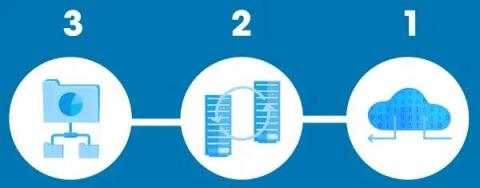
Understanding the 3-2-1 Backup Rule
While data disasters are inevitable, having a planned backup strategy can mitigate its damaging effects. According to the Cybersecurity and Infrastructure Security Agency, businesses and organizations should observe the 3-2-1 backup strategy for assured data safety. Superficially, the 3-2-1 backup rule is a backup strategy that increases and diversifies the number of backups used.