Operations | Monitoring | ITSM | DevOps | Cloud
August 2023
How to Reduce IT Security Risk With IT Asset Management
How New Mexico State University accelerates compliant federal research with Ubuntu
How AI Is Challenging Cybersecurity Efforts
What are the Benefits of Using Cribl Stream with Amazon Security Lake?
In a recent user group meeting, guest speaker Marc Luescher from Amazon Web Services (AWS) joined us to give an overview of Amazon Security Lake. We talked about Cribl use cases and how Cribl Stream can bring your non-AWS data into the Security Lake. Enterprises are dealing with some significant challenges with security data in 2023. Inconsistent, incomplete, poorly-formatted log data is simultaneously scattered across companies and locked up in different silos within the organization.
5 Reasons Why NIS2 Directive Preparation Should Start Now, Part One: Audits Take Time
You probably heard about the European Union’s updated Network and Information Security Directive (NIS2). This directive will translate into active law in October 2024. You should be ready for it, as there are high fines and sanctions for non-compliance. But you might be tempted to think that October 2024 is far away, right? Think twice. After all, how can you know if you have plenty of time to prepare if you don’t know how well you currently comply with the projected regulations?
5 Reasons Why NIS2 Directive Preparation Should Start Now, Part Two: Implementation Takes Time
In a previous blog post, I discussed the two main areas to audit before the European Union’s updated Network and Information Security Directive (NIS2) becomes ratified law in October 2024. Specifically, these audits would: Identify your gaps with the NIS2 directive’s requirements now. Review your current supply chain security flaws. Now that we’ve discovered these security flaws, we must fix them — before time runs out in October 2024.
Your Guide to ACSC Essential 8 Compliance
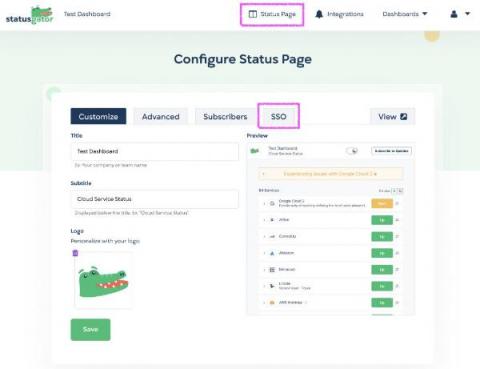
New Feature: Enhance Security with Status Page SSO
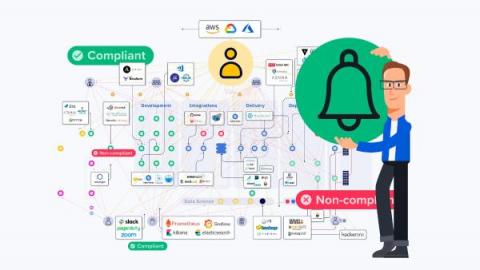
We’ve heard your feedback and it’s here: Status page SSO is now available on our Enterprise plan. Status Page Single Sign-On (SSO) empowers StatusGator customers to safeguard their status pages through a seamless Single Sign-On experience. You can now restrict access to your status page to only your team, employees, or users who have SSO access through your organization’s identity provider.
Blackhat 2023 Recap: How Will Advanced AI Impact Cybersecurity?
Online Security For Businesses: Threats, Weaknesses, And Solutions
Everbridge Smart Security
How to Utilize Dark Web Monitoring Protection
Odds are, you've heard about the dark web. Nevertheless, you may be unsure about its threat to your business and how to address it. The dark web is a set of anonymously hosted websites within the deep web accessible through anonymizing software, commonly "TOR" (The Onion Router). The anonymity these websites provide makes them the perfect online marketplace for illegal activities.
What is MITRE ATT&CK and How to Use the Framework?
The MITRE ATT@CK® framework is one of the most widely known and used. The Flowmon Anomaly Detection System (ADS) incorporates knowledge of the MITRE ATT&CK framework. Using ADS and its MITRE ATT&CK knowledge makes detecting advanced threats against networks and IT systems easier and simplifies explaining the danger and risks when outlining an attack to all stakeholders.
