Operations | Monitoring | ITSM | DevOps | Cloud
June 2023
Security Customer Fireside Chat with Dr. Joel Fulton, CEO of Lucidum
Managing Compliance: Tips + Strategies for Breaking the Vicious Scan-Fix-Drift Cycle
10 Essential Security Tips for Safeguarding Your Cloud Services
In today’s digital era, the cloud has revolutionized the way we store, process, and transmit data, offering scalability, efficiency, and flexibility. As we continue to transition towards this cloud-first approach, the importance of robust cloud security can’t be overstated. This article will provide ten essential tips for ensuring the safety and security of your data in the cloud.
How Kentik reduces the likelihood of a full-blown cyber-attack before it happens
Organizations are under constant attack, and it’s critical to reduce the time it takes to detect attacks to minimize their cost. This first article in our new security series dives deep into how Kentik helps customers before, during, and after a cyber attack.
Managing security vulnerabilities and compliance for U.S. Government with Ubuntu Pro
The founding moments: Tracing the origins of confidential computing
Why Trust Zero Trust Ep. 16
CFEngine: The agent is in 26 - Demo of CFEngine 3.22
Why Data Privacy Should Be a Top Priority for Every Business
RapidSpike PCI & GDPR Audit
Strengthen your cloud cyber security with Ubuntu Pro and confidential VMs
15 surprisingly scary application security statistics
Take a research-based look at the state of application security and learn how leveraging security builds user trust, resilience and revenue growth. According to the cybersecurity readiness index released by Cisco in March of 2023, less than 10% of all companies worldwide are considered mature enough to tackle today’s cybersecurity issues. In part, this lag in maturity can be attributed to 92% of technologists prioritizing rapid innovation across application development ahead of app security.
New Apple Zero-Days: Patch CVE 2023-32434 and CVE 2023-32435
Network visibility makes all the difference! The key to Managed Service Providers to protecting your customer data
Strengthening Aviation Cybersecurity: Take Flight with Teneo and Akamai Guardicore
In today’s digital landscape, the aviation industry faces increasingly sophisticated cyber threats that can compromise the safety and security of critical systems. To combat these challenges, the Transportation Security Administration (TSA) has implemented new cybersecurity requirements. In this blog post, we’ll explore how Teneo, in collaboration with Akamai Guardicore, can help aviation organizations meet these requirements and strengthen their cybersecurity defenses.
Leveraging Calico flow logs for enhanced observability
In my previous blog post, I discussed how transitioning from legacy monolithic applications to microservices based applications running on Kubernetes brings a range of benefits, but that it also increases the application’s attack surface. I zoomed in on creating security policies to harden the distributed microservice application, but another key challenge this transition brings is observing and monitoring the workload communication and known and unknown security gaps.
The Power Duo: Authentication and AML Strategies for Tech Companies
Phishing 2.0: How to Stop Cyberattacks Even Pros Can't Catch
Logz.io Cloud SIEM Available on AWS AppFabric at Launch
Logz.io is honored to have our Cloud SIEM as one of the products available as part of the launch of AWS AppFabric. For customers invested in AWS, this inclusion allows you to use our cloud-based, agile SIEM seamlessly alongside other critical SaaS applications.
How to record events in your CI pipelines with Kosli Flows
In an ideal world CI pipelines would never fail and deployments would be easy to navigate. The reality is that the journey from commit to production can fail in subtle ways that can be hard to understand. And this problem is multiplied by the number of pipelines in your system.
What Is Reasonable Suspicion And Why Is It Important
Cyberattack Prevention with AI
Cyberattack prevention involves proactive steps organizations take to protect their digital assets, networks, and systems from potential cyber threats. Preventive measures, such as a combination of best practices, policies, and technologies, are employed to identify and mitigate security breaches before they can cause significant damage.
Enforcing Policy as Code with Cloudify, Terraform, and Open Policy Agent
In my previous article, I provided an example of using Cloudify’s native REST plugin to send a policy evaluation request to an Open Policy Agent (OPA) service. While dispatching requests to an upstream OPA endpoint is a great way to integrate policy enforcement throughout an environment blueprint, Cloudify has also been working toward native integration of OPA throughout our ecosystem.
Streamlining Data Management for Enterprise Security | SpyCloud
Enforce fine-grained policy control across your data infrastructure
6 Security Tips For Companies Using Cloud Technology
Monetizing APIs: Strategies and Considerations
Building better software security with a BSIMM app
In a rapidly changing world, security is more important than ever. With good security, customers can trust organizations to take their digital infrastructure to the next level. But how do you implement top security measures across a large, complex company? At ServiceNow, we use our own products to protect ourselves and our customers—and to extend the functionality of the Now Platform.
