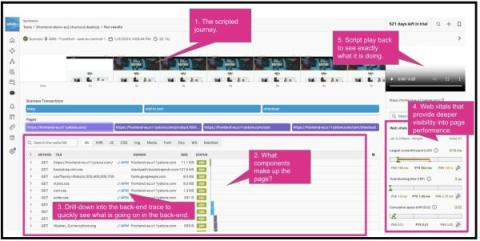
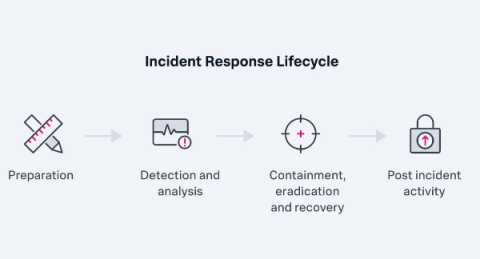
Up Your Observability Game With Attributes
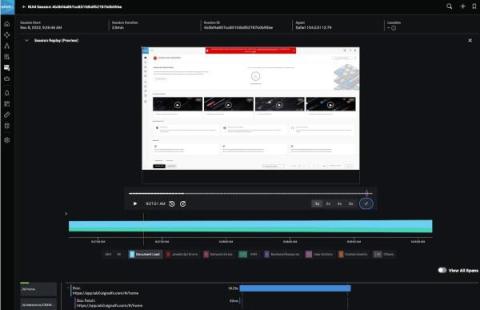
Splunk Observability Cloud includes powerful features which automatically identify patterns within your data to surface trends. The resulting insights tell you why some customers aren’t getting an optimal experience from your application, and how you can improve it. Unlocking these features requires attributes to be included with your application traces. But how do you know which attributes are the most valuable for your application and business?