Operations | Monitoring | ITSM | DevOps | Cloud
Quest
Data Explosion
Security and Compliance
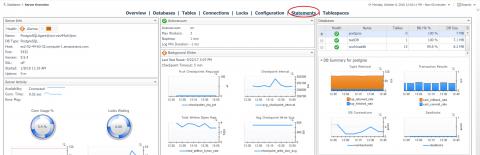
Optimize Postgres Query Performance with Foglight
One of the primary tasks of any DBA is to find and optimize poorly performing queries. This is not a trivial job as often times there is too much data to sort through and pinpoint problems. Quest’s Foglight provides alerts for Postgres queries that have suspect behavior.
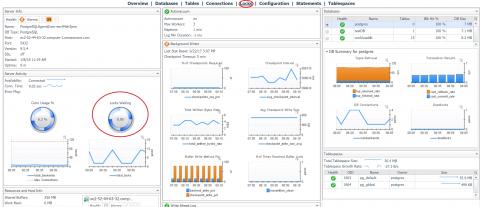
Monitoring and Managing Locks in Postgres with Foglight
One of the most valuable capabilities of Postgres is its support for concurrent ACID transactions. ACID is an acronym for Atomicity, Consistency, Isolation, and Durability. These database transaction properties help verify data validity. It is important to understand that locking can be a common occurrence in active Postgres databases. This is because Postgres uses these levels of locking as one of the ways to safely implement these (concurrent ACID) transactions.
Manage mobile devices with KACE Cloud MDM
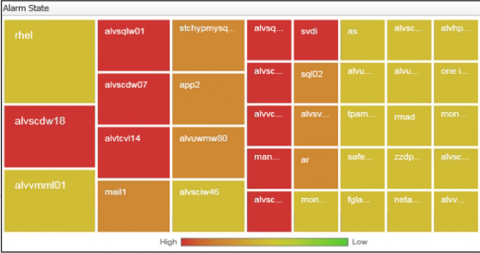
Take Your Monitoring Insights to another Level Using New Analytic Views
Foglight 5.9.3 (core Foglight release) includes among its features new components for building dashboards called “analytic views”. The new view types are: Scatter Plot Chart, Bubble Chart and Tree Map Chart. Specifically, I’ll cover here how to use these in the Foglight “Drag and Drop” interface to easily create new views that can show your monitoring data in new, powerful ways.
Groovy, groovier, grooviest: Getting metrics collected by Foglight
What if you could get a list of all metrics and observations collected by Foglight, and have the ability to filter/sort by cartridge and topology type? That would be groovy. My colleague Mark.Bai developed the script below. To run it, navigate to Administration -> Tooling -> Script Console. Select the Scripts tab and click the Add button.