How to connect a private data source
What is an Endpoint Device? Overview for IT Professionals
Endpoints can be found in a variety of industries and settings, but we’ll be focusing on endpoint devices within IT environments. In this article, we provide a general overview about what endpoint devices are, the purpose they serve, as well as how you can better manage and protect these devices within your organization.
CISA's BOD 23-02: How to Mitigate The Risk of Internet-Exposed Management Interfaces
Microsoft Teams' IDOR Lets Attackers Inject Malware Into Your Organization - Here's How to Prevent it
New in Grafana 10: Securely monitor and query network-secured data sources from Grafana Cloud
Grafana is designed to visualize data in beautiful dashboards, no matter where the information lives. However, if you are considering the hosted Grafana Cloud observability stack for visualizing your data, you might run into a roadblock: network security. The problem is that some data sources, like MySQL databases or Elasticsearch clusters, are hosted within private networks.
Maximizing Security and Compliance with Outsourced Back-End Development
How IT Device Discovery Can Identify Your Network's Assets and Vulnerabilities
The security of your organization’s network is paramount to its success. With the ever-changing landscape of cyber threats, it's important to take the necessary steps to ensure that your network is secure and compliant with industry regulations. Ensuring compliance requires you to know what’s on your network. But how can that be done when only 48% of leaders and security professionals say they run their asset discovery program at least once per week?
Learn the top 4 best practices for effective firmware vulnerability management
Cybersecurity Made Easy: Simplifying Account Protection
Introduction to SBOMs - What is it and do I need one? - Cloudsmith's Unpacked Conference 2023
Real World Strategies for Securing the Software Supply Chain - Cloudsmith's Unpacked Conference 2023
Fleet: Multi-Cluster Deployment with the Help of External Secrets
Fleet, also known as “Continuous Delivery” in Rancher, deploys application workloads across multiple clusters. However, most applications need configuration and credentials. In Kubernetes, we store confidential information in secrets. For Fleet’s deployments to work on downstream clusters, we need to create these secrets on the downstream clusters themselves.
Cloud Native Security for the Rest of Us
Why Scammers Want Your Information and How to Protect Yourself Online
Applying Zero Trust to Data Centre Networks
Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems. We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.
The 8 Best Practices for Reducing Your Organization's Attack Surface
Increases in attack surface size lead to increased cybersecurity risk. Thus, logically, decreases in attack surface size lead to decreased cybersecurity risk. While some attack surface management solutions offer remediation capabilities that aid in this effort, remediation is reactive. As with all things related to security and risk management, being proactive is preferred. The good news is that ASM solutions aren't the only weapons security teams have in the attack surface fight.
How Implementing Risk-Based Patch Management Prioritizes Active Exploits
Resistance to change is always present, especially if you think the processes you have in place are efficient and effective. Many organizations feel this way about their software management procedures until they have a security breach or incident and are left wondering where they went wrong. The reality is that most patch management programs are built on assumptions and recommendations, rather than facts about actively exploited vulnerabilities. Risk-based patch management is the answer to this issue.
Data security at scale: How IT modernization impacts cybersecurity and data access for the U.S. Department of Defense
As more and more of the public sector enact large-scale digital transformation initiatives, government organizations must find new ways to manage massive amounts of data securely while maintaining compliance. With new mandates from the Biden administration to enhance cybersecurity best practices in both the private and public sectors, organizations like the Department of Defense (DoD) face new challenges to their data management and communication practices.
The Evils of Data Debt
In this livestream, Jackie McGuire and I discuss the harmful effects of data debt on observability and security teams. Data debt is a pervasive problem that increases costs and produces poor results across observability and security. Simply put — garbage in equals garbage out. We delve into what data debt is and some long term solutions. You can also subscribe to Cribl’s podcast to listen on the go!
The Definitive Guide to IT Risk Management
Top 5 cloud security risks
RapidSpike ROI Calculator
Is Linux secure?
Meet Pal. Pal is a senior developer working at PalBank. For the next 6 months, Pal will be responsible for leading the development of the bank’s web application client, which will be used daily by millions of customers.
FWaaS (Firewall as a Service): How to Monitor Your Traffic Through Cloud
Cybersecurity remains a key concern for any organization. The cost of cybercrime is expected to rise to $8 trillion in 2023 and reach $10.5 trillion by 2025. Various cybersecurity solutions are available, with Firewall as a Service (FWaaS) emerging as one of the most valuable assets when it comes to protecting your interests. We will investigate FWaaS solutions, how they work, how they're different from traditional firewalls, and what benefits they can provide for a range of organizations.