Modernizing Cybersecurity: New Challenges, New Practices
The practice of cybersecurity is undergoing radical transformation in the face of new threats introduced by new technologies. As a McKinsey & Company survey notes, “an expanding attack surface is driving innovation in cybersecurity.” Kubernetes and the cloud are infrastructure technologies with many moving parts that have introduced new attack surfaces and created a host of new security challenges.
Breaking the Cloud Illusion: The Hard Truth about Successful Migrations
How to Secure IoT Devices: 5 Best Practices
Internet of Things (IoT) devices, computing devices that send and receive information via the Internet and that run very specific applications, can be anything from smart thermostats to smart TVs. The main advantage of IoT devices is their constant connectivity, which allows users to access information and control the devices remotely at any time.
10 Best Firewalls for Small Business to Use in 2023
New report: The state of Calico Open Source 2023
We are excited to announce the publication of our 2023 State of Calico Open Source, Usage & Adoption report! The report compiles survey results from more than 1,200 Calico Open Source users from around the world, who are actively using Calico in their container and Kubernetes environments. It sheds light on how they are using Calico across various environments, while also highlighting different aspects of Calico’s adoption in terms of platforms, data planes, and policies.
Patch And Vulnerability Management: How to Find Vulnerable Software
Black Hat 2023 Recap: The Future is Artificial
After a solid week in Vegas and another solid week of recovery, I’m back in the office (AKA sitting on my couch eating Doritos with chopsticks so I don’t get my keyboard dirty) to bring you my official Black Hat 2023 recap. This year’s event was noticeably scaled back, with fewer people swag surfing the business hall and more technical security folks in search of solutions for actual business problems.
Securing Firmware Updates With AES Encryption
Connected devices require a secure point-to-point channel to ensure that there is no possibility of exposing important data for the integrity of an embedded system. This is especially true when we talk about over-the-air (OTA) software updates, where the new firmware has a long way to go before reaching its destination and being installed by our bootloader. In this publication, we will explore a simple method to encrypt the firmware using the AES algorithm, using open-source libraries in Python.
Securing Company Data With Enterprise Access Control
Access control is a vital security measure that manages user interactions with systems, networks, or resources, safeguarding sensitive information and preventing unauthorized access. By granting or denying specific permissions based on user roles, organizations ensure that only authorized individuals have access to data, mitigating the risk of data breaches and cyberattacks.
AZcopy and GDPR compliance
In today’s data-driven world, managing information is more crucial than ever. With the constant flow of data, both individuals and organizations are increasingly concerned about privacy and security. The General Data Protection Regulation (GDPR) has emerged as a key legislative framework in the European Union to protect citizens’ personal data. But how does this relate to the tools we use to manage and transfer data, like Microsoft’s AzCopy?
Why should every organization invest in cybersecurity software?
In today’s digital age, organizations across industries are increasingly reliant on technology for their operations, communication, and data management. While this technological advancement is no doubt beneficial, it also brings with it a heightened risk of cyber threats and attacks. From data breaches and ransomware attacks to intellectual property theft and financial fraud, the consequences of a cybersecurity breach can be devastating for any organization.
How to Use Kentik to Perform a Forensic Analysis After a Security Breach
In this post, Phil Gervasi uses the power of Kentik’s data-driven network observability platform to visualize network traffic moving globally among public cloud providers and then perform a forensic analysis after a major security incident.
How to Use Nmap: Complete Guide with Examples
In the constantly changing cybersecurity landscape, staying one step ahead of malicious actors is crucial - and understanding the intricacies of your networks is an integral part of that. A tool that can help you do this has earned its reputation as a cybersecurity stalwart - Nmap. Nmap, short for Network Mapper, holds the keys to unlocking valuable insights in your network infrastructure.
Optimizing Web Security Operations for Remote Work Environments
Managing Users and User Groups: A Guide to OKTA and Cloudsmith Integration
Explore Cloudsmith’s powerful OKTA integration for user and user group management. Dive into the benefits, security considerations, and best practices to optimize user access, streamline workflows, and bolster security in your software operations. User management is the backbone of secure and efficient software operations. As businesses grow and evolve, the tools they use must keep pace. Enter OKTA and Cloudsmith.
