Operations | Monitoring | ITSM | DevOps | Cloud
November 2022
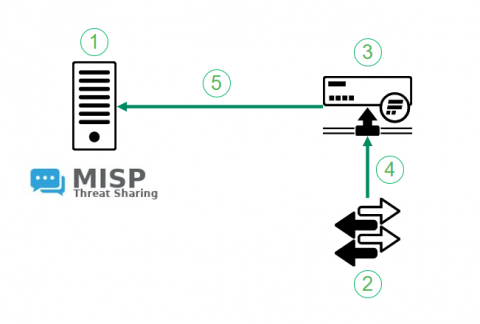
Flowmon Anomaly Detection & MISP
Back in 2021 we have introduced the integration between MISP, a community threat intelligence sharing platform and Flowmon ADS. The integration turns indicators of compromise shared through MISP to actionable intelligence. Flowmon ADS will automatically pick up on latest indicators of compromise using MISP API and leverage those indicators of compromise to detect adversary activities in the target network. The integration is available in Flowmon ADS 11.2 and newer versions.
When Stream Meets Lake: Cribl Integrates With New Amazon Security Lake to Help Customers Address Data Interoperability
We’re excited to announce that Cribl integrates with Amazon Security Lake. Amazon Security Lake allows customers to build a security data lake from integrated cloud and on-premises data sources as well as from their private applications using the Open Cybersecurity Schema Framework (OSCF).
4 Most Common Website Security Threats (2023) + Solutions
For infrastructure administrators tasked with ensuring the reliable operation of their applications, the thought of a lurking cyberattack can be one to lose sleep over. An attack on your system and the services you provide could render your applications unresponsive, resulting in a security breach, or loss of data.
Why unmanaged Apple devices make your customers vulnerable
Let’s start with a simple but harsh fact: If you say you’re protecting your customers’ networks and you’re not managing their Apple devices, then you’re lying to them and yourself! Over the years hackers have targeted everything from HVAC machines (Target) to fish tank thermometers (an unnamed Las Vegas casino) and a whole host of devices in between in order to prise their way into company networks. Let’s stop for a minute to consider that fact.
Cybercrime Trends and the Economy
Sunrex Technology Removes Network Security Bottlenecks in Information Security with Progress Flowmon
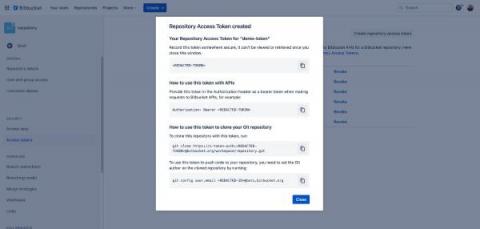
Access Bitbucket Cloud repositories more securely with resource-scoped access tokens.
Open source and cybersecurity: from prevention to recovery
So you have just installed the latest antivirus and turned on your shiny new firewall. Now your organisation is fully secure, right? The reality is that all the security products in the world will never be able to fully protect your data centre or your business from security threats. Because of the asymmetry between attackers and enterprises, cybersecurity is a problem that can never be solved and is never going away.
Using Calico to create a Kubernetes cluster mesh for multi-cluster environments
Kubernetes has come of age with more organizations adopting a microservices architecture at scale. But scale brings a whole slew of new challenges, especially with Kubernetes, which is designed to operate as a single cluster. However, the usage of Kubernetes, especially at leading-edge organizations operating at scale, has crossed the single-cluster threshold.
CFEngine: The agent is in 19 - Sneak peek of CFEngine 3.21
Dealing with Privacy and Security Issues in a Hybrid Workplace, Especially a BYOD Environment
The Challenges & Solutions for a Hybrid Workplace Bring Your Own Device (BYOD) is quickly becoming the new standard in hybrid workplace technology. BYOD programs allow employees to use their personal devices for work and get appropriately reimbursed. This is a great cost control option, providing more efficiency because of flexibility and convenience – particularly for companies looking for scalability.
5 Web Security Tips For Small Businesses
Torq Announces Advisory Board Featuring Global Cybersecurity Visionaries
Torq is extremely proud to announce the formation of the Torq Advisory Board, a group of some of the world’s most respected cybersecurity professionals, including several industry-leading CISOs and heads of information security. All of our advisors have made major impacts in cybersecurity for their companies, and for the industry at large.
Torq's No-Code Security Automation Solution Now Available in AWS Marketplace
Torq is proud to announce the immediate general availability of its no-code security solution in AWS Marketplace, the curated digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on Amazon Web Services (AWS).