Security maintenance vs support: what's the difference?
CFEngine 3.22 released - Coordination
Today, we are pleased to announce the release of CFEngine 3.22.0! The focus of this new version has been coordination. This is a non-LTS (non-supported) release, where we introduce new features for users to test and give feedback on, allowing us to polish before the next LTS.(CFEngine 3.24 LTS is scheduled to release summer 2024).
The Role of Penetration Testing in Strengthening Your Cybersecurity
Successfully Navigating Your Business Through a Cyber Attack
Securing open source software with Platform One and Canonical
Storing Secrets with Telegraf
Telegraf is an open source plugin-driven agent for collecting, processing, aggregating, and writing time series data. Telegraf relies on user-provided configuration files to define the various plugins and flow of this data. These configurations may require secrets or other sensitive data. The new secret store plugin type allows a user to store secrets and reference those secrets in their Telegraf configuration file.
Data Tampering: A Comprehensive Guide
In an increasingly interconnected and data-driven world, where information shapes decisions and fuels innovation, the integrity of data has become paramount. However, lurking beneath the surface is a silent threat that can undermine trust, compromise systems, and wreak havoc on organizations: data tampering. In this post, we delve into the realm of data tampering, exploring the vulnerabilities, the reasons behind data tampering practices, and countermeasures against them.
Digital Leap: Understanding the Transformative Impact of Software on Healthcare
The ABC of Risk Management Automation
It's Official, Scout is SOC 2 Certified
Valued customers, friends, and Scout APM users: Our goal has always been to provide you with the peace of mind of knowing your systems are healthy and serving your customers as expected. While security has always been paramount to us, we’ve recently made it official. We are thrilled to share with you a recent significant achievement for our team and those who trust us with their data. After many months of hard work, we have obtained our SOC 2 certification!
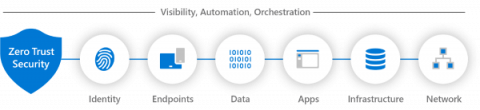
What is Zero Trust Security and Why Should You Care?
Automation has become a game changer for businesses seeking efficiency and scalability in a rather unclear and volatile macroeconomic landscape. Streamlining processes, improving productivity, and reducing incidence for human error are just a few benefits that automation brings. However, as organizations embrace automation, it’s crucial to ensure modern security measures are in place to protect these new and evolving assets.
What Do Our Users Love About Cove Data Protection?
At N-able’s recent Empower partner event in Prague, we took the opportunity to ask some Cove Data Protection users what they actually think about the product. Naturally, we were pleased to hear so many positive comments, but we also found that their reasons for choosing Cove varied, as did the capabilities they value most. Here’s a little sample.
10 Most Common PHP Security Threats and the Best Ways to Fix Them
PHP is a powerful language used by at least 80% of all the applications you use today as their backend scripting language. This can be attributed to its relatively simpler syntax, which is on the same line as other C-style languages. It supports different operating systems (Windows, Linux, macOS), web servers, databases and integrates seamlessly with popular databases like MySQL, PostgreSQL, and Oracle, making it a suitable choice for database-driven applications.
A guide to dynamic application security testing (DAST)
Dynamic application security testing (DAST) is a critical security measure for modern software delivery pipelines. It involves evaluating the security of web applications by actively testing them in real-time, simulating real-world attacks to identify vulnerabilities. As the cybersecurity threat landscape has evolved, DAST has emerged as a key tool for enforcing application security in continuous integration and continuous delivery (CI/CD) pipelines.
Ribbon's STIR/SHAKEN Solution Enables Unyc to Fulfill Regulatory Requirements, Protecting Customers from Bad Actors
Benefits of Monitoring for Cloud Security
DNS observability and troubleshooting for Kubernetes and containers with Calico
In Kubernetes, the Domain Name System (DNS) plays a crucial role in enabling service discovery for pods to locate and communicate with other services within the cluster. This function is essential for managing the dynamic nature of Kubernetes environments and ensuring that applications can operate seamlessly. For organizations migrating their workloads to Kubernetes, it’s also important to establish connectivity with services outside the cluster.
