Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
It's Not Black Magic: Malware & Ransomware in Plain English
Aggregate Data in Cribl Stream to Optimize Your SIEM Data and Its Performance
Major Hospital System Cuts Azure Sentinel Costs by Over 50% with Observo.ai
Revealing Suspicious VPN Activity with Anomaly Detection
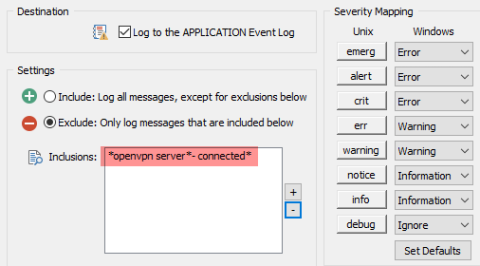
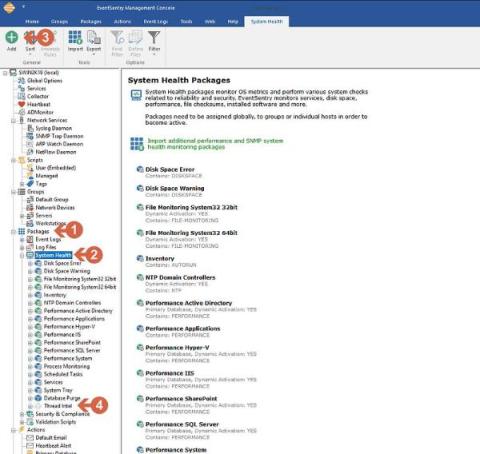
EventSentry Troubleshooting: Managing Database Size
EventSentry Troubleshooting: Reducing the number of email notifications
5 Best SIEM Tools and How to Choose
Cybersecurity has become something of great concern to the IT world over the last few years. The increase in remote working and the move to cloud-based and e-commerce solutions have opened up many new opportunities for cyber exploits and malware attacks. According to the FBI, the incidence of malware and network attacks, particularly ransomware, on both commercial and home systems has shown a major increase. At a corporate and personal level, ID theft has also increased greatly.
Predict the Future! A universal approach to detecting malicious PowerShell activity
So, here’s the deal with AntiVirus software these days: It’s mostly playing catch-up with super-fast athletes — the malware guys. Traditional AV software is like old-school detectives who need a picture (or, in this case, a ‘signature’) of the bad guys to know who they’re chasing. The trouble is, these malware creators are quite sneaky — constantly changing their look and creating new disguises faster than AntiVirus can keep up with their photos.
Sending Data to Elastic Security With Cribl Stream (And Making It Work With Elastic SIEM)
Cribl Stream is a real-time security and observability data processing pipeline that can be used to collect, transform, enrich, reduce, redact, and route data from a variety of sources to a variety of destinations. One of the popular destinations for Cribl users is Elastic SIEM. This blog post will walk you through the steps on how to set up Cribl Stream to normalize and forward data to use with Elastic Security for SIEM.