures Every Project Manager Should Know About
Introducing our brand new (and free!) Calico Azure Course
Calico Open Source is an industry standard for container security and networking that offers high-performance cloud-native scalability and supports Kubernetes workloads, non-Kubernetes workloads, and legacy workloads. Created and maintained by Tigera, Calico Open Source offers a wide range of support for your choice of data plane whether it’s Windows, eBPF, Linux, or VPP. We’re excited to announce our new certification course for Azure, Certified Calico Operator: Azure Expert!
The Evolution of Software Trends in 2022
How to Automate Intune Device Reports with Torq
Whether for managing remote teams, supporting ‘bring your own device’ (BYOD) policies, or simply another layer in a data protection strategy, services like Microsoft Intune offer greater control over the devices on your network. But using the data from these services often requires tedious prep work, and this process is likely repeated multiple times a week, if not daily. Tedious, repetitive, structured: these are all signs that a process can and should be automated.
Winning Over the Skeptics: How SD-WAN Is Transforming Government Networks
Beginners Guide to Kubernetes Secrets - Civo Academy #CivoCloud
Why Choice and Control Matters with Observability and Security Data
“We lost choice and control when we migrated to Splunk Cloud, but got it back when we adopted Cribl Stream.” The above quote is from a new Cribl customer talking about why they adopted Cribl Stream to manage observability and security data.
Airline Data Breaches
Travel websites, in particular airlines are key targets for cyberattacks, the reward for compromised data is high in this industry due to the sensitivity of the data involved. Over the years, there have been a number of airline data breaches, with some companies suffering multiple attacks. By analysing some of the major airline and travel attacks over the years and being aware of tactics used by hackers, security procedures can be put in place to prevent attacks.
Secure Supply Chain: Verifying Image Signatures in Kubewarden
After these last releases Kubewarden now has support for verifying the integrity and authenticity of artifacts within Kubewarden using the Sigstore project. In this post, we shall focus on verifying container image signatures using the new verify-image-signatures policy. To learn more about how Sigstore works, take a look at our previous post
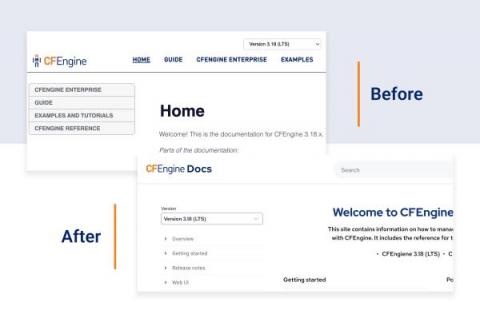
5 improvements coming to the CFEngine Docs
This year, we are improving CFEngine’s ease of use, so it should come as no surprise that we need to rethink our documentation site. For software like CFEngine, great documentation is not just “nice to have”, but a must for our users, both beginners and experienced. CFEngine has helped DevOps teams to automate their day-to-day tasks and make better decisions by providing a holistic overview of their systems.
The Crucial Difference Between IT Security and IT Compliance
What is SaaS Cloud Security and What Are SaaS Security Best Practices?
Uptrends launches new solution for SMS-based 2FA transaction monitoring
As web applications and other digital solutions become more prevalent in everyday life, securing access to these apps against cyber threats becomes more an integral part of their design rather than a separate line of thought. Global cybercrime costs are expected to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025.
Latest Features Enhance Workflow Creation, Add Modern Controls
The consensus on the state of cybersecurity professionals tends to fall somewhere between “burdened by high volumes of responsibility” and “dangerously understaffed and suffering from unhealthy levels of stress,” depending on how optimistic your source is.
New 2022 Report: Alarming Ransomware Trend Shows No Sign of Reversing
It’s no secret that ransomware threats skyrocketed – in both volume and boldness – during the pandemic. Threat actors capitalized on the sudden transition to remote work and the resulting lapses in security. Now that the working world is beginning to settle into a permanent Everywhere Workplace, you might think the ransomware trend would begin to reverse. Not so, according to a new report from Ivanti. The report details ransomware trends from Q1 2022, and the findings are bleak.