CISO's MOST WANTED: Outsmarting Cyber Criminals with Tips from a Former FBI Agent
Key Steps for a More Secure Linux Server
Linux server hardening means fortifying and securing a Linux server in order to protect it from vulnerabilities and threats. While total security will always remain a moving target in the security arms race, this article explores some important fundamental steps you can take to help keep your servers safe and secure.
How to secure your database
Everything I Needed to Know about Securing a DevOps Platform - Civo Navigate NA 23
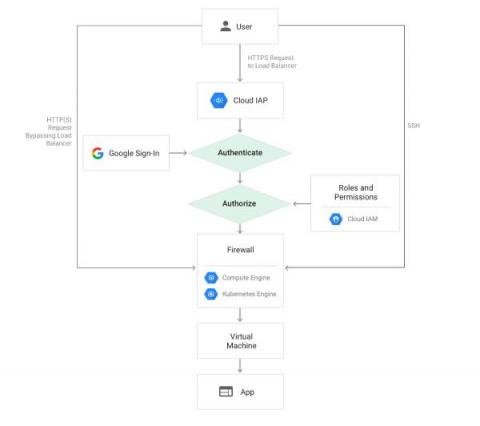
Authenticating Users with Google IAP in Rails
Google Identity-Aware Proxy (IAP) is a Google Cloud service that provides authentication for web applications. This service simplifies the process of building web applications authenticated with Google, eliminating the need to handle user-related concerns within your application code. This is especially valuable for internal applications within organizations that already utilize GSuite. It is straightforward to use, particularly when operating on Google Cloud.
Identity Theft Trends in the Digital Age: New Methods and Prevention Strategies
How to Strengthen Kubernetes with Secure Observability
Kubernetes is the leading container orchestration platform and has developed into the backbone technology for many organizations’ modern applications and infrastructure. As an open source project, “K8s” is also one of the largest success stories to ever emanate from the Cloud Native Computing Foundation (CNCF). In short, Kubernetes has revolutionized the way organizations deploy, manage, and scale applications.
Why Encryption is Crucial for Your Business' Data Security
In this digital age, businesses of all sizes rely on technology to store, transmit, and process sensitive data. While the use of digital technology brings many benefits, it also comes with its own set of challenges, and one of the biggest ones is ensuring cybersecurity. The exponential increase in cybercrime has made it essential for companies to prioritize security while working with digital technologies.
How business acumen boosts application security
To outpace the competition in an era where high-performing, secure digital experiences are expected, business acumen can inform AppSec priorities. Now more than ever, business leaders are racing to build, modernize and deploy business-critical apps on-premises and within distributed, cloud native environments.
Air-Gapping Should Be Head-Slappingly Obvious
When you think of air-gapped security, you imagine a protective distancing that separates your sensitive data from those who would steal it. In practice, the separation is a disconnection from the Internet. If no one can get to your data, no one can steal it. However, air-gapped deployments that are completely disconnected from the Internet are not the case in all instances. It’s true that many clusters are fully air-gapped, particularly in classified government installations.
What Does Real Time Mean?
Cindy works long hours managing a SecOps team at UltraCorp, Inc. Her team’s days are spent triaging alerts, managing incidents, and protecting the company from cyberattacks. The workload is immense, and her team relies on a popular SOAR platform to automate incident response including executing case management workflows that populate cases with relevant event data and enrichment with IOCs from their TIP, as well execute a playbook to block the source of the threat at the endpoint.
How to Perform a Forensic Analysis After a Security Breach
The Impact of Cyber Security on Disaster Recovery and Continuity Planning
Exploring the Intelligence Gap: Robocop and Cyber Criminals
As technology professionals, we must consider the evolution of security and its connection to literature, such as George Orwell’s “1984” and Aldous Huxley’s “Brave New World.” The digital threats we face are often unseen, lying dormant until they can be weaponized for both good and evil purposes. Advancements in machine learning and algorithms have revolutionized data analysis, allowing us to observe and analyze behavioral patterns both online and offline.
Integrating Calico statistics with Prometheus
Metrics are important for a microservices application running on Kubernetes because they provide visibility into the health and performance of the application. This visibility can be used to troubleshoot problems, optimize the application, and ensure that it is meeting its SLAs. Some of the challenges that metrics solve for microservices applications running on Kubernetes include: Calico is the most adopted technology for Kubernetes networking and security.
