Operations | Monitoring | ITSM | DevOps | Cloud
July 2023
Azure Blob Storage Malware Scanning soon to be GA
On September 1, 2023, Microsoft’s Defender for Azure Blob Storage is set to introduce a groundbreaking feature: Malware Scanning. This highly-anticipated addition to the Defender suite brings real-time protection against malicious content, making it a vital component in fortifying your data security and safeguarding against the ever-evolving threat landscape.
Cloud Native Application Observability - Sensitive Data Masking for logs
SBoMs Are Growing Up: Reflections on CISA's SBoM Conference
Last month, the Cybersecurity and Infrastructure Security Agency (CISA) organized a one-day software bill of materials (SBoM)-centric conference, both amusingly and aptly entitled SBoM-a-Rama. It was a hybrid event allowing for both in-person and remote participation; I chose the latter. As a long-term security practitioner, I’ve been observing the development of this field with great enthusiasm, but always from the periphery.
Selecting the Ideal Business Computer: A Comprehensive Guide
Beyond Borders: 7 Ways to Safeguard International Business Privacy
Keeping up with European security and privacy compliance - the role of infrastructure and automation
Understanding and Preventing Email Spoofing Attacks
Now that most people are familiar with and thus able to avoid standard phishing attacks, malicious actors have shifted to something more insidious. Email spoofing is an attack in which attackers impersonate someone the target knows, is a much more subtle way to compromise a user’s credentials or device. Like phishing, however, once you know the signs of a spoofed email and train other users on how to spot them, addressing the issue is often straightforward.
You're Only as Strong as Your Weakest Link: The Importance of Vendor Risk Assessment
When you choose to work with another organization, for the sake of your reputation and security, you need to carefully vet each organization before finalizing the decision. Choosing a vendor with which to do business relies on that vendor ranking highly on a vendor risk assessment, which occurs when that vendor practices robust security, ensures compliance with local regulations, and implements effective policies and procedures to ensure smooth daily operations.
The DevSecOps Toolchain: Vulnerability Scanning, Security as Code, DAST & More
DevSecOps is a philosophy that integrates security practices within the DevOps process. DevSecOps involves creating a ‘security as code’ culture with ongoing, flexible collaboration between release engineers and security teams. The main aim of DevSecOps is to make everyone accountable for security in the process of delivering high-quality, secure applications. This culture promotes shorter, more controlled iterations, making it easier to spot code defects and tackle security issues.
How can I test CFEngine Policy?
This question was covered in The Agent is In, Episode 27 CFEngine Q&A: Policy Questions. Testing is an important part of the software life-cycle. Writing tests for your CFEngine policy can help to bring improved assurance that your policy behaves as expected. Follow along and write your first test policy.
How can I get a list of specific key values from an array of objects in JSON?
This question was covered in The Agent is In, Episode 27 CFEngine Q&A: Policy Questions. Given the following JSON, how can I get a list containing just the values of name?
Democratizing Data Through Secure Self-Service Concierge Access of Cribl Stream
Ah, the age-old question of how to manage screen time for kids – it’s like trying to navigate a minefield of Peppa Pig, Paw Patrol, and PJ Masks! I mean, who knew Octonauts and Bubble Guppies would become household names? As a dad of two young kids, managing screen time is a balancing act, especially keeping our 5-year-old happy with access to her shows.
CFEngine: The agent is in 27 - CFEngine Q&A: Policy questions
New in Grafana 10: A UI to easily configure SAML authentication
In addition to the built-in user authentication that utilizes usernames and passwords, Grafana also provides support for various mechanisms to authenticate users, so you can securely integrate your instance with external identity providers. We are excited to announce that with the release of Grafana 10.0, we have introduced a new user interface that simplifies the configuration of SAML authentication for your Grafana instances.