3 ways IT can secure open source software
Critics of open source software have long argued that giving everyone access to a project’s source code creates security issues. But in active projects with highly engaged communities, the opposite is actually true: Open source software helps organizations become more secure. That said, any piece of technology can be exploited.
Shorten Recovery from Cyberattack with Cove's Standby Image
Mezmo Is Now ISO 27001 Certified
We’re proud to announce that we have received ISO 27001 certification. This certification is another significant milestone for Mezmo this year.
Recovering Your Business From A Cybersecurity Breach
How Federal Buildings Are Converging Their Cyber And Physical Technologies For Futureproof Security
Understanding Kubernetes Limits and Requests
When working with containers in Kubernetes, it’s important to know what are the resources involved and how they are needed. Some processes will require more CPU or memory than others. Some are critical and should never be starved. Kubernetes defines Limits as the maximum amount of a resource to be used by a container. Requests, on the other hand, are the minimum guaranteed amount of a resource that is reserved for a container.
How Automation Playbooks Double Down on the Value of SOARs
So you’ve set up a Security Orchestration, Automation and Response (SOAR) platform. You’re now ready to detect, respond to and remediate whichever threats cyberspace throws at you, right? Well, not necessarily. In order to deliver their maximum value, SOAR tools should be combined with playbooks, which can be used to drive SOAR systems and ensure that SOARs remediate threats as quickly as possible — in some cases, without even waiting on humans to respond.
How to Monitor Kubernetes API Server
Content Learning how to monitor the Kubernetes API server is crucial when running cloud-native applications in Kubernetes environments. The Kubernetes API server can be considered as the front end of the Kubernetes control plane. Any interaction or request from users or internal Kubernetes components with the control plane go through this component. Ensuring you monitor the Kubernetes API server properly is of vital importance to ensure your Kubernetes cluster works as expected.
Why Cloud-First Data Protection is the best option for DPaaS
The MSP industry is facing and ongoing movement across customers’ transition to the cloud, the evolving threat landscape, and a skills shortage that seems to be more pronounced than ever. Consider these facts from Gartner: The threat landscape is also evolving as highlighted by some of the following statistics: Data protection is a service that managed service providers (MSPs) need to consider as critical.
7 Most Powerful Cybersecurity Software Tools in 2022
When looking for cybersecurity software tools in 2022, it is important to know your needs and how the software can protect you against cyberattacks. In an era when people are increasingly reliant on machines, software, computers, and networks, it is important to have solid protection and make sure that your critical data is safe across every device. Today’s blog is meant just for that – to help you see and choose the ideal cybersecurity software solution.
How Linux Benefits Businesses
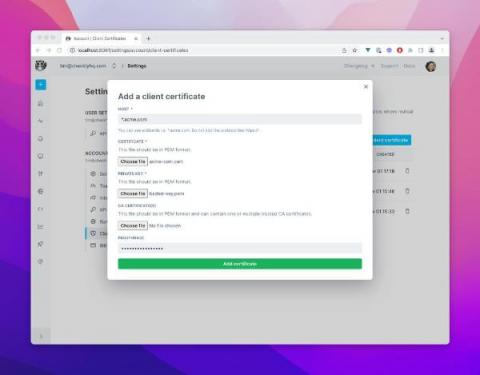
Authenticating Icinga 2 API Users with TLS Client Certificates
When interacting with the Icinga 2 API, the client is commonly authenticated using a password provided via HTTP basic auth. Icinga 2 also support a second authentication mechanism: TLS client certificates. This is a feature of TLS that also allows the client to send a certificate, just like the server does, allowing the server to authenticate the client as well.
Being Secure When Moving to the Cloud - N-able Chief Security Officer David MacKinnon - Empower 2022
Log4Shell and Log4j - Where it all went Wrong?
On 10th December 2021, Apache foundation admitted the Log4Shell vulnerability of its Log4j 2.16 version. Chen Zhao Jun was an Alibaba cloud services security analyst who first found out about this security threat and consequently reported it to the foundation. Upon further investigation, they identified that the vulnerability had existed since 2013. Unfortunately, by then all the corporations, big and small were affected by this malicious security breach.
Torq Joins the Cloud Security Alliance
We’re extremely happy to announce that Torq has joined the Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. The CSA has more than 80,000 members worldwide and has been endorsed by the American Presidential Administration, which selected the CSA Summit as the venue for announcing the federal government’s cloud computing strategy.