Merging to Main #3: CI/CD Secrets
The Future of DevOps and Platform Engineering - Civo.com
NinjaOne Debuts Patch Management Advancements to Mitigate Security Vulnerabilities
How to Be a Target for Cybercriminals: Reuse Your Passwords
Challenges and Guidelines for Generative AI in companies
In today’s rapidly evolving technological landscape, companies continue to explore ways to innovate and stay ahead of the competition. One of the most promising technologies available today for companies is Generative AI, which helps automate creative tasks that were previously only possible through human intervention. The use of Generative AI in companies has grown rapidly over the years due to its numerous benefits such as increased productivity and efficiency while minimizing costs.
Ask What Air-Gapping Can Do for You
In our recent webinar on air-gapped security, D2iQ VP of Product Dan Ciruli shared a new way of thinking about air-gapping, explaining how air-gapping could be applied in places that are not usually considered candidates for air-gapping. In an exchange of insights with Paul Nashawaty, principal analyst at Enterprise Strategy Group, Ciruli explained how the need for air-gapped security has become more critical as more organizations move to the cloud.
3 Keys to Maximizing SIEM Value
SIEM has been a crucial component of security systems for nearly two decades. While there’s ample information on operating SIEM solutions out there, guidance on evaluating and managing them effectively is lacking. We’ve noticed many SIEM vendors are taking advantage of this dearth of knowledge and not providing customers with needed value for what they’re buying.
Transforming Your Business through Security Offerings
Visualizing service connectivity, dependencies, and traffic flows in Kubernetes clusters
Today, the cloud platform engineers are facing new challenges when running cloud native applications. Those applications are designed, deployed, maintained and monitored unlike traditional monolithic applications they are used to working with. Cloud native applications are designed and built to exploit the scale, elasticity, resiliency, and flexibility the cloud provides. They are a group of micro-services that are run in containers within a Kubernetes cluster and they all talk to each other.
Accelerate Investigations, Forensics and Audits Using Cribl Search and Amazon S3
In the era of big data, data lakes have emerged as a popular way to store and process massive amounts of data. Fortunately, with Cribl Search and Cribl Stream, you can create a Data Loop to optimize the use of your data lake by saving Search results as part of an investigation. Our four-part video series explains how to set up Cribl Search and Cribl Stream to establish a Data Loop using the Amazon S3 Data Lake destination in Cribl Stream and the Cribl Stream in_cribl_http source.
A holistic approach to securing Spark-based data engineering
CRLF Injection, Explained: An In-Depth Guide
In this in-depth guide we’ll explore CRLF injection, a web application security vulnerability that can have severe consequences. First, we’ll cover what CRLF injection is, the types of CRLF injection attacks, and their potential impacts. Additionally, we’ll discuss similarities with other attacks, payloads used in these exploits, and how to prevent CRLF injection. Finally, we’ll touch on the role of OWASP in addressing this security risk.
Terraform Import: What It Is and How to Use It
In this post we’ll explore Terraform Import, a powerful command-line tool that allows you to bring existing infrastructure under Terraform management. We’ll cover what Terraform Import is, its common use cases, and how to use it effectively. Additionally, we’ll discuss some limitations you should be aware of when using Terraform Import.
Modernize Your SIEM Architecture
Docker container security: demystifying FIPS-enabled containers with Ubuntu Pro
In today’s rapidly changing digital environment, the significance of robust Docker container security measures cannot be overstated. Even the containerised layer is subject to compliance standards, which raise security concerns and compliance requirements. Docker container security measures entail safeguarding our lightweight, appliance-type containers –each encapsulating code and its dependencies– from threats and vulnerabilities.
Protecting Our Partners from Cyber Attacks
Securing Apache Spark Big Data Operations
The Human Element of Preventing Supply Chain Attacks: Security Insights Podcast Ep. 12
Top 3 SIEM Optimizations - How to Get More From Your Existing Tech Stack
In today’s digital-first world, most security problems are actually data problems, and data volumes are outpacing organizations’ abilities to handle, process, and get value from it. You’ll have 250% more data in five years than you have today, but the chances of your budget increasing to match that are slim. The challenges that come with managing the rise in enterprise data volume directly affect your ability to adequately address cybersecurity risks.
Zero trust security for CI/CD pipelines
The zero trust security model is an approach to network security that enforces strict access controls and authentication at every stage of the software development lifecycle. It treats every user, device, and transaction as a security risk and uses the principle of least privilege to restrict access to sensitive resources and minimize the potential attack surface.
Migrating to cfbs
Traditionally, CFEngine policy sets are managed as a whole. When upgrading the Masterfiles Policy Framework (MPF)1 users must download the new version of the policy framework and integrate it into the existing policy set, carefully diffing the vendored policy files against their currently integrated policy. Updates to policy authored by others must be sought out and similarly integrated.