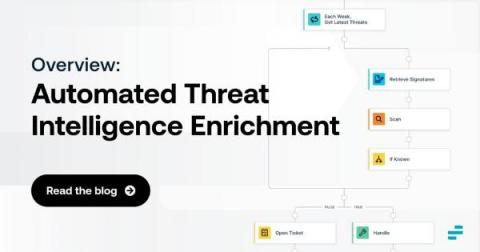
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.