Operations | Monitoring | ITSM | DevOps | Cloud
May 2023
Why Your Observability Strategy Needs Security Observability
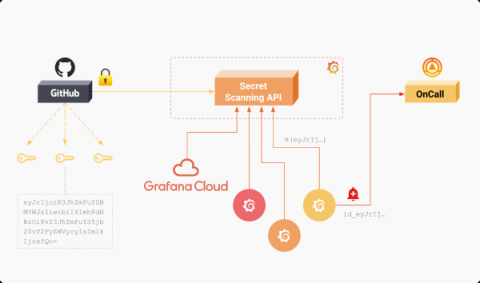
Grafana Labs partners with GitHub to enable secret scanning
As part of our ongoing commitment to security, we are excited to announce we have partnered with GitHub to protect our users on public repositories via GitHub’s secret-scanning feature. Through the partnership, GitHub will notify Grafana Labs when one of the following secret types is exposed in the code of a public repository: GitHub actively monitors public repositories for leaked secrets. When a secret is detected, its hash is stored in Grafana Labs’ Secret Scanning API.
Managing the Cyber Threat Landscape in Today's Cloud Environments
What is so Pro in Ubuntu Pro?
What is Palo Alto Panorama?
Amazon Security Lake & ChaosSearch deliver security analytics with industry-leading cost & unlimited retention
Kubernetes Security: Secrets from the Trenches
Kubernetes is a popular open-source container orchestration platform. It is highly configurable and feature-rich, but it also requires a deep understanding of containerization. When you are running Kubernetes in production, you need to account for cluster monitoring and logging, governance, and security. In this article, you will learn about Kubernetes security, including pro tips to help you handle architecture concerns, dependencies, and container vulnerabilities.
The new ransomware-as-a-service (RaaS) operation MichaelKors
CFEngine: The agent is in 25 - Migrating traditionally managed policy to cfbs
The Dark Side of DevSecOps and the case for Governance Engineering
For today’s software organizations security has never been more top of mind. On one side there is the present and growing threat of being hacked by malicious actors, set out in Crowdstrike’s recent Global threat report. And, on the other, there is a wave of cybersecurity regulation from the government to mitigate such cybersecurity vulnerabilities.
The Swedbank Outage shows that Change Controls don't work
This week I’ve been reading through the recent judgment from the Swedish FSA on the Swedbank outage. If you’re unfamiliar with this story, Swedbank had a major outage in April 2022 that was caused by an unapproved change to their IT systems. It temporarily left nearly a million customers with incorrect balances, many of whom were unable to meet payments.
SIEM Tools: For Enhanced Threat Intelligence and System Security
SIEM is an overarching mechanism combining Security Event Management (SEM) and Security Information Management (SIM). It is a combination of different tools such as Event Logs, Security Event Logs, Event Correlation, SIM etc. These work in tandem to provide you an up-to-date threat intelligence infrastructure and enhanced security for your applications and hardware.
Agent and agentless: An ongoing battle
Observability of an SAP environment is critical. Whether you have a large complex and hybrid environment or a small set of simply architected systems, the importance of these systems is probably crucial to your business. Just thinking about system outages keeps us up at night, let alone the pressure of system performance, cross system communication and proper backend processing.
How to Conduct a Workplace Risk Assessment
How to secure your MLOps tooling?
Generative AI projects like ChatGPT have motivated enterprises to rethink their AI strategy and make it a priority. In a report published by PwC, 72% of respondents said they were confident in the ROI of artificial intelligence. More than half of respondents also state that their AI projects are compliant with applicable regulations (57%) and protect systems from cyber attacks, threats or manipulations (55%). Production-grade AI initiatives are not an easy task.
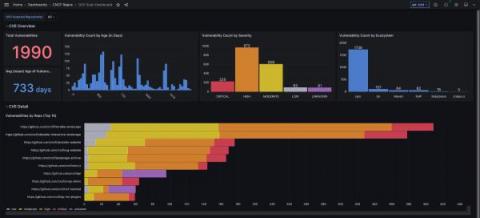
How to manage CVE security vulnerabilities with Grafana, MergeStat, and OSV-Scanner
Patrick DeVivo is a software engineer and founder of MergeStat, an open source project that makes it possible to query the contents, history, and metadata of source code with SQL. The security posture of software supply chains has been a significant topic lately. Recent high-profile breaches have shown the importance of managing risks from third party code. Take, for example, the Log4Shell vulnerability (tracked as CVE-2021-44228 — Grafana Labs was not affected).
