Operations | Monitoring | ITSM | DevOps | Cloud
February 2023
Cribl Stream 4.0: New Features, New User Interface, and Much More
Enabling TLS on a Cribl Leader Node: Step-by-Step Guide
Securing your internal systems with TLS can be a daunting task, even for experienced administrators. However, with the right tools and guidance, the process can be made more manageable. In this blog, we’ll show you how to enable TLS for your internal systems on your Cribl Leader Node. We’ll walk you through the steps, and provide a video tutorial embedded below to help you follow along.
Using Cribl Search for Anomaly Detection: Finding Statistical Outliers in Host CPU Busy Percentage
Using Cribl Search for Anomaly Detection: Finding Statistical Outliers in Host CPU Busy Percentage
In this blog post, we’ll demonstrate how to use Cribl Search for anomaly detection by finding statistical outliers in host CPU usage. By monitoring the “CPU Busy” metric, we can identify unusual spikes that may indicate malware penetration or high load/limiting conditions on customer-facing hosts. The best part? This simple but powerful analytic is easily adaptable to other metrics, making it a versatile tool for any data-driven organization.
How the All in One Worker Group Fits Into the Cribl Stream Reference Architecture
Fixing Security's Data Problem: Strategies and Solutions with Cribl and CDW
Bracing for Impact: Why a Robust Observability Pipeline is Critical for Security Professionals in 2023
2023 is well underway and now more than ever it’s important to stay ahead of data trends and security concerns that are ever mounting. With the cost of catastrophic cyber attacks estimated to be ten times that of all other disasters combined, businesses need to take proactive measures to implement a security data pipeline to protect their data and comply with security and retention requirements.
AWS Configuration for the Cribl Pack for SentinelOne Cloud Funnel
In the blog titled “Streamline Endpoint Data with Cribl Pack for SentinelOne Cloud Funnel” we dove into the Cloud Funnel data, its relevance in the modern SOC, and how Cribl Stream transforms the data while addressing visibility gaps. We left the AWS-specific details to this blog for those not yet familiar with configuring AWS S3 buckets, SQS Queues, and Identity and Access Management (IAM).
Streamline Endpoint Data with the Cribl Pack for SentinelOne Cloud Funnel
Cribl empowers you to take control of your observability, telemetry, and security data. Wherever your data originates from, wherever your data needs to go, and whatever format your data needs to be in, Cribl gives you the freedom and flexibility to make choices instead of compromises. Addressing visibility gaps by ingesting more data sources as the threat surface continues to expand has been a challenge.
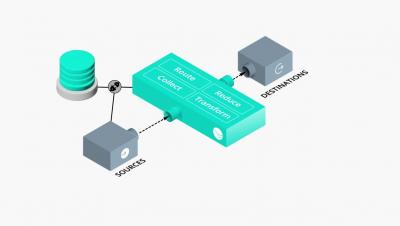
Introducing the Cribl Stream Reference Architecture
Empowering SecOps Admins: Getting the Most Value from CrowdStrike FDR Data with Cribl Stream
Tackling the Security Budget in Times of Economic Uncertainty: IT and Security Leaders Prioritize Cybersecurity
In today’s economic climate, IT and security budget owners are always looking for ways to increase efficiency while controlling costs. With tighter budgets and increasing workloads, organizations have to find ways of stretching their limited resources while making sure investments are paying off.
Future Cybersecurity Attacks Predicted to Cost 10x More Than Natural Disasters
Enterprises are entering 2023 following an increase in large-scale cybersecurity attacks over the last several years — Colonial Pipeline, Solarwinds, and even Twitter have all been victims — but events like these are not just increasing in number and sophistication. The amount of money involved is enough to make your head spin.
The Future of Tech: Exploring AI/ML and ChatGPT
You don’t often see real change, but when you do see it you know it. Artificial Intelligence/Machine Learning toolsets like ChatGPT are finally starting to offer broad capabilities that will benefit a mass audience. These tools are moving out of the domain of data scientists and math nerds and into mass markets with a little bit for everyone. The potential reach is awesome and a little scary.
Observing and Securing the Supercloud
The supercloud concept promises fewer accidental architectures and more cohesive cloud deployments with better manageability. Delivering on this vision requires a mix of vendor-agnostic tooling for performance monitoring and securing data.
Enforce Quotas on Data Ingestion with Redis
Recently, a customer brought me a challenging use case: They were looking to enforce quotas on their internal customers, i.e. other teams in the organization. The analytics team provides services such as searching and reporting capabilities to those other teams, which subscribe to the services through a chargeback model. Each team that subscribes is supposed to limit its ingestion of data to a quota: a maximum permitted ingest per 24-hour period.
In a Toxic Relationship with Your Current Observability Search Tool? There's Other Fish in the Sea
IT tools are similar to romantic relationships. Over time, you tend to fall into the same old dull routines, like Rupert Holme’s song Escape (The Piña Colada Song). That routine — collect dataset, route, ingest ($$) and then search, collect dataset, route, ingest, then search, … this approach is not only breaking your heart but your budget too.
Cribl's Zachary Kilpatrick Awarded 2023 Channel Chief Award from CRN for Second Consecutive Year
The Cribl Partner Program is designed to be a comprehensive solution for organizations looking to grow their customer relationships and revenue streams, while also enabling a fast deployment of observability solutions to serve customers. Our partners receive extensive training, tools, and support to unlock the full potential of observability data for their customers.