Breaking Down the Ransomware Index Spotlight Report Ep. 20 | Security Insights Podcast
Choosing the Right CMS for Your Business: Factors to Consider
Cisco AppDynamics launch The Age of Application Observability report highlighting how business leaders lack knowledge in security management
Norway's Government Agencies Breached by Zero-Day Attack (CVE-2023-35078)
End-to-End Risk-Based Vulnerability & Patch Management from Ivanti
SolarWinds Day: Secure By Design (6/28/23)
The Role Of Software Asset Management In Cybersecurity Preparedness
In this article, we explore the critical role Software Asset Management plays in cybersecurity preparedness. As the threat landscape continues to evolve and malicious actors become more adept at exploiting vulnerabilities, it is essential to take a proactive approach to protect your business and its valuable assets. Our experts delve into the benefits of implementing software asset management strategies, the risks associated with neglecting it, and what you can do to optimize your cybersecurity preparedness.
We used GPT-4 during a hackathon-here's what we learned
We recently ran our first hackathon in quite some time. Over two days, our team collaborated in groups on various topics. By the end of it, we had 12 demos to share with the rest of the team. These ranged from improvements in debugging HTTP request responses to the delightful “automatic swag sharer.” Within our groups, a number of us tried integrating with OpenAI’s GPT to see what smarts we could bring to our product.
Top 4 Methods Used to Attack Networks (And How to Defend)
Threat actors use a number of different techniques to gain access to company networks so that they can deliver ransomware payloads. In this blog, we look at four of the most common techniques currently being used to attack networks. The intent is to help MSPs and IT admins understand where the threats are coming from, and then where to focus their attention in order to protect their (or their customers’) networks.
What Does A Business Need To Make It Safer?
DevSecOps and DevOps: Key Differences
DevOps and DevSecOps have gained more attention in recent years in the world of software development. While both of these methodologies emphasize the agile development process and team collaboration, there are some key differences that distinguish them. Understanding these distinctions is critical for software development teams and organizations to determine which methodology is best suited to their requirements. In this article, we’ll learn about the difference between DevOps and DevSecOps.
Why do you also need confidential computing for your private datacenter?
How summertime turns up the heat on cyber readiness (and what to do about it)
“Malicious cyber actors aren’t making the same holiday plans as you.” (CISA & FBI) Summertime is prime time for cyberattacks. According to one survey, 58% of security professionals believe that there is seasonality in the attacks that their company experiences every year, with the majority citing summer as high season for breaches.
Understanding the SEO Benefits of Implementing a Web Application Firewall
RapidSpike July Customer Forum
14 Critical Log Files You Need to Monitor for System Security
In the realm of Linux system administration, monitoring log files is essential for maintaining a healthy and secure environment. Linux distributions generate a multitude of log files that capture crucial information about system events, errors, and user activities. These log files act as a silent witness, providing valuable insights into the inner workings of a Linux system.
Zero Trust: An Analyst's Perspective with Forrester Analyst, Steve Turner
Blameless Unveils Multibot Support, Empowering Enterprise Security Teams to Manage Incidents on their Terms
Azure Security Features
Welcome to the thrilling era of cloud computing, where digitization is no longer a trendy phrase but an operational reality for numerous businesses. Among the key players in this transformative phase, Microsoft Azure has carved a niche for itself. Known for its powerful and dynamic infrastructure, Azure leads the way in delivering exceptional cloud services.
Different Access for Different Roles: Cribl's New Authorization Support for Enhanced Security
When working with sensitive data, there’s no skimping on security. Keeping data protected and private is paramount at Cribl, which is why we prioritized building a robust framework for Role-Based Access Control (RBAC), and with this latest release, we created an authorization system across the entire Cribl suite. WOOHOO!!
Optimizing Network Performance using Topology Aware Routing with Calico eBPF and Standard Linux dataplane
In this blog post, we will explore the concept of Kubernetes topology aware routing and how it can enhance network performance for workloads running in Amazon. We will delve into topology aware routing and discuss its benefits in terms of reducing latency and optimizing network traffic flow. In addition, we’ll show you how to minimize the performance impact of overlay networking, using encapsulation only when necessary for communication across availability zones.
