The Quixotic Expedition into the Vastness of Edge Logs, Part 1: Analyzing Numerous Cribl Edge Nodes with Cribl Search
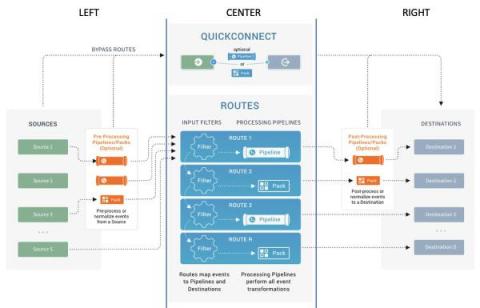
Cribl Search is a powerful tool that is designed to enhance your data search efficiency, irrespective of the location of your data. This blog will explore how this tool seamlessly integrates with numerous Cribl Edge Nodes in real time, simplifying the process of discovery and troubleshooting. An integral part of Cribl Search is the “teleport” feature, which enables users to access specific Edge Nodes for in-depth analysis, simply by clicking on a host field.