Revisit - the Balancing Act of Staying Secure While Working From Home: Ep. 11
The Ultimate Guide to Automating and Mobilizing Your Secops Processes with Derdack SIGNL4 and Microsoft Sentinel
The threat and security landscape is becoming increasingly cluttered. As incidents increase, so do alerts and notifications, leading to too many alerts and too few hours to address them. Many businesses work remote and with the ever-present smartphones, we are always on the go. Yet it is essential that security teams receive and prioritize meaningful threats, but that task is easier said than done.
Achieving High Availability (HA) Redis Kubernetes clusters with Calico Clustermesh in Microsoft AKS
According to the recent Datadog report on real world container usage, Redis is among the top 5 technologies used in containerized workloads running on Kubernetes. Redis database is deployed across multi-region clusters to be Highly Available(HA) to a microservices application.
The Ripple Effect of Meta's $1.3 Billion GDPR Fine for Businesses That Handle Data
Meta, the parent company of Facebook, has been fined a record €1.2 billion ($1.3 billion) by the European Union for violating its data privacy laws. The fine was issued by Ireland’s Data Protection Commission, which is Meta’s lead regulator in the EU, and is the largest ever levied under the EU’s General Data Protection Regulation (GDPR), which went into effect in 2018.
A comprehensive review of the best vulnerability scanning tools
A guide to static application security testing (SAST)
Static application security testing (SAST) involves analyzing source code to identify and address potential security vulnerabilities. Using SAST early in development identifies threats before they can affect a live environment. SAST is particularly important for continuous integration and continuous deployment (CI/CD) pipelines. These pipelines automate the integration of new code changes into the main codebase and deploy applications to production environments.
The Importance of Compliance for Small and Medium-Size Businesses: What You Need to Know
Navigating compliance requirements can be complex because there are so many of them, and there is a good chance that at least one set of standards applies to you. Standards can be for specific sectors, like The Health Insurance Portability and Accountability Act (HIPAA) for healthcare, or may apply more generally to organizations across industries, like the General Data Protection Regulation (GDPR).
The Role of Technology in Detecting and Preventing Business Fraud
N-able Collaborates with JCDC to Help Create a More Secure Global MSP Ecosystem
Why an incident response plan is a security must-have for every organization
“By failing to prepare, you are preparing to fail. Preparation prior to a breach is critical to reducing recovery time and costs.” (RSAConference) For 83% of companies, a cyber incident is just a matter of time (IBM). And when it does happen, it will cost the organization millions, coming in at a global average of $4.35 million per breach. The damage isn’t only financial, nor solely related to customer loyalty and brand equity.
How to adopt distributed tracing without compromising data privacy
The age-old dilemma of privacy and security vs. productivity pops up for developers every time they consider introducing a new technology to their stack. The dilemma is often viewed as a trade off: on one hand, privacy and security measures can slow down how quickly new features can be rolled out; on the other hand, prioritizing productivity and business enablement over privacy and security can increase the risk of breaches to an organization.
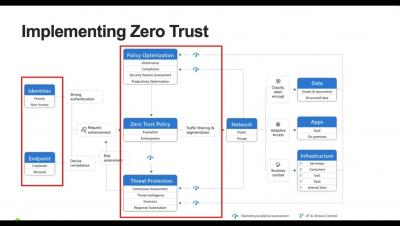
GDIT + D2iQ Reveal the Formula for Achieving Zero Trust
Join us for a must-see webinar in which Kubernetes and DevSecOps experts from D2iQ and General Dynamics International Corporation (GDIT) share their insights on how to achieve zero trust security within a Kubernetes environment as part of government modernization. GDIT is among the major system integrators that have chosen D2iQ as the Kubernetes management platform on which they are creating highly secure Kubernetes solutions for their government clients.
Can Network Monitoring Identify Security Threats? Here's What to Know
By continuously monitoring network activity and assets, network monitoring plays a key role in identifying cybersecurity threats. The network monitoring process gathers important data that can be used in analytics or in conjunction with cybersecurity applications to rapidly identify and respond to threats.
