Five worthy reads: Private 5G-Your fastest way to successful digital transformation
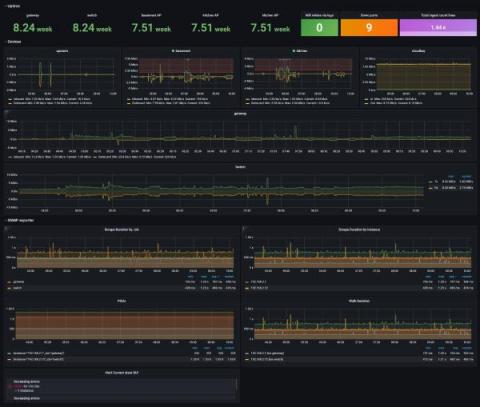
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore how Private 5G is impacting organizations worldwide. Digital transformation (DX) integrates digital technology into different areas of an organization to help change the way it operates and deliver value to its customers. Organizations that offer a higher value to their customers gain a competitive advantage over others in the marketplace.