5 Tips For Consumers To Shop Safely This Black Friday
While it makes for bleak reading, the frenzy of sales and online shopping activity surrounding Black Friday, means this pre-holiday season is a key period for cybercriminals. And each year we see an increase in cyberattacks during what should be a feel-good time. The picture is all-the-more worrying in 2022, as this Black Friday weekend (25th-28th November) falls on the same date as the USA vs England World Cup game – a highly- anticipated day of betting for bookmakers.
CFEngine Build System version 3
Our beloved cfbs CLI tool for working with CFEngine Build is rapidly evolving. At the time of writing, we are currently at version 3.2.1. Thus I would like to take this opportunity to talk a bit about the latest and greatest features; including support for users to manipulate input parameters in modules, as well as a couple of new build steps.
What Is the Purpose of Data Room Due Diligence
CFEngine 3.15.7 and 3.18.3 released
We are pleased to announce two new patch releases for CFEngine, version 3.15.7 and 3.18.3! These releases mainly contain bug fixes and dependency updates.
An Introduction to SOC Automation
The Security Operations Center, or SOC, is the backbone of modern security operations. By centralizing security monitoring, detection, and response, SOCs help organizations manage security risks more efficiently and effectively. But simply setting up a SOC doesn’t guarantee optimal security workflows. To get the very most from your SOC, you must automate its operations as much as possible.
OAuth Authentication - xMatters Support
5 Important Operations Issues to Consider When Working With an International Team
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Jason Chan on How Automation Transformed Netflix's Cybersecurity Posture
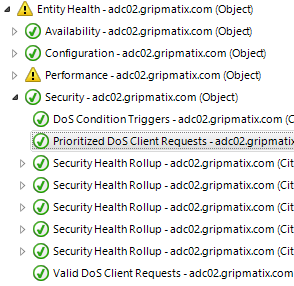
Citrix NetScaler Denial-of-Service (DoS) JavaScript Triggers
Are you aware when Denial-of-Service (DoS) JavaScript triggers occur on your Citrix NetScaler devices to block DoS attacks? Do you know when exceptions are made based on 'valid' DoS cookies? MetrixInsight for NetScaler monitors for these occurrences and alarms you whenever this happens (too often).
Effective vulnerability management for your microservices
Do VPNs Really Keep Your Browsing Data Private?
Cloud Security: Indiana Bob's Server Closet Versus Data Centers | Security Insights Podcast, Episode 28
Amanda and Chris share stories proving why your data really is more secure in the cloud than the average on-premises server closet – and what organizations should worry more about when it comes to data security.
Secure Backup Strategies for 2022
Hard drive crash. Ransomware. Equipment failure. Accidental deletion. Theft. There are plenty of reasons why end users want to have a secure and up-to-date backup of their most important files. And there are just as many approaches to backup and recovery as there are reasons to want it in place. In this article, we’ll discuss practical strategies and best practices for backing up important data, including consumer-level options and how to get the most from an enterprise-grade backup solution.
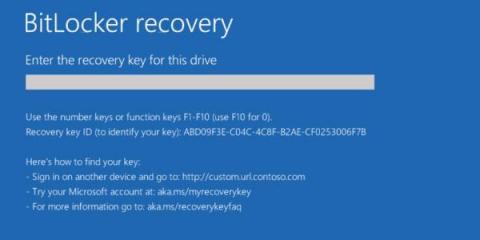
3-Step Approach to Eliminate the BitLocker Recovery Key Backup Issue using Nexthink
In today’s era of “Work from anywhere”, Data Security & Data Encryption has become a vital security step for organisations world-wide and a key component for security compliance. BitLocker is one of the popular Software Stacks for enforcing encryption on all devices & drives. Exponential complexity for managing the encryption compliance and the backup of the recovery keys for all devices in the organization has increasingly become a key challenge for EUC Professionals.
Trending topics at KubeCon + CNC NA 2022
Throughout KubeCon + CloudNativeCon NA 2022, our team was able to speak to over 100 people from the cloud-native community to learn more about their thoughts and experience of the event. This blog will explore what the community thought was the hot topic of discussion at KubeCon + CNC NA 2022, which includes topics such as security, cost, and developer experience. Check out the full video below.
Cribl is Redefining Search for Your Observability & Security Data
Cribl, a leader in open observability, today released Cribl Search, the first federated query engine focused on observability and security data. Search flips the observability market on its head, dispatching queries to where the data is already at rest. Cribl Search was engineered to let you search data-in-place, whether the data remains at the edge, in the stream, in the observability lake, at the endpoint, or even in existing search tools.