SSL/TLS Explained in 7 Minutes
How to Use Ansible Copy Module: An In-Depth Guide
In this post, we’re going to learn about the Ansible copy module. Before we look at the copy module specifically, let us first remind ourselves what Ansible is. You can install this open-source software on just one Linux machine. Then it can perform a lot of tasks on connected Linux machines without requiring Ansible installation on them. You can do tasks like copying files, fetching files, and a lot of other things all on connected machines, with a single command.
Authentication Failures: Definition, Consequences, and Prevention
Authentication is the security process that verifies a user’s identity in order to grant access to their online account. It also functions as the gateway to your product. It’s a workflow you can’t compromise on without risking negative impacts on your users and your company. Fortunately, there are lots of authentication services that can do the heavy lifting for you. It’s important to understand what you can do in case of an authentication failure, when to do it, and why.
Supply Chain Levels for Software Artifacts (SLSA)
Optimizing IT Infrastructure: Unleashing the Benefits of IT Consulting Services
Investing in the Era of Technology: Adapting to a Changing Landscape
Navigating Privacy Boundaries: 6 Ethical Considerations of Session Replay Software
Improving security: Aiven and GitHub's secret scanning partnership
Goats on the Road: RSA 2023 Recap
Dr. Anton Chuvakin, a noted warrior/poet/security cybersecurity expert, sums up my thoughts about RSAC 2023 marketing messaging perfectly with this post on Twitter. For those who are new to the vendor hall, the amount of just bad marketing can be overwhelming and confusing. . There’s only one chance to get your message across to your prospects, so make it short and sweet. Anton’s guess of “zero click zero trust” is closer than you think to the truth.
Securing the Enterprise from VoIP Network Attacks with Analytics
Voice over IP (VoIP) technologies and solutions have been widely adopted by consumers, businesses and service providers since the mid-2000s, but the rising popularity of remote work means businesses of all sizes are even more rapidly turning to VoIP for voice calls.
JCDC Collaboration Shows Security is a Team Sport for MSP Industry
Back in January, the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory notice specifically talking about RMM providers being targeted by cybercriminals. We’ve known that as a group we’ve been a target for a few years, with the bad guys continuing to look at the RMM solution providers as a route into small businesses, because there are still dollars to be made there.
Establishing Zero Trust out of the box at Enterprise scale
Less is more: industry leaders share their success with tool consolidation for maximized productivity
Ace your way through painless audits with Kosli's Evidence Vault
Preparing for a software audit can be a time-consuming and painful process where a lot of information needs to be gathered and verified in a provable audit trail. It means tracking down and piecing together evidence for pull requests, test reports, security scans, deployment logs, and more. This information is usually scattered across tools which are typically unsecured and unmanaged, so it can be easily deleted and/or modified.
Best practices to protect your business online
Why Addressing IT Challenges is Crucial for Business Sustainability and Growth
iPhone Security Settings to Protect Your Online Privacy
Understanding AI security for your organization
While organizations are quickly adopting AI to automate tasks and improve operations, it’s important to consider the security risks associated with integrating AI into your company’s processes and software. AI not only brings an opportunity to increase efficiency but also introduces additional risks to your organization if not used responsibly — just like a recent example from Samsung has shown.
RapidSpike Wallboards
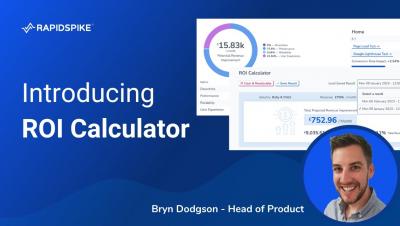
Introducing RapidSpike ROI Calculator
Command Injection: A Guide to Types, Risks, and Prevention
Command injection is a kind of cyber attack that allows an attacker to execute arbitrary commands on a system. Attackers accomplish this by exploiting vulnerabilities in an application’s input validation process.
Reduce Risk with Production Traffic Replication
Comprehensive Guide to Azure Storage Shared Access Signatures
Azure Storage is a cloud-based storage solution offered by Microsoft as part of the Azure suite of services. It is used for storing data objects such as blobs, files, tables, and queues. Azure Storage offers high scalability and availability with an accessible pay-as-you-go model that makes it an ideal choice for businesses of all sizes. In today’s digital age, data has become the most valuable asset for any business.