Mastering Zero Trust - Pillars for Security
More on Supply Chain Attacks Ep. 19
Elevate the Security of Your Kubernetes Secrets with VMware Application Catalog and Sealed Secrets
Alfredo García, manager R&D, VMware contributed to this blog post. VMware Application Catalog now includes enterprise support for Sealed Secrets, enabling customers to add an asymmetric cryptography-based protection to their Kubernetes Secrets stored in shared repositories.
A Detailed Guide to Docker Secrets
This post was written by Talha Khalid, a full-stack developer and data scientist who loves to make the cold and hard topics exciting and easy to understand. No one has any doubt that microservices architecture has already proven to be efficient. However, implementing security, particularly in an immutable infrastructure context, has been quite the challenge.
Network Detection & Response Optics
2023 Webinar UEM + Endpoint Security
SolarWinds announces its Next-Generation Build System aligns with NIST Secure Software Development Framework
2023 Webinar UEM + Endpoint Security Part1
DoD Compliance + DoD Configuration Management: How to Get Compliant with Less Effort
Spotting Vulnerabilities at Rest and at Runtime feat. Cloudsmith and Sysdig
7 Reasons To Choose SafeOpt Over Other Online Retail Software Options
Introducing the Cribl Pack for Corelight
In this blog series, we’ll explore how Corelight and Cribl Stream work together to improve observability in Security Operations Centers (SOCs). In today’s rapidly changing threat landscape, it’s crucial to efficiently monitor and manage data for effective security operations. Corelight provides exceptional network visibility, while Cribl Stream gives you control and the flexibility to optimize data pipelines and gain valuable insights.
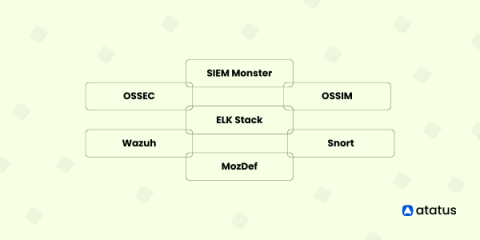
Top Open Source SIEM Tools
In the fast-paced world of cyber security, organizations face a challenging task to safeguard their digital assets from a variety of advanced threats. Security Information and Event Management (SIEM) tools have emerged as a vital solution, empowering businesses to detect, respond to, and mitigate security incidents effectively.
9 Foolproof Ways to Protect Your Employee Privacy
Cybercrime is one of the greatest threats to modern businesses, so naturally, cybersecurity is becoming a top priority among business leaders worldwide. It’s easy to see why. Cybercrime can result in significant losses for companies, particularly financially. In fact, the global cost of cybercrime is expected to rise to $23.84 trillion by 2027, up from $8.44 trillion in 2022. Businesses collect and store mountains of data daily, and are obligated to keep that data secure.
The key to secure transmission: TLS in the Raygun ecosystem
Understanding Amazon Security Lake: Enhancing Data Security in the Cloud
HAProxy and Let's Encrypt: Improved Support in acme.sh
TLS certificates are crucial for the secure flow of web traffic, but managing these digital certificates can pose a challenge. Using an ACME-based certificate authority like Let’s Encrypt can automate and simplify the management of issuing these certificates. Certificate management in HAProxy has steadily improved over the years, allowing it to become more flexible and load certificates without restarting.
How Kentik Helps You Mitigate Cyberattacks Faster
No matter how much prevention you have, serious security incidents will inevitably occur. Read the next article in our security series that covers how to understand cyberattacks as quickly as possible so that your organization can respond swiftly.
Why Cyber Resilience Is Foundational to Your SIEM Success
The common failure scenarios that occur in the cybersecurity world are typically assumed to be costs of doing business, but they’re actually more predictable and avoidable than you might imagine. Even if you’ve been lucky enough to avoid failed data sources or backups, a SIEM getting knocked offline, and other cybersecurity attack situations until now — in today’s day and age, they’re still inevitable.