The Pleasure of Finding Things Out: Federated Search Across All Major Cloud Providers and Native Support for Amazon Security Lake
The newly released Cribl Search 4.2 brings enhancements that ease data management in today’s complex, cloud-centric environments. This update provides comprehensive compatibility with all major cloud providers – Amazon S3, Google Cloud Storage, and Azure Blob Storage. It also ushers in native support for Amazon Security Lake. In this blog post, we’ll examine how new dataset providers enhance the value that Cribl Search delivers, out of the box.
Container Security Fundamentals - Linux Namespaces (Part 4): The User Namespace
Calico monthly roundup: July 2023
Welcome to the Calico monthly roundup: July edition! From open source news to live events, we have exciting updates to share—let’s get into it!
This VideoGame Vulnerability was a Huge Headache: Unpacking Log4j Ep.22 | Security Insights Podcast
How NinjaOne Rescues H.E.R.O.S. After A Ransomware Attack
Modernizing the Air Force: DAFITC 2023
D2iQ is excited to be participating in the Department of the Air Force Information Technology and Cyberpower (DAFITC) 2023, in Montgomery, Alabama, from August 28-30. The theme of this year’s DAFITC conference is “Digitally Transforming the Air & Space Force: Investing for Tomorrow’s Fight.” Digital transformation of the Air Force and Space Force is part of a wider modernization effort that is accelerating across all U.S.
G2's Most Recommended WAF & DDoS Protection
In case you missed it, HAProxy Technologies recently put out a press release about our stunning leadership position in G2’s Summer 2023 Grid® Reports for load balancing. We’re incredibly proud of these results, which are a direct result of the hard work and dedication of HAProxy’s community developers and our enterprise product and support teams. Looking at the Momentum Grid® Report for Load Balancing, the gap between HAProxy and the rest is impossible to ignore.
CIS Benchmarks Explained: Levels + Steps for Quick CIS Benchmark Compliance
Enhancing Security Workflows with Real-Time Notifications via Microsoft Teams and Slack
The integration with popular collaboration platforms like Microsoft Teams and Slack marks a pivotal advancement in security workflows. We are introducing new capability to post events from Flowmon ADS into Teams channel or Slack to instantly notify security teams. Integrations scripts are based on simple webhooks and available out of the box on our support portal both for Teams and Slack.
The Power of Gartner Magic Quadrant for Endpoint Protection Platforms (EPP)
As someone deeply immersed in the cybersecurity field for over 20 years, I have witnessed firsthand the impact of the Gartner® Magic Quadrant™ analysis on technology vendors, service providers, and their customers. Throughout my career, I have held various roles, including Global Head of Security Engineering at Warner Bros. Discovery, CTO and Co-Founder of Trapezoid, Inc., and currently, Field CISO Americas at SentinelOne.
How to record a business process with Kosli's Audit Trail
Have you ever needed to provide proof that a critical business process actually took place? It’s a painful process involving all kinds of paperwork, but it’s the reality for many organizations working in highly regulated industries. For these companies, records need to be kept for actions like the provisioning of user accounts and access to sensitive records. It’s necessary, but it’s manual and time-consuming work.
Stay on top of every change with Kosli Notifications
In this short blog, you will learn how to set up Kosli Notifications so your whole team can stay on top of environment changes and compliance events in real time. 🚀 In fast-paced technology landscapes, understanding how systems are changing is crucial. Developers, DevOps/Platform/SRE teams, security personnel, and management all need this information to manage operational risk, resolve incidents, and just for basic communication with each other.
Common API Vulnerabilities and How to Secure Them
SolarWinds Named Supplier on the Crown Commercial Service's G-Cloud 13 Framework
4 Reasons MSPs Should Be Using Cybersecurity Frameworks
Cybercriminals have become increasingly sophisticated, employing aggressive and ever-changing techniques to breach small and medium-sized businesses (SMBs). These attacks are on the rise, posing a significant threat to organizations that lack robust cybersecurity measures. Hackers are relentless in their efforts to exploit vulnerabilities in SMBs’ systems, often due to their comparatively weaker security infrastructure.