Tigera named as one of Forbes America's Best Startup Employers in 2023
We are proud to announce that we have been named one of America’s Best Startup Employers 2023 by Forbes! The Forbes list of America’s Best Startup Employers 2023 was compiled by evaluating 2,600 companies with at least 50 employees in the United States. All of the companies considered were founded between 2013 and 2020, from the ground up, and were not spin-offs of existing businesses. Just like other Forbes lists, businesses cannot pay to be considered.
What is SOC Compliance? Basic Overview for Businesses
IBM reports that the global average total cost of a data breach in 2022 was $4.35 million. Data breaches are rising each year, with an ever-increasing cost, so it’s absolutely essential to be prepared and proactive in your data protection strategy. When clients provide personal or business data to an MSP, they expect the provider to have proper policies and procedures in place to protect that data.
N-able Announces Cove Data Protection with Disaster Recovery as a Service, Introducing Microsoft Azure Recovery Option
The Importance of HIPAA Compliance in Business App Development
What is the difference between SSL vs. TLS? Which Gives Your Website the Best Protection?
One of the most important considerations if you're seeking maximum security for your website is using encryption protocols. You have two choices: SSL (secure sockets layer) and TLS (transport layer security). These commonly used protocols encrypt internet communications and protect sensitive website data from malicious attacks. Let's cover the key differences between SSL and TLS and point you in the right direction for choosing the best protocol for your website.
Simplifying Network Security: How AI is Changing the Game
As companies come to rely on digital systems in everything they do, network security has become more important than ever. Unfortunately, with that digital transformation comes complex networks to support it, and thus complex network security.
If You're Always Delivering Valuable Packages To Customers, This Is How To Secure Your Business
Introducing RapidSpike Wallboards
You can find out more about our Custom Dashboards here: https://www.rapidspike.com/kb/custom-dashboards/
Industry Experts Discuss Cybersecurity Trends and a New Fund to Shape the Future
In this live stream discussion, angel investor Ross Haleliuk joins Cribl’s Ed Bailey to make a big announcement about his new fund to shape the future of the cybersecurity industry. Ross is a big believer in focusing on the security practitioner to provide practical solutions to common issues by making early investments in companies that will promote these values.
Role-based credential management with OIDC
In our article on managing static credentials, we discussed the necessity of secrets — the passwords, tokens, and API keys that connect digital services together — and the importance of keeping them secure so that your infrastructure and data are kept safe from intrusion and misuse. For organizations delivering software at scale, managing credentials across multiple teams and projects can quickly become tedious and error-prone, creating bottlenecks and unnecessary risk.
Endpoint Monitoring Explained with Example
Today, people and businesses use endpoints to accomplish everything from day-to-day tasks to large projects. Endpoints include the physical devices that connect to and communicate with a central network. They are used to manipulate data or exchange information. The number of endpoint devices that average businesses and enterprises manage is 135,000, and that number continues to grow.
ISO 27001 and Asset Management: What Does Annex A.8.1 Say?
Cloud Transformation Strategy & Solutions
Cloud transformation is real. And it's spectacular. According to global business management and consulting firm McKinsey & Co., cloud transformation is the engine driving $1 trillion in economic activity for Fortune 500 companies alone. Innovations enabled by the cloud touch nearly every aspect of running a successful business, including the development of new products and services, access to new customers and markets, frictionless transactions, streamlined communication and collaboration, and access to talent without concern for traditional geographic barriers.
How Password Managers Help Meet Cybersecurity Requirements
The first Thursday in May is World Password Day. This is a good opportunity to look at your cybersecurity practices and privileged access strategies. As cyberattacks increase, more organizations are choosing to get some peace of mind by acquiring cyber insurance to mitigate liability and losses in case of an attack. However, getting cyber insurance may not be an easy exercise.
Introducing the Grafana Labs Bug Bounty Program
At Grafana Labs, we value the open source community and recognize the power of crowdsourcing. This is why we have decided to launch our very own bug bounty program, managed in-house by our own team, to encourage ethical hackers from around the world to help us find and responsibly report security vulnerabilities in Grafana Labs software.