Using Client Certificates for mTLS and Zero Trust Networks
You can now use Checkly to monitor API endpoints secured with TLS Client Certificates. This post dives into why and how you would use client certificates and mTLS (Mutual TLS) in your API infrastructure. Let's go!
Jason Chan on How Automation Transformed Netflix's Cybersecurity Posture
Jason Chan, a key member of the Torq Advisory Board, has spent more than 20 years working in pivotal cybersecurity roles. One of his most important positions was leading the information security organization at the video streaming behemoth Netflix for more than a decade. His Netflix team set the bar extraordinarily high, focusing on sophisticated risk assessment and management, and compliance management strategies and approaches.
The most dangerous computer viruses in history
Here, in our beloved Pandora FMS blog, we have talked a big deal about computer risks. This does not mean of course that we consider ourselves to be faint-hearted or timid, but rather cautious heroes. And in order not to be alone in a battle against the evil that lurks around, today, continuing with this theme of terror and digital desolation, we bring you: some of the most dangerous computer viruses in human history!
Protecting Your VoIP Infrastructure From DDoS Attacks
Distributed denial of service (DDoS) attacks are an ongoing issue for communications service providers, putting critical systems at risk, undercutting service level agreements, and bringing unwanted headlines. In the first half of 2022 6 million of these attacks were reported. Some metrics of DDoS attacks in 1H2022 compared to 2H2021.
Changing Perspectives: A Deep Dive into the Security Posture of 600+ Real-World AWS Environments
How to Build an Automation Strategy and Roadmap
“If you fail to plan, you plan to fail,” said Benjamin Franklin. These words cannot be overstated in most business fields, especially when it comes to automation. Process automation has the potential to enhance operations in most organizations, but problems can emerge when they don’t plan and strategize around their automation objectives.
When to Automate and When Not to Automate
Everyone loves automation, and it can be easy to assume that the more you automate, the better. Indeed, falling short of achieving fully autonomous processes can feel like a defeat. If you don't automate completely, you're the one falling behind, right? Well, not exactly. Although automation is, in general, a good thing, there is such a thing as too much automation. And blindly striving to automate everything under the sun is not necessarily the best strategy. Instead, you should be strategic about what you do and don't automate.
Endpoint Security Management Definition & Examples
From harmful malware attacks to data breaches, there are many problems that will arise if you don’t manage your endpoints. As a matter of fact, a report on endpoint security by Expert Insights states, “68% of organizations have experienced one or more endpoint attacks that successfully compromised data and/or their IT infrastructure.” Protect your organization from threats by learning more about and implementing endpoint security management.
Ivanti Neurons for UEM
Modern Canadian MSSP drives next-gen MDR with Logz.io and Tines
Today’s Managed Security Service Providers (MSSPs) are trying to grow their business quickly, improving margins and onboarding customers with high-quality tool sets that scale with the business. This means reducing cost, improving onboarding time and building the next generation of Managed Detection and Response (MDR) to deal with threats that are increasing in volume and sophistication.
5 API Security Best Practices to Protect Sensitive Data
API is short for Application Programming Interface. The software-to-software interface provides a secure and standardized way for systems to work with each other. API security means implementing practices that protect APIs from malicious attacks and data theft. Thanks to APIs, applications can deliver the information or functionality requested without user intervention. This means our everyday digital experiences remain virtually effortless.
MSPs are the epicenter of supply chain threats
Gain visibility into manufacturing OT assets to reduce cyber risk
As manufacturing operational technology (OT) ecosystems grow more connected and complex, they become vulnerable to cyberattacks. In fact, the manufacturing sector was the most attacked industry in the world in 2021, according to IBM’s X-Force Threat Intelligence Index 2022. Manufacturing surpassed finance and insurance in the number of cyberattacks for the first time in five years. A large part of the industry’s vulnerability is due to a lack of visibility.
CEO explains how Cove Data Protection exceeded his expectations
Interlink Software Achieves Cyber Essentials Certification
Cyber Essentials is a UK government backed scheme, developed by the National Cyber Security Centre. Since its inception the scheme has become the benchmark for IT security, helping organizations to deploy technical controls to guard against the common types of cyber-attacks and improve data security.
Getting started with EKS and Calico
Cloud-native applications offer a lot of flexibility and scalability, but to leverage these advantages, we must create and deploy a suitable environment that will enable cloud-native applications to work their magic. Managed services, self-managed services, and bare metal are three primary categories of Kubernetes deployment in a cloud environment.