Operations | Monitoring | ITSM | DevOps | Cloud
Quest
Don't Worry About Your (Con)figure, Have The PI !
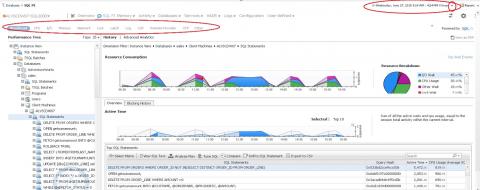
Congratulations! You have Foglight installed and it is collecting meaningful performance data. There’s no doubt it is providing a ‘smorgasbord’ of actionable information about your mission-critical environment. Help yourself to delicious servings of baseline data, proactive alerts, and custom dashboards and reports. Now make room for dessert! Foglight is probably best known for its generous helping of PI. PI is an abbreviation for Performance Investigator.
Quest Enhances KACE Product Line to Simplify Unified Endpoint Management
ALISO VIEJO, CALIF. – June 20, 2018 – Quest Software, a global systems management and security software provider, today announced several enhancements to its KACE product line. The updates enable and empower organizations as they move to a unified endpoint management (UEM) environment by simplifying their endpoint infrastructure to create a more secure computing environment.