Operations | Monitoring | ITSM | DevOps | Cloud
November 2023
Diving into JTAG - Overview (Part 1)
As the first segment of a three-part series on JTAG, this post will give an overview of JTAG to set up some more in-depth discussions on debugging and JTAG Boundary-Scan. We will dive into the intricacies of the interface, such as the Test Access Port (TAP), key registers, instructions, and JTAG’s finite state machine. Like Interrupt? Subscribe to get our latest posts straight to your inbox.
NXP + Memfault + Golioth: Bringing Observability and Device Management to IoT Devices
Visualizing Real-time Data With STMViewer
If you’ve ever wanted to plot data acquired on your embedded target, this article is for you. It explores common use cases for real-time data visualization using STMViewer. Say goodbye to manual, time-consuming, and error-prone data collection and display methods to speed up your debugging process.
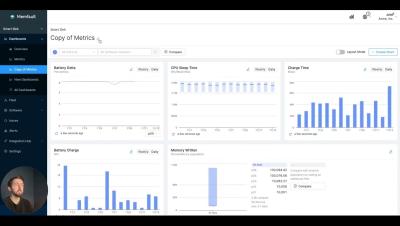
Configurable Dashboards || Memfault Feature Highlights
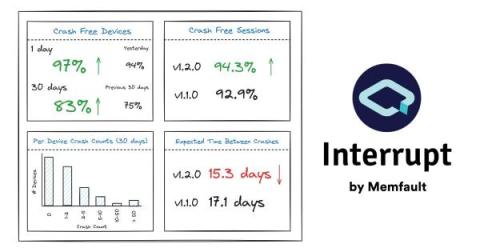
Counting Crashes to Improve Device Reliability
The first step to making reliable IoT devices is understanding that they are inherently unreliable. They will never work 100% of the time. This is partially because we firmware engineers will never write perfect code. Even if we did, our devices need to operate through various networks and gateways, such as cellular modems, mobile phone Bluetooth applications, Wi-Fi routers, cloud backends, and more, and each of these may introduce unreliability.