4 Key Steps of a Vulnerability Management Process
Vulnerabilities within an IT environment pose a big security risk and are a threat to digital data within an organization. These vulnerabilities can be exploited by others, or a lack of necessary precautions can result in damaged or lost organizational data. Therefore, it is essential to have a vulnerability management process in place for these reasons.
What is UAC Virtualization? Benefits and Pitfalls
Top 3 Ways Remote Working Has Unknowingly Increased Your Security Risk
Riverbed Webinar Demo - Security Workflows
Securing SD-WAN in a Cloudy World
How Zero Trust Enables Work from Anywhere and Builds Toward a SASE Vision
What's New in Calico v3.23
Hey everyone. We’re excited to announce the release of Calico v3.23! Thanks to everyone in the community who contributed to the release. We could not have fitted this many improvements in without you. To view the detailed release notes, please visit us here. While we have many improvements in this release, here’s a brief overview of some of the larger features to be aware of.
3 Agile SIEM Requirements for Agile Security Teams
Regardless of economic conditions, IT usually operates under an axiom no one in business ever likes to hear: “We have to do more with less.” Doing more with less is essentially the default position for IT, but when it comes to security operations, that position can have real consequences.
Ransom Threats and Higher Education
Higher education is a hot spot for physical and digital threats. However, digital threats have pushed the world of higher education to a breaking point, with ransomware becoming one of the most devastating threats to higher education in recent years.
The Top 10 Best DevSecOps Tools for 2022
Why should you use Single Sign-On?
Why should you use Single Sign-On? It’s simple; one less password!
Centralized Log Management for Reporting Compliance to Management
It’s 3pm on a Wednesday, and you’re really just done with the week already. You hear that “ping” from your Slack and know that you set notifications for direct messages only, which means, ugh, you have to pay attention to this one. It’s your boss, and she’s telling you to check your email. Then you see it, the dreaded audit documentation request. This will take you the rest of today and most of tomorrow.
What Should I Know About Defending IoT Attack Surfaces?
The Internet of Things needs to be part of the overall corporate information security policy to prevent adversaries from using these devices as an entry point. There are several reasons why it’s critical for organizations to defend their IoT attack surface, most importantly being that IoT devices are powerful systems containing compute, storage, and networking that threat actors view as the easiest way to breach an organization or enable exploits.
Three Ways COVID-19 Altered Federal, State IT Budget Allocations
5 Ways Automated Incident Response Reduces Toil
Toil — endless, exhausting work that yields little value in DevOps and site reliability engineering (SRE) — is the scourge of security engineers everywhere. You end up with mountains of toil if you rely on manual effort to maintain cloud security. Your engineers spend a lot of time doing mundane jobs that don’t actually move the needle. Toil is detrimental to team morale because most technicians will become bored if they spend their days repeatedly solving the same problems.
How Advances in Cloud Security Can Help with Ransomware
Organizations must update their ransomware protection at the same pace that as the attackers changes their tactics. The ransomware scourge continues, with incidents hitting a U.S. record in the second quarter of 2021, as attackers expand into vertical industries and target critical infrastructure. Ransom demands have also been growing. According to IT Governance, the average decryption key rate from attackers is $140,000 yet many organizations end up paying much more than that.
Efforts to Secure OSS fired up after Log4Shell
Who would have thought software could rattle the White House? But a vulnerability in Log4J, a popular open source software project, exposed critical digital infrastructure to remote code execution attacks. This prompted the US Government to engage big tech, infosec professionals, and open source organizations to come together to help secure open source software.
DevOps Horror Stories: Repository of Horror
Just when you thought it was safe to go back in the water... Is there anything more frightening than the unknown? Anything the mind can conjure up is frequently scarier than something realized. The shark in Jaws is terrifying because you don’t see it until it’s too late. It’s a silent, relentless death machine, hiding in the water. A software vulnerability is the unknown, hidden deep within an ocean of code, packages and container dependencies.
RapidSpike - Who are we?
Elastic Announces New Capabilities to Help Customers Solve Their Biggest Business Challenges
Millions of IoT devices and routers could have a mega security flaw
An unpatched vulnerability in a popular C standard library found in a wide range of IoT products and routers could put millions of devices at risk of attack. The vulnerability, tracked as CVE-2022-05-02 and discovered by Nozomi Networks, is present in the domain name system (DNS) component of the library uClibc and its uClibc-ng fork from the OpenWRT team.