The First 48 Hours of Ransomware Incident Response
The Quixotic Expedition Into the Vastness of Edge Logs, Part 2: How to Use Cribl Search for Intrusion Detection
For today’s IT and security professionals, threats come in many forms – from external actors attempting to breach your network defenses, to internal threats like rogue employees or insecure configurations. These threats, if left undetected, can lead to serious consequences such as data loss, system downtime, and reputational damage. However, detecting these threats can be challenging, due to the sheer volume and complexity of data generated by today’s IT systems.
How to Harness Technology for Effective Digital Marketing
How to Get Started with a Security Data Lake
Cloud Native Security Must Go Beyond the Perimeter
One month after the MOVEit vulnerability was first reported, it continues to wreak havoc on U.S. agencies and commercial enterprises. Unfortunately, the victim list keeps growing and includes organizations such as the U.S. Department of Health and Human Services, the U.S. Department of Energy, Merchant Bank, Shell, and others.
Cybersecurity Myth Busting Ep. 21 | Security Insights Podcast
Government Organizations Embrace Upskilling In-House IT Staff to Meet the Latest Executive Orders
This post was co-written by Nazhin Beiramee, Jazmin Childress, Kevin Clark, and Nick Weiss. Advancement in technology, along with the ever changing political landscape (e.g., the Executive Order on Transforming Federal Customer Experience and Service Delivery to Rebuild Trust in Government, as well as billions in funding to support this mandate, and a potential administration change after the 2024 election) uncover new needs, opportunities, and demands for government organizations.
What Should You Do If One Of Your Employees Gets Hurt Outside Of Work?
Azure's Robust Journey with GDPR Compliance
In an age where data is the new gold, safeguarding personal information has become more vital than ever before. The General Data Protection Regulation, or GDPR, is no longer a buzzword in the corporate corridors of Europe; it’s a binding legislation that has set the global standard for privacy and security. Enter the world of Microsoft Azure, one of the leading cloud computing platforms that’s shaping the way businesses store, manage, and analyze data.
Cisco completes Cisco AppDynamics and Cisco Secure Application IRAP assessment
Learn why IRAP recognition at the PROTECTED level for Cisco AppDynamics and Cisco Secure Application enables end users to rest assured their applications are secure. Cisco has completed an Infosec Registered Assessors Program (IRAP) assessment of Cisco AppDynamics and Cisco Secure Application at the PROTECTED level. This milestone represents a crucial step in reaffirming Cisco’s commitment to its Australian public sector customers, including its industry partners.
Exploring AKS networking options
At Kubecon 2023 in Amsterdam, Azure made several exciting announcements and introduced a range of updates and new options to Azure-CNI (Azure Container Networking Interface). These changes will help Azure Kubernetes Services (AKS) users to solve some of the pain points that they used to face in previous iterations of Azure-CNI such as IP exhaustion and big cluster deployments with custom IP address management (IPAM).
The Uphill Battle of Consolidating Security Platforms
A recently conducted survey of 51 CISOs and other security leaders a series of questions about the current demand for cybersecurity solutions, spending intentions, security posture strategies, tool preferences, and vendor consolidation expectations. While the report highlights the trends around platform consolidation over the short run, 82% of respondents stated they expect to increase the number of vendors in the next 2-3 years.
An Insider Look at Zero Trust with GDIT DevSecOps Experts
As cyber attacks have become ever more sophisticated, the means of protecting against cyber attacks have had to become more stringent. With zero trust security, the model has changed from “trust but verify” to “never trust, always verify.” Joining D2iQ VP of Product Dan Ciruli for an in-depth discussion of zero trust security was Dr. John Sahlin, VP of Cybersolutions at General Dynamics Information Technology (GDIT), and David Sperbeck, DevSecOps Capability Lead at GDIT.
5 important features to look for in cybersecurity applications
In today’s digital landscape, organizations need the right cybersecurity applications to address evolving cyber threats effectively. To keep security teams aligned and streamline mission-critical workflows, one of the most important cybersecurity applications organizations need is a secure and efficient cybersecurity collaboration platform that enables seamless communication, information sharing, and coordinated incident response.