IT in Motion Podcast: Protecting your Data from the Dark Side
Longtime ScienceLogician Tim May joins the podcast for an entertaining discussion surrounding the number of different roles he's held within the organization in his 17 years with ScienceLogic, and a glimpse into his admiration of Star Wars! https://sciencelogic.com/product/resources/protecting-your-data-from-the-dark-side
Unpatched Microsoft 0-Day: How to Mitigate CVE-2023-36884 with PowerShell
Microsoft's July 2023 Patch Tuesday updates highlighted several vulnerabilities under active exploitation, including one (or more?) that remains unpatched. Here's what you need to know about CVE-2023-36884, a zero-day vulnerability that attackers are exploiting to gain remote code execution via "specially-crafted" Microsoft Office documents.
Work Injury Prevention: Creating a Culture of Safety in the Workplace
The Role of SSL Certificates in Enhancing Website Security and SEO
Securing Your Network: OpenWrt Firmware for Improved Router Protection
Trusted Types: How we mitigate XSS threats in Grafana 10
Grafana is a rich platform for data visualization, giving you full control over how your data should be visualized. However, this flexibility and freedom comes with some challenges from a security perspective — challenges that need to be solved to protect the data in Grafana. For years, cross-site scripting (XSS) has been among the most common web application security vulnerabilities.
Maximizing Efficiency: 6 Online Services That Can Help Your New Business
Better security for your app's secrets
The incident-io/core application uses a mixture of environment variables, config files and secrets stored in Google Secret Manager to configure the app. This is a reference guide to all the parts that make up this flow.
Chaos AI Assistant (Security Overview)
Chaos AI Assistant (Security Analysis via Chain of Thought)
Chaos AI Assistant (Security Analysis)
SOAR vs. SIEM: Understanding the Differences
This post was written by Joe Cozzupoli. Scroll down to read the author’s bio. As the cybersecurity landscape evolves and threats become more sophisticated, organizations need to stay ahead with the right tools and strategies to protect their valuable data. Two key technologies in this domain are Security Orchestration, Automation, and Response (SOAR) and Security Information and Event Management (SIEM).
CNAPP: A Comprehensive Solution for Cloud-Native Application Security
A unique approach to security is needed when developing cloud-native apps that use microservices, containers, and serverless computing. The specific security issues that these cloud-native architectures provide are the focus of CNAPPs. Traditional security solutions are frequently created to protect on-premises infrastructure and applications. However, new security strategies are required due to the adoption of cloud-native architectures and the migration to cloud computing.
Work Anywhere. Secure Everywhere.
Big Cybersecurity News Ep. 17
Generative AI for InfoSec and Hackers- What Security Teams Need to Know
Turbocharging host workloads with Calico eBPF and XDP
In Linux, network-based applications rely on the kernel’s networking stack to establish communication with other systems. While this process is generally efficient and has been optimized over the years, in some cases it can create unnecessary overhead that can impact the overall performance of the system for network-intensive workloads such as web servers and databases.
10 Best Security Tools for eCommerce
The eCommerce businesses have expanded in leaps and bounds during the COVID-19 and post-COVID situations and continue to show the same trend. People across the globe continue to shop online for their needs of clothing and apparel, home needs of groceries, home appliances, home décor, health and fitness products, sports needs, automotive accessories, jewelry, and much more. Today’s modern-day customers prefer to purchase online many of their needs with a single click through their mobiles.
8 Common Uses of VPN in 2023: How People Leverage Its Benefits
10 Steps to Create a Risk Management Plan
From Monitoring to Action - Get Faster Incident Response with Change Forensics
In this post you’ll learn how Kosli’s Change Forensics gives DevOps, Platform, and Site Reliability Engineers the ability to rapidly pinpoint and understand changes and events in their infrastructure and applications, and get to the cause(s) of an incident quickly.