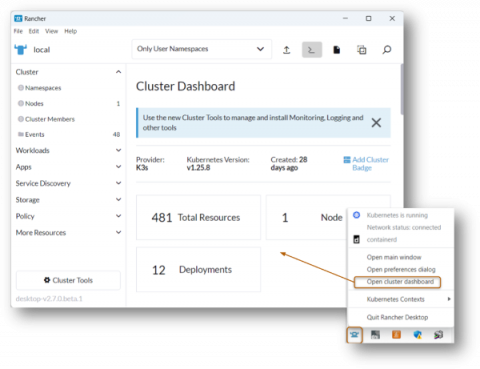
Patch management automation: Is it worth the hype?
Patch management is a term that’s familiar to all within the depths and boundaries of endpoint security. While the addition of “automation” to this term might make it seem like one among the thousands of other automated tasks, cybersecurity experts have been going gung ho over it in the last few years. If you’re reading this, it probably doesn’t make sense to explain to you what patch management automation or automated patch management is.