Getting Better Sysmon Data Using Cribl Stream
System Monitor, better known as Sysmon, is one of my favorite security datasets. The data is crazy detailed and offers a great way to power security detection and response since it gives cyber security teams a roadmap to understand exactly what systems or people are doing while they use any Windows operating systems. The avalanche of the data is the downside and why observability engineers need tools like Cribl Stream to manage and enrich Sysmon data to make it more useful and more cost-effective.
ElasticON Solution Series Keynote: Celebrating 10 Years of Elastic
7 Important Things to Include in Your Company Security Policy
What Is DevSecOps? How Great Developers Shift Left for Security
In the alphabet soup of IT buzzwords, DevSecOps is one of the more confusing abbreviations. More than just a trendy buzzword, DevSecOps is the mature organization’s next evolution in comprehensive development processes.
NinjaOne Partnership with SaaS Alerts Provides Enhanced Security
Managed Service Providers (MSPs) are charged with protecting their customers from all of the threat vectors that target devices, networks, and applications. The diligence required to provide this level of protection for customers is unending. However, if an MSP is going to properly secure their customers’ environments, they first must secure their own, which is why NinjaOne has collaborated with the cybersecurity company SaaS Alerts to better protect MSPs from RMM supply chain attacks.
Compliance And The Cloud
Looming 2022 (and Beyond) Network Security Threats
Every year hackers grow in numbers, aggressiveness, organization, and sophistication. And every year there are new attack types and new areas of IT infrastructure that cybercriminals target. 2022 is no different. We are about a third of the way in already and IT pros and security specialists already have their hands full with new attacks and new issues.
5 Ways To Prevent Unauthorized Access to Your Company Data
N-able Introduces Cove Data Protection
Phishing and Identity Fraud Protection for Remote Teams
Protect the Business with Cribl Packs: Webinar Recap
The second in our Feature Highlights webinar series, Protect the Business with Cribl Packs, highlights Packs and security use cases. Packs enable you to share complex Stream/Edge configurations across multiple Worker Groups/Fleets, between Stream/Edge deployments or with the Cribl Community. Packs roll up best practices to ensure Site Reliability Engineering (SRE) teams have the required data to protect the business.
Open Source Hacktivism, Open Source Gains Traction in the Enterprise, and More: Open Source Matters
SIEM: Introduction to SIEM and 4 Top SIEM Tools
Security Information and Event Management (SIEM) technology has become a fundamental part of identifying and guarding against cyber attacks. It is one of the essential technologies powering the modern security operations center (SOC). SIEM is an umbrella term that includes multiple technologies, including log management, security log aggregation, event management, event correlation, behavioral analytics, and security automation.
Secure K3s Cluster Hosts with AppArmor
Best Enterprise Password Managers According to IT Specialists
What Is CSPM? A Closer Look at Cloud Security Posture Management
As we previously discussed in the Automating Your Cloud Security Posture Management (CSPM) Response blog post, CSPM is a vital component in any environment leveraging cloud services. Whether you are using a single cloud or are in a multi-cloud scenario, the complexity of these cloud platforms is constantly expanding. Staying on top of new changes in policies and functionality to ensure that you are maintaining a secure environment is daunting - and almost impossible to do without automation. No one has the resources to spend on maintaining a large team of cloud specialists who just audit everything that is in use.
How CISOs Can Guard Against Evolving Physical and Digital Corporate Security Threats
A rise in both physical and digital security threats is placing greater pressure on CISOs and other security professionals to prepare for and mitigate evolving security threats of all kinds. To protect organizations and their people, security teams need to be able to visualize threats, respond quickly and communicate effectively.
Inbox Monitoring & Phishing Remediation - Intro to Torq Webinar
Confidential Computing and financial services cloud
Cloud computing has been transforming financial IT infrastructure into a utility allowing financial institutions (FIs) to access computing resources on-demand letting FIs offload costs and effort of setting-up and managing their own on-premises infrastructure, improving agility and time to business value. As more and more financial institutions rely on hybrid cloud services, data security in the cloud is a business imperative.