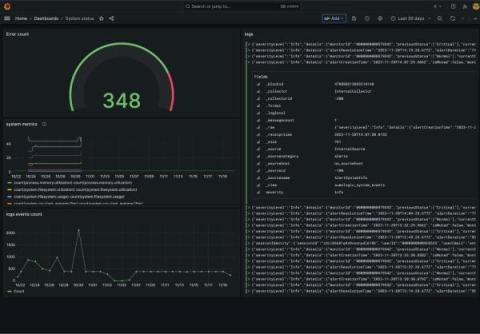
Decoding .NET8: Unveiling Cloud-Native Observability
The.NET programming language is taking cloud native deployment and observability seriously, and most notably with the recent announcement of.NET Aspire stack unveiled at the recent.NET Conf 2023. In the latest episode of OpenObservability Talks, we reviewed the journey to making.NET a “by default, out of the box observable platform,” as ASP.NET Core creator David Fowler put it.