Monitoring Kubernetes clusters activity with Azure Managed Grafana and Calico
Cloud computing revolutionized how a business can establish its digital presence. Nowadays, by leveraging cloud features such as scalability, elasticity, and convenience, businesses can deploy, grow, or test an environment in every corner of the world without worrying about building the required infrastructure.
SIEM Optimizations with Cribl Stream
This Month in Datadog: DASH 2023, In-App WAF and User Protection, Cloudcraft for Azure, and more!
Strengthen Your Security Strategy to Safeguard Against Migrations Risks
In part 1 of this post, we talked about how Cribl is empowering security functions by giving our customers freedom of choice and control over their data. This post focuses on their experiences and the benefits they are getting from our suite of products. In a past life, I was in charge of security and operational logging at Transunion — around 2015, things started going crazy.
Applying Zero Trust to Data Centre Networks
Big data security foundations in five steps
We’ve all read the headlines about spectacular data breaches and other security incidents, and the impact that they have had on the victim organisations. From LastPass to SolarWinds, “data security” seems to be the phrase on the lips of every CTO these days. And in some ways there’s no place more vulnerable to attack than a big data environment like a data lake.
RCA Series: Accelerate security investigations w/ machine learning and Elastic (3/4)
Unpacking the Hype: Navigating the Complexities of Advanced Data Analytics in Cybersecurity
POS Security: How to Protect Your Android POS Systems
The adoption of POS devices across industries is advancing, fast! Businesses including restaurants, grocers, and retail stores are seeing POS devices as a multi-functional hub that offers menu creation, tableside ordering, employee management, CRM, inventory management, and more. According to statistics, 59% of retailers made focusing on omnichannel capabilities their top POS priority in 2020.
Avantra SAP security FAQ
We understand the importance of security when it comes to your SAP system(s) within your organization. As cyber attacks continue to become more successful, it is essential to have a process in place. Below are several frequently asked questions regarding security to provide some insight on our approach and how Avantra can help you navigate through this journey.
Empowering Security Teams: The Importance of Data Control and Freedom of Choice
Enterprises are getting increasingly tired of feeling locked into vendors, and rightfully so. As soon as you put your observability data into a SaaS vendors’ storage, it’s now their data, and it’s difficult to get it out or reuse it for other purposes. As a result, strategic independence is becoming increasingly important as organizations decide what data management tools they’re going to invest time and resources into.
Docker Secrets: An Introductory Guide with Examples
Securing sensitive data is crucial for any application, but managing this data can be complex and error-prone. Docker secrets provide a reliable and secure way to handle sensitive information like passwords, API keys, and certificates in your Docker environment. In this introductory guide, we’ll explore what Docker secrets are, how to use them with practical examples, and share some best practices to help you safeguard your sensitive data effectively.
What Is Broken-Access Control? Examples and Prevention
Access control is a security mechanism that regulates who has access to sensitive data, resources, and systems. It ensures that only authorized users can access sensitive data and activities while keeping unauthorized users out. Access control is critical for protecting sensitive data such as personally identifiable information (PII), financial information, and intellectual property.
Best Solutions to Protect Against Malware in 2023
The modern threat actor is using the most advanced technologies to gain access to your systems, wreak havoc, and steal your sensitive data. In the constant cybersecurity “arms race,” IT providers, MSPs, and security professionals are incorporating these same advanced technologies to stop these sophisticated attacks. In this article, we’ll discuss the current malware threat and work to better understand what you can do to stop these attacks.
Lightrun Bolsters Security Measures with Role-Based Access Control (RBAC)
Lightrun enhances its enterprise-grade platform with the addition of RBAC support to ensure that only authorized users have access to sensitive information and resources as they troubleshoot their live applications. By using Lightrun’s RBAC solution, organizations can create a centralized system for managing user permissions and access rights, making it easier to enforce security policies and prevent security breaches.
Start with endpoint security fundamentals and build from there
Global cyberattacks increased by 38% in 2022 (Source). And because attacks are not only becoming more common, as well as difficult to detect, 65% of organizations plan to increase their cybersecurity spending in 2023 (Source). Even so, hackers will continue to hone their skills and exploit vulnerabilities. Successful ransomware attacks will happen. Theft and sale of personally identifiable information (PII) and other “valuables” on the dark web will happen.