Kubernetes Security Considerations for IDS/IPS in the age of TLS v1.3
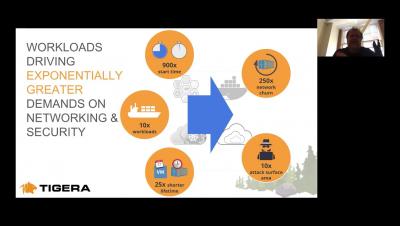
TLS v1.3 introduces several new security improvements over TLS 1.2 but some of these enhancements have an impact on network-based security solutions such as IDS/IPS. While the goal is to enhance the overall security at the application level, there are a few scenarios that are not easily solved when introducing the new technology, especially in Kubernetes environments. Watch this webinar to learn about security and compliance considerations for Kubernetes when implementing TLS v1.3.